Powerpoint Templates and Google slides for Security Different
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Overview Of Different Types Of Network Security Training Ppt
Overview Of Different Types Of Network Security Training PptPresenting Overview of Different Types of Network Security. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Data security it requirement of data security in different sectors
Data security it requirement of data security in different sectorsThis slide depicts the requirement of data security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Present the topic in a bit more detail with this Data Security IT Requirement Of Data Security In Different Sectors. Use it as a tool for discussion and navigation on Medical, Military, Govt, Corporate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
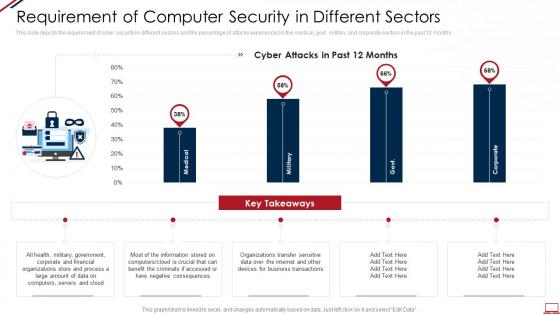 Computer system security requirement of computer security in different sectors
Computer system security requirement of computer security in different sectorsThis slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Present the topic in a bit more detail with this Computer System Security Requirement Of Computer Security In Different Sectors. Use it as a tool for discussion and navigation on Organizations, Process, Business. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Types Of Secure Web Gateway Deployment Network Security Using Secure Web Gateway
Different Types Of Secure Web Gateway Deployment Network Security Using Secure Web GatewayThis slide demonstrates the various kinds of SWG deployments. The purpose of this slide is to explain the different types of Secure Web Gateway deployment methods such as on-premises deployment, cloud-based deployment and hybrid deployment. Increase audience engagement and knowledge by dispensing information using Different Types Of Secure Web Gateway Deployment Network Security Using Secure Web Gateway. This template helps you present information on three stages. You can also present information on Deployment, Businesses, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Your Digital Assets Application Of Different Sectors In Crypto Wallets
Secure Your Digital Assets Application Of Different Sectors In Crypto WalletsThis slide showcases business sectors, including cryptocurrency, in daily functions. This slide aims to highlight sectors such as travel, entertainment, gaming, education, trading, healthcare, banking, etc. Introducing Secure Your Digital Assets Application Of Different Sectors In Crypto Wallets to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Entertainment Industry, Businesses And Corporations, Gaming Industry, Travel Sector, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Requirement Of Ethical Hackers In Different Sectors
Ethical Hacking And Network Security Requirement Of Ethical Hackers In Different SectorsThis slide depicts the requirement of ethical hackers in different sectors such as the medical, military, government sector, and corporate sectors. Present the topic in a bit more detail with this Ethical Hacking And Network Security Requirement Of Ethical Hackers In Different Sectors. Use it as a tool for discussion and navigation on Requirement Of Ethical Hackers, Military, Government Sector, Corporate Sectors. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks
Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber AttacksThis slide represents the different types of cyber-attacks throughout the year, including the percentage of total loss caused by these attacks. Present the topic in a bit more detail with this Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks. Use it as a tool for discussion and navigation on Cyber Attacks Throughout, Online Or Web Based Attacks, Malware Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Decrease In Cyber Attacks On Different Mobile Devices Mobile Device Security Cybersecurity SS
Decrease In Cyber Attacks On Different Mobile Devices Mobile Device Security Cybersecurity SSThis slide showcases decline in cyber attacks after implementation of mobile security techniques. It highlights decrease in cyber attacks on android and iOS devices Deliver an outstanding presentation on the topic using this Decrease In Cyber Attacks On Different Mobile Devices Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Security Attacks, Mobile Devices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Difference Between ZTNA And Software Defined Perimeter Zero Trust Security Model
Difference Between ZTNA And Software Defined Perimeter Zero Trust Security ModelThis slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Deliver an outstanding presentation on the topic using this Difference Between ZTNA And Software Defined Perimeter Zero Trust Security Model. Dispense information and present a thorough explanation of Definition, Deployment, Key Features using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Different Types Of Network Security For Preventing Data Safely
Different Types Of Network Security For Preventing Data SafelyThis slide showcases various types of network security. The main purpose of this template is to ensure organizational data safety from any kind of threats. This includes firewall, remote access VPN, Network segmentation, email security, etc. Presenting our set of slides with Different Types Of Network Security For Preventing Data Safely. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Segmentation, Data Loss Prevention.
