Powerpoint Templates and Google slides for Security And Operational
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Facilitating it security and operations powerpoint presentation slides
Facilitating it security and operations powerpoint presentation slidesPresenting our illustrative facilitating IT security and operations PowerPoint template. This PPT presentation is available for download in both standard and widescreen formats. You can easily edit the content inside the PPT design. It is compatible with all prominent presentation software, including Microsoft Office and Google Slides, among others. This PPT slide can also be edited for print and digital formats such as JPEG, PNG, and PDF.
-
 Security and operations integration powerpoint presentation slides
Security and operations integration powerpoint presentation slidesPresenting our security and operations integration PowerPoint presentation slides. This PowerPoint design contains fifty-three slides in it which can be completely customized and edited. It is available for both standard as well as for widescreen formats. This PowerPoint template is compatible with all the presentation software like Microsoft Office, Google Slides, etc. You can download this PPT layout from below.
-
 Implementing Identity And Access Management For Operational Security OPSEC Training Ppt
Implementing Identity And Access Management For Operational Security OPSEC Training PptPresenting Implementing Identity and Access Management for Operational Security OPSEC. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Overview Of Key KPMG Cyber Security KPMG Operational And Marketing Strategy SS V
Overview Of Key KPMG Cyber Security KPMG Operational And Marketing Strategy SS VThis slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights Increase audience engagement and knowledge by dispensing information using Overview Of Key KPMG Cyber Security KPMG Operational And Marketing Strategy SS V. This template helps you present information on five stages. You can also present information on Digital, Security, Automation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Role Of ZTNA To Improve Business Operations And Security Zero Trust Security Model
Role Of ZTNA To Improve Business Operations And Security Zero Trust Security ModelThis slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Deliver an outstanding presentation on the topic using this Role Of ZTNA To Improve Business Operations And Security Zero Trust Security Model. Dispense information and present a thorough explanation of Enhanced User Experience, Remote Workforce Protection, Improve Data Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Zero Trust Security Model
Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Zero Trust Security ModelThis slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Deliver an outstanding presentation on the topic using this Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Zero Trust Security Model. Dispense information and present a thorough explanation of Operational, Implement, Performance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Response Plan Secure Operations Data Breach Prevention And Mitigation
Data Breach Response Plan Secure Operations Data Breach Prevention And MitigationThis slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. Present the topic in a bit more detail with this Data Breach Response Plan Secure Operations Data Breach Prevention And Mitigation. Use it as a tool for discussion and navigation on Assemble Expert Team, Consult With Legal Counsel, Secure Physical Areas. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Operating Model In Powerpoint And Google Slides Cpb
Security Operating Model In Powerpoint And Google Slides CpbPresenting our Security Operating Model In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Operating Model This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Buying Securities Open Market Operations In Powerpoint And Google Slides Cpb
Buying Securities Open Market Operations In Powerpoint And Google Slides CpbPresenting Buying Securities Open Market Operations In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Buying Securities, Open Market, Operations. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Secops V2 Challenges And Solutions Of Security Operations Centres
Secops V2 Challenges And Solutions Of Security Operations CentresThis slide outlines the key challenges and solutions of security operations centers. The purpose of this slide is to highlight the problems faced by SOC teams and methods to overcome those problems. The main challenges include talent gaps, sophisticated attackers, increased data and network traffic, etc. Present the topic in a bit more detail with this Secops V2 Challenges And Solutions Of Security Operations Centres. Use it as a tool for discussion and navigation on Challenges And Solutions, Security Operations Centres, Sophisticated Attackers, Data And Network Traffic. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secops V2 Roles And Responsibilities Of Security Operations Center Team
Secops V2 Roles And Responsibilities Of Security Operations Center TeamThis slide outlines the roles and responsibilities of the security operations center team. The purpose of this slide is to showcase the roles as well as duties of the SOC team. The prominent roles include incident responder, security investigator, advanced security analyst, SOC manager, and security engineer. Introducing Secops V2 Roles And Responsibilities Of Security Operations Center Team to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Incident Responder, Security Investigator, Advanced Security Analyst, Security Engineer Or Architect, using this template. Grab it now to reap its full benefits.
