Powerpoint Templates and Google slides for Security Audit
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Security Audit Powerpoint PPT Template Bundles
Security Audit Powerpoint PPT Template BundlesIf you require a professional template with great design, then this Security Audit Powerpoint PPT Template Bundles is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using Nineteen slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Cyber Security Audit Powerpoint PPT Template Bundles
Cyber Security Audit Powerpoint PPT Template BundlesEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Cyber Security Audit Powerpoint PPT Template Bundles is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With Eightee slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
 Black Box Security Audit As An Application Security Approach Training Ppt
Black Box Security Audit As An Application Security Approach Training PptPresenting Black-Box Security Audit as an Application Security Approach. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Automated Saas Compliance Audit Framework For Data Security
Automated Saas Compliance Audit Framework For Data SecurityThis slide shows automated compliance audit framework for building scalable security practices in SaaS businesses. The purpose of this slide is to assist businesses in gaining competitive advantage by simplifying SaaS compliance processes. It covers components such as deadline, controls implemented, compliance status, etc. Introducing our Automated Saas Compliance Audit Framework For Data Security set of slides. The topics discussed in these slides are Automated Saas Compliance, Audit Framework For Data Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Concern Of Audit Cost At A Hotel Training Ppt
Security Concern Of Audit Cost At A Hotel Training PptPresenting Security Concern of Audit Cost at a Hotel. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Network security audit remote operations ppt powerpoint presentation outline information cpb
Network security audit remote operations ppt powerpoint presentation outline information cpbPresenting Network Security Audit Remote Operations Ppt Powerpoint Presentation Outline Information Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Network Security Audit Remote Operations. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Digital Security And Data Audit Icon
Digital Security And Data Audit IconIntroducing our Digital Security And Data Audit Icon set of slides. The topics discussed in these slides are Data, Security, Digital. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Audit Smart Contracts With Review Checklist Security Token Offerings BCT SS
Audit Smart Contracts With Review Checklist Security Token Offerings BCT SSThe following slide depicts smart contract review checklist to ensure security and trustworthiness. It includes elements such as pre requisites, core checks, automation, manual testing, resiliency, auditing, etc. Deliver an outstanding presentation on the topic using this Audit Smart Contracts With Review Checklist Security Token Offerings BCT SS. Dispense information and present a thorough explanation of Review Agreement, Blockchain Operations, Performance Summary using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Auditing Broken Shield Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Security Auditing Broken Shield Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon features a broken shield with a distressed texture. It is perfect for conveying a sense of vulnerability, fragility, or failure in presentations. It is available in a range of vibrant colours and can be used to highlight key points or draw attention to important concepts.
-
 Security Auditing Broken Shield Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Security Auditing Broken Shield Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint icon depicts a broken shield, representing a lack of protection or security. It is perfect for conveying a sense of vulnerability, fragility, or danger in presentations. It can also be used to illustrate a lack of trust or loyalty.
-
 Security Compliance Audits For Risk Assessment
Security Compliance Audits For Risk AssessmentThis slide shows risk and assessment audits of security compliance which helps to make penetration tests and vulnerability assessments. It further includes requirements such as performing regular risk assessments, carrying out audits and establishing remedition plan etc. Introducing our premium set of slides with Security Compliance Audits For Risk Assessment. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Performing Regular, Carrying Out Internal. So download instantly and tailor it with your information.
-
 Classifying IT Audits For Network Security
Classifying IT Audits For Network SecurityThis slide represents categorization of IT Audit for evaluating systems and determining potential risks to establish effectiveness. It includes types such as technology progressive process audit, innovative contrasting audit, technology location audit, etc. Presenting our well structured Classifying IT Audits For Network Security. The topics discussed in this slide are Technology Progressive Process Audit, Innovative Contrasting Audit, Technological Location Audit. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 IT Audit Evaluation Icon For Data Security
IT Audit Evaluation Icon For Data SecurityIntroducing our premium set of slides with IT Audit Evaluation Icon For Data Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like IT Audit, Evaluation Icon, Data Security. So download instantly and tailor it with your information.
