Powerpoint Templates and Google slides for Security Effectiveness
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Endpoint Security Approaches To Implement Effective Endpoint Security
Endpoint Security Approaches To Implement Effective Endpoint SecurityThis slide showcases the techniques of deploying effective endpoint security which include on-location, cloud, hybrid endpoint security, etc. Introducing Endpoint Security Approaches To Implement Effective Endpoint Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Agent Based Security, Remote Device Connection, Effective Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Checklist To Implement Effective Endpoint Security
Endpoint Security Checklist To Implement Effective Endpoint SecurityThis slide showcases the actions performed while deploying endpoint security, person responsible, status and comments for the same. Deliver an outstanding presentation on the topic using this Endpoint Security Checklist To Implement Effective Endpoint Security. Dispense information and present a thorough explanation of Education And Training, Recognize Known Malware, Endpoint Protection Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Endpoint Security Roadmap To Implement Effective Endpoint Security
Endpoint Security Roadmap To Implement Effective Endpoint SecurityThis slide outlines the steps to deploy endpoint security which include recognizing known malware, reduce end user access, utilizing application control, etc. Increase audience engagement and knowledge by dispensing information using Endpoint Security Roadmap To Implement Effective Endpoint Security. This template helps you present information on six stages. You can also present information on Utilize Sensible Application Control, Recognize And Avoid Known Malware, Block Dangerous Activity, Effective Endpoint Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Effective Software Of Visualization Security To Secure Access
Effective Software Of Visualization Security To Secure AccessThis slide showcases various software for visualization security. The main purpose of this template is to secure data transmission . this includes tableau, microsoft power BI, google data studio, etc. Presenting our well structured Effective Software Of Visualization Security To Secure Access. The topics discussed in this slide are Microsoft Power, Google Data Studio, Secure Access. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 How Does IP Security Work Effectively
How Does IP Security Work EffectivelyThis slide showcases ways in which IP security works. The main purpose of this template is to showcase the formation of security in data. This includes host recognition, negotiation, IPsec Circuit, etc. Introducing our premium set of slides with name How Does IP Security Work Effectively. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Host Recognition, Negotiation, Security Work Effectively. So download instantly and tailor it with your information.
-
 Effective Cyber Security Management Process
Effective Cyber Security Management ProcessFollowing slide showcases process that can help businesses in mitigating cyber security threats. It includes steps such as pinpoint cyber security risks, evaluate cybersecurity risks, mitigation measures, monitoring, etc. Presenting our well structured Effective Cyber Security Management Process. The topics discussed in this slide are Identify The Cybersecurity Risks, Identify Cybersecurity Risks, Mitigation Measures. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Effective Cyber Security Strategies In Automotive Sector
Effective Cyber Security Strategies In Automotive SectorThis slide highlights cyber security methods in automobile industry. The purpose of this slide is to help managers in safeguarding vehicles from threats by implementing robust security measures. It includes elements such as risk assessment, user education, etc. Introducing our premium set of slides with Effective Cyber Security Strategies In Automotive Sector Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk Assessment, Security By Design, Patch Management So download instantly and tailor it with your information.
-
 Addressing Mobile Application Security Vulnerabilities For Effective Risk Protection
Addressing Mobile Application Security Vulnerabilities For Effective Risk ProtectionFollowing slide showcases application security vulnerabilities of mobiles for risk protection. It further includes factors such as poor server side controls, accidental data leak, poor authorization along side description, solution, etc. Introducing our Addressing Mobile Application Security Vulnerabilities For Effective Risk Protection set of slides. The topics discussed in these slides are Accidental Data Leak, Poor Authorization, Poor Server Side ControlsThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Securing Food Safety In Online Analyzing Food Delivery App Features For Effective
Securing Food Safety In Online Analyzing Food Delivery App Features For EffectiveThis slide covers application features for restaurant business such as real time order tracking, notification and alerts and enabling promotions and discounts. Introducing Securing Food Safety In Online Analyzing Food Delivery App Features For Effective to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Pricing, Features, Personalization, POS Integration, using this template. Grab it now to reap its full benefits.