-
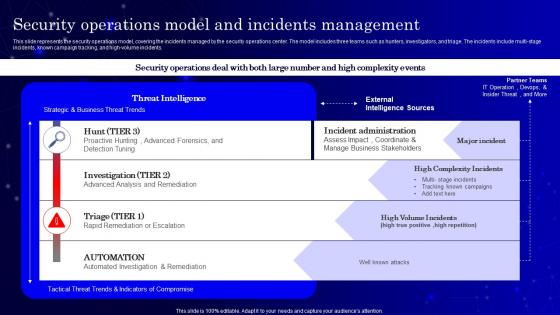 Secops V2 Security Operations Model And Incidents Management
Secops V2 Security Operations Model And Incidents ManagementThis slide represents the security operations model, covering the incidents managed by the security operations center. The model includes three teams such as hunters, investigators, and triage. The incidents include multi-stage incidents, known campaign tracking, and high-volume incidents. Present the topic in a bit more detail with this Secops V2 Security Operations Model And Incidents Management. Use it as a tool for discussion and navigation on Security Operations Model, Incidents Management, Known Campaign Tracking, Rapid Remediation Or Escalation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secops V2 Tools And Technologies Used In Security Operations Center
Secops V2 Tools And Technologies Used In Security Operations CenterThis slide highlights the crucial tools and technologies used in the SecOps environment. The purpose of this slide is to showcase the various tools and techniques a SOC requires. The main tools include log collection and management, vulnerability management, security information, and event management, etc. Deliver an outstanding presentation on the topic using this Secops V2 Tools And Technologies Used In Security Operations Center. Dispense information and present a thorough explanation of Vulnerability Management, Log Collection And Management Tool, Security Information And Event Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview And Importance Of Streamlining Security Operations Leveraging ChatGPT AI SS V
Overview And Importance Of Streamlining Security Operations Leveraging ChatGPT AI SS VThis slide showcases overview of streamlining security operations which can help organization to prevent cyber attacks in organization. It also highlight various benefits of streamlining security operations such as timely incident response, vulnerability assessment, reduction in cyber attacks etc. Present the topic in a bit more detail with this Overview And Importance Of Streamlining Security Operations Leveraging ChatGPT AI SS V Use it as a tool for discussion and navigation on Threat Intelligence, Overview Of Threat, Importance Of Threat This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Devsecops Development Security And Operations
Devsecops Best Practices For Secure Devsecops Development Security And OperationsThis slide discusses the working process of development, security and operations in DevSecOps. The purpose of this slide is to highlight the process followed by DevSecOps for providing, monitoring and managing security at each level of the software system. Introducing Devsecops Best Practices For Secure Devsecops Development Security And Operations to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Development, Security, Operations, Code Expedites Development, using this template. Grab it now to reap its full benefits.
-
 Chatgpt Security Operations Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
Chatgpt Security Operations Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases various ChatGPT use cases for streamlining and automating the cybersecurity operations of organization. Its key elements are establish security policies, automate repetitive tasks and identification of vulnerabilities Increase audience engagement and knowledge by dispensing information using Chatgpt Security Operations Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V. This template helps you present information on three stages. You can also present information on Streamlining, Operations, Identify Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview And Security Operations Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V
Overview And Security Operations Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS VThis slide showcases overview of streamlining security operations which can help organization to prevent cyber attacks in organization. It also highlight various benefits of streamlining security operations such as timely incident response, vulnerability assessment, reduction in cyber attacks etc. Deliver an outstanding presentation on the topic using this Overview And Security Operations Chatgpt For Threat Intelligence And Vulnerability Assessment AI SS V. Dispense information and present a thorough explanation of Overview, Streamlining, Operations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Case Study 1 Enhancing Operational Technology IoT Security And Privacy Safeguarding IoT SS
Case Study 1 Enhancing Operational Technology IoT Security And Privacy Safeguarding IoT SSThis slide includes a case study of the company providing operational digital safety solutions integrating Cisco technology to enhance visibility at scale. It includes elements such as objectives of company , solutions implemented, and results. Introducing Case Study 1 Enhancing Operational Technology IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Operational Technology, Identify Service Engine, Security Posture, using this template. Grab it now to reap its full benefits.
