Powerpoint Templates and Google slides for Security Effectiveness
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Incidents effective information security risk management process
Incidents effective information security risk management processThis slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level.Present the topic in a bit more detail with this Incidents Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Preform Primary Work Functions, Inconvenient, Medium Multiple. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
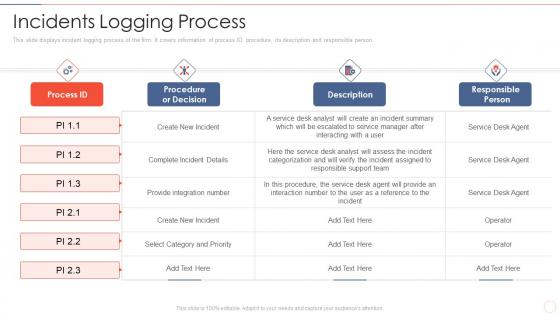 Incidents logging process effective information security risk management process
Incidents logging process effective information security risk management processThis slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person.Deliver an outstanding presentation on the topic using this Incidents Logging Process Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Select Category And Priority, Procedure, The Service, Responsible Person using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information security decision effective information security risk management process
Information security decision effective information security risk management processIncrease audience engagement and knowledge by dispensing information using Information Security Decision Effective Information Security Risk Management Process. This template helps you present information on eight stages. You can also present information on Risk Management, Implementation Responsiveness, Prioritization Weighting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information security effective information security risk management process
Information security effective information security risk management processMentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm.Present the topic in a bit more detail with this Information Security Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Asset And Consequences, Overheating In Server Room, Asset And Consequences. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introducing process workflow effective information security risk management process
Introducing process workflow effective information security risk management processFollowing slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results Deliver an outstanding presentation on the topic using this Introducing Process Workflow Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Threat Categorization, System Characterization, Assigned Remediation Measures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mitigation plan for threat effective information security risk management process
Mitigation plan for threat effective information security risk management processMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver an outstanding presentation on the topic using this Mitigation Plan For Threat Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Resources Required, Expected Resolution Time, Communication Mode using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Multitiered risk effective information security risk management process
Multitiered risk effective information security risk management processIntroducing Multitiered Risk Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Orgnization, Mission Or Business Processes, Information Systems, using this template. Grab it now to reap its full benefits.
-
 Present security effective information security risk management process
Present security effective information security risk management processFollowing slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings.Present the topic in a bit more detail with this Present Security Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Assessing Information, Incident Occurrence Identification, Vulnerability Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk reporting and likelihood effective information security risk management process
Risk reporting and likelihood effective information security risk management processMentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an outstanding presentation on the topic using this Risk Reporting And Likelihood Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Attack Scenario, Risk Encountered, Equipment Failure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Roles and responsibilities effective information security risk management process
Roles and responsibilities effective information security risk management processFollowing slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development.Increase audience engagement and knowledge by dispensing information using Roles And Responsibilities Effective Information Security Risk Management Process. This template helps you present information on one stage. You can also present information on Information Management Manager, Risk Management Officer, Development And Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security risk management process incidents prioritization matrix effective information
Security risk management process incidents prioritization matrix effective informationThis slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level Present the topic in a bit more detail with this Security Risk Management Process Incidents Prioritization Matrix Effective Information. Use it as a tool for discussion and navigation on Enterprise Or Multiple Segments, Single Segment Or Entire Site, Event Underway. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
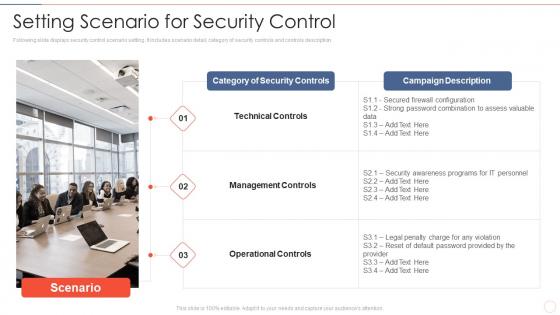 Setting scenario security control effective information security risk management process
Setting scenario security control effective information security risk management processFollowing slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Introducing Setting Scenario Security Control Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Controls, Operational Controls, Technical Controls, using this template. Grab it now to reap its full benefits.