-
 Difference Secured Unsecured Bonds In Powerpoint And Google Slides Cpb
Difference Secured Unsecured Bonds In Powerpoint And Google Slides CpbPresenting Difference Secured Unsecured Bonds In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Difference Secured Unsecured Bonds. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 5G Security Applications In Different Industries
5G Security Applications In Different IndustriesThis slide shows applications in 5G security to boost business operations. It further includes integrate IOT solutions, AR or VR,offers precision solutions etc. Presenting our set of slides with 5G Security Applications In Different Industries. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Healthcare, Public Sector.
-
 Different Types Of Cryptographic Security Techniques Cloud Cryptography
Different Types Of Cryptographic Security Techniques Cloud CryptographyThis slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric-key cryptography, asymmetric-key cryptography, hash functions, steganography, etc. Deliver an outstanding presentation on the topic using this Different Types Of Cryptographic Security Techniques Cloud Cryptography. Dispense information and present a thorough explanation of Cryptographic, Techniques, Quantum Cryptography using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Difference Securities Bonds In Powerpoint And Google Slides Cpb
Difference Securities Bonds In Powerpoint And Google Slides CpbPresenting our Difference Securities Bonds In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Difference Securities Bonds. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Different Security Threats To Be Managed By Web Strategic Guide For Web Design Company
Different Security Threats To Be Managed By Web Strategic Guide For Web Design CompanyMentioned slide provides insights into various security threats to be managed by web designers. It includes key components such as SQL injection, ransomware, spyware, phishing, cross site scription, and virus and bugs. Increase audience engagement and knowledge by dispensing information using Different Security Threats To Be Managed By Web Strategic Guide For Web Design Company. This template helps you present information on six stages. You can also present information on Injection, Scription, Developers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Your Digital Assets Difference Between Hot And Cold Wallets
Secure Your Digital Assets Difference Between Hot And Cold WalletsThis slide highlights the comparison between hot and cold wallets. These are the ways to make transactions in cryptocurrency. The comparison is made on the basis of private key, security, convenience, types, suitability, etc. Present the topic in a bit more detail with this Secure Your Digital Assets Difference Between Hot And Cold Wallets. Use it as a tool for discussion and navigation on Paper Wallets, Hardware Wallet, Spare Hard Drive Or Computer, Hot And Cold Wallets. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Your Digital Assets Different Types Of Cold Crypto Wallets
Secure Your Digital Assets Different Types Of Cold Crypto WalletsThis slide represents the variety of cold wallets available in the market for transactions in cryptocurrency. The purpose of this slide is to highlight the types which, are hardware wallets and paper wallets. Deliver an outstanding presentation on the topic using this Secure Your Digital Assets Different Types Of Cold Crypto Wallets. Dispense information and present a thorough explanation of Hardware Wallets, Paper Wallets, Paper Has A Quick Response, Cold Crypto Wallets using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Your Digital Assets Different Types Of Hot Crypto Wallets
Secure Your Digital Assets Different Types Of Hot Crypto WalletsThis slide represents the variety of hot wallets available in the market for transactions in cryptocurrency. The purpose of this slide is to highlight the types which are mobile wallets, web wallets, and desktop wallets. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Different Types Of Hot Crypto Wallets. This template helps you present information on four stages. You can also present information on Mobile Wallets, Web Wallets, Desktop Wallets, Hot Crypto Wallets using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Your Digital Assets Different Types Of Wallets Employed For Cryptocurrencies
Secure Your Digital Assets Different Types Of Wallets Employed For CryptocurrenciesThis slide discusses different varieties of crypto wallets present in the market for worldwide transactions in cryptocurrency. The purpose of this slide is the highlight the types such as hot and cold wallets, web wallets, hardware wallets, mobile wallets, etc. Introducing Secure Your Digital Assets Different Types Of Wallets Employed For Cryptocurrencies to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Hardware Wallets, Desktop Wallets, Paper Wallets, Employed For Cryptocurrencies, using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Different Firewall Types And Their Functions
