Powerpoint Templates and Google slides for Security Breach
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Outlook Of Social Engineering Attack Preventing Data Breaches Through Cyber Security
Outlook Of Social Engineering Attack Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Introducing Outlook Of Social Engineering Attack Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering, Employees, using this template. Grab it now to reap its full benefits.
-
 Overview Of Business Email Compromise Attack Preventing Data Breaches Through Cyber Security
Overview Of Business Email Compromise Attack Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to delineate an example of business email compromise attack. Information covered in this slide is related to the working of this attack and how it can result in loss of company reputation. Increase audience engagement and knowledge by dispensing information using Overview Of Business Email Compromise Attack Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Email, Services, Account using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of Cyber Security Awareness Course Preventing Data Breaches Through Cyber Security
Overview Of Cyber Security Awareness Course Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. Introducing Overview Of Cyber Security Awareness Course Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Course Content, Attendees, Learning Outcome, using this template. Grab it now to reap its full benefits.
-
 Preventing Data Breaches Through Cyber Security Awareness Table Of Contents
Preventing Data Breaches Through Cyber Security Awareness Table Of ContentsPresent the topic in a bit more detail with this Preventing Data Breaches Through Cyber Security Awareness Table Of Contents. Use it as a tool for discussion and navigation on Employees, Awareness Training, Cyber Security Breach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Pricing Plan Of Security Awareness Packages Preventing Data Breaches Through Cyber Security
Pricing Plan Of Security Awareness Packages Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Deliver an outstanding presentation on the topic using this Pricing Plan Of Security Awareness Packages Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Employees, Security, Awareness Packages using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Recognizing The Cyber Security Gaps Faced By Key Preventing Data Breaches Through Cyber Security
Recognizing The Cyber Security Gaps Faced By Key Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto jacking, IoT based attack, malware etc. Present the topic in a bit more detail with this Recognizing The Cyber Security Gaps Faced By Key Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Social Engineering Attack, Business Email Comprise, Iot Based Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Roles And Responsibilities Of Cyber Security Team Preventing Data Breaches Through Cyber Security
Roles And Responsibilities Of Cyber Security Team Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Introducing Roles And Responsibilities Of Cyber Security Team Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Risk Committee, Cyber Risk Manager, Security Operations Manager, using this template. Grab it now to reap its full benefits.
-
 Running Cyber Security Awareness Campaign For Employees Preventing Data Breaches Through Cyber Security
Running Cyber Security Awareness Campaign For Employees Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. Increase audience engagement and knowledge by dispensing information using Running Cyber Security Awareness Campaign For Employees Preventing Data Breaches Through Cyber Security. This template helps you present information on two stages. You can also present information on Data, Employees, Security Awareness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
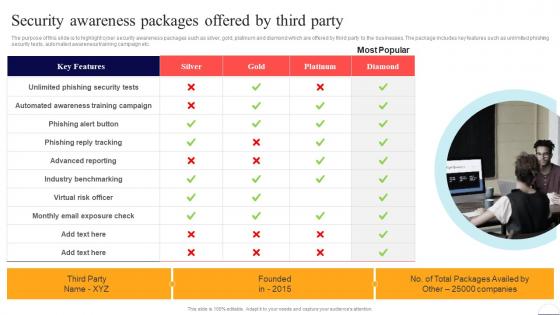 Security Awareness Packages Offered By Third Party Preventing Data Breaches Through Cyber Security
Security Awareness Packages Offered By Third Party Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. Introducing Security Awareness Packages Offered By Third Party Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Alert Button, Phishing Reply Tracking, Industry Benchmarking, using this template. Grab it now to reap its full benefits.
-
 Statistics Highlighting Lack Of Cyber Security Awareness Preventing Data Breaches Through Cyber Security
Statistics Highlighting Lack Of Cyber Security Awareness Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc. Introducing Statistics Highlighting Lack Of Cyber Security Awareness Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Employees, Confidential Data, Email, using this template. Grab it now to reap its full benefits.
-
 Strategies We Will Implement To Make Security Awareness Preventing Data Breaches Through Cyber Security
Strategies We Will Implement To Make Security Awareness Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high quality content and variety. Increase audience engagement and knowledge by dispensing information using Strategies We Will Implement To Make Security Awareness Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Gamification, Personalization, High Quality Content using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tracking Sheet To Monitor The Performance Of Employees Preventing Data Breaches Through Cyber Security
Tracking Sheet To Monitor The Performance Of Employees Preventing Data Breaches Through Cyber SecurityPresent the topic in a bit more detail with this Tracking Sheet To Monitor The Performance Of Employees Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Social Engineering Attack, Business Email Compromise, Iot Based Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Understanding The Frequency And Weightage Of Cyber Preventing Data Breaches Through Cyber Security
Understanding The Frequency And Weightage Of Cyber Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase the frequency and weightage of different cyber attacks on multiple departments. The major departments mentioned in the slide are financial, marketing, information technology IT and human resource HR. Introducing Understanding The Frequency And Weightage Of Cyber Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Financial Department, Marketing Team, IT Department, using this template. Grab it now to reap its full benefits.
