Powerpoint Templates and Google slides for Security Assessment Process
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Technology Security Process Framework Assessment Management Awareness
Technology Security Process Framework Assessment Management AwarenessThis complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Technology Security Process Framework Assessment Management Awareness and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of twelve slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.
-
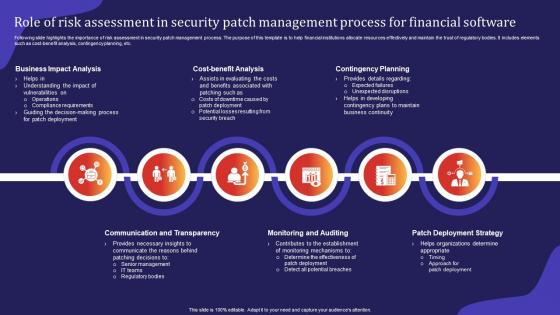 Role Of Risk Assessment In Security Patch Management Process For Financial Software
Role Of Risk Assessment In Security Patch Management Process For Financial SoftwareFollowing slide highlights the importance of risk assessment in security patch management process. The purpose of this template is to help financial institutions allocate resources effectively and maintain the trust of regulatory bodies. It includes elements such as cost benefit analysis, contingency planning, etc.Introducing our premium set of slides with Role Of Risk Assessment In Security Patch Management Process For Financial Software. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Contingency Planning, Communication Transparency, Monitoring Auditing. So download instantly and tailor it with your information.
-
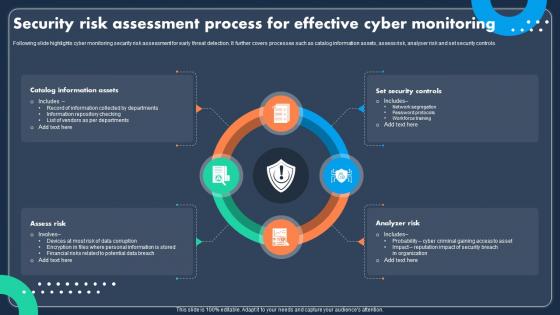 Security Risk Assessment Process For Effective Cyber Monitoring
Security Risk Assessment Process For Effective Cyber MonitoringFollowing slide highlights cyber monitoring security risk assessment for early threat detection. It further covers processes such as catalog information assets, assess risk, analyser risk and set security controls. Introducing our premium set of slides with Security Risk Assessment Process For Effective Cyber Monitoring Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Assets, Security Controls, Analyzer Risk. So download instantly and tailor it with your information.
-
 Comparative Assessment Of ACH Payment Processors Enhancing Transaction Security With E Payment
Comparative Assessment Of ACH Payment Processors Enhancing Transaction Security With E PaymentMentioned slide illustrates comparative analysis of various ACH Automated Clearing House payment processors which can be leveraged by businesses to making bank transfer. It includes key attributes such as ACH processors, best attribute, features, rating, price, and company size. Deliver an outstanding presentation on the topic using this Comparative Assessment Of ACH Payment Processors Enhancing Transaction Security With E Payment Dispense information and present a thorough explanation of ACH Payment Processors, Best Attribute, Features using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Wireless Lan Security Protocols
Comparative Assessment Of Wireless Lan Security ProtocolsThis slide represents comparative assessment of various WLAN security protocols that assist companies in selecting relevant protocol suitable for specific use cases. It includes various protocols such as WEP, WPA, WPA2, and WPA3 Presenting our well structured Comparative Assessment Of Wireless Lan Security Protocols The topics discussed in this slide are Year Release, Cryptographic Technique, Session Key SizeThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Process Phases For Application Security Assessment
Process Phases For Application Security AssessmentThis slide highlights the steps of application security assessment which include determining threats, identifying sensitive data, mapping application attacks, etc. Introducing our premium set of slides with Process Phases For Application Security Assessment Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Application Security, Statistical Representation So download instantly and tailor it with your information.
-
 Effective information security management process information security risk assessment
Effective information security management process information security risk assessmentThis slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence.Deliver an outstanding presentation on the topic using this Effective Information Security Management Process Information Security Risk Assessment. Dispense information and present a thorough explanation of Facilities And Equipment, Unauthorized Disclosure, Valuable Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact assessment matrix effective information security risk management process
Impact assessment matrix effective information security risk management processPresent the topic in a bit more detail with this Impact Assessment Matrix Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Minor To No Infringement, Suspected Malicious Intent, Impact Medium. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat assessment effective information security risk management process
Threat assessment effective information security risk management processFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Threat Assessment Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Affected Asset, Potential Vulnerability, Vulnerability Ranking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
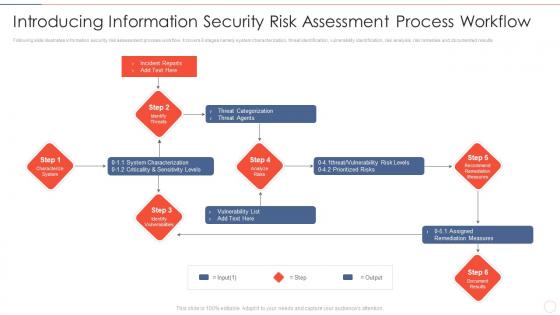 Effective information security introducing information security risk assessment process
Effective information security introducing information security risk assessment processFollowing slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results Increase audience engagement and knowledge by dispensing information using Effective Information Security Introducing Information Security Risk Assessment Process. This template helps you present information on six stages. You can also present information on Incident Reports, Threat Categorization, Vulnerability List, Assigned Remediation Measures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer Security Technical Assessment Process
Computer Security Technical Assessment ProcessThis slide signifies the technical assessment process on company security. It steps include identify, analyse, prioritize and monitoring. Introducing our premium set of slides with Computer Security Technical Assessment Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify, Analyse, Prioritize, Monitoring. So download instantly and tailor it with your information.