Firewall Network Security Different Firewall Types And Their FunctionsThis slide outlines the various types of firewalls, including their functions. The purpose of this slide is to showcase the different firewall types, such as packet layer, proxy server, circuit level, application level, and software firewalls. Introducing Firewall Network Security Different Firewall Types And Their Functions to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Packet Layer, Proxy Server, Circuit Level using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security How Are Ethical Hackers Different Than Malicious Hackers
Ethical Hacking And Network Security How Are Ethical Hackers Different Than Malicious HackersThis slide represents how ethical hackers are different from malicious hackers based on their purpose of hacking for organizational benefit and personal advantage. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security How Are Ethical Hackers Different Than Malicious Hackers. This template helps you present information on two stages. You can also present information on Ethical Hackers, Malicious Hackers, Organizational Benefit, Organizations Security Posture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Different Types Of Security Policies For Privacy Framework
Different Types Of Security Policies For Privacy FrameworkThis slide showcases three different tiers of privacy framework. The main purpose of this template is focus on establishing policies, procedures and governance. This includes operational privacy, audit, management support, etc.Introducing our premium set of slides with Different Types Of Security Policies For Privacy Framework. Ellicudate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Management, Incident Management, Operational Management. So download instantly and tailor it with your information.
-
 Internet Gateway Security IT Different Types Of Secure Web Gateway
Internet Gateway Security IT Different Types Of Secure Web GatewayThis slide demonstrates the various kinds of SWG deployments. The purpose of this slide is to explain the different types of Secure Web Gateway deployment methods such as on-premises deployment, cloud-based deployment and hybrid deployment. Introducing Internet Gateway Security IT Different Types Of Secure Web Gateway to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on On Premises Deployment, CLOUD Based Deployment, Hybrid Deployment, using this template. Grab it now to reap its full benefits.
-
 Different Security Layers In Sql Server Environments
Different Security Layers In Sql Server EnvironmentsFollowing slide showcases SQL server security layers, also including layers such as physical security, network security, database security, application security and operating system security, etc. Introducing our premium set of slides with Different Security Layers In Sql Server Environments. Ellicudate the fivestages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Physical Security, Network Security, Operating System Security. So download instantly and tailor it with your information.
-
 Different Types Of Triage Cyber Security Incidents
Different Types Of Triage Cyber Security IncidentsThis slide represents different triage cybersecurity incidents which assists to categorize, prioritize and respond to various types of security incidents. It includes different types of triage cybersecurity incidents such as heavy traffic on port 80, etc Introducing our premium set of slides with name Different Types Of Triage Cyber Security Incidents Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Phishing Attempts, Malware Attacks. So download instantly and tailor it with your information.
-
 Different Encryption Methods To Secure Business Data
Different Encryption Methods To Secure Business DataThis slide represents various types of encryption method which assists businesses to protect data and maintain regulatory compliances. It includes different encryption methods to secure business data such as advance encryption standards, rivest shamir adleman, etc. Introducing our premium set of slides with name Different Encryption Methods To Secure Business Data. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Format Preserving Encryption, Blowfish, Advance Encryption Standards. So download instantly and tailor it with your information.
-
 Estimating Different Types Strategic Retirement Planning To Build Secure Future Fin SS
Estimating Different Types Strategic Retirement Planning To Build Secure Future Fin SSThis slide shows information about multiple kinds of healthcare expenses which can be used by individuals while estimating the healthcare cost. It includes three main components which are medical insurance, medication and long term care. Introducing Estimating Different Types Strategic Retirement Planning To Build Secure Future Fin SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Medication, Medical Insurance, Health Insurance Premiums, using this template. Grab it now to reap its full benefits.
-
 Different Types Of Security Gap Mitigation Techniques
Different Types Of Security Gap Mitigation TechniquesThis slide showcases various types of security gaps for data protection to showcase data encryption for shared data. This includes role-based access control, encrypted file sharing, regular security audits, etc. Presenting our set of slides with name Different Types Of Security Gap Mitigation Techniques. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Role Based Access Control, Data Encryption Techniques, Secure Data Access Methods.
