Powerpoint Templates and Google slides for Security Effectiveness
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD
Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CDWhile your presentation may contain top-notch content, if it lacks visual appeal, you are not fully engaging your audience. Introducing our Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, it is downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck.
-
 Effective information security risk management process powerpoint presentation slides
Effective information security risk management process powerpoint presentation slidesDeliver an informational PPT on various topics by using this Effective Information Security Risk Management Process Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with fifty seven slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 Information Security Program For Effective Cybersecurity Risk Management Powerpoint Presentation Slides
Information Security Program For Effective Cybersecurity Risk Management Powerpoint Presentation SlidesThis complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fifty six slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
-
 Effective security monitoring plan to eliminate cyber threats and data breaches complete deck
Effective security monitoring plan to eliminate cyber threats and data breaches complete deckEnthrall your audience with this Effective Security Monitoring Plan To Eliminate Cyber Threats And Data Breaches Complete Deck. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising fourty four slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Secops V2 Effective Implementation Impact On Security Breaches
Secops V2 Effective Implementation Impact On Security BreachesThis slide outlines the successful implementation impact of SecOps on organizational security breaches. The purpose of this slide is to highlight the number of reduced security breaches inside a company after implementing SecOps. Security breaches include phishing, network intrusion, and so on. Present the topic in a bit more detail with this Secops V2 Effective Implementation Impact On Security Breaches. Use it as a tool for discussion and navigation on Network Intrusion, Security Breaches, Sensitive Data Leakage, Configuration Information Disclosure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
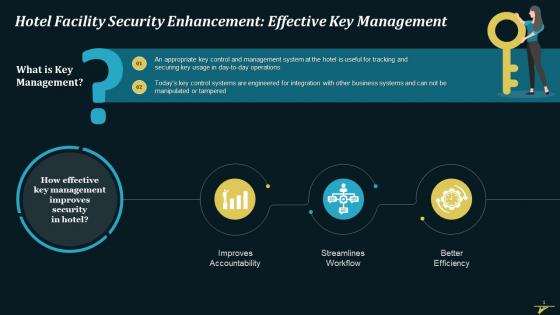 Enhanced Hotel Facility Security With Effective Key Management Training Ppt
Enhanced Hotel Facility Security With Effective Key Management Training PptPresenting Enhanced Hotel Facility Security with Effective Key Management. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizablealter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Effective Ways To Monitor Transaction Patterns Implementing E Commerce Security Measures
Effective Ways To Monitor Transaction Patterns Implementing E Commerce Security MeasuresThe slide highlights the ways to track and analyze transaction patterns and log in attempts. It provide details about risk scoring, real time monitoring, account monitoring and behavioral analytics.Present the topic in a bit more detail with this Effective Ways To Monitor Transaction Patterns Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Account Monitoring, Behavioral Analytics, Real Time Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major IOT Security Threats And Its Negative Effects
Major IOT Security Threats And Its Negative EffectsThis slide showcases major security threats that disrupt the operations. Threats covered are buffer overflow, SQL injection, worm, botnet, ransomware, password, phishing, crypto jacking, etc. Presenting our well structured Major IOT Security Threats And Its Negative Effects. The topics discussed in this slide are Negative Effective, Lack Visibility, Poor Testing. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Implement Effective Marketing Strategies For Successful Launch Security Token Offerings BCT SS
Implement Effective Marketing Strategies For Successful Launch Security Token Offerings BCT SSThe following slide depicts various marketing techniques to ensure successful launch of security token offerings STO project. It includes elements such as public relations, social media, content, affiliate, email marketing, paid ads, etc. Introducing Implement Effective Marketing Strategies For Successful Launch Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Marketing Strategies, Potential Impact, Project Awareness, using this template. Grab it now to reap its full benefits.