-
 Cyber Security Technical Assessment Process
Cyber Security Technical Assessment ProcessThis slide signifies the technical assessment process of cyber security. It include stages like identify, planning, execution, monitor and closure. Presenting our set of slides with Cyber Security Technical Assessment Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Execution, Closure, Planning, Monitor.
-
 Process For Information Security Risk Assessment And Management Plan For Information Security
Process For Information Security Risk Assessment And Management Plan For Information SecurityThis slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets Introducing Process For Information Security Risk Assessment And Management Plan For Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Process, Information, Assessment, using this template. Grab it now to reap its full benefits.
-
 Business Cyber Security Risk Assessment Process
Business Cyber Security Risk Assessment ProcessThe slide shows cyber threat detection and protection measures in order to eliminate the potential risks to the business. The steps include identifying, detecting, responding, protecting, and recovering. Presenting our set of slides with Business Cyber Security Risk Assessment Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Detect, Respond, Protect.
-
 Process For Information Security Risk Assessment Information Security Risk Management
Process For Information Security Risk Assessment Information Security Risk ManagementThis slide showcases process that can help organization to perform information security risk assessment. It can help to identify security threats and allocate vulnerability rating to information assets. Introducing Process For Information Security Risk Assessment Information Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Information Security Threats, Allocating Vulnerability, Risk Assessment, using this template. Grab it now to reap its full benefits.
-
 Process For Information Security Risk Assessment Information System Security And Risk Administration Plan
Process For Information Security Risk Assessment Information System Security And Risk Administration PlanThis slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Increase audience engagement and knowledge by dispensing information using Process For Information Security Risk Assessment Information System Security And Risk Administration Plan. This template helps you present information on four stages. You can also present information on Security Threats, Information Assets, Risk Associated using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Process For Information Security Risk Assessment Cybersecurity Risk Analysis And Management Plan
Process For Information Security Risk Assessment Cybersecurity Risk Analysis And Management PlanThis slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Introducing Process For Information Security Risk Assessment Cybersecurity Risk Analysis And Management Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Process, Assessment, Information, using this template. Grab it now to reap its full benefits.
-
 Process For Information Security Risk Assessment Formulating Cybersecurity Plan
Process For Information Security Risk Assessment Formulating Cybersecurity PlanThis slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Introducing Process For Information Security Risk Assessment Formulating Cybersecurity Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identifying Internal, Information Security Threats, Information Assets, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Audit Assessment Process
Cloud Security Audit Assessment ProcessThe slide exhibits various steps of cloud security audit for getting an excellent performance. Various steps included are understand the model, analyse, validate controls and calculate score. Introducing our premium set of slides with Cloud Security Audit Assessment Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Calculate Score, Validate Controls, Understand The Model . So download instantly and tailor it with your information.
-
 Information security risk assessment process ppt powerpoint presentation shapes cpb
Information security risk assessment process ppt powerpoint presentation shapes cpbPresenting this set of slides with name Information Security Risk Assessment Process Ppt Powerpoint Presentation Shapes Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Information Security Risk Assessment Process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Process of security risk assessment and audit
Process of security risk assessment and auditPresenting this set of slides with name Process Of Security Risk Assessment And Audit. The topics discussed in these slides are Process Security, Risk Assessment, Audit. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Organization security assessment process with monitor and mitigate
Organization security assessment process with monitor and mitigatePresenting this set of slides with name Organization Security Assessment Process With Monitor And Mitigate. This is a six stage process. The stages in this process are Monitor, Assessment, Analysis, Identify, Mitigate. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Security assessment process ppt powerpoint presentation portfolio portrait cpb
Security assessment process ppt powerpoint presentation portfolio portrait cpbPresenting our Security Assessment Process Ppt Powerpoint Presentation Portfolio Portrait Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Assessment Process This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Enhanced security event management insider attacker method and behaviour assessment ppt rules
Enhanced security event management insider attacker method and behaviour assessment ppt rulesThis slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Present the topic in a bit more detail with this Enhanced Security Event Management Insider Attacker Method And Behaviour Assessment Ppt Rules. Use it as a tool for discussion and navigation on Insider Attacker Method And Behaviour Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introducing information security risk assessment process workflow ppt portfolio
Introducing information security risk assessment process workflow ppt portfolioFollowing slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. Deliver an outstanding presentation on the topic using this Introducing Information Security Risk Assessment Process Workflow Ppt Portfolio. Dispense information and present a thorough explanation of Categorization, Prioritized Risks, System Characterization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.



