Powerpoint Templates and Google slides for Security Component
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Network Security A Cybersecurity Component Training Ppt
Network Security A Cybersecurity Component Training PptPresenting Network Security a Cybersecurity Component. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Application Security A Cybersecurity Component Training Ppt
Application Security A Cybersecurity Component Training PptPresenting Application Security a Cybersecurity Component. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 End User Security A Cybersecurity Component Training Ppt
End User Security A Cybersecurity Component Training PptPresenting End User Security a Cybersecurity Component. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Operational Security A Cybersecurity Component Training Ppt
Operational Security A Cybersecurity Component Training PptPresenting Operational Security a Cybersecurity Component. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content and present it with confidence.
-
 Information Security A Cybersecurity Component Training Ppt
Information Security A Cybersecurity Component Training PptPresenting Information Security a Cybersecurity Component. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content and present it with confidence.
-
 Information Security As A Component Of Cybersecurity Training Ppt
Information Security As A Component Of Cybersecurity Training PptPresenting Information Security as a Component of Cybersecurity. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Application Security As A Component Of Cybersecurity Training Ppt
Application Security As A Component Of Cybersecurity Training PptPresenting Application Security as a Component of Cybersecurity. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Network Security As A Component Of Cybersecurity Training Ppt
Network Security As A Component Of Cybersecurity Training PptPresenting Network Security as a Component of Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 End User Security As A Component Of Cybersecurity Training Ppt
End User Security As A Component Of Cybersecurity Training PptPresenting End User Security as a Component of Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Key Components Of Endpoint Security Training Ppt
Key Components Of Endpoint Security Training PptPresenting Key Components of Endpoint Security. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Operational Security As A Component Of Cybersecurity Training Ppt
Operational Security As A Component Of Cybersecurity Training PptPresenting Operational Security as a Component of Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Security framework analysis management components organization assessment
Security framework analysis management components organization assessmentIf you require a professional template with great design, then this Security Framework Analysis Management Components Organization Assessment is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using eleven slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Working Components Of Secure Web Gateway Architecture Network Security Using Secure Web Gateway
Working Components Of Secure Web Gateway Architecture Network Security Using Secure Web GatewayThis slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc. Increase audience engagement and knowledge by dispensing information using Working Components Of Secure Web Gateway Architecture Network Security Using Secure Web Gateway. This template helps you present information on five stages. You can also present information on Application Control, Website Content Inspection, Gateway Architecture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 External Components Of Zero Trust Network Architecture Zero Trust Security Model
External Components Of Zero Trust Network Architecture Zero Trust Security ModelThis slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Deliver an outstanding presentation on the topic using this External Components Of Zero Trust Network Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Documentation, Potential using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Logical Components Of Zero Trust Architecture Zero Trust Security Model
Logical Components Of Zero Trust Architecture Zero Trust Security ModelThis slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. Deliver an outstanding presentation on the topic using this Logical Components Of Zero Trust Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Components, Architecture, Threat Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Storage Area Network San Key Components Of Storage Area Network Security
Storage Area Network San Key Components Of Storage Area Network SecurityThis Slide Outlines The Main Elements Of The SAN Security Mechanism. The Purpose Of This Slide Is To Highlight The Primary Components Of Storage Area Network Security, Including Digital Certificates, Network Protocols, Backup, Access Control, And Employee Training. Increase Audience Engagement And Knowledge By Dispensing Information Using Storage Area Network San Key Components Of Storage Area Network Security. This Template Helps You Present Information On Five Stages. You Can Also Present Information On Digital Certificates, Network Protocols, Access Controls Using This PPT Design. This Layout Is Completely Editable So Personaize It Now To Meet Your Audiences Expectations.
-
 Grid Computing Architecture Key Components Of Grid Computing Security
Grid Computing Architecture Key Components Of Grid Computing SecurityThis slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Introducing Grid Computing Architecture Key Components Of Grid Computing Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security Component, Grid Computing Network, Protects The System, Authentication And Authorization Processes, using this template. Grab it now to reap its full benefits.
