Powerpoint Templates and Google slides for Security Control
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Enterprise Risk Management Security Criteria And Control Measures For IT System Vulnerabilities
Enterprise Risk Management Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing Enterprise Risk Management Security Criteria And Control Measures For IT System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management Technical Security Control Model With Supporting Function
Enterprise Risk Management Technical Security Control Model With Supporting FunctionThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Introducing Enterprise Risk Management Technical Security Control Model With Supporting Function to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identify, Cryptographic Administration, Security Management, System Protection, using this template. Grab it now to reap its full benefits.
-
 Security Criteria And Control Measures For IT System Vulnerabilities
Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing Security Criteria And Control Measures For IT System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
 Technical Security Control Model With Isk Management Guide For Information Technology Systems
Technical Security Control Model With Isk Management Guide For Information Technology SystemsThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver an outstanding presentation on the topic using this Technical Security Control Model With Isk Management Guide For Information Technology Systems. Dispense information and present a thorough explanation of Technical Security, Control Model, Supporting Technical, Control Function using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Controls To Reduce The Risk Of Ransomware Security Incident Response Playbook
Security Controls To Reduce The Risk Of Ransomware Security Incident Response PlaybookMentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Present the topic in a bit more detail with this Security Controls To Reduce The Risk Of Ransomware Security Incident Response Playbook. Use it as a tool for discussion and navigation on Ransomwarem, Impacts Organization, Encrypts Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enabling Automation In Cyber Security Operations Domain Security Controls That Can Be Automated
Enabling Automation In Cyber Security Operations Domain Security Controls That Can Be AutomatedThis slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Present the topic in a bit more detail with this Enabling Automation In Cyber Security Operations Domain Security Controls That Can Be Automated. Use it as a tool for discussion and navigation on Communication, Management, Human Resources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ways To Control Cyber Security And Privacy Issues
Ways To Control Cyber Security And Privacy IssuesThe following slide illustrates some ways to monitor cybersecurity and privacy issues. It includes activities such as protecting CRM platform, keeping security system updated, modifying passwords regularly etc. Presenting our set of slides with name Ways To Control Cyber Security And Privacy Issues. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Protect CRM Platform, Keep Security System, Change Passwords Regularly.
-
 Security Automation In Information Technology Domain Security Controls That Can Be Automated
Security Automation In Information Technology Domain Security Controls That Can Be AutomatedThis slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Present the topic in a bit more detail with this Security Automation In Information Technology Domain Security Controls That Can Be Automated. Use it as a tool for discussion and navigation on Information Security, Organization, Operations Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Assessment Of It Systems Security Criteria And Control Measures For It System Vulnerabilities
Risk Assessment Of It Systems Security Criteria And Control Measures For It System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Deliver an outstanding presentation on the topic using this Risk Assessment Of It Systems Security Criteria And Control Measures For It System Vulnerabilities. Dispense information and present a thorough explanation of Management Security, Operational Security, Technical Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Assessment Of It Systems Detection And Prevention Of Management Security Controls
Risk Assessment Of It Systems Detection And Prevention Of Management Security ControlsThe following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Present the topic in a bit more detail with this Risk Assessment Of It Systems Detection And Prevention Of Management Security Controls. Use it as a tool for discussion and navigation on Prevention, Management, Security Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
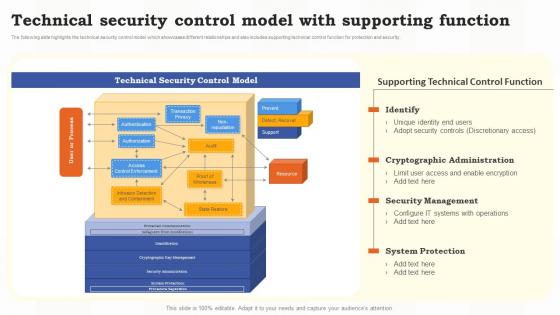 Technical Security Control Model With Supporting Function Risk Assessment Of It Systems
Technical Security Control Model With Supporting Function Risk Assessment Of It SystemsThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver an outstanding presentation on the topic using this Technical Security Control Model With Supporting Function Risk Assessment Of It Systems. Dispense information and present a thorough explanation of Technical, Security Management, System Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Domain Security Controls That Can Be Automated Security Automation To Investigate And Remediate Cyberthreats