-
 System categorization worksheet effective information security risk management process
System categorization worksheet effective information security risk management processThis slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information.Present the topic in a bit more detail with this System Categorization Worksheet Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on System Accessibility, Accessible Within Organization Boundary, Valuable Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 System disposal checklist effective information security risk management process
System disposal checklist effective information security risk management processMentioned slide shows system disposal checklist. It covers information such as system requirement, its compliance and remarks.Deliver an outstanding presentation on the topic using this System Disposal Checklist Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Stored Information Is Removed, Hardcopy Information, Requirement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 System management checklist effective information security risk management process
System management checklist effective information security risk management processFollowing slide displays system management checklist. It includes system management activities and frequency of performing them.Present the topic in a bit more detail with this System Management Checklist Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on System Monitoring, Security Patches, Virus Scanning . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table of contents for effective information security risk management process
Table of contents for effective information security risk management processDeliver an outstanding presentation on the topic using this Table Of Contents For Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Present Scenario, Training And Budget, Dashboards using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat assessment effective information security risk management process
Threat assessment effective information security risk management processFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Threat Assessment Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Affected Asset, Potential Vulnerability, Vulnerability Ranking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Defining risk level effective information security
Defining risk level effective information securityFollowing slide defines the incident risk level. It includes details about risk level, risk score and its description. Present the topic in a bit more detail with this Defining Risk Level Effective Information Security. Use it as a tool for discussion and navigation on Risk Level, Score, Extreme, High, Medium, Low. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security asset criticality of identified system components
Effective information security asset criticality of identified system componentsFollowing slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost. Deliver an outstanding presentation on the topic using this Effective Information Security Asset Criticality Of Identified System Components. Dispense information and present a thorough explanation of Host Computers, Impact Rating, Business, Criticality Rating using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Effective information security budget for information security management
Effective information security budget for information security managementMentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost. Present the topic in a bit more detail with this Effective Information Security Budget For Information Security Management. Use it as a tool for discussion and navigation on Incident Management, Risk Management, Asset Management . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security defining categories of information security threats
Effective information security defining categories of information security threatsThis slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures. Increase audience engagement and knowledge by dispensing information using Effective Information Security Defining Categories Of Information Security Threats. This template helps you present information on four stages. You can also present information on Human Error, Natural Disaster, Environmental Control Failures, Deliberate Software Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Effective information security defining vulnerability rating
Effective information security defining vulnerability ratingFollowing slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Present the topic in a bit more detail with this Effective Information Security Defining Vulnerability Rating. Use it as a tool for discussion and navigation on Vulnerability Ranking, Organization, Occurrence Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security employee training schedule
Effective information security employee training scheduleThis slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Deliver an outstanding presentation on the topic using this Effective Information Security Employee Training Schedule. Dispense information and present a thorough explanation of Training Mode, Course Type, Training Duration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Effective information security impact assessment matrix ppt slides outline
Effective information security impact assessment matrix ppt slides outlinePresent the topic in a bit more detail with this Effective Information Security Impact Assessment Matrix Ppt Slides Outline. Use it as a tool for discussion and navigation on Impact Area, Impact High, Impact Medium, Impact Low. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