-
 Key Components Of A Security Management Plan
Key Components Of A Security Management PlanThis slide showcases the critical components of a business security plan. This slide aims to help the business management develop an effective security plan in case of emergencies or uncertainties to avoid financial losses. It includes elements such as risk assessments, security policy development, training and awareness of employees, etc.Presenting our set of slides with Key Components Of A Security Management Plan. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Develop Suitable, Strategies Procedures, Customized Business.
-
 Key Components Of Data Security Breach Management Plan
Key Components Of Data Security Breach Management PlanThis slide showcases the critical components of a business security breach management plan. This slide aims to help the business effectively manage a data security breach to prevent financial loss, market share loss, or reputational damage.Introducing our premium set of slides with Key Components Of Data Security Breach Management Plan. Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Prevent Identity, Credit Report Monitoring, Review Security Measures. So download instantly and tailor it with your information.
-
 Information Security Strategic Plan Components
Information Security Strategic Plan ComponentsThis slide showcase major components of information security strategic plan to reduce cyber security incident threat .It involves security awareness, risk prevention, data management, network security and control and monitor security measures. Presenting our set of slides with Information Security Strategic Plan Components. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Awareness, Data Management, Monitor Security Measures.
-
 Components Of Effective Enterprise Security System
Components Of Effective Enterprise Security SystemThis slide represents enterprise security system components for effectiveness. This further includes components such as security cameras, video monitoring, smartphone alerts, manage employee access. Presenting our set of slides with Components Of Effective Enterprise Security System. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Cameras, Video Monitoring, Smartphone Alerts.
-
 IOT Solution Components In Cyber Security System
IOT Solution Components In Cyber Security SystemThis slide highlights cyber security system components for IOT solutions. This includes secure device, secure communication, secured cloud and further includes messaging control and device integrated connections. Presenting our set of slides with IOT Solution Components In Cyber Security System. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure Device, Secure Communication, Secured Cloud.
-
 Cloud Access Security Broker CASB V2 Architectural Components Ppt Gallery Microsoft
Cloud Access Security Broker CASB V2 Architectural Components Ppt Gallery MicrosoftThis slide outlines the main components of Cloud Access Security Broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Architectural Components Ppt Gallery Microsoft. Dispense information and present a thorough explanation of Cloud Access Security, Broker Architectural, Connectivity Gateway, Software As A Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 CASB Deployment With Optional Components Pricing
Cloud Access Security Broker CASB V2 CASB Deployment With Optional Components PricingThis slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 CASB Deployment With Optional Components Pricing. Dispense information and present a thorough explanation of Data Security Subscription, Threat Protection Subscription, Data Retention, Customer Relationship Admins using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 CASB Deployment With Standard Components Pricing
Cloud Access Security Broker CASB V2 CASB Deployment With Standard Components PricingThis slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 CASB Deployment With Standard Components Pricing. Use it as a tool for discussion and navigation on Pricing Of Classic Elements, Components Include Visibility, Threat Protection, Data Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Key Components Of Internet Protocol Security
Encryption Implementation Strategies Key Components Of Internet Protocol SecurityThe purpose of this slide is to discuss the main components of internet protocol security IPsec architecture. These three components are encapsulating security payload ESP, authentication header AH, and internet key exchange IKE. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Key Components Of Internet Protocol Security. Dispense information and present a thorough explanation of Data Integrity, Encryption, Anti Replay, Payload Authentication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Web Gateway SWG Functional Components Cloud Security Model
Secure Web Gateway SWG Functional Components Cloud Security ModelThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Present the topic in a bit more detail with this Secure Web Gateway SWG Functional Components Cloud Security Model. Use it as a tool for discussion and navigation on Components, Prevention, Inspection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Secure Web Gateway Swg Functional Components
Sase Security Secure Web Gateway Swg Functional ComponentsThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Present the topic in a bit more detail with this Sase Security Secure Web Gateway Swg Functional Components. Use it as a tool for discussion and navigation on Functional, Components, Enforcement. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Swg Functional Components Secure Access Service Edge Sase
Secure Swg Functional Components Secure Access Service Edge SaseThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Deliver an outstanding presentation on the topic using this Secure Swg Functional Components Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Demonstrate, Enforcement, Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Web Gateway SWG Functional Components SASE Network Security
Secure Web Gateway SWG Functional Components SASE Network SecurityThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Present the topic in a bit more detail with this Secure Web Gateway SWG Functional Components SASE Network Security. Use it as a tool for discussion and navigation on Policy, Prevention, Malware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Components Of Zero Trust Security Architecture