-
 Impact Of Cashless Payment On Different Stakeholder Enhancing Transaction Security With E Payment
Impact Of Cashless Payment On Different Stakeholder Enhancing Transaction Security With E PaymentFollowing slide provides information about various benefits of cashless payment availed by business stakeholders. It includes key stakeholders such as business owners, customers, sponsors, partners and marketing employees. Introducing Impact Of Cashless Payment On Different Stakeholder Enhancing Transaction Security With E Payment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Business Owners, Customers, Sponsors And Partners using this template. Grab it now to reap its full benefits.
-
 Difference Between Authentication And Authorization In Application Security
Difference Between Authentication And Authorization In Application SecurityThis slide showcase the difference between authentication and authorization in application security on aspects such as purpose, operation, etc. Deliver an outstanding presentation on the topic using this Difference Between Authentication And Authorization In Application Security. Dispense information and present a thorough explanation of Confirms Credentials, Authentication, Authorization, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Different Categories Of Cobit Cyber Security Framework
Different Categories Of Cobit Cyber Security FrameworkThis slide discusses the different categories of COBIT which includes plan and organize, acquire and implement, deliver and support, monitor and evaluate, etc. Increase audience engagement and knowledge by dispensing information using Different Categories Of Cobit Cyber Security Framework. This template helps you present information on five stages. You can also present information on Acquire And Implement, Monitor And Evaluate, Plan And Organize, Cyber Security Framework using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Different Types Of Visualization Security For Protecting Data
Different Types Of Visualization Security For Protecting DataThis slides showcases various types of visualization data. The main purpose of this template is to showcase data encryption for shared data. This includes role based access control, encrypted file sharing, regular security audits, etc. Introducing our premium set of slides with Different Types Of Visualization Security For Protecting Data. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Methods, Regular Security Audits, Encrypted File Sharing. So download instantly and tailor it with your information.
-
 Different Modes Of IP Security For Securing Data
Different Modes Of IP Security For Securing DataThis slide showcases various modes of IP security. The main purpose of this template is to secure communication between two endpoints. This includes Point-to-point security, tunnel mode, remote access, etc. Introducing our Different Modes Of IP Security For Securing Data set of slides. The topics discussed in these slides are IP Security, Secure Communication, Point To Point Security, Tunnel Mode. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Tokenization For Improved Data Security Difference Between Tokenization And Masking Technology
Tokenization For Improved Data Security Difference Between Tokenization And Masking TechnologyThis slide represents the comparison between tokenization and masking. The purpose of this slide is to represent a comparative analysis on the basis of various components such as process, purpose, use cases, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Difference Between Tokenization And Masking Technology. Dispense information and present a thorough explanation of Data Preservation, Masking Technology, Maintains Data Format using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Different Phases Of Implementing Tokenization In Ds
Tokenization For Improved Data Security Different Phases Of Implementing Tokenization In DsThis slide highlights the steps for working of tokenization. The purpose of this slide is to outline the various ways of creating token and the phases which include initiating card transaction, producing tokens, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Different Phases Of Implementing Tokenization In Ds. This template helps you present information on six stages. You can also present information on Mathematically Reversible, Cryptographic Function, Producing Tokens using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Impact Of Tokenization On Different Industries
Tokenization For Improved Data Security Impact Of Tokenization On Different IndustriesThis slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Impact Of Tokenization On Different Industries. This template helps you present information on six stages. You can also present information on Tokenization, Data Security, Rapid Defect Detection, Ensuring Trust And Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Communication Different Stakeholders Business Recovery Plan To Overcome Cyber Security Threat
Cyber Communication Different Stakeholders Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various stakeholders to be taken care of during and after the business recovery periods such as customers, internal stakeholders, external agencies, and recovery team. Introducing Cyber Communication Different Stakeholders Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Customer, Government, Recovery Team, using this template. Grab it now to reap its full benefits.