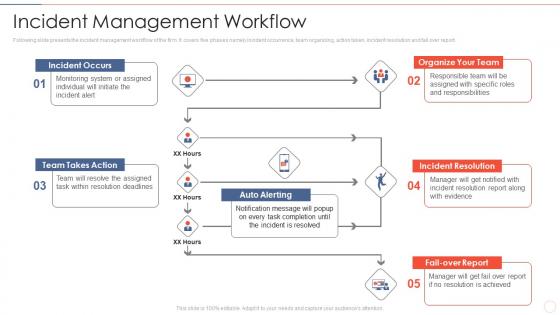 Effective information security incident management workflow
Effective information security incident management workflowFollowing slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Present the topic in a bit more detail with this Effective Information Security Incident Management Workflow. Use it as a tool for discussion and navigation on Incident Occurs, Team Takes Action, Organize Team, Auto Alerting, Incident Resolution, Fail Over Report. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security incidents logging process
Effective information security incidents logging processThis slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person. Present the topic in a bit more detail with this Effective Information Security Incidents Logging Process. Use it as a tool for discussion and navigation on Complete Incident Details, Select Category And Priority, Provide Integration Number. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security information security decision framework prism workflow
Effective information security information security decision framework prism workflowDeliver an outstanding presentation on the topic using this Effective Information Security Information Security Decision Framework Prism Workflow. Dispense information and present a thorough explanation of Key Risk Areas Vectors, Risk Factors, Prioritization Weighting using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Effective information security information security risk assessment worksheet
Effective information security information security risk assessment worksheetThis slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Present the topic in a bit more detail with this Effective Information Security Information Security Risk Assessment Worksheet. Use it as a tool for discussion and navigation on Facilities And Equipment, Software Application, At Personnel Level, Risk. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
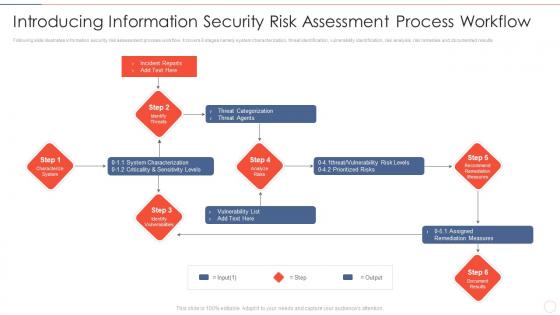 Effective information security introducing information security risk assessment process
Effective information security introducing information security risk assessment processFollowing slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results Increase audience engagement and knowledge by dispensing information using Effective Information Security Introducing Information Security Risk Assessment Process. This template helps you present information on six stages. You can also present information on Incident Reports, Threat Categorization, Vulnerability List, Assigned Remediation Measures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Effective information security mitigation plan for resolving encountered threat
Effective information security mitigation plan for resolving encountered threatMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Present the topic in a bit more detail with this Effective Information Security Mitigation Plan For Resolving Encountered Threat. Use it as a tool for discussion and navigation on Security Breach, System Failure, Risk Level, Mitigation Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security multitiered risk management framework diagram
Effective information security multitiered risk management framework diagramIncrease audience engagement and knowledge by dispensing information using Effective Information Security Multitiered Risk Management Framework Diagram. This template helps you present information on three stages. You can also present information on Strategic Risk, Orgnization, Mission, Business Processes, Information Systems using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Effective information security present security management capabilities of the firm
Effective information security present security management capabilities of the firmFollowing slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Present the topic in a bit more detail with this Effective Information Security Present Security Management Capabilities Of The Firm. Use it as a tool for discussion and navigation on Core Value, Key Enablers, Required Standard Rating, Actual Standard Rating. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security risk reporting and likelihood ppt slides layout
Effective information security risk reporting and likelihood ppt slides layoutMentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an outstanding presentation on the topic using this Effective Information Security Risk Reporting And Likelihood Ppt Slides Layout. Dispense information and present a thorough explanation of Risk Encountered, Frequency, Attack Scenario, Affected Asset using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Budget for effective threat managing critical threat vulnerabilities and security threats
Budget for effective threat managing critical threat vulnerabilities and security threatsFirm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an outstanding presentation on the topic using this Budget For Effective Threat Managing Critical Threat Vulnerabilities And Security Threats. Dispense information and present a thorough explanation of Incident Management, Risk Management, Client Onboarding Process, Document Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact analysis for effective managing critical threat vulnerabilities and security threats
Impact analysis for effective managing critical threat vulnerabilities and security threatsThis slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Introducing Impact Analysis For Effective Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Security Requirement, Focus Areas, using this template. Grab it now to reap its full benefits.