Components Of Zero Trust Security ArchitectureThis slide depicts the critical elements of a zero trust network architecture. The purpose of this slide is to help the business establish network security by safeguarding all components. It includes component such as zero trust architecture, micro segmentation, etc. Presenting our well structured Components Of Zero Trust Security Architecture. The topics discussed in this slide are Access Controls, Zero Trust Network Architecture, Real Time Monitoring. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Functional Testing Checklist To Review Key Components Hands On Blockchain Security Risk BCT SS V
Functional Testing Checklist To Review Key Components Hands On Blockchain Security Risk BCT SS VThe following slide showcases checklist for functional testing to ensure blockchain security. It includes elements such as size of blockchain, addition of blocks, data transmission, API, integration, performance and security testing, etc. Present the topic in a bit more detail with this Functional Testing Checklist To Review Key Components Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Parameters, Description, Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Components Cyber Security Strategy In Powerpoint And Google Slides Cpb
Components Cyber Security Strategy In Powerpoint And Google Slides CpbPresenting Components Cyber Security Strategy In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Components Cyber Security Strategy. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Components Of Virtual Infrastructure For Effective Data Management And Security
Components Of Virtual Infrastructure For Effective Data Management And SecurityThis slide represents key components of virtual infrastructure that help businesses with data security and disaster management. It includes various components such as virtualized computing, virtualized storage, management solutions, and virtualized security. Introducing our premium set of slides with Components Of Virtual Infrastructure For Effective Data Management And Security. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Virtualized Compute, Virtualized Networking Security, Virtualized Storage. So download instantly and tailor it with your information.
-
 Components Of 5G Security Architecture To Prevent Cyberattacks
Components Of 5G Security Architecture To Prevent CyberattacksThis slide depicts the components of a 5 G security architecture utilized for preventing cyber attacks. The purpose of this slide is to help the business safeguard its networks through proper implementation of critical components such as network security, scaling security, etc. Presenting our set of slides with Components Of 5G Security Architecture To Prevent Cyberattacks. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network, Hardware, Security.
-
 Cloud Access Security Broker Architectural Components Next Generation CASB
Cloud Access Security Broker Architectural Components Next Generation CASBThis slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Architectural Components Next Generation CASB Dispense information and present a thorough explanation of Secondary Enterprise Core, Platform As A Service, Connectivity Gateway using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Key Components Of Firewall Management System
Firewall Network Security Key Components Of Firewall Management SystemThis slide talks about the important elements of the firewall management system. The purpose of this slide is to showcase the vital components of a firewall management system, such as a graphical interface, policy control, threat management, device management, third-party integrations, and scalability. Introducing Firewall Network Security Key Components Of Firewall Management System to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Secure Access Service, Artificial Intelligence using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Key Components Of Firewall Protection System
Firewall Network Security Key Components Of Firewall Protection SystemThis slide talks about the primary elements of a firewall security system. The purpose of this slide is to showcase the different components of a firewall, such as network policy, advanced authentication, packet filtering, and application gateway. Present the topic in a bit more detail with this Firewall Network Security Key Components Of Firewall Protection System Use it as a tool for discussion and navigation on Misconfiguration, Software Vulnerabilities, Missing Firewall Policy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Secure Web Gateway Swg Functional Components
SD WAN Model Secure Web Gateway Swg Functional ComponentsThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Deliver an outstanding presentation on the topic using this SD WAN Model Secure Web Gateway Swg Functional Components. Dispense information and present a thorough explanation of Data Loss Prevention, Policy Enforcement, Secure Web Gateway, Functional Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Secure Web Gateway SWG Functional Components
Sase Model Secure Web Gateway SWG Functional ComponentsThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Present the topic in a bit more detail with this Sase Model Secure Web Gateway SWG Functional Components. Use it as a tool for discussion and navigation on Components, Working, Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Components Of Internet Protocol Security Encryption For Data Privacy In Digital Age It
Key Components Of Internet Protocol Security Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to discuss the main components of Internet Protocol Security IPsec architecture. These three components are Encapsulating Security Payload ESP, Authentication Header AH, and Internet Key Exchange IKE. Deliver an outstanding presentation on the topic using this Key Components Of Internet Protocol Security Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Authentication Header, Internet Key Exchange, Encapsulating Security Payload using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Internet Gateway Security IT Working Components Of Secure Web Gateway
Internet Gateway Security IT Working Components Of Secure Web GatewayThis slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc. Introducing Internet Gateway Security IT Working Components Of Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Traffic Inspection, URL Filtering, Application Control, Website Content Inspection, Secure Socket Layer SSL Inspection, using this template. Grab it now to reap its full benefits.