-
 Different Types Of Malware Security Attacks Mobile Security
Different Types Of Malware Security Attacks Mobile SecurityThis slide gives an overview of malware and the various types associated with it which includes ransomware, worms, scareware and fileless malware. Increase audience engagement and knowledge by dispensing information using Different Types Of Malware Security Attacks Mobile Security This template helps you present information on Two stages. You can also present information on Security Of Mobile Device, Security Of Mobile Database, Security Of Mobile Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Fraud Prevention Training Program For Different Implementing E Commerce Security Measures
Fraud Prevention Training Program For Different Implementing E Commerce Security MeasuresThe slide represent ecommerce fraud prevention training program designed for various departments. It covers team such as fulfilment, marketing, IT and also training focus and action items. Increase audience engagement and knowledge by dispensing information using Fraud Prevention Training Program For Different Implementing E Commerce Security Measures. This template helps you present information on three stages. You can also present information on Training Purpose, Department, Action Items using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Web Security Upgradation Comparative Analysis Of Different Web Security Tools
Web Security Upgradation Comparative Analysis Of Different Web Security ToolsThis slide highlights the availability of various services in different web security tools, such as selenium, WATIR, RFT, testRigor, etc. Present the topic in a bit more detail with this Web Security Upgradation Comparative Analysis Of Different Web Security Tools. Use it as a tool for discussion and navigation on Recognize Security Issues, Bug And Website Scanner, Vulnerability Removal With Simplicity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Chatbot Security Measures For Different Development Stages
Chatbot Security Measures For Different Development StagesThis slide shows information regarding various security measures that organizations should adopt for different stages of chatbot development. These measures include deploying anti-virus, conducting threat modelling, performing static analysis, etc. Presenting our set of slides with Chatbot Security Measures For Different Development Stages. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Intial Phase, Design And Architecture, Development And Coding.
-
 Impact Of Different Chatbot Security Attacks
Impact Of Different Chatbot Security AttacksThis slide shows detailed information regarding various types of chatbot security attacks faced by IT teams or companies. These attacks are poisoning and privacy attacks. It also includes details related to impact of these attacks. Introducing our Impact Of Different Chatbot Security Attacks set of slides. The topics discussed in these slides are Poisoning Attacks, Privacy Attacks, Attacks. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Different Strategies For Securing Appropriate Grants Implementation Of Fundraising Strategy For Social
Different Strategies For Securing Appropriate Grants Implementation Of Fundraising Strategy For SocialThe slide illustrates various strategies to secure the right grant option as per the fiscal needs of the social enterprise. Various strategies included are align project with funding requirements, review fiscal needs and improve funding information.Introducing Different Strategies For Securing Appropriate Grants Implementation Of Fundraising Strategy For Social to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Improve Funding Information, Review Fiscal Needs, Funding Requirements, using this template. Grab it now to reap its full benefits.
-
 Impact Of Web Security On Different Businesses
Impact Of Web Security On Different BusinessesThis slide showcases the various factors that have improved which include security, reduced cyber threats in web, and so on. Introducing Impact Of Web Security On Different Businesses to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Decrease In Cyber Threats, Businesses Face Comparatively Less Expenses, Increased Security, using this template. Grab it now to reap its full benefits.
-
 How Different Biometric Technique Can Enhance Mobile Device Security Cybersecurity SS
How Different Biometric Technique Can Enhance Mobile Device Security Cybersecurity SSThis slide showcases use cases of different biometric techniques for enhancing mobile security. Biometric techniques used are fingerprint scanner, facial recognition, voice recognition etc. Introducing How Different Biometric Technique Can Enhance Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Company Financial Loss, Operational Disruption using this template. Grab it now to reap its full benefits.