-
 Manage Investor Relations With Effective Communication Security Token Offerings BCT SS
Manage Investor Relations With Effective Communication Security Token Offerings BCT SSThe following slide illustrates some ways to maintain effective and healthy relations with investors. It includes elements such as transparent communication, building investor relations team, conducting feedbacks and surveys, ensuring investor integration, etc. Increase audience engagement and knowledge by dispensing information using Manage Investor Relations With Effective Communication Security Token Offerings BCT SS. This template helps you present information on four stages. You can also present information on Transparent Communication, Investor Relations Team, Feedback And Surveys using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Reach Out To Investors For Effective Communication Security Token Offerings BCT SS
Reach Out To Investors For Effective Communication Security Token Offerings BCT SSThe following slide showcases various methods through which security token offerings STO project managers can reach out to investors. It includes elements such as online platforms, social media, networking, direct outreach, etc. Increase audience engagement and knowledge by dispensing information using Reach Out To Investors For Effective Communication Security Token Offerings BCT SS. This template helps you present information on four stages. You can also present information on Online Platforms, Social Media, Networking, Direct Outreach using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Effective GCP Identity And Security Services
Effective GCP Identity And Security ServicesThis slide exhibits the google cloud platform GCP security services which ensure and maintain the security of the infrastructure. It includes security tools such as cloud resource manager, cloud IAM, cloud security scanner, and stack driver logging. Introducing our premium set of slides with Effective GCP Identity And Security Services. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Manager, Security, Scanner. So download instantly and tailor it with your information.
-
 Effective Ways Of Improving Network Security In Organization
Effective Ways Of Improving Network Security In OrganizationThis slide showcases various ways of improving network security. The main purpose of this template is maintaining data safe place and save data from getting hacked. This includes hiring security consultant, encrypting data, monitoring network activity etc. Introducing our premium set of slides with Effective Ways Of Improving Network Security In Organization. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Hiring Security Consultant, Encrypting Data. So download instantly and tailor it with your information.
-
 Best Practices For Effective Endpoint Security Delivering ICT Services For Enhanced Business Strategy SS V
Best Practices For Effective Endpoint Security Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business-owned devices, and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Best Practices For Effective Endpoint Security Delivering ICT Services For Enhanced Business Strategy SS V. This template helps you present information on three stages. You can also present information on Educate Users, Find And Track Devices, Operating System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network Security Model To Effective Delivering ICT Services For Enhanced Business Strategy SS V
Network Security Model To Effective Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Introducing Network Security Model To Effective Delivering ICT Services For Enhanced Business Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threats, Security Breaches, Virtual Private, using this template. Grab it now to reap its full benefits.
-
 Implementation Of Information Best Practices For Effective Endpoint Security Strategy SS V
Implementation Of Information Best Practices For Effective Endpoint Security Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users finding and tracking business owned devices and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Implementation Of Information Best Practices For Effective Endpoint Security Strategy SS V. This template helps you present information on three stages. You can also present information on Educate Users, Installation Maintenance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementation Of Information Data Encryption Model For Effective Information Security Strategy SS V
Implementation Of Information Data Encryption Model For Effective Information Security Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Present the topic in a bit more detail with this Implementation Of Information Data Encryption Model For Effective Information Security Strategy SS V. Use it as a tool for discussion and navigation on Backup Repository, Encrypted Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Network Security Model To Effective Communication Strategy SS V
Implementation Of Information Network Security Model To Effective Communication Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Present the topic in a bit more detail with this Implementation Of Information Network Security Model To Effective Communication Strategy SS V. Use it as a tool for discussion and navigation on Message Transformation, Information Channel. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies For Creating Effective Security Awareness Communication Plan
Strategies For Creating Effective Security Awareness Communication PlanThe slide showcases strategies that assist in effectively creating security awareness and communication plan in an organization. It contains strategies such as impact of security incidents, responsibilities, IT security help mechanism, etc. Introducing our Strategies For Creating Effective Security Awareness Communication Plan set of slides. The topics discussed in these slides are Strategies, Description, Incidents. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Roadmap For Establishing Effective Business Security Management Plan
Roadmap For Establishing Effective Business Security Management PlanThis slide showcases the roadmap for executing an effective business security management plan. This slide aims to help the business ensure sufficient security measures are put in place to avoid cyber attacks and data thefts. It includes steps such as risk assessment, framework development, plan reviews, etc.Presenting our set of slides with Roadmap For Establishing Effective Business Security Management Plan. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Conduct Security Assessment, Conduct Technology Evaluation, Implement Security Plan.
-
 Components Of Effective Enterprise Security System
Components Of Effective Enterprise Security SystemThis slide represents enterprise security system components for effectiveness. This further includes components such as security cameras, video monitoring, smartphone alerts, manage employee access. Presenting our set of slides with Components Of Effective Enterprise Security System. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Cameras, Video Monitoring, Smartphone Alerts.
-
 Empowering Business With Effective Security System Icon
Empowering Business With Effective Security System IconIntroducing our premium set of slides with Empowering Business With Effective Security System Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Empowering Business With Effective, Security System Icon. So download instantly and tailor it with your information.