-
 Components Of Business Security Incident Response Plans
Components Of Business Security Incident Response PlansThis slide highlights the components of business security incident response plan. The purpose of this slide is to help the business develop effective security incident response plans through the use of components use as incident taxonomy, data classification frameworks, etc. Introducing our premium set of slides with Components Of Business Security Incident Response Plans. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Operating Models, Performance Objectives, Incident Taxonomy. So download instantly and tailor it with your information.
-
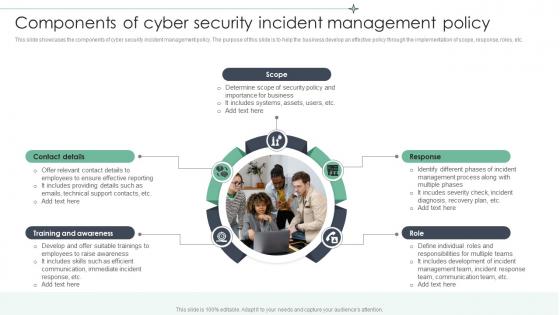 Components Of Cyber Security Incident Management Policy
Components Of Cyber Security Incident Management PolicyThis slide showcases the components of cyber security incident management policy. The purpose of this slide is to help the business develop an effective policy through the implementation of scope, response, roles, etc. Presenting our set of slides with Components Of Cyber Security Incident Management Policy. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Contact Details, Training And Awareness, Includes Systems.
-
 Effective Components Of Csirt Cyber Security
Effective Components Of Csirt Cyber SecurityThis slide highlights necessary components of CSIRT cyber security. The main purpose of this template is to showcase mitigation of potential threats. This includes regular security assessment, collaboration, post incident review, etc. Presenting our set of slides with Effective Components Of Csirt Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Assessment, External Entities, Incident Review.
-
 Key Components Of Host Server Security
Key Components Of Host Server SecurityFollowing slide highlights components and functions for host security server console, also including components such as cloud protection center, management console and agent. Introducing our Key Components Of Host Server Security set of slides. The topics discussed in these slides are Cloud Protection Center, Management Console, Server Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Essential EDR Capabilities Security Components
Essential EDR Capabilities Security ComponentsThis slide showcases EDR capabilities including components, authorized head, impact, status, and improvement areas. Presenting our well structured Essential EDR Capabilities Security Components. The topics discussed in this slide are Behavioral Analytics, Actionable Threat Intelligence, Managed Threat Hunting. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Key Components Of Crypto Ledger Security Model
Key Components Of Crypto Ledger Security ModelThis template aims to cover core elements of crypto ledger security model for asset protection. It covers elements such as offline storage, security, trusted display, etc. Deliver an outstanding presentation on the topic using this Key Components Of Crypto Ledger Security Model. Dispense information and present a thorough explanation of Offline Storage, Security, Trusted Display using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 CASB Deployment With Optional Components Pricing CASB Cloud Security
CASB Deployment With Optional Components Pricing CASB Cloud SecurityThis slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on. Present the topic in a bit more detail with this CASB Deployment With Optional Components Pricing CASB Cloud Security. Use it as a tool for discussion and navigation on Threat Protection Subscription, Optional Components Pricing, Annual Pricing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 CASB Deployment With Standard Components Pricing CASB Cloud Security
CASB Deployment With Standard Components Pricing CASB Cloud SecurityThis slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. Deliver an outstanding presentation on the topic using this CASB Deployment With Standard Components Pricing CASB Cloud Security. Dispense information and present a thorough explanation of Standard Components Pricing, Data Security With Salesforce, Deployment In An Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Architectural Components CASB Cloud Security
Cloud Access Security Broker Architectural Components CASB Cloud SecurityThis slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Architectural Components CASB Cloud Security. Dispense information and present a thorough explanation of Secondary Enterprise Core, Bidirectional Integration, Connectivity Gateway using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Components Of Basic Living Strategic Retirement Planning To Build Secure Future Fin SS
