Powerpoint Templates and Google slides for Security Facts
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Security Factors To Consider While Buying Nfts Training Ppt
Security Factors To Consider While Buying Nfts Training PptPresenting Security Factors to Consider while Buying NFTs. Our PowerPoint experts have included all the necessary templates, designs, icons, graphs, and other essential material. This deck is well crafted by extensive research. Slides consist of amazing visuals and appropriate content. These PPT slides can be instantly downloaded with just a click. Compatible with all screen types and monitors. Supports Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Security As A Factor For Choosing A Cryptocurrency Exchange Training Ppt
Security As A Factor For Choosing A Cryptocurrency Exchange Training PptPresenting Security as a Factor for choosing a Cryptocurrency Exchange. Our PowerPoint experts have included all the necessary templates, designs, icons, graphs, and other essential material. This deck is well crafted by extensive research. Slides consist of amazing visuals and appropriate content. These PPT slides can be instantly downloaded with just a click. Compatible with all screen types and monitors. Supports Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Multi factor authentication secure access process application server through
Multi factor authentication secure access process application server throughDeliver a lucid presentation by utilizing this Multi Factor Authentication Secure Access Process Application Server Through. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Multi Factor Authentication, Secure, Access, Process, Application. All the twelve slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
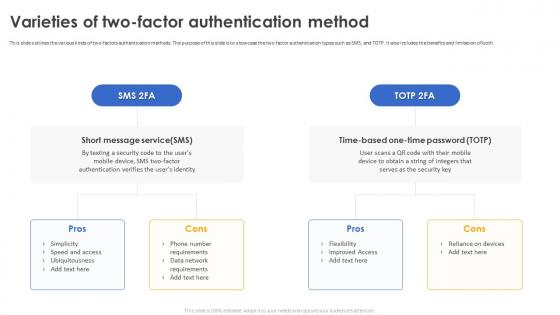 Secure Your Digital Assets Varieties Of Two Factor Authentication Method
Secure Your Digital Assets Varieties Of Two Factor Authentication MethodThis slide outlines the various kinds of two-factors authentication methods. The purpose of this slide is to showcase the two factor authentication types such as SMS, and TOTP. It also includes the benefits and limitation of both. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Varieties Of Two Factor Authentication Method. This template helps you present information on two stages. You can also present information on Phone Number Requirements, Data Network Requirements, Time Based One Time Password using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comprehensive Guide To Understand Two Factor Authentication For Improved Security Fin SS
Comprehensive Guide To Understand Two Factor Authentication For Improved Security Fin SSThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Present the topic in a bit more detail with this Comprehensive Guide To Understand Two Factor Authentication For Improved Security Fin SS. Use it as a tool for discussion and navigation on Possession Verification, Biometric Verification, Enter Username And Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Two Factor Authentication Process Flow For Enhanced Security E Wallets As Emerging Payment Method Fin SS V
Two Factor Authentication Process Flow For Enhanced Security E Wallets As Emerging Payment Method Fin SS VThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Present the topic in a bit more detail with this Two Factor Authentication Process Flow For Enhanced Security E Wallets As Emerging Payment Method Fin SS V. Use it as a tool for discussion and navigation on Authentication, Process, Possession Verification. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Factors Responsible For Cloud Security Failures Cloud Cryptography
Factors Responsible For Cloud Security Failures Cloud CryptographyThe purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc. Present the topic in a bit more detail with this Factors Responsible For Cloud Security Failures Cloud Cryptography. Use it as a tool for discussion and navigation on Information, Businesses, Cybersecurity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Interesting Facts In Powerpoint And Google Slides Cpb
Cyber Security Interesting Facts In Powerpoint And Google Slides CpbPresenting our Cyber Security Interesting Facts In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cyber Security Interesting Facts This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Adopt Two Factor Authentication To Reduce Hacking Hands On Blockchain Security Risk BCT SS V
Adopt Two Factor Authentication To Reduce Hacking Hands On Blockchain Security Risk BCT SS VThe following slide illustrates some tips and practices to ensure two factor authentication and safeguard blockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Increase audience engagement and knowledge by dispensing information using Adopt Two Factor Authentication To Reduce Hacking Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Restricts Unauthorized Access, Extends User Authentication, Safeguards Personal Key using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 NEO Banks For Digital Funds Two Factor Authentication Process Flow For Enhanced Security Fin SS V
NEO Banks For Digital Funds Two Factor Authentication Process Flow For Enhanced Security Fin SS VThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Deliver an outstanding presentation on the topic using this NEO Banks For Digital Funds Two Factor Authentication Process Flow For Enhanced Security Fin SS V. Dispense information and present a thorough explanation of Authentication Process Flow, Enhanced Security, Verify Biometrics, Authentication Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Your Digital Assets Factors To Consider While Selecting Cryptocurrency Wallet
Secure Your Digital Assets Factors To Consider While Selecting Cryptocurrency WalletThis slide discusses some attributes that should be considered while buying crypto wallets. This slide highlights factors such as customer service, fees, security, and types of crypto supported in the wallet, etc. Introducing Secure Your Digital Assets Factors To Consider While Selecting Cryptocurrency Wallet to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Buying Crypto Wallets, Customer Service, Security, Crypto Supported In The Wallet, using this template. Grab it now to reap its full benefits.