-
 Cyber Security Risk Audit Process Flowchart Improving Cyber Security Risks Management
Cyber Security Risk Audit Process Flowchart Improving Cyber Security Risks ManagementThe following slide depicts the cyber security review flowchart to manage risk and minimize its impact. It includes elements such as request access, grantor, authorizer, tools, auditor, follow up, alert to end user etc. Present the topic in a bit more detail with this Cyber Security Risk Audit Process Flowchart Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Request Access, Validate User Identity, Dismiss Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Adopt Security Auditing Checklist To Verify Processes Hands On Blockchain Security Risk BCT SS V
Adopt Security Auditing Checklist To Verify Processes Hands On Blockchain Security Risk BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Adopt Security Auditing Checklist To Verify Processes Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Parameters, Description, Comments. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist For Cyber Security Audit In Companies
Checklist For Cyber Security Audit In CompaniesThis slide covers online protection audits and provides details about parameters that give valuable insights to organizations before implementing cyber audits. It includes elements such as management, employees, etc. Introducing our Checklist For Cyber Security Audit In Companies set of slides. The topics discussed in these slides are Management, Company Security Policies Organizations, Security Policies Enforced. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis Of Cyber Security Network Audit Tools
Comparative Analysis Of Cyber Security Network Audit ToolsThis slide covers a comparison of cyber audit tools and provides details about features that help to identify suitable software for organizations. It includes elements such as description, subscriptions, etc. Introducing our Comparative Analysis Of Cyber Security Network Audit Tools set of slides. The topics discussed in these slides are Vulnerability Assessment, Tamper Protection, Cloud Based. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Network Security Audit Technology Icon
Cyber Network Security Audit Technology IconPresenting our set of slides with Cyber Network Security Audit Technology Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Network Security, Audit Technology Icon.
-
 Cyber Security And It Audit Trends
Cyber Security And It Audit TrendsThis slide covers emerging trends in cyber audit and provides details about market situation in global level cybersecurity audit. It includes elements such as advisory auditing, skilled employee shortage, etc. Introducing our premium set of slides with Cyber Security And It Audit Trends. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Skilled Employee Shortage, Advisory Auditing, Automation Analytics. So download instantly and tailor it with your information.
-
 Cyber Security Audit Process For Digital Ecosystem
Cyber Security Audit Process For Digital EcosystemThis slide elaborates on cybersecurity audit process and provides details about how to implement protection in a digital ecosystem. It includes elements such as build blueprint, audit frequently, etc. Presenting our set of slides with Cyber Security Audit Process For Digital Ecosystem. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Define Audit Purpose, Build Blueprint, Identify Evaluate Risk Management.
-
 Cyber Security Audit Protection Icon
Cyber Security Audit Protection IconIntroducing our premium set of slides with Cyber Security Audit Protection Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security, Audit Protection Icon. So download instantly and tailor it with your information.
-
 Key Metrics For Cyber Network Security Audit
Key Metrics For Cyber Network Security AuditThis slide covers various KPIs of cyber audit and provides details about metrics to identify problems to resolve issues in organizations. It includes elements such as compliance score, security ROI, etc. Introducing our Key Metrics For Cyber Network Security Audit set of slides. The topics discussed in these slides are Compliance Score, Vulnerability Count, Incident Response Time. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Major Cyber Security Audit Areas
Major Cyber Security Audit AreasThis slide covers major areas in cyber security and provides details about various regions to optimize performance from threads in system. It includes elements such as data security, supply chain, etc. Presenting our set of slides with Major Cyber Security Audit Areas. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Security, Process Practices, Service Tools .
-
 Techniques For Cyber Security Audit
Techniques For Cyber Security AuditThis slide covers approaches in cyber security audit and provides details about various techniques to protect systems from risk in a organization. It includes elements such as manual analysis , manual documentation, etc. Introducing our premium set of slides with Techniques For Cyber Security Audit. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Manual Specification Analysis, Automate Testing, Automate Static Analysis. So download instantly and tailor it with your information.
-
 Various Types Of Cyber Security Audit
Various Types Of Cyber Security AuditThis slide covers various kinds of audit and provides details about categories to optimize performance in organization. It includes elements such as new audit, repeat audit , etc. Presenting our set of slides with Various Types Of Cyber Security Audit. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on New Audit, Repeat Audit, Incident Audit .
-
 Best Practices For Cyber Security Audit
Best Practices For Cyber Security AuditThis slide depicts best practices in cyber audit and provides details about how company uses this to secure data in a organization. It includes elements such as strong password protocol, encrypted backup data drive , etc. Presenting our set of slides with Best Practices For Cyber Security Audit. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Encrypted Messaging Server, Adopt Decentralize Cybersecurity, Cybersecurity Awareness Program.