-
 Role Of ZTNA To Improve Business Operations And Security Identity Defined Networking
Role Of ZTNA To Improve Business Operations And Security Identity Defined NetworkingThis slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Present the topic in a bit more detail with this Role Of ZTNA To Improve Business Operations And Security Identity Defined Networking. Use it as a tool for discussion and navigation on Traditional Method, Workforce Protection, Data Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Zero Trust Architecture ZTA Role Of ZTNA To Improve Business Operations And Security
Zero Trust Architecture ZTA Role Of ZTNA To Improve Business Operations And SecurityThis slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Introducing Zero Trust Architecture ZTA Role Of ZTNA To Improve Business Operations And Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Traditional Method, ZTNA Approach, Login Capability, using this template. Grab it now to reap its full benefits.
-
 Overview And Importance Of Streamlining Security Operations Impact Of Generative AI SS V
Overview And Importance Of Streamlining Security Operations Impact Of Generative AI SS VThis slide showcases overview of streamlining security operations which can help organization to prevent cyber attacks in organization. It also highlight various benefits of streamlining security operations such as timely incident response, vulnerability assessment, reduction in cyber attacks etc. Increase audience engagement and knowledge by dispensing information using Overview And Importance Of Streamlining Security Operations Impact Of Generative AI SS V. This template helps you present information on four stages. You can also present information on Organization Infrastructure, Cyber Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Roles And Responsibilities Of Security Operations Center
Roles And Responsibilities Of Security Operations CenterThe following slide illustrates the roles and responsibility framework of security operations center organization that manages security infrastructure. The different levels of responsibility are triage specialist, incident responder, etc. Presenting our well structured Roles And Responsibilities Of Security Operations Center. The topics discussed in this slide are Security Consultant, External Personnel. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Operations Center Challenges And Solutions
Security Operations Center Challenges And SolutionsThe below slide provides the various challenges faced by security operations center along with the solutions implemented to overcome them. The different categories of challenges are talent gap, 3rd part attacks, etc. Introducing our Security Operations Center Challenges And Solutions set of slides. The topics discussed in these slides are Timeline, Aspect, Challenge, Risk Level. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Technology Trends And Impact Of Security Operations Center
Technology Trends And Impact Of Security Operations CenterThe following slide represents the technological trends of security operations center along with their impact on security. The various trends are rise in adoption of cloud deployment, increased use of AI and ML, etc. Presenting our set of slides with name Technology Trends And Impact Of Security Operations Center. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Impact, MDR Security Assessment.
-
 Tool And Technologies For Security Operations Center
Tool And Technologies For Security Operations CenterThe following slide showcases the various tools that are used in functioning of security operations center for effective monitoring and prevention of threats. The different tools are log collection and management, endpoint detection, etc. Introducing our premium set of slides with name Tool And Technologies For Security Operations Center. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Log Collection And Management, Endpoint Detection And Response. So download instantly and tailor it with your information.
-
 Security Operations Dashboard For Detection And Response Effectiveness
Security Operations Dashboard For Detection And Response EffectivenessThis slide exhibits security operations dashboard. It include positive incidents, false positive incidents, false positive risk score, false positive security incident etc. Introducing our Security Operations Dashboard For Detection And Response Effectiveness set of slides. The topics discussed in these slides are Security Operations Dashboard, Detection, Response Effectiveness. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Operational Technology Security Challenges And Solutions To Overcome
Operational Technology Security Challenges And Solutions To OvercomeMentioned slide illustrates various operational technology OT security challenges. It also cover information about the multiple solutions which will assist organization to overcome challenges and build a strong security IT system. Introducing Operational Technology Security Challenges And Solutions To Overcome to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Challenges, Solutions, Employees, using this template. Grab it now to reap its full benefits.