Domain Security Controls That Can Be Automated Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Deliver an outstanding presentation on the topic using this Domain Security Controls That Can Be Automated Security Automation To Investigate And Remediate Cyberthreats. Dispense information and present a thorough explanation of Resources Security, Asset Management, Communications using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SAAS Security Controls In Powerpoint And Google Slides Cpb
SAAS Security Controls In Powerpoint And Google Slides CpbPresenting SAAS Security Controls In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like SAAS Security Controls. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Access Control In Secured Database Management System
Access Control In Secured Database Management SystemThis slide represents the block diagram representing the access control in secured database management system. It includes details related to database and security administrator, authorization system, database schemas, application programs etc. Presenting our well structured Access Control In Secured Database Management System. The topics discussed in this slide are Access Control, Secured Database, Management System. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Business Integrated Security Control For Threat Prevention
Business Integrated Security Control For Threat PreventionThis slide covers business integrated security control for threat prevention which includes Business process and security system. Introducing our Business Integrated Security Control For Threat Prevention set of slides. The topics discussed in these slides are Integrated Security, Detection, Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Business Security Recommended And Essential Control
Business Security Recommended And Essential ControlThis slide covers business security recommended and essential control which includes identifying informative asset, determining threats, acquiring strategic information and continuously evaluating security report. Introducing our Business Security Recommended And Essential Control set of slides. The topics discussed in these slides are Essential, Recommended Controls, Implement. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Business Strategy And Attributes Mapping For Security Controls
Business Strategy And Attributes Mapping For Security ControlsThis slide covers business strategy and attributes mapping for security controls which includes mapping business requirements, evaluating risk and product with service mapping. Introducing our Business Strategy And Attributes Mapping For Security Controls set of slides. The topics discussed in these slides are Governance, Business Strategy, Security Controls. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Domain Security Controls That Can Be Automated Security Orchestration Automation And Response Guide
Domain Security Controls That Can Be Automated Security Orchestration Automation And Response GuideThis slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Increase audience engagement and knowledge by dispensing information using Domain Security Controls That Can Be Automated Security Orchestration Automation And Response Guide. This template helps you present information on one stages. You can also present information on Security Policy, Communication And Operations, Security Controls using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Role Based Access Control RBAC Securities Icon
Role Based Access Control RBAC Securities IconIntroducing our premium set of slides with name Role Based Access Control RBAC Securities Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Control, Securities Icon, Audiences Attention. So download instantly and tailor it with your information.
-
 Security Controls To Reduce The Risk Of Ransomware Cybersecurity Incident And Vulnerability
Security Controls To Reduce The Risk Of Ransomware Cybersecurity Incident And VulnerabilityMentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Deliver an outstanding presentation on the topic using this Security Controls To Reduce The Risk Of Ransomware Cybersecurity Incident And Vulnerability. Dispense information and present a thorough explanation of Gains Access, Takes Control, Impacts Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Controls To Reduce The Risk Of Ransomware Upgrading Cybersecurity With Incident Response Playbook
Security Controls To Reduce The Risk Of Ransomware Upgrading Cybersecurity With Incident Response PlaybookMentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Present the topic in a bit more detail with this Security Controls To Reduce The Risk Of Ransomware Upgrading Cybersecurity With Incident Response Playbook. Use it as a tool for discussion and navigation on Ransomware, Informational Impact, Recoverability Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Nist Framework Process For Security Control Selection
Nist Framework Process For Security Control SelectionMentioned Slide Showcases The Process To Choose Security Controls Based On Nist Security Control. It Include Steps Like Security Categorization Using Fips 199, Identify Baseline Security Controls, Tailoring Baseline Security Controls And Document The Control Selection Process. Presenting Our Well Structured Nist Framework Process For Security Control Selection. The Topics Discussed In This Slide Are Framework, Process, Categorization. This Is An Instantly Available Powerpoint Presentation That Can Be Edited Conveniently. Download It Right Away And Captivate Your Audience.