-
 Blockchain And Cybersecurity Adopt Security Auditing Checklist To Verify Processes BCT SS V
Blockchain And Cybersecurity Adopt Security Auditing Checklist To Verify Processes BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Blockchain And Cybersecurity Adopt Security Auditing Checklist To Verify Processes BCT SS V Use it as a tool for discussion and navigation on Parameters, Description, Verify Processes This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V
Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V Dispense information and present a thorough explanation of Consensus Mechanism, Smart Contract Security, Data Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Firewall Audit Icon
Cyber Security Firewall Audit IconPresenting our well structured Cyber Security Firewall Audit Icon. The topics discussed in this slide are Cyber Security, Firewall Audit Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Evaluating Security Capabilities For Firewall Auditing
Evaluating Security Capabilities For Firewall AuditingThis slide covers various techniques to evaluate security of information system for firewall auditing. The purpose of this slide is to help organizations in ensuring reliable and secure network. It covers techniques such as defining assessment scope, conducting security audit, implementing changes, evaluating risks, etc. Presenting our set of slides with Evaluating Security Capabilities For Firewall Auditing. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Conduct Security Audit, Implement Changes, Define Assessment Scope.
-
 Firewall Audit For Ensuring Network Infrastructure Security
Firewall Audit For Ensuring Network Infrastructure SecurityThis slide shows reasons for implementing firewall audit in an organization. The purpose of this slide is to help security professionals in maintaining integrity and security of network infrastructure. It covers various reasons such as ensuring network security, risk management, rules optimization and access control mechanism.Introducing our premium set of slides with Firewall Audit For Ensuring Network Infrastructure Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Security, Risk Management, Access Control Mechanism. So download instantly and tailor it with your information.
-
 Firewall Audit Icon For Network Security
Firewall Audit Icon For Network SecurityIntroducing our Firewall Audit Icon For Network Security set of slides. The topics discussed in these slides are Firewall Audit Icon, Network Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Firewall Audit Software Solutions For Security Compliance
Firewall Audit Software Solutions For Security ComplianceThis slide shows major features offered by firewall audit software that helps in maintaining a strong network security posture by complying with organizational regulatory standards. It covers solutions such as rule analysis, workflow automation and configuration management.Presenting our set of slides with Firewall Audit Software Solutions For Security Compliance. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Workflow Automation, Configuration Management, Firewall Rule Analysis.
-
 Adopt Security Auditing Checklist To Verify Processes Guide For Blockchain BCT SS V
Adopt Security Auditing Checklist To Verify Processes Guide For Blockchain BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Adopt Security Auditing Checklist To Verify Processes Guide For Blockchain BCT SS V Use it as a tool for discussion and navigation on Network Security, Node Security, Consensus Mechanism This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Adopt Security Auditing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS V
Adopt Security Auditing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Adopt Security Auditing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS V. Use it as a tool for discussion and navigation on Parameters, Comments, Comply Safe Communication Protocols. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Factors Affecting Security Compliance In It Audit
Factors Affecting Security Compliance In It AuditFollowing slide showcases factors in IT audit that affect security compliance for risk mitigation. It further covers factors such as logical and physical security, regulatory compliance and hardware. Introducing our premium set of slides with Factors Affecting Security Compliance In It Audit. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Physical Security, Regulatory Compliance, Management System. So download instantly and tailor it with your information.
-
 Website Server Security Audit Checklist For Reducing Cyberattacks
Website Server Security Audit Checklist For Reducing CyberattacksFollowing slide highlights checklist for website server security audit to reduce cyberattacks, also including description such as set up essential website framework, incorporate outside services, etc. Introducing our Website Server Security Audit Checklist For Reducing Cyberattacks set of slides. The topics discussed in these slides are Data Safely, Outside Services, Website Extensions. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
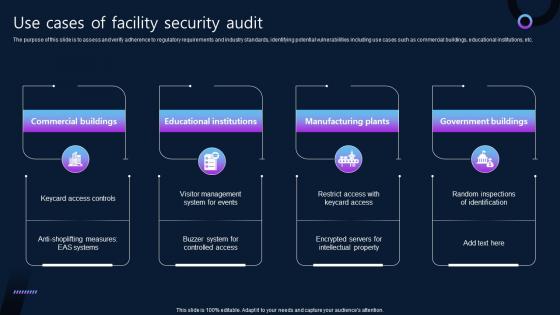 Use Cases Of Facility Security Audit
Use Cases Of Facility Security AuditThe purpose of this slide is to assess and verify adherence to regulatory requirements and industry standards, identifying potential vulnerabilities including use cases such as commercial buildings, educational institutions, etc. Presenting our set of slides with name Use Cases Of Facility Security Audit. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Government Buildings, Manufacturing Plants, Educational Institutions, Commercial Buildings.