-
 Securing Food Safety In Online Route Optimization Software For Effective Food
Securing Food Safety In Online Route Optimization Software For Effective FoodThis slide covers utilizing route optimization software to get real time updates. It involves key features such as real time routes updates, temperature control and minimizes food spoilage. Introducing Securing Food Safety In Online Route Optimization Software For Effective Food to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Real Time Updates, Temperature Control, Minimizes Food Spoilage, using this template. Grab it now to reap its full benefits.
-
 Effective Features Of SIEM Cyber Security
Effective Features Of SIEM Cyber SecurityThis slide showcases the SIEM cyber security package. Its aim is to log event management. This slide includes network hardware, firewall, system, operating system, security alerts and analysis. Introducing our premium set of slides with name Effective Features Of SIEM Cyber Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Workstations, System Imports, Siem System. So download instantly and tailor it with your information.
-
 Effective Methods For Assuring Building Security
Effective Methods For Assuring Building SecurityPresenting our set of slides with Effective Methods For Assuring Building Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Regulate Key Control, Develop Reception Area, Provide Employee Trainings.
-
 Best Practices To Implement NIDS For Maintaining Effective Cyber Security
Best Practices To Implement NIDS For Maintaining Effective Cyber SecurityThis Slide Represents Effective Strategies For Employing NIDS. It Aims To Help Organizations Implement NIDS To Detect, Respond And Mitigate Cyber Threats Within Networks. Introducing Our Premium Set Of Slides With Best Practices To Implement NIDS For Maintaining Effective Cyber Security. Ellicudate The Three Stages And Present Information Using This PPT Slide. This Is A Completely Adaptable Powerpoint Template Design That Can Be Used To Interpret Topics Like Proper Network Segmentation, Thorough Traffic Analysis, Signature Database Upgradation. So Download Instantly And Tailor It With Your Information.
-
 Checklist For Effective Application Security Deployment
Checklist For Effective Application Security DeploymentThis slide showcases the actions performed while deploying application security, person responsible, status and comments for the same. Presenting our well structured Checklist For Effective Application Security Deployment The topics discussed in this slide are Person Responsible, StatusThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Checklist To Ensure Effective Completion Of IT Security Awareness Training Cybersecurity SS
Checklist To Ensure Effective Completion Of IT Security Awareness Training Cybersecurity SSThis slide represents checklist for promoting strategy adopted by security professionals for preventing and mitigating cyber security risks. It includes activities such as gain executive buy-in etc. Present the topic in a bit more detail with this Checklist To Ensure Effective Completion Of IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Organizational Activities, Security Awareness Training, Ensure Effective Completion. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Essential Components Of Effective IT Security Awareness Training Program Cybersecurity SS
Essential Components Of Effective IT Security Awareness Training Program Cybersecurity SSThis slide represents essential elements for developing training program which helps to mitigate cyber security risks. It include components such as educational content, testing etc. Introducing Essential Components Of Effective IT Security Awareness Training Program Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Educational Content, Metrics And Reporting, Testing, Security Awareness Training Program, using this template. Grab it now to reap its full benefits.
-
 Steps For Creating Effective IT Security Awareness Training Program Cybersecurity SS
Steps For Creating Effective IT Security Awareness Training Program Cybersecurity SSThis slide represents procedure for developing training program which helps to mitigate cyber security risks. It include steps such as identify risks, change behavior etc. Increase audience engagement and knowledge by dispensing information using Steps For Creating Effective IT Security Awareness Training Program Cybersecurity SS. This template helps you present information on five stages. You can also present information on Change Behavior, Identify Risks, Security Awareness, Training Program, Track Metrics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Raci Matrix For Effective Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS
Raci Matrix For Effective Endpoint Security Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint security team responsible, accountable, consulted and informed RACI matrix. It provides details about endpoint detection and response, network security, etc.Deliver an outstanding presentation on the topic using this Raci Matrix For Effective Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Monitor Security, Identity Strategic Risk, Perform Business Impact Assessments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Organization Security Maturity Model For Effective Communication
Organization Security Maturity Model For Effective CommunicationThis slide represents a maturity model matrix for organization security that helps to foster effective communication of security measures to board. Key components are fundamentals, awareness level, technology, ownership, etc. Presenting our well structured Organization Security Maturity Model For Effective Communication. The topics discussed in this slide are Organizing Fundamental, Awareness Level, Technology. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Effective Security Configuration Management Tools
Effective Security Configuration Management ToolsThis slide includes various tools for managing security configuration in the organisation. Its objective is to use the best available tool which is feature rich. This slide showcases tool such as solar winds, auvik, Microsoft intune, etc. Presenting our well structured Effective Security Configuration Management Tools. The topics discussed in this slide are Software, Endpoint Central Manage Engine, Network Configuration Manager. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Architecture Of Effective Application Security Implementation
Architecture Of Effective Application Security ImplementationThis slide represents the architecture of efficient application security deployment which includes components such as client tier, user applications and data, etc. Presenting our well structured Architecture Of Effective Application Security Implementation The topics discussed in this slide are Clients Tier, Users Data and ApplicationsThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities And Prevent Threats, Protect Organizations Networks, Filter Out Malicious Activities, Security Devices Or Controls, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing our well researched set of slides titled Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security
Table Of Contents For Implementing Intrusion Prevention System For Effective Network SecurityIntroducing Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Issues Experienced Due Inefficient Network Security, Impact On Organizational Operations, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Budget Plan, Impact Assessment, Dashboards, Case Study Analysis, using this template. Grab it now to reap its full benefits.