-
 Secure Your Digital Assets Overview And Working Of Two Factor Authentication
Secure Your Digital Assets Overview And Working Of Two Factor AuthenticationThis slide represents an overview and working of 2-factor authentication 2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security, it is user-friendly, etc. Deliver an outstanding presentation on the topic using this Secure Your Digital Assets Overview And Working Of Two Factor Authentication. Dispense information and present a thorough explanation of Phishing, Social Engineering, Password Brute Force Attacks, Prevents Attackers, Stolen Credentials using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Facts Investor Capital Pitch Deck For Pauboxs Secure Email Platform
Key Facts Investor Capital Pitch Deck For Pauboxs Secure Email PlatformThis slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies. Increase audience engagement and knowledge by dispensing information using Key Facts Investor Capital Pitch Deck For Pauboxs Secure Email Platform This template helps you present information on Three stages. You can also present information on Net Promoter Score, Owned Companies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management Process
Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management ProcessThe following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Introducing Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering, Data Breaches, Mobile Malware Attacks, using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Key Factors To Contribute Firewall Failures
Firewall Network Security Key Factors To Contribute Firewall FailuresThis slide describes the prominent causes of firewall system failures. The purpose of this slide is to showcase the four main factors that contribute the firewall failures, such as misconfiguration, software vulnerabilities, missing firewall policy, and hardware bottlenecks. Introducing Firewall Network Security Key Factors To Contribute Firewall Failures to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Protect The Firewall, Firewall Configuration Testing using this template. Grab it now to reap its full benefits.
-
 Connecting Ecosystems Introduction Security Factors To Consider When Two BCT SS
Connecting Ecosystems Introduction Security Factors To Consider When Two BCT SSThis slide mentions various security factors to be considered when multiple blockchain networks interoperate with each other. It mentions various compatibility factors and their corresponding considerations and means of reconciliation. Deliver an outstanding presentation on the topic using this Connecting Ecosystems Introduction Security Factors To Consider When Two BCT SS. Dispense information and present a thorough explanation of Cryptography, Decentralization, Consistency using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ensure Secure Access Icon Using Multi Factor Authentication Tool
Ensure Secure Access Icon Using Multi Factor Authentication ToolPresenting our set of slides with Ensure Secure Access Icon Using Multi Factor Authentication Tool. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure, Factor, Authentication.
-
 Provide Adaptive Security Icon Based On Multi Factor Authentication
Provide Adaptive Security Icon Based On Multi Factor AuthenticationPresenting our set of slides with Provide Adaptive Security Icon Based On Multi Factor Authentication. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Adaptive, Factor, Security.
-
 Reinforce Multi Factor Authentication Security For Unauthorized Use
Reinforce Multi Factor Authentication Security For Unauthorized UseThis slide showcases multi factor authentication practices for mitigating common security risks associated with relying solely on passwords. It includes aspects such as detailed multi factor authentication plan, configurable authentication factors, forgotten password plans, etc. Introducing our premium set of slides with Reinforce Multi Factor Authentication Security For Unauthorized Use. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Authentication, Configurable, Compatibility. So download instantly and tailor it with your information.
