Powerpoint Templates and Google slides for Security Applications
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Applications Of Big Data Infrastructure Security
Applications Of Big Data Infrastructure SecurityThis slide represents the application infrastructure security in big data. Its objective is to manage application and examine the system for better efficiency. This slide includes network traffic examination, study of behaviour and cloud monitoring. Introducing our Applications Of Big Data Infrastructure Security set of slides. The topics discussed in these slides are Network, Behaviour, Evaluation. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Checklist To Protect Saas Applications
Cyber Security Checklist To Protect Saas ApplicationsThis slide represents cybersecurity checklist for SaaS applications to protect data. It aims to assist organizations in identifying potential vulnerabilities as well as examining security standards. It includes various elements such as backing up creation and testing, using real-time security service, etc. Introducing our Cyber Security Checklist To Protect Saas Applications set of slides. The topics discussed in these slides are Determines Data Isolation, Safeguards Against Data Theft This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Role Of Saas Applications In Cyber Security
Role Of Saas Applications In Cyber SecurityThis slide represents SaaS apps significance to cyber security. It aims to ensure continuous monitoring and updates to mitigate risks and protect sensitive data within applications. It includes various aspects such as authentication, leveraging data, etc. Introducing our premium set of slides with Role Of Saas Applications In Cyber Security Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Authentication, Enhanced Security, High Scalability, Strong Encryption. So download instantly and tailor it with your information.
-
 Applications Of Digital Solution For Ensuring Data Security
Applications Of Digital Solution For Ensuring Data SecurityThis slide showcases use cases of digital solution. The main purpose of this template is to showcase methods for optimizing resources in business. This includes streamlining operations, improving decision making, enabling remote work, etc. Presenting our set of slides with Applications Of Digital Solution For Ensuring Data Security This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Streamlining Operations, Enhancing Customer Experience, Improve Decision Making
-
 Analyzing Mobile Application Security Checklist
Analyzing Mobile Application Security ChecklistThis slide covers checklist to analyze mobile security for long-term scenarios and includes tasks, applicable and not applicable. Presenting our set of slides with name Analyzing Mobile Application Security Checklist. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Tasks, Applicable, Not Applicable.
-
 Impactful Areas Of Mobile Application Security
Impactful Areas Of Mobile Application SecurityThis slide exhibits key areas of testing applications based on mobile security and includes customer information, financial information, and cloning. Presenting our set of slides with name Impactful Areas Of Mobile Application Security. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Customer Information, Financial Information, Cloning.
-
 Mobile Application Security Risk Assessment
Mobile Application Security Risk AssessmentThis slide demonstrates mobile application security to assess risks and includes improper platform usage, insecure data storage, and insecure communication. Presenting our set of slides with name Mobile Application Security Risk Assessment. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Improper Platform Usage, Insecure Data Storage, Insecure Communication.
-
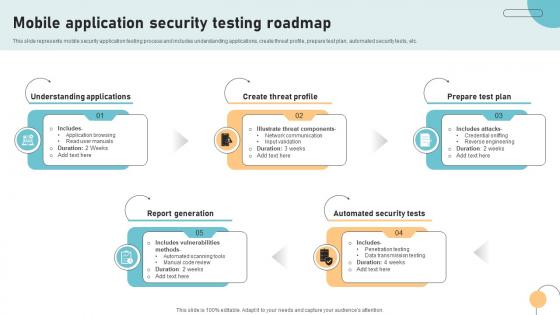 Mobile Application Security Testing Roadmap
Mobile Application Security Testing RoadmapThis slide represents mobile security application testing process and includes understanding applications, create threat profile, prepare test plan, automated security tests, etc. Presenting our set of slides with name Mobile Application Security Testing Roadmap. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Understanding Applications, Report Generation, Create Threat Profile, Automated Security Tests, Prepare Test Plan.