-
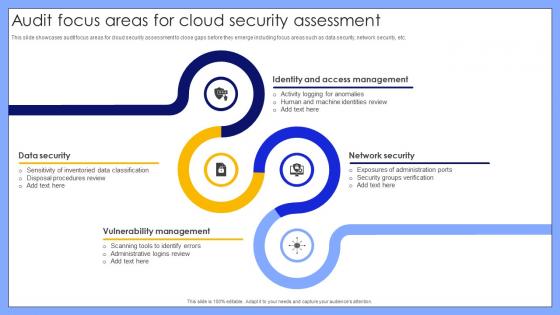 Audit Focus Areas For Cloud Security Assessment
Audit Focus Areas For Cloud Security AssessmentThis slide showcases audit focus areas for cloud security assessment to close gaps before they emerge including focus areas such as data security, network security, etc. Introducing our premium set of slides with name Audit Focus Areas For Cloud Security Assessment. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Security, Vulnerability Management, Network Security, Identity And Access Management. So download instantly and tailor it with your information.
-
 Cloud Security Audit Checklist For Businesses
Cloud Security Audit Checklist For BusinessesThis slide showcases checklist for cloud security audit to fix loopholes including checkpoints such as identifying cloud providers and services, access level management in cloud, etc. Introducing our Cloud Security Audit Checklist For Businesses set of slides. The topics discussed in these slides are Identify Cloud Providers And Services, Encrypt Data In Transit, Detecting Unusual Or Suspicious Activity. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Security Audit Techniques For Operational Efficiency
Cloud Security Audit Techniques For Operational EfficiencyThis slide showcases cloud security audit techniques to analyze data retention such as configuration review, access controls assessments, etc. Introducing our premium set of slides with name Cloud Security Audit Techniques For Operational Efficiency. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Configuration Review, Access Controls Assessment, Patch Management Review, Vendor Security Evaluation. So download instantly and tailor it with your information.
-
 Cloud Security Challenges And Solutions For Internal Audit
Cloud Security Challenges And Solutions For Internal AuditThis slide showcases solutions to overcome cloud security challenges for internal audit to ensure data protection such as lack of visibility, compliance, shared responsibility, etc. Presenting our well structured Cloud Security Challenges And Solutions For Internal Audit. The topics discussed in this slide are Lack Of Visibility, Compliance, Shared Responsibility, Identity And Access Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cloud Security Configuration Audit Icon
Cloud Security Configuration Audit IconPresenting our set of slides with name Cloud Security Configuration Audit Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Security, Configuration Audit Icon.
-
 Comparative Analysis Of Open Source Cloud Security Audit Tools
Comparative Analysis Of Open Source Cloud Security Audit ToolsThis slide showcases open source cloud security audit tools comparison to improve organizational position such as. Introducing our Comparative Analysis Of Open Source Cloud Security Audit Tools set of slides. The topics discussed in these slides are Comparative Analysis, Cloud Security Audit Tools, Audit Tools Comparison, Organizational Position. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Solutions To Overcome Cloud Security Audit Challenges
Solutions To Overcome Cloud Security Audit ChallengesThis slide showcases challenges and solutions of cloud security audit to standardize workloads including challenges such as effective communication, encryption strategy, etc. Presenting our set of slides with name Solutions To Overcome Cloud Security Audit Challenges. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Effective Communication, Encryption Strategy, Address Colocation, Scale And Complexity.
-
 Standards Covering Cloud Security Audit
Standards Covering Cloud Security AuditThis slide showcases standards related to cloud security audit to safeguard data and systems such as implementation, CIS foundation benchmarks, etc. Introducing our premium set of slides with name Standards Covering Cloud Security Audit. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Policies For Governance, Cloud Control Matrix, Cloud Security Audit. So download instantly and tailor it with your information.
-
 Steps To Conduct Cloud Security Audit
Steps To Conduct Cloud Security AuditThis slide showcases process to conduct cloud security audit for risk assessment such as evaluating cloud provider security, determining attack surface, etc. Presenting our well structured Steps To Conduct Cloud Security Audit. The topics discussed in this slide are Evaluate Cloud Provider Security, Determine Attack Surface, Automate Patching, Cloud Security Audit. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Audit Smart Contracts Beginners Guide To Successfully Launch Security Token BCT SS V
Audit Smart Contracts Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide depicts smart contract review checklist to ensure security and trustworthiness. It includes elements such as pre-requisites, core checks, automation, manual testing, resiliency, auditing, etc. Introducing Audit Smart Contracts Beginners Guide To Successfully Launch Security Token BCT SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Audit, Smart Contracts, Review Checklist, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Insurance Audit Checklist
Cyber Security Insurance Audit ChecklistThis slide showcases cyber security insurance audit checklist which helps in providing coverage to reduce the financial risks associated with cybercrimes. Introducing our Cyber Security Insurance Audit Checklist set of slides. The topics discussed in these slides are Network And Perimeter Security, Password Policy And Authentication, Vulnerability Management, Backups And Disaster Recovery.This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Audit Procedure Icon To Verify Company Data Protection
Security Audit Procedure Icon To Verify Company Data ProtectionPresenting our set of slides with Security Audit Procedure Icon To Verify Company Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Audit Procedure, Verify Company, Data Protection.
