Powerpoint Templates and Google slides for Security Assessment
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Information security risk assessment plan for business management
Information security risk assessment plan for business managementIntroducing our premium set of slides with Information Security Risk Assessment Plan For Business Management. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Assessment, Business, Management. So download instantly and tailor it with your information.
-
 Risk management plan assessment metrics for improving it security
Risk management plan assessment metrics for improving it securityIntroducing our Risk Management Plan Assessment Metrics For Improving It Security set of slides. The topics discussed in these slides are Management, Assessment, Information. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security assessment process ppt powerpoint presentation portfolio portrait cpb
Security assessment process ppt powerpoint presentation portfolio portrait cpbPresenting our Security Assessment Process Ppt Powerpoint Presentation Portfolio Portrait Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Assessment Process This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 3 clusters slide for cloud native security assessments infographic template
3 clusters slide for cloud native security assessments infographic templateThis is a single slide titled 3 Clusters Slide For Cloud Native Security Assessments Infographic Template. It is crafted using high quality vector based visuals that are 100 percent editable and available for immediate download in standard and widescreen aspect ratios.
-
 Cloud native security assessment ppt powerpoint presentation summary layout ideas cpb
Cloud native security assessment ppt powerpoint presentation summary layout ideas cpbPresenting our Cloud Native Security Assessment Ppt Powerpoint Presentation Summary Layout Ideas Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cloud Native Security Assessment This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security control assessment ppt powerpoint presentation pictures sample cpb
Security control assessment ppt powerpoint presentation pictures sample cpbPresenting our Security Control Assessment Ppt Powerpoint Presentation Pictures Sample Cpb PowerPoint template design. This PowerPoint slide showcases seven stages. It is useful to share insightful information on Security Control Assessment This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Types security risk assessments ppt powerpoint presentation show ideas cpb
Types security risk assessments ppt powerpoint presentation show ideas cpbPresenting Types Security Risk Assessments Ppt Powerpoint Presentation Show Ideas Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Types Security Risk Assessments. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Security and data breach incident assessment
Security and data breach incident assessmentThis slide exhibits security and data breach incidence assessment model. It includes multiple sections such as- rules and regulations sharing with third parties, communication with incidence response team and so on. Presenting our set of slides with Security And Data Breach Incident Assessment. This exhibits information on six stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Survey, Limit, Learn, Engage, Record.
-
 Assessment matrix of cyber risks cyber security it ppt powerpoint presentation slide
Assessment matrix of cyber risks cyber security it ppt powerpoint presentation slideThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Increase audience engagement and knowledge by dispensing information using Assessment Matrix Of Cyber Risks Cyber Security IT Ppt Powerpoint Presentation Slide. This template helps you present information on one stages. You can also present information on Multifamily, Industrial, Health Care, Data Center, Retail using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enhanced security event management assessing different alternate sites for backup maintenance ppt outfit
Enhanced security event management assessing different alternate sites for backup maintenance ppt outfitThis slide portrays information regarding how firm will assess different alternate sites for backup maintenance on certain parameters such as implementation cost, hardware and telecommunication connection requirement, setup time, location. Present the topic in a bit more detail with this Enhanced Security Event Management Assessing Different Alternate Sites For Backup Maintenance Ppt Outfit. Use it as a tool for discussion and navigation on Implementation, Cost, Location, Telecommunication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enhanced security event management assessment of security maturity spectrum ppt gallery
Enhanced security event management assessment of security maturity spectrum ppt galleryThis slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an outstanding presentation on the topic using this Enhanced Security Event Management Assessment Of Security Maturity Spectrum Ppt Gallery. Dispense information and present a thorough explanation of Minimalists, Reactive, Concerned, Advanced, Security Mature using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enhanced security event management insider attacker method and behaviour assessment ppt rules