-
 WIFI Security Access Control Colored Icon In Powerpoint Pptx Png And Editable Eps Format
WIFI Security Access Control Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a visual representation of WIFI security. It features a shield with a lock to represent the protection of your WIFI network. It is a great visual aid for presentations on WIFI security and can be used to highlight the importance of keeping your network secure.
-
 WIFI Security Access Control Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
WIFI Security Access Control Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is perfect for illustrating the concept of WIFI Security. It features a simple, modern design that is sure to make your presentation stand out. It is perfect for any project related to WIFI Security, from educational materials to corporate presentations.
-
 Mobile Access Control Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Mobile Access Control Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon will provide a visually engaging representation of Mobile Security. It is a great addition to any presentation and can be used to demonstrate the importance of mobile security and the various measures that can be taken to protect mobile devices.
-
 Mobile Access Control Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Mobile Access Control Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Mobile Security is perfect for presentations on the importance of mobile security. It is a simple yet effective way to illustrate the need for secure mobile practices.
-
 Control Protect Secure Account In Powerpoint And Google Slides Cpb
Control Protect Secure Account In Powerpoint And Google Slides CpbPresenting our Control Protect Secure Account In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Control Protect Secure Account. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 3 Key Areas For Document Management Security Controls
3 Key Areas For Document Management Security ControlsThis slide presents the key areas of security control that enable companies to manage information access and permissions. It includes cryptography, best practice guidelines, compliance certifications and attestations. Introducing our premium set of slides with 3 Key Areas For Document Management Security Controls. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Best Practice Guidelines, Cryptography, Compliance Certifications. So download instantly and tailor it with your information.
-
 Types Of It Security Control Framework
Types Of It Security Control FrameworkThis slide presents a framework showing multiple types of IT cyber security control to protect system integrity and information. It includes key components such as COBIT, CIS control, NIST cyber security, HITRUST CSF, NIST SP model and ISO series. Presenting our set of slides with Types Of It Security Control Framework. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Framework, Framework Options.
-
 W24 Software Defined Networking Architecture Control Layer SDN Security IT
W24 Software Defined Networking Architecture Control Layer SDN Security ITThis slide outlines the control layer of SDN architecture, which is the second layer in the model. It also includes its functions, such as receiving commands and requirements from the application layer and forwarding them to the networking components. Present the topic in a bit more detail with this W24 Software Defined Networking Architecture Control Layer SDN Security IT. Use it as a tool for discussion and navigation on Software, Networking, Layer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Hazard Prevention And Control Best Practices For Workplace Security
Hazard Prevention And Control Best Practices For Workplace SecurityThis slide highlights the hard prevention and control measures which includes check control options, select control plan, measure non routine operations and implement hazard controls.Increase audience engagement and knowledge by dispensing information using Hazard Prevention And Control Best Practices For Workplace Security. This template helps you present information on four stages. You can also present information on Check International, Control Measures, Complex Workplace using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Safety Guidelines To Control Chemical Hazards At Workplace Best Practices For Workplace Security
Safety Guidelines To Control Chemical Hazards At Workplace Best Practices For Workplace SecurityThe following slide showcases the steps or measures for chemical hazards at organization. It showcase five ways to deal elimination, substitution, engineering controls, administrative controls and PPE.Increase audience engagement and knowledge by dispensing information using Safety Guidelines To Control Chemical Hazards At Workplace Best Practices For Workplace Security. This template helps you present information on five stages. You can also present information on Safety Glasses, Safety Googles, Safety Helmet using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Safety Guidelines To Control Fire At Workplace Best Practices For Workplace Security
Safety Guidelines To Control Fire At Workplace Best Practices For Workplace SecurityThis slide highlights the measures to control fire at workplace which includes steps such as raise the alarm, alert everyone, fight fire and evacuate from the worksite.Introducing Safety Guidelines To Control Fire At Workplace Best Practices For Workplace Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Replace Hazard, Physically Remove Hazard, Isolate People Hazard, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Access Control Policy Icon
Cyber Security Access Control Policy IconPresenting our set of slides with Cyber Security Access Control Policy Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security, Access Control Policy Icon.