-
 Cyber Security Mesh Applications For Business
Cyber Security Mesh Applications For BusinessThe following slide features key elements like IAM support, MSSPS, identity-proofing tools, standards, and demographic bias in illustrating the diverse applications of cybersecurity mesh for business. This aids in understanding its potential impact on security and operations. Presenting our set of slides with Cyber Security Mesh Applications For Business This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Mesh Supporting Iam Requests, Identity Life Cycle, Decentralized Identity Standards
-
 Addressing Mobile Application Security Gap For Risk Protection
Addressing Mobile Application Security Gap For Risk ProtectionFollowing slide showcases application security vulnerabilities of mobiles for risk protection. It further includes factors such as poor server-side controls, accidental data leak, poor authorization alongside description, solution, etc. Introducing our Addressing Mobile Application Security Gap For Risk Protection set of slides. The topics discussed in these slides are Poor Server Side Controls, Accidental Data Leak, Poor Authorization, Solution. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Checklists For Security Gap Web Application
Checklists For Security Gap Web ApplicationThis slide highlights a security vulnerability web application checklist for mitigation of risks. It further covers authentication of all files for configuration and authentication of all cyber variables alongside priority and responsible person. Introducing our Checklists For Security Gap Web Application set of slides. The topics discussed in these slides are Data Received, Semantics For Exception Handling, Cyber Variables. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis Of Security Gap Software Application
Comparative Analysis Of Security Gap Software ApplicationFollowing slide highlights software applications security gap analysis for enhanced user trust. It further covers tools, best used for, free trial, price and rating along with deployment such as desktop app, on-premise and web hosted etc. Introducing our Comparative Analysis Of Security Gap Software Application set of slides. The topics discussed in these slides are Tool, Deployment, Free Trial, Price, Our Rating. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Crypto Tokens Unlocking Applications Of Security Tokens For Real World Assets BCT SS
Crypto Tokens Unlocking Applications Of Security Tokens For Real World Assets BCT SSThis slide covers key use cases of security tokens for real-world assets tokenization. It includes real estate tokenization, artwork ownership tokens, commodities tokenization, revenue-sharing agreements, etc. Increase audience engagement and knowledge by dispensing information using Crypto Tokens Unlocking Applications Of Security Tokens For Real World Assets BCT SS This template helps you present information on Five stages. You can also present information on Artwork Ownership Tokens, Revenue-Sharing Agreements using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Crypto Tokens Unlocking Other Major Applications Of Security Tokens BCT SS
Crypto Tokens Unlocking Other Major Applications Of Security Tokens BCT SSThis slide covers various other use cases of security tokens. It includes application areas such as identity verification, secure communication, access control, and payment processing. Deliver an outstanding presentation on the topic using this Crypto Tokens Unlocking Other Major Applications Of Security Tokens BCT SS Dispense information and present a thorough explanation of Identity Verification, Secure Communication, Access Control using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 ACH Payment Application Impact On Business Enhancing Transaction Security With E Payment
ACH Payment Application Impact On Business Enhancing Transaction Security With E PaymentMentioned slide provides insights into ACH payment method impact on business transactions. It includes key points such as pay recurring bills, lower transaction costs, easy remote payment, and improve sales conversion. Introducing ACH Payment Application Impact On Business Enhancing Transaction Security With E Payment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Pay Recurring Bills, Lower Transaction Cost, Easy Remote Payment using this template. Grab it now to reap its full benefits.