Enhanced security event management insider attacker method and behaviour assessment ppt rulesThis slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Present the topic in a bit more detail with this Enhanced Security Event Management Insider Attacker Method And Behaviour Assessment Ppt Rules. Use it as a tool for discussion and navigation on Insider Attacker Method And Behaviour Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security risk management assessment measures ways mitigate security management challenges
Security risk management assessment measures ways mitigate security management challengesThis slide shows a security risk management assessment checklist with multiple categories. Deliver an outstanding presentation on the topic using this Security Risk Management Assessment Measures Ways Mitigate Security Management Challenges. Dispense information and present a thorough explanation of Information Security Policy, Security Of Third Party Access, Responding To Security Threat Incidents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact assessment matrix information security risk management program
Impact assessment matrix information security risk management programPresent the topic in a bit more detail with this Impact Assessment Matrix Information Security Risk Management Program. Use it as a tool for discussion and navigation on Financial, Reputation, Regulatory. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information security risk assessment worksheet critical ppt visual aids icon
Information security risk assessment worksheet critical ppt visual aids iconMentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Deliver an outstanding presentation on the topic using this Information Security Risk Assessment Worksheet Critical Ppt Visual Aids Icon. Dispense information and present a thorough explanation of Asset And Consequences, Vulnerability, Operational using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information security risk assessment worksheet level ppt styles example
Information security risk assessment worksheet level ppt styles exampleThis slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Present the topic in a bit more detail with this Information Security Risk Assessment Worksheet Level Ppt Styles Example. Use it as a tool for discussion and navigation on Facilities And Equipment, Disclosure, Unauthorized. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introducing information security risk assessment process workflow ppt portfolio
Introducing information security risk assessment process workflow ppt portfolioFollowing slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. Deliver an outstanding presentation on the topic using this Introducing Information Security Risk Assessment Process Workflow Ppt Portfolio. Dispense information and present a thorough explanation of Categorization, Prioritized Risks, System Characterization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat identification assessment information security risk management program
Threat identification assessment information security risk management programThreat Agent, Potential Vulnerability, Vulnerability Ranking Deliver an outstanding presentation on the topic using this Threat Identification Assessment Information Security Risk Management Program. Dispense information and present a thorough explanation of Threat Agent, Potential Vulnerability, Vulnerability Ranking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security risk assessment implementing security management plan ppt portfolio information
Security risk assessment implementing security management plan ppt portfolio informationThis slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis. Present the topic in a bit more detail with this Security Risk Assessment Implementing Security Management Plan Ppt Portfolio Information. Use it as a tool for discussion and navigation on Threat, Perform, Organizations, Business. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise security operations assessing different alternate sites for backup maintenance ppt aids
Enterprise security operations assessing different alternate sites for backup maintenance ppt aidsThis slide portrays information regarding how firm will assess different alternate sites for backup maintenance on certain parameters such as implementation cost, hardware and telecommunication connection requirement, setup time, location. Present the topic in a bit more detail with this Enterprise Security Operations Assessing Different Alternate Sites For Backup Maintenance Ppt Aids. Use it as a tool for discussion and navigation on Implementation, Cost, Location, Telecommunication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise security operations assessment of security maturity spectrum ppt powerpoint visual aids
Enterprise security operations assessment of security maturity spectrum ppt powerpoint visual aidsThis slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an outstanding presentation on the topic using this Enterprise Security Operations Assessment Of Security Maturity Spectrum Ppt Powerpoint Visual Aids. Dispense information and present a thorough explanation of Minimalists, Reactive, Concerned, Advanced, Security Mature using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise security operations insider attacker method and behavior assessment ppt gridlines