-
 Various Techniques To Successfully Prevent Business Email Preventing Data Breaches Through Cyber Security
Various Techniques To Successfully Prevent Business Email Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Increase audience engagement and knowledge by dispensing information using Various Techniques To Successfully Prevent Business Email Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Sender Policy Framework, Strong Password Policy, Strong Process For Wire Transfers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Icon To Reduce Data Breaches
Cloud Security Icon To Reduce Data BreachesPresenting our set of slides with Cloud Security Icon To Reduce Data Breaches. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Security, Icon To Reduce, Data Breaches.
-
 Communicating Large Event Security Plan Breach Icon
Communicating Large Event Security Plan Breach IconIntroducing our Communicating Large Event Security Plan Breach Icon set of slides. The topics discussed in these slides are Communicating Large, Event Security, Plan Breach. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Communication Plan Matrix For Security Breach In Large Events
Communication Plan Matrix For Security Breach In Large EventsFollowing slide consists of a communication plan matrix to understand and respond to a security breach in large events. Key elements include communication plan situation, level of urgency, risk impact, communication stakeholders etc.Introducing our Communication Plan Matrix For Security Breach In Large Events set of slides. The topics discussed in these slides are Communication Plan Situation, Level Urgency, Communication Stakeholders. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Secops Icon To Prevent Security Breaches
Secops Icon To Prevent Security BreachesIntroducing our Secops Icon To Prevent Security Breaches set of slides. The topics discussed in these slides are Secops Icon, Prevent Security Breaches. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Bank Security Breached Icon Of Identity Fraud
Bank Security Breached Icon Of Identity FraudPresenting our well structured Bank Security Breached Icon Of Identity Fraud. The topics discussed in this slide are Bank Security, Breached Icon, Identity Fraud. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Breaches In Powerpoint And Google Slides Cpb
Security Breaches In Powerpoint And Google Slides CpbPresenting our Security Breaches In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Security Breaches This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber Security Breach In Powerpoint And Google Slides Cpb
Cyber Security Breach In Powerpoint And Google Slides CpbPresenting Cyber Security Breach In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Security Breach. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Massive Security Breach In Powerpoint And Google Slides Cpb
Massive Security Breach In Powerpoint And Google Slides CpbPresenting Massive Security Breach In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Massive Security Breach. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber Security Data Breach Post Crisis Communication Plan
Cyber Security Data Breach Post Crisis Communication PlanThis slides provide information about post crisis communication plan how to handle it in effective manner. It includes elements such as crisis team, fast, precise, and sincereresponses, clear line of communication and restorative services. Introducing our premium set of slides with Cyber Security Data Breach Post Crisis Communication Plan Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Crisis Team, Clear Line Of Communication, Restorative Services. So download instantly and tailor it with your information.
-
 RCA Plan For System Security Breach
RCA Plan For System Security BreachThis slide shows RCA format to address every activity in proper timeline for identifying potential risks and strategies to resolve same. It include elements such as event timeline, security breach activities and action plan, etc.Presenting our well structured RCA Plan For System Security Breach. The topics discussed in this slide are Incident Communication, Evaluate Internal, Mitigation Strategies. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Post Credit Breach Cyber Security In Powerpoint And Google Slides Cpb
Post Credit Breach Cyber Security In Powerpoint And Google Slides CpbPresenting Post Credit Breach Cyber Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Post Credit Breach Cyber Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Document Security Breach Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Document Security Breach Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Data Breach is a simple yet powerful visual representation of the risks associated with data security. It is perfect for presentations, reports, and other documents to help illustrate the dangers of data breaches. Its minimalistic design ensures it wont take away from the overall message.
-
 Document Security Breach Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Document Security Breach Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Data Breach is a simple yet powerful visual representation of the risks associated with data security. It is perfect for presentations, reports, and other documents to help illustrate the dangers of data breaches. Its minimalistic design ensures it wont take away from the overall message.