-
 Adopt Two Factor Authentication Securing Blockchain Transactions A Beginners Guide BCT SS V
Adopt Two Factor Authentication Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Introducing Adopt Two Factor Authentication Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Restricts Unauthorized Access, Extends User Authentication, Safeguards Personal Key, using this template. Grab it now to reap its full benefits.
-
 Digital Signal Processing In Modern Important Factors To Contemplate Regarding DSP Security
Digital Signal Processing In Modern Important Factors To Contemplate Regarding DSP SecurityThis slide represents the important attributes to contemplate DSP security. The purpose of this slide is to highlight the factors of DSPO security such as data encryption, Access control, secure communication, etc. Increase audience engagement and knowledge by dispensing information using Digital Signal Processing In Modern Important Factors To Contemplate Regarding DSP Security. This template helps you present information on twelve stages. You can also present information on Firmware Security, Physical Security, Secure Communication, Data Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Awareness Facts And Statistics Cyber Risk Assessment
Cyber Security Awareness Facts And Statistics Cyber Risk AssessmentThe following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Awareness Facts And Statistics Cyber Risk Assessment This template helps you present information on four stages. You can also present information on Malware Attacks, Company, Social Engineering using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Facts Investor Capital Pitch Deck For Secure Digital Payment Platform
Key Facts Investor Capital Pitch Deck For Secure Digital Payment PlatformThe following slide highlights key statistics and fact associated with company. It comprises of number of business leaders process, currencies and payment methods supported, accessible countries, etc. Increase audience engagement and knowledge by dispensing information using Key Facts Investor Capital Pitch Deck For Secure Digital Payment Platform This template helps you present information on four stages. You can also present information on Business Leaders, Payment Methods using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age It
Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc. Introducing Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Data Protection, Poor Key Management, Software Engineers, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Awareness Facts And Statistics Creating Cyber Security Awareness
Cyber Security Awareness Facts And Statistics Creating Cyber Security AwarenessThe following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Awareness Facts And Statistics Creating Cyber Security Awareness This template helps you present information on Four stages. You can also present information on Classify Incident, Continue Strengthening using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Factors Affecting Security Compliance In It Audit
Factors Affecting Security Compliance In It AuditFollowing slide showcases factors in IT audit that affect security compliance for risk mitigation. It further covers factors such as logical and physical security, regulatory compliance and hardware. Introducing our premium set of slides with Factors Affecting Security Compliance In It Audit. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Physical Security, Regulatory Compliance, Management System. So download instantly and tailor it with your information.
-
 Key Facts Secure Email Solution Investor Funding Elevator Pitch Deck By Paubox
Key Facts Secure Email Solution Investor Funding Elevator Pitch Deck By PauboxThis slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies. Introducing Key Facts Secure Email Solution Investor Funding Elevator Pitch Deck By Paubox to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Certified Since, Net Promoter, Fastest Growing Privately, using this template. Grab it now to reap its full benefits.
-
 Major Factors To Select Api Security Technology Stack
Major Factors To Select Api Security Technology StackThis slide showcases the crucial factors sheet choosing application programming interface security technology stack which helps an organization to minimize cyber and other potential risks. It include details such as accuracy, costs, automation, reliability, speed, etc. Introducing our Major Factors To Select Api Security Technology Stack set of slides. The topics discussed in these slides are Vulnerability Scanning, Virus Bounty Programs. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Awareness Facts And Statistics Implementing Strategies To Mitigate Cyber Security Threats
Cyber Security Awareness Facts And Statistics Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases some facts and figures to generate awareness about cyber crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc Introducing Cyber Security Awareness Facts And Statistics Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Malware Attacks, Employees, Social Engineering Attacks using this template. Grab it now to reap its full benefits.