-
 Comparative Assessment Of Multiple Mobile Wallet Applications Enhancing Transaction Security With E Payment
Comparative Assessment Of Multiple Mobile Wallet Applications Enhancing Transaction Security With E PaymentFollowing slide shows comparative analysis of multiple types of mobile wallet which can be leverages by business to go contactless. It includes key components such as features, transaction level, payment fees, transaction time, security and type of wallet. Present the topic in a bit more detail with this Comparative Assessment Of Multiple Mobile Wallet Applications Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Features, Transaction Level, Payment Fees This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Assessment Of Mobile Wallet Application Enhancing Transaction Security With E Payment
Impact Assessment Of Mobile Wallet Application Enhancing Transaction Security With E PaymentMentioned slide provides information about mobile wallet payment implementation impact on business activities. It includes impacts such as easy customer data analytics, offer reward and loyalty points, smooth workflow, and improved security. Increase audience engagement and knowledge by dispensing information using Impact Assessment Of Mobile Wallet Application Enhancing Transaction Security With E Payment This template helps you present information on four stages. You can also present information on Easy Customer Data Analytics, Smooth Workflow, Improved Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Applications Of Oracle Database Crypto Secure Exploring Diverse Blockchain BCT SS
Applications Of Oracle Database Crypto Secure Exploring Diverse Blockchain BCT SSThis slide covers key use cases of Oracle Database Crypto-Secure Data Management such as healthcare data protection, financial transactions, government data security, retail customer privacy, and intellectual property protection. Deliver an outstanding presentation on the topic using this Applications Of Oracle Database Crypto Secure Exploring Diverse Blockchain BCT SS Dispense information and present a thorough explanation of Healthcare Data, Financial Transactions, Customer Privacy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Owasp Mobile Application Security Architecture
Owasp Mobile Application Security ArchitectureThis slide is a representation of architecture of mobile application security design which includes requirements, design, verification and rulebooks. Presenting our well structured Owasp Mobile Application Security Architecture. The topics discussed in this slide are Mobile Application, Security Architecture, Verification And Rulebooks. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Improvement In Mobile Application Development
Security Improvement In Mobile Application DevelopmentThis slide highlights the different ways to improve security in mobile application development which includes enforce updates, enable two factor authentication, etc. Introducing our premium set of slides with name Security Improvement In Mobile Application Development. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Improvement, Mobile Application Development, Handle Sensitive Data Carefully. So download instantly and tailor it with your information.
-
 30 60 90 Days Plan Of Application Security Ppt Diagram Graph Charts
30 60 90 Days Plan Of Application Security Ppt Diagram Graph ChartsThis slide depicts the 30 60 90 days plan for application security which includes tasks such as assessment, security implementation, etc. Present the topic in a bit more detail with this 30 60 90 Days Plan Of Application Security Ppt Diagram Graph Charts. Use it as a tool for discussion and navigation on Security Implementation, Assessment Phase, Training And Awareness, Application Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Access Control Safeguards In Application Security Ppt Diagram Templates
Access Control Safeguards In Application Security Ppt Diagram TemplatesThis slide highlights the introduction of access control safeguards in application security for preventing malicious attacks in applications. Introducing Access Control Safeguards In Application Security Ppt Diagram Templates to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identity Confirmation, Regulating Resource Interaction, Application Security, using this template. Grab it now to reap its full benefits.
-
 Agenda For Application Security Ppt File Background Images
Agenda For Application Security Ppt File Background ImagesIncrease audience engagement and knowledge by dispensing information using Agenda For Application Security Ppt File Background Images. This template helps you present information on four stages. You can also present information on Application Security, Authentication, Authorization, Security Testing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Case Study Kroll Ppt File Infographic Template
Application Security Case Study Kroll Ppt File Infographic TemplateThis slide highlights the overview of the company, problems faced, and their related solutions in the case study. Deliver an outstanding presentation on the topic using this Application Security Case Study Kroll Ppt File Infographic Template. Dispense information and present a thorough explanation of Risk To Data Security, Urgent App Security Scaling, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Comparative Analysis Of Vulnerability Scanning And Penetration Testing
Application Security Comparative Analysis Of Vulnerability Scanning And Penetration TestingThis slide showcases the difference between vulnerability scanning and penetration testing based on aspects such as nature, purpose, etc. Present the topic in a bit more detail with this Application Security Comparative Analysis Of Vulnerability Scanning And Penetration Testing. Use it as a tool for discussion and navigation on Explores Weaknesses In Systems, Comparative Analysis, Vulnerability Scanning, Penetration Testing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security For Table Of Contents Ppt File Background Designs
Application Security For Table Of Contents Ppt File Background DesignsDeliver an outstanding presentation on the topic using this Application Security For Table Of Contents Ppt File Background Designs. Dispense information and present a thorough explanation of Web Security, Deployment And Monitoring, Performance Monitoring Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Main Goals Of Application Level Encryption
Application Security Main Goals Of Application Level EncryptionThis slide showcases the objectives of application-level encryption in application security which include data protection, increased security, etc. Introducing Application Security Main Goals Of Application Level Encryption to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Enhanced Data Protection, Compliance Simplification, Security Against Insider Threats, using this template. Grab it now to reap its full benefits.