-
 Strategies For Effective Enterprise Cyber Security Action Plan
Strategies For Effective Enterprise Cyber Security Action PlanThis slide showcases strategies that involve in creating an effective enterprise cyber security action plan for better incident responses. It contains points such as assessment, protection, detect and respond to incidents, security and data protection, etc. Presenting our set of slides with Strategies For Effective Enterprise Cyber Security Action Plan. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Protection, Assessment, Respond.
-
 Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS V
Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business-owned devices, and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS V This template helps you present information on Three stages. You can also present information on Educate Users, Find And Track Devices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V
Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Present the topic in a bit more detail with this Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V Use it as a tool for discussion and navigation on Employee Headcount, Average Employee Age, Gender Diversity Ratio This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Network Security Model To Effective Communication Strategy SS V
Strategic Plan To Implement Network Security Model To Effective Communication Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Deliver an outstanding presentation on the topic using this Strategic Plan To Implement Network Security Model To Effective Communication Strategy SS V Dispense information and present a thorough explanation of Communication, Data Management, Marketing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Effective Security Patch Management Process For Manufacturing Business
Effective Security Patch Management Process For Manufacturing BusinessThis slide showcases process of security patch management for manufacturing business. This template aims to help businesses integrate key components into a comprehensive security patch management process to maintain the stability of their operations. It includes phases such as vulnerability assessment, risk assessment, etc.Introducing our premium set of slides with Effective Security Patch Management Process For Manufacturing Business. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Vulnerability Assessment, Risk Assessment, Change Management. So download instantly and tailor it with your information.
-
 Network Security Model To Effective Comprehensive Guide For Deployment Strategy SS V
Network Security Model To Effective Comprehensive Guide For Deployment Strategy SS VThis slide represents the network security model for effective communication in the organization It covers information regarding security threats, firewalls, virtual private networks, etc Present the topic in a bit more detail with this Network Security Model To Effective Comprehensive Guide For Deployment Strategy SS V Use it as a tool for discussion and navigation on Protection Computer, Components Detect, Information Channel This template is free to edit as deemed fit for your organization Therefore download it now
-
 Establish Effective Internet Security Protocols In Network Layer
Establish Effective Internet Security Protocols In Network LayerThis slide exhibits network layer security architecture for providing virtual private network between two locations. It includes protocols such as encapsulating security payload, authentication header and internet key exchange. Presenting our set of slides with Establish Effective Internet Security Protocols In Network Layer. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication Header, Authentication Methods, Encapsulating Security Payload.
-
 Effective Steps Used To Manage Network Security
Effective Steps Used To Manage Network SecurityThis slide showcases the effective steps used to manage network security which helps an organization to mitigate risk and improve decision making process. It include details such as stay organized, create strong password policy, install endpoint and antivirus, etc. Introducing our premium set of slides with Effective Steps Used To Manage Network Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Stay Organized, Create Strong Password Policy, Install Endpoint Antivirus. So download instantly and tailor it with your information.
-
 Components Of Virtual Infrastructure For Effective Data Management And Security
Components Of Virtual Infrastructure For Effective Data Management And SecurityThis slide represents key components of virtual infrastructure that help businesses with data security and disaster management. It includes various components such as virtualized computing, virtualized storage, management solutions, and virtualized security. Introducing our premium set of slides with Components Of Virtual Infrastructure For Effective Data Management And Security. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Virtualized Compute, Virtualized Networking Security, Virtualized Storage. So download instantly and tailor it with your information.
-
 Firewall Network Security Firewall Features To Effectively Prevent Cyber Attacks
Firewall Network Security Firewall Features To Effectively Prevent Cyber AttacksThis slide outlines the primary characteristics a firewall should have to prevent cyber attacks on a network. The purpose of this slide is to showcase the different features that a firewall should possess, including scalable performance, unified security management, threat prevention, and so on. Introducing Firewall Network Security Firewall Features To Effectively Prevent Cyber Attacks to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on URL Categories By Traffic, Traffic Source IP, Traffic Desintation IP using this template. Grab it now to reap its full benefits.