-
 Key Facts Smart Farming Technology Pitch Deck For Food Security
Key Facts Smart Farming Technology Pitch Deck For Food SecurityFollowing slide showcases major facts associated with company performance. It includes elements such as average margin, total outstanding funding, disbursed funding, current year funding, cost etc. Increase audience engagement and knowledge by dispensing information using Following slide showcases major facts associated with company performance. It includes elements such as average margin, total outstanding funding, disbursed funding, current year funding, cost etc. This template helps you present information on Eight stages. You can also present information on Average Margin, Total Outstanding Funding using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Factors Considered While Strategic Retirement Planning To Build Secure Future Fin SS
Factors Considered While Strategic Retirement Planning To Build Secure Future Fin SSThis slide covers the three main factors considered while determining asset allocation strategies. The purpose of this template is to define the factors considered while developing a strategy. It covers information about time, risk and financial conditions. Deliver an outstanding presentation on the topic using this Factors Considered While Strategic Retirement Planning To Build Secure Future Fin SS. Dispense information and present a thorough explanation of Time Horizon, Risk Tolerance, Financial Situations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Factors For Updating Cyber Security Policy
Key Factors For Updating Cyber Security PolicyThis slide covers key reasons for updating cybersecurity policies. The purpose of this template is to serve as a quick reference for stakeholders, outlining the pivotal circumstances that necessitate policy revisions. It includes regulatory changes, technology upgrades, security incidents, and organizational shifts. Introducing our premium set of slides with Key Factors For Updating Cyber Security Policy Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Regulatory Changes, Technology Upgrades, Security Incidents. So download instantly and tailor it with your information.
-
 Mobile Security Two Factor Authentication Process
Mobile Security Two Factor Authentication ProcessThis slide showcases roadmap for 2FA mobile security and includes assessment, select solutions, planning and integration, implementation, etc. Presenting our set of slides with name Mobile Security Two Factor Authentication Process. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Assessment, Select Solution, Implementation, Testing And Optimization.
-
 Two Factor Authentication For Mobile Security Icon
Two Factor Authentication For Mobile Security IconIntroducing our premium set of slides with name Two Factor Authentication For Mobile Security Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Two Factor Authentication, Mobile Security Icon. So download instantly and tailor it with your information.
-
 Tokenization For Improved Data Security Factors To Consider While Choosing Tokenization Over Encryption
Tokenization For Improved Data Security Factors To Consider While Choosing Tokenization Over EncryptionThis slide showcases the aspects to consider while choosing tokenization over encryption. The purpose of this slide is to outline the aspects such as reduction of compliance scope, format attributes, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Factors To Consider While Choosing Tokenization Over Encryption. Dispense information and present a thorough explanation of Elimination Of Encryption Key Management, Format Attributes, Reduction Of Compliance Scope using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Benefits Of Using SMS In Two Factor Authentication Mobile Security
Benefits Of Using SMS In Two Factor Authentication Mobile SecurityThis slide represents the benefits of using SMS in two factor authentication in mobile security which includes security, speed and access and wide availability. Introducing Benefits Of Using SMS In Two Factor Authentication Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Security Policy, Mobile Security using this template. Grab it now to reap its full benefits.
-
 Common Threats Addressed By Two Factor Authentication Mobile Security
Common Threats Addressed By Two Factor Authentication Mobile SecurityThis slide discusses the common threats addressed by two factor authentication which includes stolen passwords, social engineering, key logging, etc. Increase audience engagement and knowledge by dispensing information using Common Threats Addressed By Two Factor Authentication Mobile Security This template helps you present information on Six stages. You can also present information on Sandbox Isolation, Robust Application using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Factors Of Authentication In Mobile Security Mobile Security
Key Factors Of Authentication In Mobile Security Mobile SecurityThis slide highlights the key factors of authentication in mobile security which include knowledge factor, inherence factor, time factor and possession factor. Increase audience engagement and knowledge by dispensing information using Key Factors Of Authentication In Mobile Security Mobile Security This template helps you present information on Six stages. You can also present information on Security Broker, Email Security, Virtual Private Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Two Factor Authentication In Mobile Security Mobile Security
Two Factor Authentication In Mobile Security Mobile SecurityThis slide gives an overview of two factor authentication in mobile security and is defined as specific type of multi-factor authentication which strengthens access. Increase audience engagement and knowledge by dispensing information using Two Factor Authentication In Mobile Security Mobile Security This template helps you present information on Five stages. You can also present information on Spear Phishing, Voice Phishing, Credential Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Types Of Two Factor Authentication In Mobile Security Mobile Security
Types Of Two Factor Authentication In Mobile Security Mobile SecurityThis slide discusses the types of two factor authentication in mobile security which includes SMS 2FA, push based 2FA, web authentication API and so on. Increase audience engagement and knowledge by dispensing information using Types Of Two Factor Authentication In Mobile Security Mobile Security This template helps you present information on Five stages. You can also present information on No Authentication, Hacker Access, Security Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Essential Factors For Fintech Cyber Security
Essential Factors For Fintech Cyber SecurityThis slide showcases the essential factors for fintech cyber security. Its aim is to manage the business policies and use the right risk management measures. This slide includes business nature, implementation cost, skills and generality. Presenting our set of slides with name Essential Factors For Fintech Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implementation Cost, Generality, Skills, Business Nature .
