Powerpoint Templates and Google slides for Security Engine
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Social Engineering In Cyber Security Training Ppt
Social Engineering In Cyber Security Training PptPresenting Social Engineering in Cyber Security. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
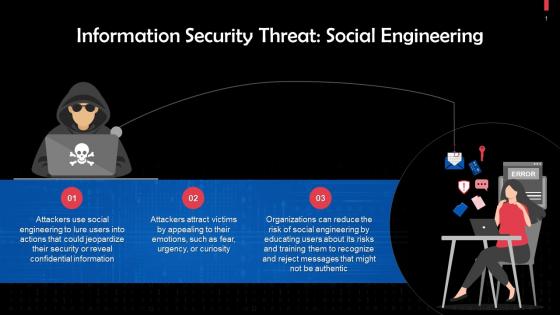 Social Engineering As An Information Security Threat Training Ppt
Social Engineering As An Information Security Threat Training PptPresenting Social Engineering as an Information Security Threat. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Social Engineering Training Awareness And Defense IT Security Awareness Training Cybersecurity SS
Social Engineering Training Awareness And Defense IT Security Awareness Training Cybersecurity SSThis slide represents overview of training course for mitigating cybercrime which involves tracking a target into giving money or data. It includes details related to training program overview, target audience etc. Introducing Social Engineering Training Awareness And Defense IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering Training, Awareness And Defense Course Outline, Training Program Overview, Target Audience, using this template. Grab it now to reap its full benefits.
-
 Reverse engineering cyber security ppt powerpoint presentation infographic portfolio cpb
Reverse engineering cyber security ppt powerpoint presentation infographic portfolio cpbPresenting Reverse Engineering Cyber Security Ppt Powerpoint Presentation Infographic Portfolio Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Reverse Engineering Cyber Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Social Engineering Attacks Prevention Checklist To Secure Organizations From Social Engineering
Social Engineering Attacks Prevention Checklist To Secure Organizations From Social EngineeringThis slide outlines the steps to be taken to protect the organization and its employees from social engineering attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan. Present the topic in a bit more detail with this Social Engineering Attacks Prevention Checklist To Secure Organizations From Social Engineering. Use it as a tool for discussion and navigation on Provide Staff Training, Multi Factor Authentication, Develop An Incident Response Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Digital Systems Engineering Creation Of Secure Networks Using Mbse Principles
Digital Systems Engineering Creation Of Secure Networks Using Mbse PrinciplesThe purpose of this slide is to explain how MBSE principles can be applied to create secure networks and align with the criteria and models of information security management systems. This slide also highlights the steps involved, such as plan, do, check, and act. Present the topic in a bit more detail with this Digital Systems Engineering Creation Of Secure Networks Using Mbse Principles. Use it as a tool for discussion and navigation on Techniques, Information, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Engineering Icon To Enhance Information Security
Data Engineering Icon To Enhance Information SecurityPresenting our well structured Data Engineering Icon To Enhance Information Security. The topics discussed in this slide are Data Engineering Icon, Enhance Information Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Creation Of Secure Networks Using MBSE Integrated Modelling And Engineering
Creation Of Secure Networks Using MBSE Integrated Modelling And EngineeringThe purpose of this slide is to explain how MBSE principles can be applied to create secure networks and align with the criteria and models of information security management systems. This slide also highlights the steps involved, such as plan, do, check, and act. Present the topic in a bit more detail with this Creation Of Secure Networks Using MBSE Integrated Modelling And Engineering. Use it as a tool for discussion and navigation on Series Of Steps, Overview, Check. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Lifecycle In Mobile Security Mobile Security
Social Engineering Lifecycle In Mobile Security Mobile SecurityThis slide gives an overview of lifecycle of social engineering in mobile security which includes information gathering, developing relationship, exploitation, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Lifecycle In Mobile Security Mobile Security This template helps you present information on Five stages. You can also present information on Create An Asset Inventory, Software Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Objectives Of Social Engineering Awareness Program IT Security Awareness Training Cybersecurity SS
Objectives Of Social Engineering Awareness Program IT Security Awareness Training Cybersecurity SSThis slide represents objectives for facilitating training related to cybercrime which involves tracking a target into giving money or data. It includes objectives such as implementing strategies for mitigating personnel attacks etc. Introducing Objectives Of Social Engineering Awareness Program IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering Attacks, Prevent Data Breaches, Procedures For Defeating Deceptions, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Attack Prevention Techniques Building A Security Awareness Program
Social Engineering Attack Prevention Techniques Building A Security Awareness ProgramThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. Deliver an outstanding presentation on the topic using this Social Engineering Attack Prevention Techniques Building A Security Awareness Program. Dispense information and present a thorough explanation of Public Information, Prevention Techniques, Social Engineering Attack using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Attack Prevention Techniques Conducting Security Awareness
Social Engineering Attack Prevention Techniques Conducting Security AwarenessThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Conducting Security Awareness. Use it as a tool for discussion and navigation on Techniques, Limit Public Information, Verify Source. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attack Prevention Techniques Developing Cyber Security Awareness Training
Social Engineering Attack Prevention Techniques Developing Cyber Security Awareness TrainingThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. Deliver an outstanding presentation on the topic using this Social Engineering Attack Prevention Techniques Developing Cyber Security Awareness Training. Dispense information and present a thorough explanation of Limit Public Information, Verify The Source, No Sharing Of Password using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security
Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Limit Public Information, Verify The Source, No Sharing Of Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attack Prevention Techniques Implementing Security Awareness Training
Social Engineering Attack Prevention Techniques Implementing Security Awareness TrainingThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Limit Public Information, Verify The Source, No Sharing Of Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attack Prevention Techniques Raising Cyber Security Awareness In Organizations
Social Engineering Attack Prevention Techniques Raising Cyber Security Awareness In OrganizationsThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Raising Cyber Security Awareness In Organizations. Use it as a tool for discussion and navigation on Verify The Source, Sharing Of Password, Public Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devops engineer skills software security skills ppt summary graphics pictures
Devops engineer skills software security skills ppt summary graphics picturesThis slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Introducing Devops Engineer Skills Software Security Skills Ppt Summary Graphics Pictures to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability Management, Compliance Monitoring, Code Analysis, Security Training, Change Management, using this template. Grab it now to reap its full benefits.