-
 Application Security Setting Up Access Control System In Organization
Application Security Setting Up Access Control System In OrganizationThis slide represents the installation process of access control system for application security in an organization. Increase audience engagement and knowledge by dispensing information using Application Security Setting Up Access Control System In Organization. This template helps you present information on ten stages. You can also present information on Combine Tools With Infrastructure, Implement And Utilize Tools, Select Access Control Models using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Testing Tool Pyramid Ppt File Background Image
Application Security Testing Tool Pyramid Ppt File Background ImageThis slide represents the application security testing tool pyramid which includes tools such as correlation tools, test coverage analysis, etc. Introducing Application Security Testing Tool Pyramid Ppt File Background Image to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Application Security, Testing Tool Pyramid, Test Coverage Analysis, Correlation Tools, using this template. Grab it now to reap its full benefits.
-
 Application Security Testing Tools Reference Model Ppt File Infographics
Application Security Testing Tools Reference Model Ppt File InfographicsThis slide showcases the application security testing tools reference model along with the workflow. Deliver an outstanding presentation on the topic using this Application Security Testing Tools Reference Model Ppt File Infographics. Dispense information and present a thorough explanation of Software Composition Analysis, Static Application Security Testing, Dynamic Application Security Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Tools For Vulnerability Scanning In Security Testing
Application Security Tools For Vulnerability Scanning In Security TestingThis slide highlights the tools used for vulnerability scanning in security testing in application security which include Acunetix, Akto, etc. Present the topic in a bit more detail with this Application Security Tools For Vulnerability Scanning In Security Testing. Use it as a tool for discussion and navigation on Tools For Vulnerability, Scanning In Security Testing, Application Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Training Schedule For IT Teams
Application Security Training Schedule For IT TeamsThis slide represents the training schedule for IT teams in an organization to efficiently implementing application security. Deliver an outstanding presentation on the topic using this Application Security Training Schedule For IT Teams. Dispense information and present a thorough explanation of Application Security Fundamentals, Application Security Deployment, Application Security Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Authentication In Application Security For Data Protection
Authentication In Application Security For Data ProtectionThis slide discusses about the overview of authentication in application security and the various elements of MFA. Increase audience engagement and knowledge by dispensing information using Authentication In Application Security For Data Protection. This template helps you present information on five stages. You can also present information on Knowledge Factor, Possession Factor, Biometric Factor, Data Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Authorization In Application Security For Data Privacy
Authorization In Application Security For Data PrivacyThis slide discusses the overview of authorization in application security for authorized access of resource. Increase audience engagement and knowledge by dispensing information using Authorization In Application Security For Data Privacy. This template helps you present information on five stages. You can also present information on Application Security, Data Privacy, Helps Servers Identify Clients using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Before Vs After Implementation Of Application Security
Before Vs After Implementation Of Application SecurityThis slide discusses the overview of authorization in application security for authorized access of resource. Introducing Before Vs After Implementation Of Application Security to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Implement Encryption Protocols, Patch Management System, Vulnerable Authentication Mechanisms, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Implementing Application Security
Best Practices For Implementing Application SecurityThis slide discusses the best approaches for application security deployment which include assess threats, shift security left, control rights, etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Implementing Application Security. This template helps you present information on five stages. You can also present information on Shift Security Left, Track Application Security Outcomes, Assess Threats, Application Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Budget Allocation For Implementing Application Security
Budget Allocation For Implementing Application SecurityThis slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc. Present the topic in a bit more detail with this Budget Allocation For Implementing Application Security. Use it as a tool for discussion and navigation on Budget Allocation, Application Security, Technology Cost Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Capturing Security Events For Log Management Application Security
Capturing Security Events For Log Management Application SecurityThis slide discusses the selection of security events that need to be logged for application security to ensure user accountability. Introducing Capturing Security Events For Log Management Application Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Authentication Events, User Privilege Changes, Configuration Settings Changes, using this template. Grab it now to reap its full benefits.