-
 Best Practices Of Effective Network Security
Best Practices Of Effective Network SecurityThis slide displays best practices for companies to deploy network security including multi factor authentication, security awareness training, and cybersecurity risk assessment. Presenting our set of slides with name Best Practices Of Effective Network Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Multi Factor Authentication, Security Awareness Training, Cybersecurity Risk Assessment.
-
 Types Of Effective Web Filtering To Secure System
Types Of Effective Web Filtering To Secure SystemThis slide showcases various types of web filtering firewall system. Its objective is to understand the importance of firewall system to maintain secure environment. This slide includes packet, inspection, proxy, application and next generation firewall. Presenting our set of slides with name Types Of Effective Web Filtering To Secure System. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Packet Filtering, Stateful Inspection, Proxy, Application Level .
-
 Current security infrastructure effective information security risk management process
Current security infrastructure effective information security risk management processMentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Present the topic in a bit more detail with this Current Security Infrastructure Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Asset Management, Incident Mitigation Plan, Incident Recovery. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information security dashboard effective information security risk management process
Information security dashboard effective information security risk management processFollowing slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Present the topic in a bit more detail with this Information Security Dashboard Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Risk Rating Breakdown, Risk Analysis Progress Action Plan Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat and dashboard effective information security risk management process
Threat and dashboard effective information security risk management processFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Threat And Dashboard Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Security Recommendation, Security Controls, Active Remediation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security current security infrastructure performance analysis
Effective information security current security infrastructure performance analysisMentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an outstanding presentation on the topic using this Effective Information Security Current Security Infrastructure Performance Analysis. Dispense information and present a thorough explanation of Performance, Actual Target Met, Target To Be Met, Asset Management, Data Security, Incident Recovery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Effective information security impact on security infrastructure performance
Effective information security impact on security infrastructure performanceMentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver an outstanding presentation on the topic using this Effective Information Security Impact On Security Infrastructure Performance. Dispense information and present a thorough explanation of NIST Core Functions, Performance, Actual Target met using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Effective information security information security risk management dashboard
Effective information security information security risk management dashboardFollowing slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an outstanding presentation on the topic using this Effective Information Security Information Security Risk Management Dashboard. Dispense information and present a thorough explanation of Risk Threshold, Risk Analysis, Progress Response, Progress Risks Threshold using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Building organizational security strategy plan ensuring effective intellectual property security
Building organizational security strategy plan ensuring effective intellectual property securityThis slide provides information about effective intellectual property security by protecting intellectual property assets such as patents, trade secrets, trademarks, etc. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Ensuring Effective Intellectual Property Security. Use it as a tool for discussion and navigation on Information, Intellectual, Trademarks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Impact Of Effective Mobile Android Device Security Management
Determine Impact Of Effective Mobile Android Device Security ManagementThis slide covers information regarding the impact of effective mobile device management solution such as reduction in data breaches and records exposed, reduction in malwares samples per quarter. Deliver an outstanding presentation on the topic using this Determine Impact Of Effective Mobile Android Device Security Management. Dispense information and present a thorough explanation of Malwares Samples, Data Breaches, Device Management Solution using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPI Metrics Dashboard To Effectively Building A Security Awareness Program
KPI Metrics Dashboard To Effectively Building A Security Awareness ProgramThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this KPI Metrics Dashboard To Effectively Building A Security Awareness Program. Use it as a tool for discussion and navigation on Threat Management, Metrics Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Developing Cyber Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Management