-
 Outlook Of Social Engineering Attack Building A Security Awareness Program
Outlook Of Social Engineering Attack Building A Security Awareness ProgramThe purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Deliver an outstanding presentation on the topic using this Outlook Of Social Engineering Attack Building A Security Awareness Program. Dispense information and present a thorough explanation of Congratulation, Engineering Attack using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Outlook Of Social Engineering Attack Developing Cyber Security Awareness Training Program For Staff
Outlook Of Social Engineering Attack Developing Cyber Security Awareness Training Program For StaffThe purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Increase audience engagement and knowledge by dispensing information using Outlook Of Social Engineering Attack Developing Cyber Security Awareness Training Program For Staff. This template helps you present information on one stages. You can also present information on Social Engineering, Attack Works, Completion Of A Survey using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Outlook Of Social Engineering Attack Conducting Security Awareness
Outlook Of Social Engineering Attack Conducting Security AwarenessThe purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Deliver an outstanding presentation on the topic using this Outlook Of Social Engineering Attack Conducting Security Awareness. Dispense information and present a thorough explanation of Employees, Social Engineering, Attack Works using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Outlook Of Social Engineering Attack Implementing Security Awareness Training
Outlook Of Social Engineering Attack Implementing Security Awareness TrainingThe purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Introducing Outlook Of Social Engineering Attack Implementing Security Awareness Training to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Engineering Attack, Completion Of A Survey, Social Engineering Attack, using this template. Grab it now to reap its full benefits.
-
 Security Engineer Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Security Engineer Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Security engineer colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Security Engineer Helmet Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Security Engineer Helmet Colored Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Security engineer helmet colored icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Security Engineer Helmet Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Security Engineer Helmet Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Security engineer helmet monotone icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Security Engineer Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Security Engineer Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Security engineer monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Security Management Engineer Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Security Management Engineer Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Security management engineer colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Security Management Engineer Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Security Management Engineer Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Security management engineer monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Outlook Of Social Engineering Attack Preventing Data Breaches Through Cyber Security
Outlook Of Social Engineering Attack Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Introducing Outlook Of Social Engineering Attack Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering, Employees, using this template. Grab it now to reap its full benefits.
-
 Cloud Engineering Data Security Service Icon
Cloud Engineering Data Security Service IconIntroducing our premium set of slides with Cloud Engineering Data Security Service Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security, Service, Data. So download instantly and tailor it with your information.
-
 Social Engineering Business Security In Powerpoint And Google Slides Cpb
Social Engineering Business Security In Powerpoint And Google Slides CpbPresenting Social Engineering Business Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Social Engineering Business Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 How An Ad Auction Works To Secure Top Spots Search Engine Marketing To Increase MKT SS V
How An Ad Auction Works To Secure Top Spots Search Engine Marketing To Increase MKT SS VThis slide showcases the working of an Ad auction. It includes steps such as google Das algorithm, bid, ad quality, ad rank and competitor analysis. It includes elements such as keywords to bid on and budget specification. Increase audience engagement and knowledge by dispensing information using How An Ad Auction Works To Secure Top Spots Search Engine Marketing To Increase MKT SS V. This template helps you present information on three stages. You can also present information on Identify Keywords To Bid, Specify Budget That using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How An Ad Auction Works To Secure Search Engine Marketing To Generate Qualified Traffic MKT SS
How An Ad Auction Works To Secure Search Engine Marketing To Generate Qualified Traffic MKT SSThis slide showcases the working of an Ad auction. It includes steps such as google Das algorithm, bid, ad quality, ad rank and competitor analysis. It includes elements such as keywords to bid on and budget specification. Introducing How An Ad Auction Works To Secure Search Engine Marketing To Generate Qualified Traffic MKT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Working, Auction, Secure, using this template. Grab it now to reap its full benefits.