Enterprise security operations insider attacker method and behavior assessment ppt gridlinesThis slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Present the topic in a bit more detail with this Enterprise Security Operations Insider Attacker Method And Behavior Assessment Ppt Gridlines. Use it as a tool for discussion and navigation on Insider Attacker Method And Behaviour Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
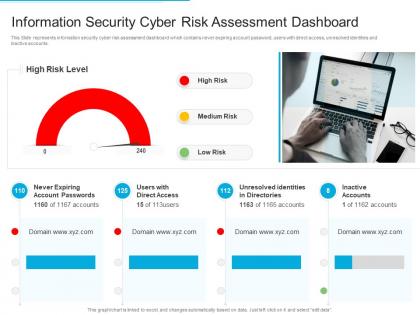 Information security cyber risk assessment dashboard
Information security cyber risk assessment dashboardPresenting our well structured Information Security Cyber Risk Assessment Dashboard. The topics discussed in this slide are Accounts, Risk. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information security dashboard depicting threat assessment
Information security dashboard depicting threat assessmentPresenting our well structured Information Security Dashboard Depicting Threat Assessment. The topics discussed in this slide are Implementation, Techniques. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information security risk assessments ppt powerpoint presentation model graphics example cpb
Information security risk assessments ppt powerpoint presentation model graphics example cpbPresenting this set of slides with name Information Security Risk Assessments Ppt Powerpoint Presentation Model Graphics Example Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Information Security Risk Assessments to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security risk management assessment checklist ppt ideas graphics tutorials
Security risk management assessment checklist ppt ideas graphics tutorialsThis slide shows a security risk management assessment checklist with multiple categories. Present the topic in a bit more detail with this Security Risk Management Assessment Checklist Ppt Ideas Graphics Tutorials. Use it as a tool for discussion and navigation on Security Policy, Identification Of Risks, Reporting Security, Security Awareness, Review And Evaluation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Assessing different alternate sites for backup maintenance security operations integration
Assessing different alternate sites for backup maintenance security operations integrationThis slide portrays information regarding how firm will assess different alternate sites for backup maintenance on certain parameters such as implementation cost, hardware and telecommunication connection requirement, setup time, location.Present the topic in a bit more detail with this Assessing Different Alternate Sites For Backup Maintenance Security Operations Integration. Use it as a tool for discussion and navigation on Implementation Cost, Hardware Equipment Requirement, Telecommunication Connection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Assessment of security maturity spectrum security operations integration ppt summary
Assessment of security maturity spectrum security operations integration ppt summaryThis slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security.Deliver an outstanding presentation on the topic using this Assessment Of Security Maturity Spectrum Security Operations Integration Ppt Summary. Dispense information and present a thorough explanation of Assessment Of Security Maturity Spectrum using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Insider attacker method and behaviour assessment security operations integration ppt themes
Insider attacker method and behaviour assessment security operations integration ppt themesThis slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver an outstanding presentation on the topic using this Insider Attacker Method And Behaviour Assessment Security Operations Integration Ppt Themes. Dispense information and present a thorough explanation of Insider Behavior, Insider Attack Method, Compromised Insider using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security management plan steps in detail risk assessment and analysis ppt guidelines
Security management plan steps in detail risk assessment and analysis ppt guidelinesThis slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Risk Assessment and Analysis. Deliver an outstanding presentation on the topic using this Security Management Plan Steps In Detail Risk Assessment And Analysis Ppt Guidelines. Dispense information and present a thorough explanation of Potential Consequence, Low, Medium, High, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 It security operations assessing different alternate sites for backup maintenance ppt gallery
It security operations assessing different alternate sites for backup maintenance ppt galleryThis slide portrays information regarding how firm will assess different alternate sites for backup maintenance on certain parameters such as implementation cost, hardware and telecommunication connection requirement, setup time, location. Present the topic in a bit more detail with this IT Security Operations Assessing Different Alternate Sites For Backup Maintenance Ppt Gallery. Use it as a tool for discussion and navigation on Implementation, Cost, Location, Telecommunication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It security operations assessment of security maturity spectrum ppt powerpoint ideas elements
It security operations assessment of security maturity spectrum ppt powerpoint ideas elementsThis slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an outstanding presentation on the topic using this IT Security Operations Assessment Of Security Maturity Spectrum Ppt Powerpoint Ideas Elements. Dispense information and present a thorough explanation of Minimalists, Reactive, Concerned, Advanced, Security Mature using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 It security operations insider attacker method and behaviour assessment ppt graphics tutorials