-
 Budget for effective threat management at workplace corporate security management
Budget for effective threat management at workplace corporate security managementFirm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Present the topic in a bit more detail with this Budget For Effective Threat Management At Workplace Corporate Security Management. Use it as a tool for discussion and navigation on Incident Management, Risk Management, Client Onboarding Process, Information Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact analysis for effective threat management in corporate security management
Impact analysis for effective threat management in corporate security managementThis slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Present the topic in a bit more detail with this Impact Analysis For Effective Threat Management In Corporate Security Management. Use it as a tool for discussion and navigation on Impact Analysis For Effective Threat Management In Securing Workplace. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cios Cost Optimization Playbook Role Of Management Effective Information Security Governance
Cios Cost Optimization Playbook Role Of Management Effective Information Security GovernanceThis slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an outstanding presentation on the topic using this Cios Cost Optimization Playbook Role Of Management Effective Information Security Governance. Dispense information and present a thorough explanation of Information, Security, Governance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Program Effective Cybersecurity Risk Management Table Of Contents
Security Program Effective Cybersecurity Risk Management Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Security Program Effective Cybersecurity Risk Management Table Of Contents. This template helps you present information on seven stages. You can also present information on Risk Governance, Enterprise Risk Ecosystem, Program Effectiveness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide Information Security Program For Effective Cybersecurity Risk Management
Icons Slide Information Security Program For Effective Cybersecurity Risk ManagementIntroducing our well researched set of slides titled Icons Slide Information Security Program For Effective Cybersecurity Risk Management. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Agenda Security Program For Effective Cybersecurity Risk Management
Agenda Security Program For Effective Cybersecurity Risk ManagementIntroducing Agenda Security Program For Effective Cybersecurity Risk Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Digitalization, Cybersecurity, Business, using this template. Grab it now to reap its full benefits.
-
 Information Security Program Cybersecurity Checklist Effectively Managing Asset Security
Information Security Program Cybersecurity Checklist Effectively Managing Asset SecurityFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Present the topic in a bit more detail with this Information Security Program Cybersecurity Checklist Effectively Managing Asset Security. Use it as a tool for discussion and navigation on Checklist For Effectively Managing Asset Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Responsibility Matrix To Ensure Effective Risk Management
Information Security Program Responsibility Matrix To Ensure Effective Risk ManagementThis slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Present the topic in a bit more detail with this Information Security Program Responsibility Matrix To Ensure Effective Risk Management. Use it as a tool for discussion and navigation on Responsibility, Management, Accountable. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Information Security Program For Effective Cybersecurity Risk Management
Table Of Contents Information Security Program For Effective Cybersecurity Risk ManagementIncrease audience engagement and knowledge by dispensing information using Table Of Contents Information Security Program For Effective Cybersecurity Risk Management. This template helps you present information on eight stages. You can also present information on Requirements, Technologies, Gap Identification using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Checklist For Effectively Managing Asset Security Risk Based Methodology To Cyber
Checklist For Effectively Managing Asset Security Risk Based Methodology To CyberFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them.Increase audience engagement and knowledge by dispensing information using Checklist For Effectively Managing Asset Security Risk Based Methodology To Cyber This template helps you present information on one stage. You can also present information on System Monitoring, Data Backup, Security Patches using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Checklist For Effectively Managing Asset Security Introducing A Risk Based Approach
Checklist For Effectively Managing Asset Security Introducing A Risk Based ApproachFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them.Introducing Checklist For Effectively Managing Asset Security Introducing A Risk Based Approach to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on System Monitoring, Virus Scanning, System Monitoring using this template. Grab it now to reap its full benefits.
-
 Budget for effective threat management workplace cyber security risk management
Budget for effective threat management workplace cyber security risk managementFirm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Present the topic in a bit more detail with this Budget For Effective Threat Management Workplace Cyber Security Risk Management. Use it as a tool for discussion and navigation on Incident Management, Risk Management, Client Onboarding Process, Document Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact analysis for effective threat management in cyber security risk management
Impact analysis for effective threat management in cyber security risk managementThis slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Introducing Impact Analysis For Effective Threat Management In Cyber Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Focus Areas, Actual Access Violations, Access Rights Authorized, using this template. Grab it now to reap its full benefits.