-
 Checklist To Implement Effective Application Security
Checklist To Implement Effective Application SecurityThis slide showcases the actions performed while deploying application security, person responsible, status and comments for the same. Deliver an outstanding presentation on the topic using this Checklist To Implement Effective Application Security. Dispense information and present a thorough explanation of Assessment And Planning, Education And Training, Patch Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Native Application Security Overview Ppt File Design Templates
Cloud Native Application Security Overview Ppt File Design TemplatesThe purpose of this slide is to highlight the introduction of second type of web security, that is, cloud native application security. Increase audience engagement and knowledge by dispensing information using Cloud Native Application Security Overview Ppt File Design Templates. This template helps you present information on five stages. You can also present information on Secure Configurations, Early Focus Crucial, Cloud Native Application, Security Overview using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Concerns And Solution For Application Security Deployment
Concerns And Solution For Application Security DeploymentThis slide outlines the problems and relevant solutions of application security deployment to ensure smooth functioning. Present the topic in a bit more detail with this Concerns And Solution For Application Security Deployment. Use it as a tool for discussion and navigation on Implement Strict Input Validation, Employ Bot Detection Mechanisms, Application Security Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Encryption Features In Application Security
Data Encryption Features In Application SecurityThis slide outlines the characteristics of encryption in application security such as security, easy-to-use, document support, etc. Introducing Data Encryption Features In Application Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implement Strict Input Validation, Employ Bot Detection Mechanisms, Application Security Deployment, using this template. Grab it now to reap its full benefits.
-
 Data Encryption Method In Application Security
Data Encryption Method In Application SecurityThis slide outlines the characteristics of encryption in application security such as security, easy-to-use, document support, etc. Increase audience engagement and knowledge by dispensing information using Data Encryption Method In Application Security. This template helps you present information on five stages. You can also present information on Encodes Plaintext To Ciphertext, Decryption Needs Specific Keys, Create Cryptographic Models using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Difference Between Authentication And Authorization In Application Security
Difference Between Authentication And Authorization In Application SecurityThis slide showcase the difference between authentication and authorization in application security on aspects such as purpose, operation, etc. Deliver an outstanding presentation on the topic using this Difference Between Authentication And Authorization In Application Security. Dispense information and present a thorough explanation of Confirms Credentials, Authentication, Authorization, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Five Step Roadmap To Implement Application Security
Five Step Roadmap To Implement Application SecurityThis slide outlines the steps to deploy application security in organization such as defining objectives, planning, monitoring, etc. Introducing Five Step Roadmap To Implement Application Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Monitoring And Logging, Education And Planning, Five Step Roadmap, Application Security, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Application Security Ppt File Designs Download
Icons Slide For Application Security Ppt File Designs DownloadPresenting our well crafted Icons Slide For Application Security Ppt File Designs Download set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Introduction Of Application Security For Data Privacy
Introduction Of Application Security For Data PrivacyThis slide discusses the overview of application security which includes its objectives such as protecting data, minimize risk, etc. Increase audience engagement and knowledge by dispensing information using Introduction Of Application Security For Data Privacy. This template helps you present information on four stages. You can also present information on Covers Post Deployment Protection, Protects Data And Code, Application Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Benefits Of Implementing Application Security
Key Benefits Of Implementing Application SecurityThis slide highlights the key advantages of application security which include minimum risk exposure, security, etc. Introducing Key Benefits Of Implementing Application Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Safeguards Sensitive Information, Preserves The Brand Reputation, Minimizes Risk, using this template. Grab it now to reap its full benefits.
-
 Log Management Process In Application Security
Log Management Process In Application SecurityThis slide showcases the introduction of log management in application security for decreasing the security threats. Increase audience engagement and knowledge by dispensing information using Log Management Process In Application Security. This template helps you present information on five stages. You can also present information on Handling Security Logs, Non Compliance Risks Attacks, Ensure Data Security, Log Management Process using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Main Features For Robust Application Security
Main Features For Robust Application SecurityThis slide outlines the key characteristics of application security which include authentication, authorization, encryption, logging, etc. Introducing Main Features For Robust Application Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Authorization, Application Security Testing, Robust Application Security, using this template. Grab it now to reap its full benefits.
