Powerpoint Templates and Google slides for Security Attacks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Security Hacker Loss Due To Different Cyber Attacks Ppt Powerpoint Presentation Slides
Security Hacker Loss Due To Different Cyber Attacks Ppt Powerpoint Presentation SlidesThis slide represents the different types of cyber attacks throughout the year, including the percentage of total loss caused by these attacks. Present the topic in a bit more detail with this Security Hacker Loss Due To Different Cyber Attacks Ppt Powerpoint Presentation Slides. Use it as a tool for discussion and navigation on Different Cyber Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attack Prevention Techniques Building A Security Awareness Program
Social Engineering Attack Prevention Techniques Building A Security Awareness ProgramThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. Deliver an outstanding presentation on the topic using this Social Engineering Attack Prevention Techniques Building A Security Awareness Program. Dispense information and present a thorough explanation of Public Information, Prevention Techniques, Social Engineering Attack using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Rising Number Of Information Security Attacks Risk Assessment And Management Plan For Information Security
Rising Number Of Information Security Attacks Risk Assessment And Management Plan For Information SecurityThis slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection Present the topic in a bit more detail with this Rising Number Of Information Security Attacks Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Organizations, Information, Cybersecurity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attack Prevention Techniques Conducting Security Awareness
Social Engineering Attack Prevention Techniques Conducting Security AwarenessThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Conducting Security Awareness. Use it as a tool for discussion and navigation on Techniques, Limit Public Information, Verify Source. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determining The Actors Behind Most Significant Cyber Attack Developing Cyber Security Awareness
Determining The Actors Behind Most Significant Cyber Attack Developing Cyber Security AwarenessThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present the topic in a bit more detail with this Determining The Actors Behind Most Significant Cyber Attack Developing Cyber Security Awareness. Use it as a tool for discussion and navigation on Determining The Actors, Behind Most Significant, Cyber Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Common Cyber Attack Faced By Our Employees Developing Cyber Security Awareness Training Program
Most Common Cyber Attack Faced By Our Employees Developing Cyber Security Awareness Training ProgramThe purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, iot based attacks, malware, social engineering attack and business email compromise. Increase audience engagement and knowledge by dispensing information using Most Common Cyber Attack Faced By Our Employees Developing Cyber Security Awareness Training Program. This template helps you present information on eight stages. You can also present information on Ransomware, Password Attack, Social Engineering Attack, Business Email Compromise using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attack Prevention Techniques Developing Cyber Security Awareness Training
Social Engineering Attack Prevention Techniques Developing Cyber Security Awareness TrainingThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. Deliver an outstanding presentation on the topic using this Social Engineering Attack Prevention Techniques Developing Cyber Security Awareness Training. Dispense information and present a thorough explanation of Limit Public Information, Verify The Source, No Sharing Of Password using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Attacks Faced By Organization In Previous Information Security Risk Management
Cyber Attacks Faced By Organization In Previous Information Security Risk ManagementThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different types of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization In Previous Information Security Risk Management. Dispense information and present a thorough explanation of Cyber Attacks Faced, Organization, Previous Financial Year using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Rising Number Of Information Security Attacks Information Security Risk Management
Rising Number Of Information Security Attacks Information Security Risk ManagementThis slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, dos attack, phishing and SQL injection. Present the topic in a bit more detail with this Rising Number Of Information Security Attacks Information Security Risk Management. Use it as a tool for discussion and navigation on Rising Number, Information Security Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now
-
 KPI Metrics Of Cyber Security For Attacks Dashboard
KPI Metrics Of Cyber Security For Attacks DashboardThis slide shows dashboard of cyber threats and attacks and predictions made for the same. It includes threats by class name and attacks by month. Introducing our KPI Metrics Of Cyber Security For Attacks Dashboard set of slides. The topics discussed in these slides are KPI Metrics, Cyber Security, Attacks Dashboard. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Determining The Actors Behind Most Significant Cyber Attack Conducting Security Awareness
Determining The Actors Behind Most Significant Cyber Attack Conducting Security AwarenessThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Deliver an outstanding presentation on the topic using this Determining The Actors Behind Most Significant Cyber Attack Conducting Security Awareness. Dispense information and present a thorough explanation of Online Criminals, Foreign Government Officials, Malicious Insiders using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Most Common Cyber Attack Faced By Our Employees Conducting Security Awareness