-
 Data Breach Security Communication Plan Icon
Data Breach Security Communication Plan IconPresenting our well structured Data Breach Security Communication Plan Icon. The topics discussed in this slide are Data Breach Security, Communication Plan Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Amazon map opportunities weekly report breach management social security cpb
Amazon map opportunities weekly report breach management social security cpbThis is an editable four stages graphic that deals with topics like Amazon Map, Opportunities, Weekly Report, Breach Management, Social Security to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Types security breaches ppt powerpoint presentation show slide cpb
Types security breaches ppt powerpoint presentation show slide cpbPresenting this set of slides with name Types Security Breaches Ppt Powerpoint Presentation Show Slide Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Types Security Breaches to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Solutions avoid security breach ppt powerpoint presentation portfolio designs cpb
Solutions avoid security breach ppt powerpoint presentation portfolio designs cpbPresenting this set of slides with name Solutions Avoid Security Breach Ppt Powerpoint Presentation Portfolio Designs Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Solutions Avoid Security Breachto help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Icon of hacker performing cyber attack leading to security breach
Icon of hacker performing cyber attack leading to security breachPresenting this set of slides with name Icon Of Hacker Performing Cyber Attack Leading To Security Breach. This is a three stage process. The stages in this process are Icon Of Hacker Performing Cyber Attack Leading To Security Breach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Passive active security breach response ppt powerpoint presentation file slide cpb
Passive active security breach response ppt powerpoint presentation file slide cpbPresenting this set of slides with name Passive Active Security Breach Response Ppt Powerpoint Presentation File Slide Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Passive Active Security Breach Response to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Risk management worksheet security breach ppt powerpoint outline
Risk management worksheet security breach ppt powerpoint outlineThe risk management worksheet will help in keeping the track of various issues concerns that are existing in the firm by looking at the initial level of risk associated with them and the residual risk that is the amount of risk which remains after the inherited risk which the firm has tried to reduce through risk control measures. Presenting this set of slides with name Risk Management Worksheet Security Breach Ppt Powerpoint Outline. The topics discussed in these slides are Risk Management, Worksheet Security, Breach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Developing firewall to prevent human error for cyber security breaches
Developing firewall to prevent human error for cyber security breachesPresenting this set of slides with name Developing Firewall To Prevent Human Error For Cyber Security Breaches. The topics discussed in these slide is Developing Firewall To Prevent Human Error For Cyber Security Breaches. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Data theft from computer through security breach
Data theft from computer through security breachPresenting this set of slides with name Data Theft From Computer Through Security Breach. This is a one stage process. The stage in this process is Data Theft From Computer Through Security Breach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Hackers breaching network security through cyber attack
Hackers breaching network security through cyber attackPresenting our set of slides with Web Portal For Providing Job Vacancies Alerts. This exhibits information on two stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Web Portal For Providing Job Vacancies Alerts.
-
 Cyber information security laws breaching ppt powerpoint presentation model background image cpb
Cyber information security laws breaching ppt powerpoint presentation model background image cpbPresenting Cyber Information Security Laws Breaching Ppt Powerpoint Presentation Model Background Image Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both 4.3 and 16.9 aspect ratios. It is also a useful set to elucidate topics like Cyber Information Security Laws Breaching. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cloud computing security breaches ppt powerpoint presentation portfolio maker cpb
Cloud computing security breaches ppt powerpoint presentation portfolio maker cpbPresenting our Cloud Computing Security Breaches Ppt Powerpoint Presentation Portfolio Maker Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Cloud Computing Security Breaches This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security breaches cloud computing ppt powerpoint presentation icon vector cpb
Security breaches cloud computing ppt powerpoint presentation icon vector cpbPresenting Security Breaches Cloud Computing Ppt Powerpoint Presentation Icon Vector Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Breaches Cloud Computing. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber security breach icon with laptop
Cyber security breach icon with laptopPresenting our set of slides with Cyber Security Breach Icon With Laptop. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Breach Icon With Laptop.
-
 Cyber security breach minimization steps
Cyber security breach minimization stepsThis slide exhibits cyber security breach minimization steps, it includes several steps such as- provide insights to all the users to not share company insights, malware attack prevention, assessment of all networks and so on. Introducing our Cyber Security Breach Minimization Steps set of slides. The topics discussed in these slides are Survey, Delivery, Breach, Affect. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data and security breach process
Data and security breach processThis slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as- link forwarding by emails, data sharing and attacking and so on. Introducing our Data And Security Breach Process set of slides. The topics discussed in these slides are Research, Stage Attack, Exfiltrate. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data breach security requirements and goals
Data breach security requirements and goalsThis slide exhibits data breach security requirement with major goals and requirements. It includes multiple section like securing cardholder data, manage vulnerability program and so on. Introducing our Data Breach Security Requirements And Goals set of slides. The topics discussed in these slides are Goals, Measures, Management, Secure Network, Product. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data security breach response plan
Data security breach response planFollowing slide exhibits data security breach response plan. It includes major elements such as-developing containment plan, hardware requirement assessment and so on. Introducing our Data Security Breach Response Plan set of slides. The topics discussed in these slides are Response Stage, Response Team, Key Questions And Tasks. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data security breach steps with customer centric approach
Data security breach steps with customer centric approachData security breach steps with customer centric approach. It includes 5 steps such as- proactive and preventive analysis, data protection as the default and so on. Presenting our set of slides with Data Security Breach Steps With Customer Centric Approach. This exhibits information on five stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Minimization, Security, Data Protection, Proactive And Preventive.
