Powerpoint Templates and Google slides for Security Configuration Management
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Security Configuration Management Powerpoint Ppt Template Bundles
Security Configuration Management Powerpoint Ppt Template BundlesDeliver a lucid presentation by utilizing this Security Configuration Management Powerpoint Ppt Template Bundles. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Security Configuration Management Impact,Cyber Network Security Configuration Management,Checklist Security Configuration Management,Techniques Of Security Configuration Management,Information Security Configuration Framework. All the Seventeen slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 Business Security Configuration Management Icon
Business Security Configuration Management IconPresenting our well structured Business Security Configuration Management Icon. The topics discussed in this slide are Business Security Configuration Management Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Advantages In Configuration Management
Cyber Security Advantages In Configuration ManagementThis slide formulates the benefits of cyber security in configuration management. Its use is to control the data better and increase visibility. Introducing our premium set of slides with name Cyber Security Advantages In Configuration Management. Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Better Control Of Data, Better Understanding Of Environment, Produce Efficiency, Visibility. So download instantly and tailor it with your information.
-
 Effective Security Configuration Management Tools
Effective Security Configuration Management ToolsThis slide includes various tools for managing security configuration in the organisation. Its objective is to use the best available tool which is feature rich. This slide showcases tool such as solar winds, auvik, Microsoft intune, etc. Presenting our well structured Effective Security Configuration Management Tools. The topics discussed in this slide are Software, Endpoint Central Manage Engine, Network Configuration Manager. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Essential Checklist For Security Configuration Management
Essential Checklist For Security Configuration ManagementThis slide depicts the important components required for security configuration management. This slide suggest disabling unnecessary accounts, changing passwords, authentication, best practices, etc. Presenting our well structured Essential Checklist For Security Configuration Management. The topics discussed in this slide are Disable Unnecessary Accounts, Change Default Passwords, Remove Unnecessary Software. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
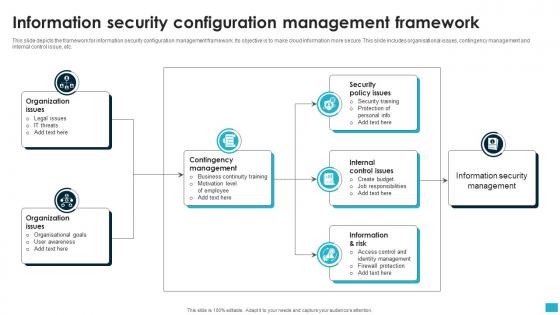 Information Security Configuration Management Framework
Information Security Configuration Management FrameworkThis slide depicts the framework for information security configuration management framework. Its objective is to make cloud information more secure. This slide includes organisational issues, contingency management and internal control issue, etc. Introducing our premium set of slides with name Information Security Configuration Management Framework. Ellicudate the Seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Organization Issues, Contingency Management, Internal Control Issues. So download instantly and tailor it with your information.
-
 Information Security Configuration Management Phases
Information Security Configuration Management PhasesThis slide depicts a set of activities for securing configuration management in phases. Its objective is to support information system and avoid organisational risk. This slide includes planning, implementing configuration, configuration changes, monitoring, etc. Introducing our premium set of slides with name Information Security Configuration Management Phases. Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Planning, Controlling Configuration Changes, Monitoring. So download instantly and tailor it with your information.
-
 Monitor Security Configuration Management System
Monitor Security Configuration Management SystemThis slide depicts the security configuration management flow. Its aim is to manage the configuration system efficiently. This slide includes publisher, automatic checks, configuration guide, rule implementation, administrator monitoring, etc. Presenting our well structured Monitor Security Configuration Management System. The topics discussed in this slide are Administrator, System Testing, Legend, Implement Rules. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Configuration Management Flowchart
Security Configuration Management FlowchartThis slide depicts the flowchart for security configuration management. Its objective is to analyse the changes and report the new requirements. This slide includes taking up new changes, verifying, generating new ECR, etc. Introducing our premium set of slides with name Security Configuration Management Flowchart. Ellicudate the One stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Configuration Management, Cm Database. So download instantly and tailor it with your information.