-
 Mobile Threats Faced By Different Departments Mobile Device Security Cybersecurity SS
Mobile Threats Faced By Different Departments Mobile Device Security Cybersecurity SSThis slide showcases mobile security threats faced in different departments. Its key components are department, number of mobile threats and type of attacks Increase audience engagement and knowledge by dispensing information using Mobile Threats Faced By Different Departments Mobile Device Security Cybersecurity SS This template helps you present information on Three stages. You can also present information on Compliance, Incident Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Plan To Implement Different Mobile Biometric Techniques Mobile Device Security Cybersecurity SS
Plan To Implement Different Mobile Biometric Techniques Mobile Device Security Cybersecurity SSThis slide showcases plan that can help company to implement mobile biometric solutions. Its key components are biometric technique, team responsible, expected benefits, progress and budget allocated. Deliver an outstanding presentation on the topic using this Plan To Implement Different Mobile Biometric Techniques Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Policy Development, Choose Solution, Train Users using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Requirement of electronic information security in different sectors
Requirement of electronic information security in different sectorsThis slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an outstanding presentation on the topic using this Requirement Of Electronic Information Security In Different Sectors. Dispense information and present a thorough explanation of Cyber Attacks, Past 12 Months, Devices Business Transactions, Organizations Transfer, Sensitive Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Requirement Of Information Security In Different Sectors
Information Security Requirement Of Information Security In Different SectorsThis slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an outstanding presentation on the topic using this Information Security Requirement Of Information Security In Different Sectors. Dispense information and present a thorough explanation of Requirement, Information, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Requirement Of Network Security In Different Sectors
Network Security Requirement Of Network Security In Different SectorsThis slide depicts the requirement of network security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an outstanding presentation on the topic using this Network Security Requirement Of Network Security In Different Sectors. Dispense information and present a thorough explanation of Requirement Of Network Security In Different Sectors using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Requirement Of Information Technology Security In Different Sectors
Information Technology Security Requirement Of Information Technology Security In Different SectorsThis slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an outstanding presentation on the topic using this Information Technology Security Requirement Of Information Technology Security In Different Sectors. Dispense information and present a thorough explanation of Requirement, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Hacker Loss Due To Different Cyber Attacks Ppt Powerpoint Presentation Slides
Security Hacker Loss Due To Different Cyber Attacks Ppt Powerpoint Presentation SlidesThis slide represents the different types of cyber attacks throughout the year, including the percentage of total loss caused by these attacks. Present the topic in a bit more detail with this Security Hacker Loss Due To Different Cyber Attacks Ppt Powerpoint Presentation Slides. Use it as a tool for discussion and navigation on Different Cyber Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Assessing Cost Of Information Breach In Different Countries Information Security Risk Management
Assessing Cost Of Information Breach In Different Countries Information Security Risk ManagementDeliver an outstanding presentation on the topic using this Assessing Cost Of Information Breach In Different Countries Information Security Risk Management. Dispense information and present a thorough explanation of Assessing, Information Breach, Different Countries using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assessing Cost Of Information Breach In Different Information System Security And Risk Administration Plan
Assessing Cost Of Information Breach In Different Information System Security And Risk Administration PlanPresent the topic in a bit more detail with this Assessing Cost Of Information Breach In Different Information System Security And Risk Administration Plan. Use it as a tool for discussion and navigation on Past Decade, Social Engineering, Advanced Persistent Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Different Security Priorities At Organization Strategic Organizational Security Plan
Addressing Different Security Priorities At Organization Strategic Organizational Security PlanThis slide provides information about various security priorities essential in maintaining workplace security in terms of people security, intellectual property, brand protection, crisis management, corporate governance and information security. Increase audience engagement and knowledge by dispensing information using Addressing Different Security Priorities At Organization Strategic Organizational Security Plan. This template helps you present information on six stages. You can also present information on Information Security, Brand Protection, Crisis Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Different types security services cryptography ppt powerpoint presentation icon maker cpb
Different types security services cryptography ppt powerpoint presentation icon maker cpbPresenting our Different Types Security Services Cryptography Ppt Powerpoint Presentation Icon Maker Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Different Types Security Services Cryptography. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Difference between secured unsecured loans ppt powerpoint presentation inspiration cpb
Difference between secured unsecured loans ppt powerpoint presentation inspiration cpbPresenting our Difference Between Secured Unsecured Loans Ppt Powerpoint Presentation Inspiration Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Difference Between Secured Unsecured Loans This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Difference secured unsecured loan ppt powerpoint presentation inspiration images cpb
Difference secured unsecured loan ppt powerpoint presentation inspiration images cpbPresenting our Difference Secured Unsecured Loan Ppt Powerpoint Presentation Inspiration Images Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Difference Secured Unsecured Loan This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Different types security breaches ppt powerpoint presentation portfolio file formats cpb
Different types security breaches ppt powerpoint presentation portfolio file formats cpbPresenting Different Types Security Breaches Ppt PowerPoint Presentation Portfolio File Formats Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Different Types Security Breaches. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Different types secured loans ppt powerpoint presentation styles graphics cpb
Different types secured loans ppt powerpoint presentation styles graphics cpbPresenting our Different Types Secured Loans Ppt Powerpoint Presentation Styles Graphics Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Different Types Secured Loans. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.