-
 Major Impact Of Application Security On Organization
Major Impact Of Application Security On OrganizationThis slide showcases the after application security impact on business along with factors that have improved the overall performance. Increase audience engagement and knowledge by dispensing information using Major Impact Of Application Security On Organization. This template helps you present information on five stages. You can also present information on Application Attacks, Application Security, Security Increase using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Process Phases Of Penetration Testing In Application Security
Process Phases Of Penetration Testing In Application SecurityThis slide highlights the steps for implementing penetration testing which include planning and reconnaissance, gaining access, etc. Introducing Process Phases Of Penetration Testing In Application Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Planning And Reconnaissance, Gaining Access, Maintaining Access, Analysis And WAF Configuration, using this template. Grab it now to reap its full benefits.
-
 Security Log Management Best Practices Application Security
Security Log Management Best Practices Application SecurityThis slide highlights the best approaches of logging implementation which include preventing inappropriate actions, employ logging tools, etc. Increase audience engagement and knowledge by dispensing information using Security Log Management Best Practices Application Security. This template helps you present information on five stages. You can also present information on Scrutinize Admin And Operators, Prevent Inappropriate Actions, Ensure Authorized Activities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Testing Types Code Review Application Security
Security Testing Types Code Review Application SecurityThis slide outlines the introduction of secure code review in application security for efficient working of an application. Introducing Security Testing Types Code Review Application Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Ensures Application Safety, Identify Code Vulnerabilities Collaboratively, Manual Review Of Source Code, using this template. Grab it now to reap its full benefits.
-
 Security Testing Types Penetration Testing Application Security
Security Testing Types Penetration Testing Application SecurityThis slide discusses the overview of penetration testing for application security which includes the purpose of penetration testing. Increase audience engagement and knowledge by dispensing information using Security Testing Types Penetration Testing Application Security. This template helps you present information on five stages. You can also present information on Enhances Web Security, Simulated System Vulnerability Check, Identifies App Weaknesses, Detects Input Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Testing Types Vulnerability Scanning Application Security
Security Testing Types Vulnerability Scanning Application SecurityThis slide outlines the overview of vulnerability scanning in security testing for application security. Introducing Security Testing Types Vulnerability Scanning Application Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Assessing Security Readiness, Integral To Safeguarding Organizations, Identify System Security Weaknesses, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Application Security Ppt File Slide Download
Table Of Contents For Application Security Ppt File Slide DownloadIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Application Security Ppt File Slide Download. This template helps you present information on eleven stages. You can also present information on Concerns And Solution, Impact Of Web Security, Training And Budget, Security Testing Types using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline For Implementing Efficient Application Security
Timeline For Implementing Efficient Application SecurityThis slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc. Introducing Timeline For Implementing Efficient Application Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Patch Management, Incident Response Planning, Planning Phase, Education And Training, using this template. Grab it now to reap its full benefits.
-
 Top Five Application Security Trends Ppt File Example Introduction
Top Five Application Security Trends Ppt File Example IntroductionThis slide showcases the five trends of application security which include, AppSec and CloudSec merge, expanding attack surfaces, etc. Increase audience engagement and knowledge by dispensing information using Top Five Application Security Trends Ppt File Example Introduction. This template helps you present information on five stages. You can also present information on Heightened Vulnerability, Prioritization Demand, Expanding Attack Surfaces, Appsec And Cloudsec Merge using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Top Web Application Security Threats Ppt File Example Topics
Top Web Application Security Threats Ppt File Example TopicsThis slide discusses the vulnerabilities and security threats in web application such as SQL injection, cross-site scripting, etc. Deliver an outstanding presentation on the topic using this Top Web Application Security Threats Ppt File Example Topics. Dispense information and present a thorough explanation of Cross Site Request Forgery, Insecure Direct Object References, Web Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