Most Common Cyber Attack Faced By Our Employees Conducting Security AwarenessThe purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Present the topic in a bit more detail with this Most Common Cyber Attack Faced By Our Employees Conducting Security Awareness. Use it as a tool for discussion and navigation on Ransomware, Password Attack, Cryptojacking. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Common Cyber Attack Faced By Our Employees Implementing Security Awareness Training
Most Common Cyber Attack Faced By Our Employees Implementing Security Awareness TrainingThe purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT based attacks, malware, social engineering attack and business email compromise. Introducing Most Common Cyber Attack Faced By Our Employees Implementing Security Awareness Training to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Ransomware, Password Attack, Cryptojacking, Malware, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks
Table Of Contents Implementing Security Awareness Training To Prevent Cyber AttacksPresent the topic in a bit more detail with this Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks. Use it as a tool for discussion and navigation on Security Awareness, Current Assessment, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk Administration
Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk AdministrationThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk Administration. Dispense information and present a thorough explanation of Organization Experienced, Increasing A Rapid Rate, Financial Year using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Rising Number Of Information Security Attacks Information System Security And Risk Administration Plan
Rising Number Of Information Security Attacks Information System Security And Risk Administration PlanThis slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection. Deliver an outstanding presentation on the topic using thisRising Number Of Information Security Attacks Information System Security And Risk Administration Plan. Dispense information and present a thorough explanation of Financial Years, Cyber Attacks, Information Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
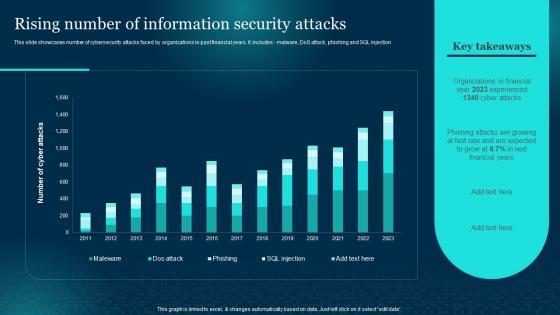 Rising Number Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan
Rising Number Of Information Security Attacks Cybersecurity Risk Analysis And Management PlanThis slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection Present the topic in a bit more detail with this Rising Number Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Information, Security Attacks, Organizations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Rising Number Of Information Security Attacks Formulating Cybersecurity Plan
Rising Number Of Information Security Attacks Formulating Cybersecurity PlanThis slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection. Deliver an outstanding presentation on the topic using this Rising Number Of Information Security Attacks Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Rising Number, Information Security, Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber Security
Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present the topic in a bit more detail with this Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Online Criminals, Foreign Government Officials, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security
Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Limit Public Information, Verify The Source, No Sharing Of Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attack Analytics Dashboard With Level Of Security
Cyber Attack Analytics Dashboard With Level Of SecurityThe given slide depicts the cyber threat analytics to track the attacks. It includes the no. of incidents, open and solved tickets, category wise no. of incidents along with malware type etc. Introducing our Cyber Attack Analytics Dashboard With Level Of Security set of slides. The topics discussed in these slides are Cyber Attack Analytics, Dashboard, Level Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Social Engineering Attack Prevention Techniques Implementing Security Awareness Training
Social Engineering Attack Prevention Techniques Implementing Security Awareness TrainingThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Limit Public Information, Verify The Source, No Sharing Of Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
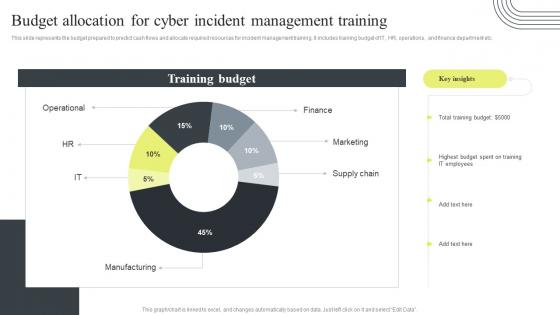 Cyber Security Attacks Response Plan Budget Allocation For Cyber Incident Management Training
Cyber Security Attacks Response Plan Budget Allocation For Cyber Incident Management TrainingThis slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Budget Allocation For Cyber Incident Management Training. Dispense information and present a thorough explanation of Budget Allocation, Cyber Incident Management, Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By Organization
Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By OrganizationThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By Organization. Use it as a tool for discussion and navigation on Consequences, Data Breaches, Unintended Disclosure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard
Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management DashboardThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Security Systems Monitoring Report
Cyber Security Attacks Response Plan Cyber Security Systems Monitoring ReportThis slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Security Systems Monitoring Report. Use it as a tool for discussion and navigation on Cyber Security Systems, Monitoring Report, Mean Detect And Resolve Time. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Supply Chain Risk Management Dashboard