-
 Fintech Cyber Security Influencing Factors
Fintech Cyber Security Influencing FactorsThis slide showcases factors influencing fintech cyber security. Its aim is to implement factors for securing fintech cyber security. This slide includes management, responsibilities, budget, training, monitor and documentation. Introducing our premium set of slides with name Fintech Cyber Security Influencing Factors. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Budget, Training, Responsibilities, Monitor. So download instantly and tailor it with your information.
-
 Cyber Security Risk Factors In Banking
Cyber Security Risk Factors In BankingThis slide represents emerging cyber security risks faced in banking industry. This slide aims to report bank network security risk related to growth of service providers incorporated into network. It includes various threats such as supply chain attacks, phishing, ransomware attacks, etc. Presenting our set of slides with Cyber Security Risk Factors In Banking. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Social Engineering Attacks, Phishing, Supply Chain Networks.
-
 Factors Contributing To Rising Cyber Security Risks In Finance And Banking
Factors Contributing To Rising Cyber Security Risks In Finance And BankingThis slide represents factors affecting cyber security concerns in finance and banking. It aims to continually invest in cyber security measures, employee training, and threat intelligence to protect from evolving landscape of cyber security risks. It includes various elements such as factors, description and strategies to reduce risks. Presenting our set of slides with Factors Contributing To Rising Cyber Security Risks In Finance And Banking. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Third Party Vendors, Onboarding New Technologies, Cloud Cybercrimes.
-
 Factors To Consider For Cyber Security Risks In Banking
Factors To Consider For Cyber Security Risks In BankingThis slide represents key considerations for cyber security concerns in banking. It aims to continually assess and adapt cyber security strategies to address evolving threats and ensure protection of sensitive financial and customer data. It includes various approaches such as cloud vulnerabilities, endpoint security, etc. Introducing our premium set of slides with Factors To Consider For Cyber Security Risks In Banking. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Emerging Technology, Vulnerabilities Cloud, Endpoint Security. So download instantly and tailor it with your information.
-
 Two Factor Authentication To Enhance Chatbot Security
Two Factor Authentication To Enhance Chatbot SecurityThis slide shows a process that can be used to highlight how companies can use two-factor authentication to protect their chatbots against various security threats or vulnerabilities. It include three stages which are user enters credentials, OTP is sent to the user and user uses OTP to verify hi identity. Presenting our set of slides with Two Factor Authentication To Enhance Chatbot Security. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication Key, Username, Email.
-
 Security facts and programme management template ppt sample file
Security facts and programme management template ppt sample filePresenting security facts and programme management template ppt sample file. This is a security facts and programme management template ppt sample file. This is a six stage process. The stages in this process are consultancy, adverse event management, audit and testing, post market surveillance, solutions, regularity compliance.
-
 Job security factors ppt powerpoint presentation model graphics download cpb
Job security factors ppt powerpoint presentation model graphics download cpbPresenting our Job Security Factors Ppt Powerpoint Presentation Model Graphics Download Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Job Security Factors. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Digital Security Facts Ppt Powerpoint Presentation Model Themes Cpb
Digital Security Facts Ppt Powerpoint Presentation Model Themes CpbPresenting Digital Security Facts Ppt Powerpoint Presentation Model Themes Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Digital Security Facts. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber Threat Facts Figures And Statistics Security Incident Response Playbook
Cyber Threat Facts Figures And Statistics Security Incident Response PlaybookThis slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack. Increase audience engagement and knowledge by dispensing information using Cyber Threat Facts Figures And Statistics Security Incident Response Playbook. This template helps you present information on six stages. You can also present information on Cyberattacks, Ransomware, Statistics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Healthcare Cloud Security Factors To Protect Data
Healthcare Cloud Security Factors To Protect DataThis slide covers the importance of healthcare cloud security. The purpose of this template is to define the elements used to adopt health information technology in an organization. It includes details related to the security, awareness, data protection and adapting measures. Presenting our set of slides with name Healthcare Cloud Security Factors To Protect Data. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Security, Data Protection, Importance Of Security.