-
 Framework for security breach minimization
Framework for security breach minimizationFollowing slide exhibits framework for minimizing security breach and improving cyber security. It includes multiple sections like analyzing priorities, segmentation of identified risk, define objectives for desired results and so on. Introducing our Framework For Security Breach Minimization set of slides. The topics discussed in these slides are Current State, Assessment, Target State, Roadmap. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Major enterprise security breach incidents
Major enterprise security breach incidentsThis slide exhibits major enterprise security breach incidents . it includes multiple breaches such as staff responding to phishing mail and website application affected. Presenting our set of slides with Major Enterprise Security Breach Incidents. This exhibits information on five stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Major Enterprise Security Breach Incidents.
-
 Major security breaches in cloud computing
Major security breaches in cloud computingThis slide exhibits major security breaches in cloud computing and management. It includes multiple sections such as data visibility and control, non compliance of rules and so on. Presenting our set of slides with Major Security Breaches In Cloud Computing. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Cloud, Major Tenants, Cloud Security, Data Control, Management.
-
 Mitigation strategies to prevent security breach incidents
Mitigation strategies to prevent security breach incidentsThis side exhibits mitigation strategies to prevent security breach incidents. It includes multiple actions such as- keeping track of all personal assets, analyzing logging process security and so on. Presenting our set of slides with Mitigation Strategies To Prevent Security Breach Incidents. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Visibility, Logging, Monitoring And Alerting, Communication Management.
-
 Network security breach with response and recovery
Network security breach with response and recoveryThis slide exhibits network security breach with response and recovery .It includes multiple steps such as- identify, project, detect, respond and recover. Introducing our Network Security Breach With Response And Recovery set of slides. The topics discussed in these slides are Identify, Protect, Detect, Respond, Recover. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Organizational cyber security breach cases
Organizational cyber security breach casesThis slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting our set of slides with Organizational Cyber Security Breach Cases. This exhibits information on five stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Organizational Cyber Security Breach Cases.
-
 Process for responding to security data breach
Process for responding to security data breachThis slide exhibits process for responding to security data breach. It includes multiple steps such as- analyzing the current damage, keeping record how much damage is caused and so on. Introducing our Process For Responding To Security Data Breach set of slides. The topics discussed in these slides are Survey, Limit, Learn, Engage, Record. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security and data breach incident assessment
Security and data breach incident assessmentThis slide exhibits security and data breach incidence assessment model. It includes multiple sections such as- rules and regulations sharing with third parties, communication with incidence response team and so on. Presenting our set of slides with Security And Data Breach Incident Assessment. This exhibits information on six stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Survey, Limit, Learn, Engage, Record.
-
 Security and data breach report chart
Security and data breach report chartFollowing slide exhibits security and data breach report chart it includes major statistics such as- loss or theft of data, failure to redirect data and data posting to incorrect recipient. Introducing our Security And Data Breach Report Chart set of slides. The topics discussed in these slides are Security And Data Breach Report Chart. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security breach plan with incident topology
Security breach plan with incident topologyFollowing slide exhibits security breach plan with incident topology. It includes major steps such as- provide incidence guidance to employees, guidance for categorization and actions etc. Introducing our Security Breach Plan With Incident Topology set of slides. The topics discussed in these slides are Section, Activities. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security breach risk management model
Security breach risk management modelThis slide exhibits data breach risk management model. It includes major evaluation criteria such as- does the management has two unique credentials to perform administer activities, does the multifactor authentication is enabled for administrative access etc. Introducing our Security Breach Risk Management Model set of slides. The topics discussed in these slides are Asset, Control Topic, Evaluation Questions, Response, Threat. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security data breach incident report
Security data breach incident reportThis slide exhibits security data breach incident report. It includes multiple steps such as- report the number of personal data record lost, analyze the possible effects of personal data breaches and so on. Introducing our Security Data Breach Incident Report set of slides. The topics discussed in these slides are Consequences, Measures, Data Breach Details. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security data breach process by backdoor
Security data breach process by backdoorFollowing slide showcase how a data breach process is performed by hacker to collect and utilize company data. It includes following activities such as- code integration with company software, so on. Introducing our Security Data Breach Process By Backdoor set of slides. The topics discussed in these slides are Execution Persistence, Defense Evasion, Supply Chain Attack, Exfiltration, Backdoor Activates. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Stages of developing security breach mitigation plan
Stages of developing security breach mitigation planThis slide exhibits stages of developing security breach mitigation plan. It includes multiple steps such as running a company centric assessment, cyber security incident assessment and so on. Presenting our set of slides with Stages Of Developing Security Breach Mitigation Plan. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security, Development, Assessment, Analyze Objective, Investigation Scenario.