Cyber Security Attacks Response Plan Cyber Supply Chain Risk Management DashboardThis slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Supply Chain Risk Management Dashboard. Use it as a tool for discussion and navigation on Cyber Supply Chain, Risk Management, Dashboard, Regulatory Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Enterprise Cyber Risk Management Dashboard
Cyber Security Attacks Response Plan Enterprise Cyber Risk Management DashboardThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Enterprise Cyber Risk Management Dashboard. Dispense information and present a thorough explanation of Enterprise Cyber, Risk Management, Dashboard, Action Plan Breakdown using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Response Kpi Dashboard Cyber Security Attacks Response Plan
Cyber Security Incident Response Kpi Dashboard Cyber Security Attacks Response PlanThis slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Present the topic in a bit more detail with this Cyber Security Incident Response Kpi Dashboard Cyber Security Attacks Response Plan. Use it as a tool for discussion and navigation on Cyber Security, Incident Response, KPI Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attack Prevention Techniques Raising Cyber Security Awareness In Organizations
Social Engineering Attack Prevention Techniques Raising Cyber Security Awareness In OrganizationsThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Raising Cyber Security Awareness In Organizations. Use it as a tool for discussion and navigation on Verify The Source, Sharing Of Password, Public Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attack Incident Generating Security Awareness Among Employees To Reduce
Cyber Attack Incident Generating Security Awareness Among Employees To ReduceThe following slide depicts the number of cyber attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Generating Security Awareness Among Employees To Reduce Use it as a tool for discussion and navigation on Infected Hosts, Prevented Attacks This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Corporate security management determine sequence phases for threat attack
Corporate security management determine sequence phases for threat attackThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Corporate Security Management Determine Sequence Phases For Threat Attack. This template helps you present information on four stages. You can also present information on Reconnaissance, Weaponization, Delivery, Exploitation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine sequence phases for threat attack actions corporate security management
Determine sequence phases for threat attack actions corporate security managementThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Introducing Determine Sequence Phases For Threat Attack Actions Corporate Security Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Installation, Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 Types network security attack ppt powerpoint presentation pictures examples cpb
Types network security attack ppt powerpoint presentation pictures examples cpbPresenting Types Network Security Attack Ppt Powerpoint Presentation Pictures Examples Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Types Network Security Attack. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Security measures to prevent phishing attacks ppt powerpoint presentation pictures display
Security measures to prevent phishing attacks ppt powerpoint presentation pictures displayThis slide represents the security measures to prevent phishing attacks, such as using the spam filter, updating security software regularly, utilization of multi factor authentication, and so on. Increase audience engagement and knowledge by dispensing information using Security Measures To Prevent Phishing Attacks Ppt Powerpoint Presentation Pictures Display. This template helps you present information on six stages. You can also present information on Security Measures To Prevent Phishing Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management determine sequence phases for threat attack
Cyber security risk management determine sequence phases for threat attackThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Determine Sequence Phases For Threat Attack. This template helps you present information on four stages. You can also present information on Reconnaissance, Weaponization, Exploitation, Delivery using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine sequence phases for threat attack contd cyber security risk management
Determine sequence phases for threat attack contd cyber security risk managementThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Introducing Determine Sequence Phases For Threat Attack Contd Cyber Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Installation, Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Kpis To Measure Phishing Attacks
Cyber Security Kpis To Measure Phishing AttacksMentioned slide showcases 5 cyber security KPI which can be used by organization to measure phishing attacks. The KPIs mentioned in the slide are intrusion attempts, security incidents, mean time to detect MTTD, etc. Presenting our well structured Cyber Security Kpis To Measure Phishing Attacks. The topics discussed in this slide are Intrusion Attempts, Security Incidents, Mean Time to Resolve. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Attacks Statistics Ppt Powerpoint Presentation File Display Cpb
Cyber Security Attacks Statistics Ppt Powerpoint Presentation File Display CpbPresenting our Cyber Security Attacks Statistics Ppt Powerpoint Presentation File Display Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Cyber Security Attacks Statistics This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Roadmap To Implement Cyber Security Cyber Terrorism Attacks
Roadmap To Implement Cyber Security Cyber Terrorism AttacksThis slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. Introducing Roadmap To Implement Cyber Security Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Personal Accounts, Awareness Training, Software Updated, using this template. Grab it now to reap its full benefits.