Components Of Basic Living Strategic Retirement Planning To Build Secure Future Fin SSThis slide shows detailed information about various elements which are included in basic living expenses for developing a compelling retirement plan. It includes components such as housing, utilities, food, etc. Present the topic in a bit more detail with this Components Of Basic Living Strategic Retirement Planning To Build Secure Future Fin SS. Use it as a tool for discussion and navigation on Transportation, Insurance, Food. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Components Of Big Data Analytics In Cyber Security
Components Of Big Data Analytics In Cyber SecurityThis slide showcases the components of big data analytics in cyber security. Its objective is to improve performance and security tactics in cyber security using big data. This includes data collection, data pre processing, data analysis, visualisation. Presenting our well structured Components Of Big Data Analytics In Cyber Security. The topics discussed in this slide are Collection, Storage, Analysis. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Key Components Of Cloud Infrastructure Security
Key Components Of Cloud Infrastructure SecurityThis slide represents the key components of cloud infrastructure security. Its aim is to manage the internet and smart devices to ensure security against threats. This slide includes network endpoint, data, authentication and security measure. Presenting our set of slides with Key Components Of Cloud Infrastructure Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication, Security, Organisation.
-
 Key Components Of Cloud Saas Cyber Security Management
Key Components Of Cloud Saas Cyber Security ManagementThis slide represents cloud SaaS cyber security management elements. It aims to focus on SaaS security posture management systems, staff training, data classification depending on security level, etc. It includes various elements such as data protection, identifying access management, etc. Presenting our set of slides with Key Components Of Cloud Saas Cyber Security Management This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Identify Access Management, Regular Pentests
-
 Global Cyber Security Policy Components
Global Cyber Security Policy ComponentsThis slide covers the key components of a National Cyber Security Strategy NCSS. The purpose of this template is to provide a succinct overview of the main pillars of the NCSS including strengthening the regulatory framework, promoting research and development, etc. Introducing our premium set of slides with Global Cyber Security Policy Components Ellicudate the Seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Regulatory Framework, Encourage Open Standards, Assurance Framework. So download instantly and tailor it with your information.
-
 Essential Components Of ATP Cyber Security
Essential Components Of ATP Cyber SecurityThis slide depicts the essential components of ATP cyber security. Its aim is to use these components to safeguard organisational system against any threats. This slide include detection of stealthy threats, software behaviour and analysis of data. Presenting our set of slides with name Essential Components Of ATP Cyber Security. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Detect Stealthy Threats, Analysis Of Data, Benign Software Behaviour.
-
 Essential Components Of Cyber Security Frameworks
Essential Components Of Cyber Security FrameworksThis slide highlights the key components of cyber security framework which includes framework core, implementation tiers, profiles and so on. Introducing Essential Components Of Cyber Security Frameworks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Framework Core, Implementation Tiers, Guides Vulnerability Reduction , using this template. Grab it now to reap its full benefits.
-
 Main Components Of Cobit Framework In Cyber Security
Main Components Of Cobit Framework In Cyber SecurityThis slide gives an overview of key components of COBIT which includes process descriptions, control objectives, maturity models and management guidelines. Increase audience engagement and knowledge by dispensing information using Main Components Of Cobit Framework In Cyber Security. This template helps you present information on five stages. You can also present information on Process Descriptions, Maturity Models, Management Guidelines, Control Objectives using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Main Components Of Endpoint Security Approach
Endpoint Security Main Components Of Endpoint Security ApproachThis slide outlines the five components of endpoint security solutions which include network control, application control, data control, etc. Introducing Endpoint Security Main Components Of Endpoint Security Approach to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Device Protection, Network Control, Application Control, Endpoint Security Approach, using this template. Grab it now to reap its full benefits.