-
 Systems Access Control Security Policy
Systems Access Control Security PolicyThis slide shows Access Control Policy for computer system and laptops of firm to ensure security of business data. It include sections such as Policy risks, Policy Key points, Information and security standards etc. Introducing our Systems Access Control Security Policy set of slides. The topics discussed in these slides are Systems, Security, Policy. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Controlling Insider And Outsider Cyber Security Threats
Controlling Insider And Outsider Cyber Security ThreatsThis slide brings forth strategic dimensions to control insider and outsider cyber security threats by business managers in order to bring about efficiency in business operations. Key steps covered are identify, monitor, encrypt, restrict, train and extend Presenting our set of slides with Controlling Insider And Outsider Cyber Security Threats. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Monitor, Encrypt.
-
 Employee Training To Control Cyber Security Threats
Employee Training To Control Cyber Security ThreatsFollowing slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email Presenting our set of slides with Employee Training To Control Cyber Security Threats. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Document Management, Internet Links.
-
 Cyber Security Risk Analysis And Control Matrix
Cyber Security Risk Analysis And Control MatrixThe purpose of this slide is to define the level of hazards and their severity in cybersecurity management along with priority levels 15 to manage risks. This is categorized as certain, likely, possible, unlikely, and rare Introducing our Cyber Security Risk Analysis And Control Matrix set of slides. The topics discussed in these slides are Consider, Hazardous Event. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key Access Security Control Models Implementation Of ICT Strategic Plan Strategy SS
Key Access Security Control Models Implementation Of ICT Strategic Plan Strategy SSThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role based access control and attributes based access control.Deliver an outstanding presentation on the topic using this Key Access Security Control Models Implementation Of ICT Strategic Plan Strategy SS. Dispense information and present a thorough explanation of Discretionary Access, Mandatory Access, Access Granted using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Mitigation Security Controls In Powerpoint And Google Slides Cpb
Risk Mitigation Security Controls In Powerpoint And Google Slides CpbPresenting our Risk Mitigation Security Controls In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Risk Mitigation Security Controls. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Access Control Security Risks Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Access Control Security Risks Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis PowerPoint icon depicts a shield with a red warning sign, representing the security risks associated with digital data. It is a great visual aid for presentations on cyber security, risk management, and data protection.
-
 Access Control Security Risks Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Access Control Security Risks Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon on Security Risks is a great visual aid for presentations on cyber security and data protection. It features a silhouette of a person in a protective stance, illustrating the need to be aware of potential risks.
-
 Cloud Security Standards And Control Frameworks Ppt Outline Example Introduction
Cloud Security Standards And Control Frameworks Ppt Outline Example IntroductionThis slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO 27001, ISO 27017, ISO 27018, GDPR, SOC reporting, PCI DSS, and HIPAA. Increase audience engagement and knowledge by dispensing information using Cloud Security Standards And Control Frameworks Ppt Outline Example Introduction. This template helps you present information on one stages. You can also present information on Standards Control, Frameworks, Description using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sdn Controller What Role Does Sdn Play In Customer Security
Sdn Controller What Role Does Sdn Play In Customer SecurityThis slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information. Introducing Sdn Controller What Role Does Sdn Play In Customer Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Provides Several, Cybersecurity Advantages, using this template. Grab it now to reap its full benefits.