-
 Determine phases of threat attack disrupting it project safety enhancing overall project security it
Determine phases of threat attack disrupting it project safety enhancing overall project security itThis slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. Introducing Determine Phases Of Threat Attack Disrupting It Project Safety Enhancing Overall Project Security It to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reconnaissance, Weaponization, Exploitation, using this template. Grab it now to reap its full benefits.
-
 Enhancing overall project security it determine phases of threat attack disrupting project safety contd
Enhancing overall project security it determine phases of threat attack disrupting project safety contdThis slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. Introducing Enhancing Overall Project Security It Determine Phases Of Threat Attack Disrupting Project Safety Contd to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 Information Security Attacks Ppt Powerpoint Presentation Outline Inspiration Cpb
Information Security Attacks Ppt Powerpoint Presentation Outline Inspiration CpbPresenting our Information Security Attacks Ppt Powerpoint Presentation Outline Inspiration Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Information Security Attacks This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Incident Response Playbook Addressing The Various Security Incidents And Attacks
Incident Response Playbook Addressing The Various Security Incidents And AttacksPurpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques. Introducing Incident Response Playbook Addressing The Various Security Incidents And Attacks to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Traditional IT Security Incidents, Cyber Security Attacks, Common Techniques, using this template. Grab it now to reap its full benefits.
-
 Incident Response Playbook Classifying Various Security Issues And Attacks
Incident Response Playbook Classifying Various Security Issues And AttacksPurpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks. Deliver an outstanding presentation on the topic using this Incident Response Playbook Classifying Various Security Issues And Attacks. Dispense information and present a thorough explanation of Internal Issues And Attacks, External Issues And Attacks, Security Issues And Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Security Threats Malware Attacks Cloud Information Security
Cloud Security Threats Malware Attacks Cloud Information SecurityThis slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss.Introducing Cloud Security Threats Malware Attacks Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Clients OR Customers, Organizations Experienced, Companies Organizations using this template. Grab it now to reap its full benefits.
-
 General Outlook Of Ransomware Attack Building A Security Awareness Program
General Outlook Of Ransomware Attack Building A Security Awareness ProgramThe purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Deliver an outstanding presentation on the topic using this General Outlook Of Ransomware Attack Building A Security Awareness Program. Dispense information and present a thorough explanation of Programme, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Outlook Of Social Engineering Attack Building A Security Awareness Program
Outlook Of Social Engineering Attack Building A Security Awareness ProgramThe purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Deliver an outstanding presentation on the topic using this Outlook Of Social Engineering Attack Building A Security Awareness Program. Dispense information and present a thorough explanation of Congratulation, Engineering Attack using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Of Business Email Compromise Attack Building A Security Awareness Program
Overview Of Business Email Compromise Attack Building A Security Awareness ProgramThe purpose of this slide is to delineate an example of business email compromise attack. Information covered in this slide is related to the working of this attack and how it can result in loss of company reputation. Introducing Overview Of Business Email Compromise Attack Building A Security Awareness Program to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Compromise Attack, Business Email, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Malware Attacks Cloud Computing Security
Cloud Security Threats Malware Attacks Cloud Computing SecurityThis slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. Introducing Cloud Security Threats Malware Attacks Cloud Computing Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Administrations, Cloud Security Threats, Malware Attacks, using this template. Grab it now to reap its full benefits.