-
 Solutions To Overcome Website Security Audit Challenges
Solutions To Overcome Website Security Audit ChallengesThis template showcases solutions and technological stack to overcome challenges faced by organizations while conducting website security audit. The purpose of this slide is to help organizations streamline auditing process for maintaining data authenticity. It covers tools and strategies to reduce web security risks such as injections, broken authentication, and data exposure. Introducing our Solutions To Overcome Website Security Audit Challenges set of slides. The topics discussed in these slides are Challenges, Solutions This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Steps To Conduct Website Security Audit
Steps To Conduct Website Security AuditThis slide showcases website security audit process. The purpose of this slide is to ensure website safety by conducting deep analysis of server setups, application software and network configurations. It covers steps such as scoping, vulnerability assessment, penetration testing, risk assessment, remediation and monitoring. Presenting our set of slides with Steps To Conduct Website Security Audit This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Scoping, Penetration Testing, Remediation
-
 Web Security Audit Controls To Reduce Threats
Web Security Audit Controls To Reduce ThreatsThis slide represents various security control methods to minimize threats to web security. The purpose of this slide is to help businesses in developing strategy for data protection. It provides techniques to minimize web security threats such as SQL injection, ransomware, denial of service attacks and phishing. Introducing our Web Security Audit Controls To Reduce Threats set of slides. The topics discussed in these slides are Ransomware, Service Attacks, Phishing This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SS
Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of auditing and monitoring for internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about response plan, etc. Increase audience engagement and knowledge by dispensing information using Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on three stages. You can also present information on Auditing And Reporting, Incident Response Planning, Record Of Security Actions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Physical Security Audit And Assessment Checklist
Physical Security Audit And Assessment ChecklistThis slide showcases security audit checklist to ensure safe working environment for the employees. The checklist includes questions regarding camera installations, fire alarms, lighting, etc. Introducing our Physical Security Audit And Assessment Checklist set of slides. The topics discussed in these slides are Procedures And Tests, Good Condition, Business. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Operations Center GDPR Audit Status
Security Operations Center GDPR Audit StatusThe below slide provides a general data protection regulation status of personal data breaches faced by company along with solution implemented and resolution status. The categories evaluated are application hacking, database hacking, etc. Introducing our premium set of slides with name Security Operations Center GDPR Audit Status. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk, Risk Severity, Solution Implemented, Resolved. So download instantly and tailor it with your information.
-
 Security Audits Report For Vulnerability Assessment Implementing E Commerce Security Measures
Security Audits Report For Vulnerability Assessment Implementing E Commerce Security MeasuresThe slide showcases security audit report to asses open vulnerabilities. It include vulnerability category, number of occurrences, and vulnerability level such as critical, high, medium and low. Present the topic in a bit more detail with this Security Audits Report For Vulnerability Assessment Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Weak Authentication, Unauthorized Access, Security Misconfiguration, Payment Gateway Vulnerability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Audit Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Audit Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentations on information security with this eye-catching PowerPoint icon. Featuring a bold and vibrant color, this icon represents the crucial aspect of information security audits. Perfect for IT professionals, consultants, and businesses looking to showcase their expertise in protecting sensitive data. Download now and make a lasting impression.
-
 Information Security Audit Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Audit Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentation with our Monotone PowerPoint icon on Information Security Audit. This sleek and professional icon represents the importance of safeguarding sensitive data and conducting thorough audits. Perfect for presentations on cyber security, compliance, and risk management. Grab your audiences attention and convey a message of security and diligence.
-
 IT Network Security Audit Checklist
IT Network Security Audit ChecklistThis slide exhibits systematic assessment of security postures of organizations IT infrastructure to protect against various threats. It includdes aspects such as access control, network security measures, incident response, etc. Introducing our IT Network Security Audit Checklist set of slides. The topics discussed in these slides are Tasks, Aspects, Applicable. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.