-
 Building organizational security strategy plan budget analysis for effective security management
Building organizational security strategy plan budget analysis for effective security managementPresent the topic in a bit more detail with this Building Organizational Security Strategy Plan Budget Analysis For Effective Security Management. Use it as a tool for discussion and navigation on Analysis, Management, Workplace. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan effective security management at workplace
Building organizational security strategy plan effective security management at workplaceThis slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Effective Security Management At Workplace. Use it as a tool for discussion and navigation on Management, Workplace, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan role of management in effective corporate
Building organizational security strategy plan role of management in effective corporateThis slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief security office in order to ensure the effective corporate security governance. Deliver an outstanding presentation on the topic using this Building Organizational Security Strategy Plan Role Of Management In Effective Corporate. Dispense information and present a thorough explanation of Management, Corporate, Governance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enhancing overall project security it budget for effective project management at workplace
Enhancing overall project security it budget for effective project management at workplaceFirm has prepared a budget for managing projects effectively by optimizing various functional areas across workplace. It also provides information about the software used and the duration required for implementation. Present the topic in a bit more detail with this Enhancing Overall Project Security It Budget For Effective Project Management At Workplace. Use it as a tool for discussion and navigation on Management, Workplace, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
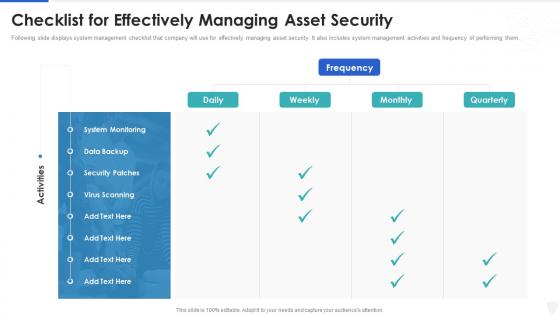 Cybersecurity and digital business risk management checklist for effectively managing asset security
Cybersecurity and digital business risk management checklist for effectively managing asset securityFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Present the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Checklist For Effectively Managing Asset Security. Use it as a tool for discussion and navigation on System Monitoring, Data Backup, Security Patches . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective Mobile Device Management Ensuring Checklist For Mobile Security Deployment
Effective Mobile Device Management Ensuring Checklist For Mobile Security DeploymentThis slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Present the topic in a bit more detail with this Effective Mobile Device Management Ensuring Checklist For Mobile Security Deployment. Use it as a tool for discussion and navigation on Ensuring Checklist For Mobile Security Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective Mobile Device Security Management Ppt Template
Effective Mobile Device Security Management Ppt TemplateThis slide portrays information regarding how firm is successful in handling security issues events and is able in reducing the occurrence of events associated to mobile device. Present the topic in a bit more detail with this Effective Mobile Device Security Management Ppt Template. Use it as a tool for discussion and navigation on Effective Mobile Device Security Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Mobile Device Security Effective Mobile Device Management Ppt Formats
Implementing Mobile Device Security Effective Mobile Device Management Ppt FormatsThis slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Present the topic in a bit more detail with this Implementing Mobile Device Security Effective Mobile Device Management Ppt Formats. Use it as a tool for discussion and navigation on Implement Enterprise Security Program, Implement Control Environment, Implement Security Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Analyzing Budget For Effective Mobile Device Management Android Device Security Management
Analyzing Budget For Effective Mobile Device Management Android Device Security ManagementFirm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Present the topic in a bit more detail with this Analyzing Budget For Effective Mobile Device Management Android Device Security Management. Use it as a tool for discussion and navigation on Incident Management, Risk Management, Document Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective Mobile Device Security Management Android Device Security Management
Effective Mobile Device Security Management Android Device Security ManagementThis slide portrays information regarding how firm is successful in handling security issues events and is able in reducing the occurrence of events associated to mobile device. Present the topic in a bit more detail with this Effective Mobile Device Security Management Android Device Security Management. Use it as a tool for discussion and navigation on Security Requirement, Security Incidents, Security Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Role Of Management In Effective Android Device Security Management
Role Of Management In Effective Android Device Security ManagementThis slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Deliver an outstanding presentation on the topic using this Role Of Management In Effective Android Device Security Management. Dispense information and present a thorough explanation of Strategic Alignment, Risk Management, Measuring Performance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents
Incident Response Playbook Impact Categories For Effectively Handling Cyber Security IncidentsMentioned slide provides information about the impact categories which can be used for effectively handling various cyber security incidents. Categories covered are function, information and recoverability impact. Increase audience engagement and knowledge by dispensing information using Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents. This template helps you present information on three stages. You can also present information on Functional Impact, Information Impact, Recoverability Impact using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