-
 Implementing Effective Software Testing Existing IT Security Infrastructure Constituents
Implementing Effective Software Testing Existing IT Security Infrastructure ConstituentsThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. These constituents are regulatory and compliance, budget, complex integration, and so on. Present the topic in a bit more detail with this Implementing Effective Software Testing Existing IT Security Infrastructure Constituents. Use it as a tool for discussion and navigation on Complex Integration, Strict Compliance Requirements, Functional Disrupt, IT Security Infrastructure Constituents. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Conduct Effective Web Security
Checklist To Conduct Effective Web SecurityThis slide showcases actions performed while conducting web security in an organization which include actions, person responsible, status, etc. Presenting our well structured Checklist To Conduct Effective Web Security. The topics discussed in this slide are Authentication And Authorization, Session Management, Connectivity. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Roadmap For Implementing Effective Web Security
Roadmap For Implementing Effective Web SecurityThis slide outlines the steps that an organization should take while conducting web security such as education, infrastructure security, etc. Presenting our set of slides with name Roadmap For Implementing Effective Web Security. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitoring, Application Security, Incident Response, Assessment And Planning.
-
 Effective Components Of Csirt Cyber Security
Effective Components Of Csirt Cyber SecurityThis slide highlights necessary components of CSIRT cyber security. The main purpose of this template is to showcase mitigation of potential threats. This includes regular security assessment, collaboration, post incident review, etc. Presenting our set of slides with Effective Components Of Csirt Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Assessment, External Entities, Incident Review.
-
 Best Practices For Effective Server Security Management
Best Practices For Effective Server Security ManagementFollowing slide highlights server security management best practices, also including elements such as server management, physical security, update software, etc. Introducing our Best Practices For Effective Server Security Management set of slides. The topics discussed in these slides are Server Management, Physical Security, Update Software. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Effective Steps To Construct Security Technology Stack
Effective Steps To Construct Security Technology StackThis slide showcases the essential and productive guidelines to develop security technology stack which helps an organization to reduce complexity within the system. It include details such as stack scheduling, creation, testing and improvements. Presenting our set of slides with name Effective Steps To Construct Security Technology Stack This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Stack Scheduling, Stack Creation, Stack Testing
-
 Steps For Effective Triage Cyber Security Process
Steps For Effective Triage Cyber Security ProcessThis slide represents steps for effective triage process which assists security teams to focus on critical threats and allocate resources effectively., It includes steps for effective triage cyber security process such as identify, map and eradicate Introducing our premium set of slides with name Steps For Effective Triage Cyber Security Process Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify Artifacts, Draw Event Timelines, System From Backup. So download instantly and tailor it with your information.
-
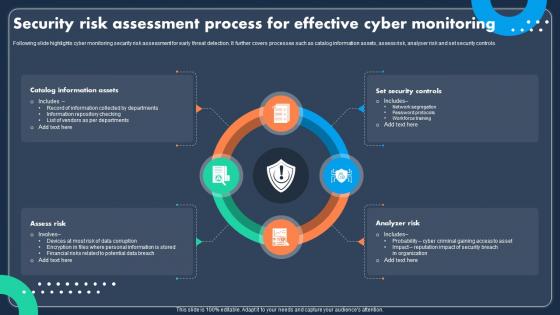 Security Risk Assessment Process For Effective Cyber Monitoring
Security Risk Assessment Process For Effective Cyber MonitoringFollowing slide highlights cyber monitoring security risk assessment for early threat detection. It further covers processes such as catalog information assets, assess risk, analyser risk and set security controls. Introducing our premium set of slides with Security Risk Assessment Process For Effective Cyber Monitoring Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Assets, Security Controls, Analyzer Risk. So download instantly and tailor it with your information.
-
 Implement Effective Marketing Beginners Guide To Successfully Launch Security Token BCT SS V
Implement Effective Marketing Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide depicts various marketing techniques to ensure successful launch of security token offerings STO project. It includes elements such as public relations, social media, content, affiliate, email marketing, paid ads, etc. Deliver an outstanding presentation on the topic using this Implement Effective Marketing Beginners Guide To Successfully Launch Security Token BCT SS V. Dispense information and present a thorough explanation of Implement Effective Marketing, Strategies, Successful Launch using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Prerequisites For Establishing Effective Cyber Security Tabletop Exercise
Prerequisites For Establishing Effective Cyber Security Tabletop ExerciseThis slide shows factors for creating an effective cyber tabletop exercise. The purpose of this slide is to provide support for development by ensuring enhanced experience of running tabletop exercises. It covers factors such as clear objectives, stakeholders involvement, realism and improvements. Presenting our set of slides with Prerequisites For Establishing Effective Cyber Security Tabletop Exercise. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Clear Objectives, Stakeholders Involvement, Realism And Relevance.