Developing Cyber Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat ManagementThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this Developing Cyber Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Management. Use it as a tool for discussion and navigation on KPI Metrics Dashboard, Effectively Track Cyber, Threat Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Architecture And Security Review Effect And Benefits To Enterprises While Using Abc Multi Cloud
Cloud Architecture And Security Review Effect And Benefits To Enterprises While Using Abc Multi CloudThis slide covers the effect and benefits of using cloud management platform such as less expensive, performance improvement, empowering enterprise and many more. Present the topic in a bit more detail with this Cloud Architecture And Security Review Effect And Benefits To Enterprises While Using Abc Multi Cloud. Use it as a tool for discussion and navigation on Consumption Or Subscription Billing, Integrated Dashboard, Empowering Enterprise. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 KPI Metrics Dashboard To Effectively Track Cyber Threat Management Conducting Security Awareness
KPI Metrics Dashboard To Effectively Track Cyber Threat Management Conducting Security AwarenessThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Deliver an outstanding presentation on the topic using this KPI Metrics Dashboard To Effectively Track Cyber Threat Management Conducting Security Awareness. Dispense information and present a thorough explanation of Monthly Threat Status, Current Risk Status, Threats Based Role using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Impact Of Effective Mobile Nterprise Mobile Security For On Device
Determine Impact Of Effective Mobile Nterprise Mobile Security For On DeviceThis slide covers information regarding the impact of effective mobile device management solution such as reduction in data breaches and records exposed, reduction in malwares samples per quarter.Deliver an outstanding presentation on the topic using this Determine Impact Of Effective Mobile Nterprise Mobile Security For On Device. Dispense information and present a thorough explanation of Records Exposed, Malwares Samples, Devices Workplace using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPI Metrics Dashboard To Effectively Track Cyber Threat Implementing Security Awareness Training
KPI Metrics Dashboard To Effectively Track Cyber Threat Implementing Security Awareness TrainingThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this KPI Metrics Dashboard To Effectively Track Cyber Threat Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Current Risk Status, Threats By Owners, Risk By Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Operations Dashboard For Detection And Response Effectiveness
Security Operations Dashboard For Detection And Response EffectivenessThis slide exhibits security operations dashboard. It include positive incidents, false positive incidents, false positive risk score, false positive security incident etc. Introducing our Security Operations Dashboard For Detection And Response Effectiveness set of slides. The topics discussed in these slides are Security Operations Dashboard, Detection, Response Effectiveness. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Incident Management Dashboard For Effective Awareness Training
Cyber Security Incident Management Dashboard For Effective Awareness TrainingThis slide covers cyber security incident management dashboard for effective awareness training. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Presenting our well-structured Cyber Security Incident Management Dashboard For Effective Awareness Training. The topics discussed in this slide are Cyber Security, Incident Management Dashboard, Effective Awareness Training. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security
Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Risk By Threats, Threat Report, Current Risk Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ensuring Effective Intellectual Property Security Defense Plan To Protect Firm Assets
Ensuring Effective Intellectual Property Security Defense Plan To Protect Firm AssetsThis slide provides information about effective intellectual property security by protecting intellectual property assets such as patents, trade secrets, trademarks, etc. Present the topic in a bit more detail with this Ensuring Effective Intellectual Property Security Defense Plan To Protect Firm Assets. Use it as a tool for discussion and navigation on Proprietary Information, Trademarks, Invention Agreements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SecOps Effective Implementation Impact On Security Breaches Ppt Elements
SecOps Effective Implementation Impact On Security Breaches Ppt ElementsThis slide outlines the successful implementation impact of SecOps on organizational security breaches. The purpose of this slide is to highlight the number of reduced security breaches inside a company after implementing SecOps. Security breaches include phishing, network intrusion, and so on. Present the topic in a bit more detail with this SecOps Effective Implementation Impact On Security Breaches Ppt Elements. Use it as a tool for discussion and navigation on Security Breaches, Implementing Secops System. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective It Cost Optimization Initiatives Strategic Plan To Secure It Infrastructure Strategy SS V
Effective It Cost Optimization Initiatives Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding effective IT cost optimization strategies for IT executives such as revamping technology procurement, DevOps deployment, enabling business process reengineering, etc. Increase audience engagement and knowledge by dispensing information using Effective It Cost Optimization Initiatives Strategic Plan To Secure It Infrastructure Strategy SS V. This template helps you present information on four stages. You can also present information on Revamping Technology Procurement, Enabling Business Process Reengineering, Optimization Initiatives using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda of effective information security risk management process