-
 Social engineering icon of information security
Social engineering icon of information securityPresenting this set of slides with name - Social Engineering Icon Of Information Security. This is a three stage process. The stages in this process are Social Engineering, Social Network, Technology.
-
 Security engineering ppt powerpoint presentation gallery designs cpb
Security engineering ppt powerpoint presentation gallery designs cpbPresenting this set of slides with name - Security Engineering Ppt Powerpoint Presentation Gallery Designs Cpb. This is an editable five stages graphic that deals with topics like Security Engineering to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cluster checklist security process engine ppt icons graphics
Cluster checklist security process engine ppt icons graphicsRuns effortlessly with all compatible software. Downloads rapidly in matter of moments. Trouble free process to add company logo, name or trademark. No pixilation when slide is viewed on widescreen. Compatible with google slides. Mention titles and subtitles without feeling constrained. High resolution PPT slides. Convert to JPG and PDF formats easily. Useful for businesses, artists, NGO’s, students, teachers etc.
-
 Information security social engineering ppt powerpoint presentation summary styles cpb
Information security social engineering ppt powerpoint presentation summary styles cpbPresenting this set of slides with name Information Security Social Engineering Ppt Powerpoint Presentation Summary Styles Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Information Security Social Engineering to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security engineering services ppt powerpoint presentation layouts layout cpb
Security engineering services ppt powerpoint presentation layouts layout cpbPresenting this set of slides with name Security Engineering Services Ppt Powerpoint Presentation Layouts Layout Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Security Engineering Services to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security engineering analysis framework ppt powerpoint diagram cpb
Security engineering analysis framework ppt powerpoint diagram cpbPresenting this set of slides with name Security Engineering Analysis Framework Ppt Powerpoint Diagram Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Security Engineering Analysis Framework to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Network security engineering ppt powerpoint presentation layouts clipart cpb
Network security engineering ppt powerpoint presentation layouts clipart cpbPresenting this set of slides with name Network Security Engineering Ppt Powerpoint Presentation Layouts Clipart Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Network Security Engineering to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security testing software engineering ppt powerpoint presentation file graphics template cpb
Security testing software engineering ppt powerpoint presentation file graphics template cpbPresenting our Security Testing Software Engineering Ppt Powerpoint Presentation File Graphics Template Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Testing Software Engineering This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security engine cloud computing standard architecture patterns ppt presentation diagram
Security engine cloud computing standard architecture patterns ppt presentation diagramShowcase your expertise on cloud computing patterns by introducing this slide titled Security Engine Cloud Computing Standard Architecture Patterns Ppt Presentation Diagram. This PowerPoint template is compatible with both the standard and widescreen sizes. Give insights into the concepts such as Security Engine, Storage Device with our pre-designed PPT theme. Download this information technology PowerPoint template now.
-
 Security software engineer ppt powerpoint presentation portfolio file formats cpb
Security software engineer ppt powerpoint presentation portfolio file formats cpbPresenting our Security Software Engineer Ppt Powerpoint Presentation Portfolio File Formats Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Software Engineer This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 4 dimensions of infrastructure security infrastructure engineering facility management ppt inspiration
4 dimensions of infrastructure security infrastructure engineering facility management ppt inspirationPresent the topic in a bit more detail with this 4 Dimensions Of Infrastructure Security Infrastructure Engineering Facility Management Ppt Inspiration. Use it as a tool for discussion and navigation on Applications, Infrastructure, Datacenters. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Interdependence resiliency and security infrastructure engineering facility management ppt download
Interdependence resiliency and security infrastructure engineering facility management ppt downloadIncrease audience engagement and knowledge by dispensing information using Interdependence Resiliency And Security Infrastructure Engineering Facility Management Ppt Download. This template helps you present information on four stages. You can also present information on Interdependence, Resiliency And Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Methods And Mitigation Checklist To Secure Organizations From Social Engineering
Social Engineering Methods And Mitigation Checklist To Secure Organizations From Social EngineeringThis slide outlines the steps to be taken to protect the organization and its employees from social engineering attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Checklist To Secure Organizations From Social Engineering. Dispense information and present a thorough explanation of Social Engineering Attacks, Real Time Monitoring, Develop An Incident Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Site Reliability Engineering Icon
Secure Site Reliability Engineering IconIntroducing our premium set of slides with name Secure Site Reliability Engineering Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Secure Site Reliability, Engineering Icon. So download instantly and tailor it with your information.
-
 Cyber Security Training Module For Social Engineering Implementing Organizational Security Training
Cyber Security Training Module For Social Engineering Implementing Organizational Security TrainingThe slide showcases a cyber security training module that teaches about social engineering. It includes points such as topics covered, module, problems, trainer name, etc. Present the topic in a bit more detail with this Cyber Security Training Module For Social Engineering Implementing Organizational Security Training. Use it as a tool for discussion and navigation on Recognizing Common Scam Scenarios, Identifying Social Engineering Tactics, Training Module. This template is free to edit as deemed fit for your organization. Therefore download it now.