-
 Framework To Manage Data Security Center Effectively
Framework To Manage Data Security Center EffectivelyThis slide showcases the framework that assist companies to manage and monitor their data center security effectively against threats. It includes various elements such as security operations, application security, security architecture, etc. Presenting our well structured Framework To Manage Data Security Center Effectively. The topics discussed in this slide are Application Platform, Access Management, Application Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Requirement For Effective Cyber Security Policy
Requirement For Effective Cyber Security PolicyThis slide covers the imperative reasons for the need of cybersecurity policies. The purpose of this template is to articulate the significance of policies in ensuring legal compliance, data protection, effective risk management, employee training, and incident response. Presenting our set of slides with Requirement For Effective Cyber Security Policy This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Legal Compliance, Data Protection, Risk Management
-
 Strategic Approach For Effective Data Migration Case Study Data Security And Compliance In Cloud Migration
Strategic Approach For Effective Data Migration Case Study Data Security And Compliance In Cloud MigrationThe following slide showcases a case study on data security and compliance in cloud migration. It includes various elements such as company details, challenges, and solutions. Increase audience engagement and knowledge by dispensing information using Strategic Approach For Effective Data Migration Case Study Data Security And Compliance In Cloud Migration. This template helps you present information on three stages. You can also present information on Data Security, Cloud Migration, Security And Confidentiality, Customer Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Approach For Effective Data Migration Checklist For Ensuring Secure Data Migration
Strategic Approach For Effective Data Migration Checklist For Ensuring Secure Data MigrationThe purpose of this slide is to showcase a checklist for ensuring safe migration of data from one source to another. It includes various tactics such as data protection impact assessment, data security and encryption, data retention and deletion, etc. Deliver an outstanding presentation on the topic using this Strategic Approach For Effective Data Migration Checklist For Ensuring Secure Data Migration. Dispense information and present a thorough explanation of Legal Limitations, Compliance Requirements, Legacy Database Schema, Intrusion Detection Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Approach For Effective Data Migration Security And Privacy Challenges Faced By Companies
Strategic Approach For Effective Data Migration Security And Privacy Challenges Faced By CompaniesThe purpose of this slide is to assess security and privacy challenges, and their impact on data migration process. It includes challenges and need for ensuring data privacy. Introducing Strategic Approach For Effective Data Migration Security And Privacy Challenges Faced By Companies to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Data Security And Privacy Challenges, Loss Of Customers, Sensitive Data, Poses Security And Privacy Concerns, using this template. Grab it now to reap its full benefits.
-
 Strategic Approach For Effective Data Migration Steps For A Secure Data Migration Process
Strategic Approach For Effective Data Migration Steps For A Secure Data Migration ProcessThe purpose of this slide is to represent the process of secure and safe data migration from one platform to another. It includes various stages such as assessing data sources, choosing method, designing architecture, etc. Introducing Strategic Approach For Effective Data Migration Steps For A Secure Data Migration Process to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Design Architecture, Validate And Verify Results, Assess Data Sources, Data Migration Process, using this template. Grab it now to reap its full benefits.
-
 Implementing Effective Tokenization Existing IT Security Infrastructure Threats
Implementing Effective Tokenization Existing IT Security Infrastructure ThreatsThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. Present the topic in a bit more detail with this Implementing Effective Tokenization Existing IT Security Infrastructure Threats. Use it as a tool for discussion and navigation on Compliance Challenges, Resource Intensiveness, Faced Security Vulnerabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Effective Tokenization Steps To Implement Security Tokenization Strategy
Implementing Effective Tokenization Steps To Implement Security Tokenization StrategyThis slide represents the different phases of deploying security tokenization which include identifying sensitive data, implementing tokenization, etc. Increase audience engagement and knowledge by dispensing information using Implementing Effective Tokenization Steps To Implement Security Tokenization Strategy. This template helps you present information on seven stages. You can also present information on Implement Security Tokenization, Identify Sensitive Data, Secure Storage Of Tokens using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization Working Process For Data Security Implementing Effective Tokenization
Tokenization Working Process For Data Security Implementing Effective TokenizationThis slide represents the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Deliver an outstanding presentation on the topic using this Tokenization Working Process For Data Security Implementing Effective Tokenization. Dispense information and present a thorough explanation of Tokenization Working Process, Data Security, Mobile Payment Application, Generating Tokens using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Implement Effective Application Security