-
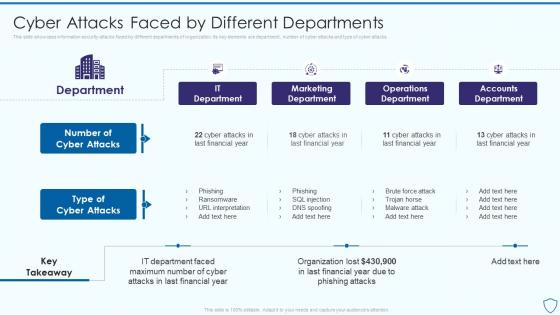 Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different
Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By DifferentThis slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks Deliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different. Dispense information and present a thorough explanation of Marketing Department, Operations Department, Accounts Department using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Attacks Faced By Risk Assessment And Management Plan For Information Security
Information Security Attacks Faced By Risk Assessment And Management Plan For Information SecurityThis slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack Deliver an outstanding presentation on the topic using this Information Security Attacks Faced By Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Malware, Phishing, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Security Threats Malware Attacks Cloud Data Protection
Cloud Security Threats Malware Attacks Cloud Data ProtectionThis slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. Introducing Cloud Security Threats Malware Attacks Cloud Data Protection to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispense information on Frameworks, Targets, Technology, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Response Plan For Attack
Cyber Security Incident Response Plan For AttackThe following slide highlights the cyber security incident response plan for attack illustrating objective, planning and action, which helps the management to take decision for risk mitigation strategy and allocation of budget and resources depending on criticality of cyber attack. Presenting our set of slides with name Cyber Security Incident Response Plan For Attack. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Objective, Planning, Action.
-
 Understanding The Frequency And Weightage Of Cyber Attacks Conducting Security Awareness
Understanding The Frequency And Weightage Of Cyber Attacks Conducting Security AwarenessThe purpose of this slide is to showcase the frequency and weightage of different cyber attacks on multiple departments. The major departments mentioned in the slide are financial, marketing, information technology IT and human resource HR. Increase audience engagement and knowledge by dispensing information using Understanding The Frequency And Weightage Of Cyber Attacks Conducting Security Awareness. This template helps you present information on four stages. You can also present information on Financial Department, Marketing Team, HR Department, IT Department using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Elements IT Types Of Cyber Attackers Ppt Professional
Cyber Security Elements IT Types Of Cyber Attackers Ppt ProfessionalThis slide represents the types of cyber attackers, including cyber criminals, hacktivists, state sponsored attackers, and insider threats. Insider threats can be occurred from within the organization and can be malicious, accidental or negligent. Introducing Cyber Security Elements IT Types Of Cyber Attackers Ppt Professional to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Criminals, Insider Threats, Hacktivists, using this template. Grab it now to reap its full benefits.
-
 Dos And Donts Of Prevention From Ransomware Attack Developing Cyber Security Awareness Training
Dos And Donts Of Prevention From Ransomware Attack Developing Cyber Security Awareness TrainingThe purpose of this slide is to showcase the Dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Increase audience engagement and knowledge by dispensing information using Dos And Donts Of Prevention From Ransomware Attack Developing Cyber Security Awareness Training. This template helps you present information on two stages. You can also present information on Confidential Files, Devices Safe, Firewall Software, Malware Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 General Outlook Of Ransomware Attack Developing Cyber Security Awareness Training Program For Staff
General Outlook Of Ransomware Attack Developing Cyber Security Awareness Training Program For StaffThe purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Introducing General Outlook Of Ransomware Attack Developing Cyber Security Awareness Training Program For Staff to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Files Are Encrypted, Ransomware Works, General Outlook, using this template. Grab it now to reap its full benefits.
-
 Outlook Of Social Engineering Attack Developing Cyber Security Awareness Training Program For Staff
Outlook Of Social Engineering Attack Developing Cyber Security Awareness Training Program For StaffThe purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Increase audience engagement and knowledge by dispensing information using Outlook Of Social Engineering Attack Developing Cyber Security Awareness Training Program For Staff. This template helps you present information on one stages. You can also present information on Social Engineering, Attack Works, Completion Of A Survey using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of Business Email Compromise Attack Developing Cyber Security Awareness Training Program
Overview Of Business Email Compromise Attack Developing Cyber Security Awareness Training ProgramThe purpose of this slide is to delineate an example of business email compromise attack. Information covered in this slide is related to the working of this attack and how it can result in loss of company reputation. Introducing Overview Of Business Email Compromise Attack Developing Cyber Security Awareness Training Program to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Overview Of Business, Email Compromise Attack, Restricted, using this template. Grab it now to reap its full benefits.