It security operations insider attacker method and behaviour assessment ppt graphics tutorialsThis slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Present the topic in a bit more detail with this IT Security Operations Insider Attacker Method And Behaviour Assessment Ppt Graphics Tutorials. Use it as a tool for discussion and navigation on Insider Attacker Method And Behaviour Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk assessment and analysis steps set up advanced security management plan ppt designs
Risk assessment and analysis steps set up advanced security management plan ppt designsThis slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Risk Assessment and Analysis. Present the topic in a bit more detail with this Risk Assessment And Analysis Steps Set Up Advanced Security Management Plan Ppt Designs. Use it as a tool for discussion and navigation on Security Management Plan Steps In Detail Risk Assessment And Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security risk management assessment checklist steps set up advanced security management plan
Security risk management assessment checklist steps set up advanced security management planThis slide shows a security risk management assessment checklist with multiple categories. Present the topic in a bit more detail with this Security Risk Management Assessment Checklist Steps Set Up Advanced Security Management Plan. Use it as a tool for discussion and navigation on Information Security Policy, Security Of Third Party Access, Responding To Security Threat Incidents. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Assessment Of SaaS Security Using KPI Dashboard
Assessment Of SaaS Security Using KPI DashboardThis slide showcases assessment of software as security to meet safety standards. This includes incidents, tasks, junctions, risk, risky incident analysis, quarterly incident status and several incidents. Introducing our Assessment Of SaaS Security Using KPI Dashboard set of slides. The topics discussed in these slides are Quarterly Incident Status, Risk Incidents Analysis, Several Incidents. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information Security System Audit And Risk Assessment
Information Security System Audit And Risk AssessmentThe following slide highlights the information security system audit and risk assessment illustrating key headings which includes security risk assessment, security auditing, security incident monitoring, security incident response Presenting our set of slides with name Information Security System Audit And Risk Assessment. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Risk Assessment, Security Auditing, Security Incident Monitoring.
-
 Comparative Assessment Of Security Audit Tools
Comparative Assessment Of Security Audit ToolsThis slide shows comparison of various security audit software to conduct vulnerability scans of network services. The purpose of this slide is to help businesses in selecting an efficient tool for managing threats and vulnerabilities across distributed network. Comparison is done on the basis of features, pricing and rating. Presenting our well structured Comparative Assessment Of Security Audit Tools. The topics discussed in this slide are Features, Pricing, Rating. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information Security Audit Icon For Vulnerability Assessment
Information Security Audit Icon For Vulnerability AssessmentPresenting our set of slides with Information Security Audit Icon For Vulnerability Assessment. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Information Security Audit, Icon For Vulnerability Assessment
-
 IT Security Audit Workflow For Risk Assessment
IT Security Audit Workflow For Risk AssessmentThis slide presents four step workflow for conducting an IT security audit. The purpose of this slide is to help businesses in managing operational risks and compliance activities. It covers tasks such as deciding assessment criteria, planning security audit, executing and sharing results. Presenting our set of slides with IT Security Audit Workflow For Risk Assessment. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Decide Assessment Criteria, Plan Security Audit, Execute Security Audit
-
 Email Security Employee Skill Assessment
Email Security Employee Skill AssessmentThe purpose of this slide is to highlight how Email security employee skill assessment ensures a proactive approach to identify and address potential vulnerabilities, enhancing the organizations defense against cyber threats. Presenting our well structured Email Security Employee Skill Assessment. The topics discussed in this slide are Awareness, Phishing Detection, Password Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 SaaS Security Maturity Assessment Analysis
SaaS Security Maturity Assessment AnalysisThis slide showcases SaaS security analysis to prevent data breaches and safeguards from cyber attacks. It constitutes three security levels basic, intermediate, and advanced based on that certain points are allocated and overall maturity is assessed. Presenting our well structured SaaS Security Maturity Assessment Analysis. The topics discussed in this slide are Prevents Access, Sensitive Data, Other Device. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.