Agenda of effective information security risk management processIncrease audience engagement and knowledge by dispensing information using Agenda Of Effective Information Security Risk Management Process. This template helps you present information on three stages. You can also present information on Agenda using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Asset components effective information security risk management process
Asset components effective information security risk management processFollowing slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost.Present the topic in a bit more detail with this Asset Components Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Impact Rating On Business, Criticality Rating, Failure Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Budget for information effective information security risk management process
Budget for information effective information security risk management processMentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost.Deliver an outstanding presentation on the topic using this Budget For Information Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Incident Management, Asset Management, Training Duration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Defining risk level effective information security risk management process
Defining risk level effective information security risk management processFollowing slide defines the incident risk level. It includes details about risk level, risk score and its description. Deliver an outstanding presentation on the topic using this Defining Risk Level Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Immediate Controlling, Controlling Measures, Offered By The Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Defining security threats effective information security risk management process
Defining security threats effective information security risk management processThis slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures.Introducing Defining Security Threats Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Natural Disaster, Environmental Control Failures, Deliberate Software Attacks, using this template. Grab it now to reap its full benefits.
-
 Defining vulnerability rating effective information security risk management process
Defining vulnerability rating effective information security risk management processFollowing slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description.Present the topic in a bit more detail with this Defining Vulnerability Rating Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Occurrence Of Attack, Organization Is Reasonably, Organization Is Capable Enough. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security management process information security risk assessment
Effective information security management process information security risk assessmentThis slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence.Deliver an outstanding presentation on the topic using this Effective Information Security Management Process Information Security Risk Assessment. Dispense information and present a thorough explanation of Facilities And Equipment, Unauthorized Disclosure, Valuable Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Employee training schedule effective information security risk management process
Employee training schedule effective information security risk management processThis slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration.Present the topic in a bit more detail with this Employee Training Schedule Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Training Duration, Intermediate, Training Mode. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons slide for effective information security risk management process
Icons slide for effective information security risk management processPresenting our well crafted Icons Slide For Effective Information Security Risk Management Process set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Impact assessment matrix effective information security risk management process
Impact assessment matrix effective information security risk management processPresent the topic in a bit more detail with this Impact Assessment Matrix Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Minor To No Infringement, Suspected Malicious Intent, Impact Medium. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact on security performance effective information security risk management process
Impact on security performance effective information security risk management processMentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver an outstanding presentation on the topic using this Impact On Security Performance Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of After Introducing, Risk Assessment Process, Assets Efficiently using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Incident management tool effective information security risk management process
Incident management tool effective information security risk management processMentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform.Present the topic in a bit more detail with this Incident Management Tool Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Notify Employee, Message During Any Breach, Automated Workflow. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
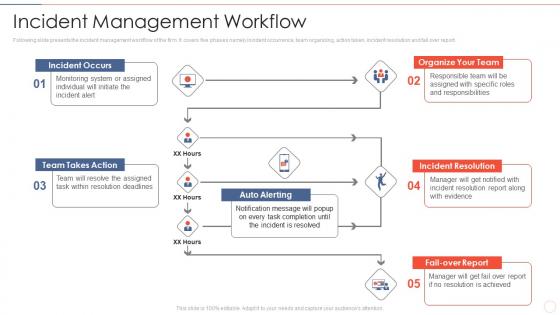 Incident management workflow effective information security risk management process
Incident management workflow effective information security risk management processFollowing slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report.Introducing Incident Management Workflow Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Organize Your Team, Incident Resolution, Team Takes Action, using this template. Grab it now to reap its full benefits.