-
 F1561 Factors To Consider While Selecting Security Cameras Iot Smart Homes Automation IOT SS
F1561 Factors To Consider While Selecting Security Cameras Iot Smart Homes Automation IOT SSThis slide provides an overview of the consideration factors for purchasing security cameras. Major factors covered are video resolution, field of view, night vision, multi-factor authentication, facial recognition and privacy shutter. Increase audience engagement and knowledge by dispensing information using F1561 Factors To Consider While Selecting Security Cameras Iot Smart Homes Automation IOT SS. This template helps you present information on six stages. You can also present information on Video Resolution, Field Of View, Night Vision using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Factors Affecting Security And Communication Plan For Large Event Costings
Factors Affecting Security And Communication Plan For Large Event CostingsThis slide highlights major factors which affect the cost structure and budget allocations for security and communication plans for large events. Key factors are event security experience, time and place of the event, size of event, etc.Introducing our premium set of slides with Factors Affecting Security And Communication Plan For Large Event Costings. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Event Security Experience, Armed Unarmed Security, Communication Tools. So download instantly and tailor it with your information.
-
 Factors For Cloud Computing Security Audit
Factors For Cloud Computing Security AuditThe slide highlights the factors to be considered while auditing the cloud services for data protection. Various factors considered are transparency, encryption and colocation. Introducing our premium set of slides with factors for Factors For Cloud Computing Security Audit. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Transparency, Encryption, Colocation . So download instantly and tailor it with your information.
-
 SDN Security IT Factors Influencing Software Defined Networking SDN Adoption
SDN Security IT Factors Influencing Software Defined Networking SDN AdoptionThis slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Introducing SDN Security IT Factors Influencing Software Defined Networking SDN Adoption to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Software, Influencing, Networking, using this template. Grab it now to reap its full benefits.
-
 Factors Of Successful Byod Phone Security Policy
Factors Of Successful Byod Phone Security PolicyThis slide show factors for creating an effective BYOD security policy for phone. The purpose of this slide is to highlight all important factors for framing BYOD policy at workplace. It include factors such as be specific, follow strict policy, etc. Presenting our set of slides with Factors Of Successful Byod Phone Security Policy. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Be Specific, Follow Strict Security.
-
 Two Factor Authentication Process Security Mobile Banking For Convenient And Secure Online Payments Fin SS
Two Factor Authentication Process Security Mobile Banking For Convenient And Secure Online Payments Fin SSThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Present the topic in a bit more detail with this Two Factor Authentication Process Security Mobile Banking For Convenient And Secure Online Payments Fin SS. Use it as a tool for discussion and navigation on Authentication, Process, Possession Verification . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Facts Awake Security Investor Funding Elevator Pitch Deck
Key Facts Awake Security Investor Funding Elevator Pitch DeckThe following slide showcases various statistics outlining company overview that assists investors to gain understanding of business performance. It consists of threat detection accuracy, false positive rete, mean time to respond, customer satisfaction score and security incident response time. Introducing Key Facts Awake Security Investor Funding Elevator Pitch Deck to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Detection Accuracy, Positive Rate, Customer Satisfaction, using this template. Grab it now to reap its full benefits.
-
 Risk factors defining service delivery system development data security and management
Risk factors defining service delivery system development data security and managementPresenting this set of slides with name - Risk Factors Defining Service Delivery System Development Data Security And Management. This is a six stage process. The stages in this process are Risk Factors, Risk Management, Risk Variable.
-
 Risk factors showing innovation cyber security price capital access and productivity
Risk factors showing innovation cyber security price capital access and productivityPresenting this set of slides with name - Risk Factors Showing Innovation Cyber Security Price Capital Access And Productivity. This is a five stage process. The stages in this process are Risk Factors, Risk Management, Risk Variable.