-
 Software Defined Networking And Security Sdn Controller
Software Defined Networking And Security Sdn ControllerThis slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Deliver an outstanding presentation on the topic using this Software Defined Networking And Security Sdn Controller. Dispense information and present a thorough explanation of Threat Defense, SDN Telemetry using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Access Control Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Access Control Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon depicts a shield with a checkmark, symbolizing that your account is safe and secure. It is perfect for presentations on security, privacy, and protection of data. The icon is bright and colourful, adding a modern touch to your slides.
-
 Access Control Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Access Control Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon is perfect for illustrating a secure and protected account. It features a padlock icon with a checkmark, indicating that the account is safe and secure. Use this icon to show that your account is safe and secure.
-
 Security Access Control Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Security Access Control Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon depicts a Sensor Lock, an electronic device used to secure a door or gate. It is easy to install and use, and offers reliable security with advanced features. It is the ideal choice for residential, commercial and industrial applications.
-
 Security Access Control Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Security Access Control Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon on Sensor Lock is perfect for adding a modern, professional touch to presentations. It features a sleek, black and white design with a sensor lock graphic, making it ideal for security-related topics.
-
 Improved Access Control Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Improved Access Control Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon represents improved security. It features a padlock icon in a vibrant blue and green colour scheme, symbolising a secure and reliable system. Perfect for presentations on data protection and cyber security.
-
 Improved Access Control Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Improved Access Control Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon on Improved Security is perfect for presentations on data security. It features a shield with a lock, representing strong protection of sensitive information. Use this icon to illustrate the importance of secure data storage and transmission.
-
 Data Security Encryption Access Control Illustration
Data Security Encryption Access Control IllustrationThis coloured PowerPoint Illustration depicts a data security concept, with a padlock and a key to represent secure data protection. It is ideal for presentations on data protection, cyber security, and other related topics.
-
 Security Access Control Measures Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Security Access Control Measures Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon depicts a shield with a lock, representing security measures. Its perfect for presentations on data protection, cyber security, and other related topics. The icon is bright and vibrant, making it stand out and draw attention to your message.
-
 Security Access Control Measures Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Security Access Control Measures Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon is the perfect visual representation of security measures, providing a simple and effective way to communicate the importance of safety and security to any audience. It is an essential tool for any presentation on security topics.
-
 Key Access Security Control Models ICT Strategic Framework Strategy SS V
Key Access Security Control Models ICT Strategic Framework Strategy SS VThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role based access control and attributes based access control, Present the topic in a bit more detail with this Key Access Security Control Models ICT Strategic Framework Strategy SS V. Use it as a tool for discussion and navigation on Discretionary Access, Mandatory Access, Role Based Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Billing customer security e source control circular process with icon in centre
Billing customer security e source control circular process with icon in centrePresenting billing customer security e source control circular process with icon in centre. This is a billing customer security e source control circular process with icon in centre. This is a seven stage process. The stages in this process are billing process, billing procedure, billing cycle.
-
 Management experience process control advanced training privacy security
Management experience process control advanced training privacy securityPresenting this set of slides with name - Management Experience Process Control Advanced Training Privacy Security. This is an editable four graphic that deals with topics like Management Experience, Process Control, Advanced Training, Privacy Security to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Application environment security controls application development security information accuracy
Application environment security controls application development security information accuracyPresenting this set of slides with name - Application Environment Security Controls Application Development Security Information Accuracy. This is an editable seven stages graphic that deals with topics like Application Environment Security Controls, Application Development Security, Information Accuracy to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Select full wipe security enforcement access control certificate management
Select full wipe security enforcement access control certificate managementPresenting this set of slides with name - Select Full Wipe Security Enforcement Access Control Certificate Management. This is an editable five stages graphic that deals with topics like Select Full Wipe, Security Enforcement, Access Control, Certificate Management to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Information security strategy activities controls monitor measure
Information security strategy activities controls monitor measurePresenting this set of slides with name - Information Security Strategy Activities Controls Monitor Measure. This is a three stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.