-
 Security Configuration Management Impact Analysis
Security Configuration Management Impact AnalysisThis slide showcases the security configuration management impact analysis. Its objective is to identify vulnerability and change the configuration to reduce risk. This slide includes understanding change, assess risk, evaluate control, deploy countermeasures, etc. Introducing our premium set of slides with name Security Configuration Management Impact Analysis. Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Assess Risk, Identify Vulnerability, Evaluate Impact On Controls. So download instantly and tailor it with your information.
-
 Security Configuration Management Solutions In Cyber Network
Security Configuration Management Solutions In Cyber NetworkThis slide depicts the management solution for security configuration in cyber network. Its objective is to find the weak points of the company and fix them fast to safeguard them from attacks. This slide includes vulnerability assessment, remediation phase, etc. Introducing our premium set of slides with name Security Configuration Management Solutions In Cyber Network. Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Vulnerability, Automated Remediation, Configuration Assessment. So download instantly and tailor it with your information.
-
 Security Configuration Management User Roles
Security Configuration Management User RolesThis slide showcases the roles assigned to users for security configuration management. Its aim is to record the activities of the configuration management users. This slide includes auditor, administrator, configuration, tools, etc. Presenting our well structured Security Configuration Management User Roles. The topics discussed in this slide are Configuration Administrator, Configuration Auditor, Configuration Manager. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Protection And Configuration Management Icon
Security Protection And Configuration Management IconIntroducing our premium set of slides with name Security Protection And Configuration Management Icon. Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Protection And Configuration Management Icon. So download instantly and tailor it with your information.
-
 Steps For Security Configuration Management Process
Steps For Security Configuration Management ProcessThis slide depicts the process for security configuration management. Its objective is to harden the system to perform and control the tasks. This slide includes security requirement, identify, control, establish process, etc. Introducing our premium set of slides with name Steps For Security Configuration Management Process. Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify, Control, Develop And Adapt, Establish Process. So download instantly and tailor it with your information.
-
 Steps In Security Configuration Management System
Steps In Security Configuration Management SystemThis slide depicts the security configuration management steps. Its aim Is to discover assets, solve problem, initiate baseline and make changes in it. This slide includes discovery of asset, baseline device, solve problem and make changes. Introducing our premium set of slides with name Steps In Security Configuration Management System. Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Discover Asset, Initiate Baseline, Make Changes, Solve Problem. So download instantly and tailor it with your information.
-
 Techniques Of Including Security Configuration Management
Techniques Of Including Security Configuration ManagementThis slide depicts the techniques to handle security configuration management in an enterprise. Its aim is to reduce security vulnerabilities. This slide includes monitoring, endpoint, configuration, avoid jams, etc. Introducing our premium set of slides with name Techniques Of Including Security Configuration Management. Ellicudate the Seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Configure Remote Endpoints, Monitor Results, Operating System Endpoint. So download instantly and tailor it with your information.
-
 Determine Various Configuration Android Device Security Management
Determine Various Configuration Android Device Security ManagementThis slide provides information regarding various configuration profiles using MDM technology such as basics, email accounts, internet and additional settings. Increase audience engagement and knowledge by dispensing information using Determine Various Configuration Android Device Security Management. This template helps you present information on four stages. You can also present information on Email Accounts, Internet Settings, Additional Settings using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application security effectiveness change management configuration management malicious software
Application security effectiveness change management configuration management malicious softwarePresenting this set of slides with name - Application Security Effectiveness Change Management Configuration Management Malicious Software. This is an editable four stages graphic that deals with topics like Application Security Effectiveness, Change Management, Configuration Management, Malicious Software to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Manager configuration specify security needs manage project risk
Manager configuration specify security needs manage project riskPresenting this set of slides with name - Manager Configuration Specify Security Needs Manage Project Risk. This is an editable eight graphic that deals with topics like Manager Configuration, Specify Security Needs, Manage Project Risk to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Application environment security controls configuration management malicious software
Application environment security controls configuration management malicious softwarePresenting this set of slides with name - Application Environment Security Controls Configuration Management Malicious Software. This is an editable three stages graphic that deals with topics like Application Environment Security Controls, Configuration Management, Malicious Software to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security configuration management compliance ppt powerpoint presentation gallery cpb
Security configuration management compliance ppt powerpoint presentation gallery cpbPresenting this set of slides with name Security Configuration Management Compliance Ppt Powerpoint Presentation Gallery Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Security Configuration Management Compliance to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.