Checklist To Implement Effective Application SecurityThis slide showcases the actions performed while deploying application security, person responsible, status and comments for the same. Deliver an outstanding presentation on the topic using this Checklist To Implement Effective Application Security. Dispense information and present a thorough explanation of Assessment And Planning, Education And Training, Patch Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identity And Access Management Function As Security Tool IAM Process For Effective Access
Identity And Access Management Function As Security Tool IAM Process For Effective AccessThis slide showcases function of Identity and Access Management as a security tool. The purpose of this slide is to explain the function of IAM as an essential security tool these include context awareness, identity and access governance, and so on. Present the topic in a bit more detail with this Identity And Access Management Function As Security Tool IAM Process For Effective Access. Use it as a tool for discussion and navigation on Context Awareness, Identity And Access Governance, Management Function. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Security Issue IAM Process For Effective Access
Identity And Access Management Security Issue IAM Process For Effective AccessThis slide discusses the security issue of the Identity and Access Management process. The purpose of this slide is to explain the security challenges of IAM these include impractical security policies, inconsistent security policies, slow de-provision, etc. Deliver an outstanding presentation on the topic using this Identity And Access Management Security Issue IAM Process For Effective Access. Dispense information and present a thorough explanation of Impractical Security Policies, Inconsistent Security Policies, Inconsistent Identity Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
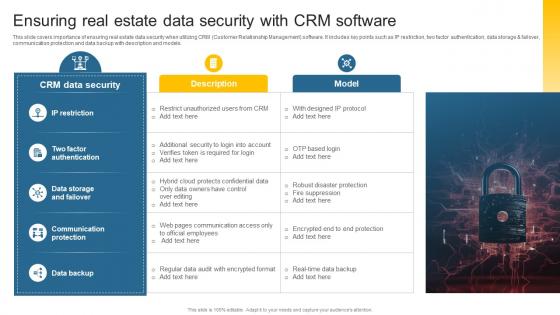 Ensuring Real Estate Data Security With CRM Leveraging Effective CRM Tool In Real Estate Company
Ensuring Real Estate Data Security With CRM Leveraging Effective CRM Tool In Real Estate CompanyThis slide covers importance of ensuring real estate data security when utilizing CRM Customer Relationship Management software. It includes key points such as IP restriction, two factor authentication, data storage and failover, communication protection and data backup with description and models. Introducing Ensuring Real Estate Data Security With CRM Leveraging Effective CRM Tool In Real Estate Company to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Data Storage And Failover, Communication Protection, Data Backup, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Checklist For Effective Application Security Implementation
Application Security Implementation Plan Checklist For Effective Application Security ImplementationThis slide showcases the actions performed while deploying application security, person responsible, status and comments for the same. Present the topic in a bit more detail with this Application Security Implementation Plan Checklist For Effective Application Security Implementation. Use it as a tool for discussion and navigation on Assessment And Planning, Education And Training, Incident Response Planning. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Implementing Effective Security Testing In Organization
Application Security Implementation Plan Implementing Effective Security Testing In OrganizationThis slide showcases the deployment process of security testing parallel to Software Development Testing Lifecycle SDLC stages. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Implementing Effective Security Testing In Organization. This template helps you present information on seven stages. You can also present information on System Testing, Implementation System Testing, Integration Testing, Requirement using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Process Phases For Effective Authentication Implementation
Application Security Implementation Plan Process Phases For Effective Authentication ImplementationThis slide showcases the steps for deploying effective authentication which include defining requirements, selecting authentication method, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Process Phases For Effective Authentication Implementation. This template helps you present information on seven stages. You can also present information on Implement Login Mechanism, Choose Authentication Method, Secure Storage Of Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Steps For Effective Encryption Method Deployment
Application Security Implementation Plan Steps For Effective Encryption Method DeploymentThis slide highlights the steps for deploying effective encryption which include selecting appropriate algorithm, choosing correct key size, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Steps For Effective Encryption Method Deployment. This template helps you present information on six stages. You can also present information on Select Appropriate Algorithm, Select Appropriate Program, Maintain Key Security, Encryption Method Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Working Process Of Effective Logging Implementation
Application Security Implementation Plan Working Process Of Effective Logging ImplementationThis slide outlines the steps for deploying effective logging which include assess requirements, select logging tool, defining logging standards, etc. Introducing Application Security Implementation Plan Working Process Of Effective Logging Implementation to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Ensure Security, Centralize Log Management, Define Logging Standards, Select Logging Tools, using this template. Grab it now to reap its full benefits.