-
 Company Operations In Us And Canada Home Security Systems Company Profile
Company Operations In Us And Canada Home Security Systems Company ProfileThis slide showcases the security company current operations in USA and Canada through map. It includes the total states covered of USA and Canada along which total served customers. Present the topic in a bit more detail with this Company Operations In Us And Canada Home Security Systems Company Profile . Use it as a tool for discussion and navigation on Company Operations In US And Canada. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Security Lock Operations Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Enterprise Security Lock Operations Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Enterprise security lock operations colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Enterprise Security Lock Operations Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Enterprise Security Lock Operations Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Enterprise security lock operations monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Enterprise Security Operations Monitoring Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Enterprise Security Operations Monitoring Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Enterprise security operations monitoring colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Enterprise Security Operations Monitoring Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Enterprise Security Operations Monitoring Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Enterprise security operations monitoring monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Enterprise Security Operations Processing Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Enterprise Security Operations Processing Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Enterprise security operations processing colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Enterprise Security Operations Processing Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Enterprise Security Operations Processing Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Enterprise security operations processing monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Company Operations In Us And Canada Smart Security Systems Company Profile Ppt Show Format Ideas
Company Operations In Us And Canada Smart Security Systems Company Profile Ppt Show Format IdeasThis slide showcases the security company current operations in USA and Canada through map. It includes the total states covered of USA and Canada along which total served customers. Present the topic in a bit more detail with this Company Operations In Us And Canada Smart Security Systems Company Profile Ppt Show Format Ideas. Use it as a tool for discussion and navigation on Operations, Canadian Provinces, Customers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Competitive Operations And Financials Performance Analysis Smart Security Systems Company Profile
Competitive Operations And Financials Performance Analysis Smart Security Systems Company ProfileThis slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count. Deliver an outstanding presentation on the topic using this Competitive Operations And Financials Performance Analysis Smart Security Systems Company Profile. Dispense information and present a thorough explanation of Competitive, Operations, Performance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Company Operations In Us And Canada Security Alarm And Monitoring Systems Company Profile
Company Operations In Us And Canada Security Alarm And Monitoring Systems Company ProfileThis slide showcases the security company current operations in USA and Canada through map. It includes the total states covered of USA and Canada along which total served customers. Present the topic in a bit more detail with this Company Operations In Us And Canada Security Alarm And Monitoring Systems Company Profile. Use it as a tool for discussion and navigation on Company, Operations, Customers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Competitive Operations And Financials Performance Security Alarm And Monitoring Systems Company Profile
Competitive Operations And Financials Performance Security Alarm And Monitoring Systems Company ProfileThis slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count. Deliver an outstanding presentation on the topic using this Competitive Operations And Financials Performance Security Alarm And Monitoring Systems Company Profile. Dispense information and present a thorough explanation of Competitive, Operations, Performance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Smart Home Operating System Integration Security Alarm And Monitoring Systems Company Profile
Smart Home Operating System Integration Security Alarm And Monitoring Systems Company ProfileThis slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation. Deliver an outstanding presentation on the topic using this Smart Home Operating System Integration Security Alarm And Monitoring Systems Company Profile. Dispense information and present a thorough explanation of Integration, Automation, Processing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Operations Of Logistics Through Integrated Enabling Smart Shipping And Logistics Through Iot
Securing Operations Of Logistics Through Integrated Enabling Smart Shipping And Logistics Through IotThis slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. Deliver an outstanding presentation on the topic using this Securing Operations Of Logistics Through Integrated Enabling Smart Shipping And Logistics Through Iot. Dispense information and present a thorough explanation of Potential Impact, Iot Security System, Securing Operations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Company Operations In Us And Canada Wireless Home Security Systems Company Profile
Company Operations In Us And Canada Wireless Home Security Systems Company ProfileThis slide showcases the security company current operations in USA and Canada through map. It includes the total states covered of USA and Canada along which total served customers. Increase audience engagement and knowledge by dispensing information using Company Operations In Us And Canada Wireless Home Security Systems Company Profile. This template helps you present information on one stages. You can also present information on Company Operations using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Competitive Operations And Financials Wireless Home Security Systems Company Profile
Competitive Operations And Financials Wireless Home Security Systems Company ProfileThis slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count. Deliver an outstanding presentation on the topic using this Competitive Operations And Financials Wireless Home Security Systems Company Profile. Dispense information and present a thorough explanation of Revenue, Recurring Monthly Revenue, Net Profit using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Criteria To Automate Security Analysis And Response Enabling Automation In Cyber Security Operations
Criteria To Automate Security Analysis And Response Enabling Automation In Cyber Security OperationsThis slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Present the topic in a bit more detail with this Criteria To Automate Security Analysis And Response Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Intervention, Malware Analysis, Automate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security Operations
Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security OperationsThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Present the topic in a bit more detail with this Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Information, Management, Automation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security Operations
Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security OperationsThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deceptio Increase audience engagement and knowledge by dispensing information using Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security Operations. This template helps you present information on four stages. You can also present information on Endpoint Protection, Network Protection, User Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations
Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security OperationsThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Present the topic in a bit more detail with this Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Automation, Integrates, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
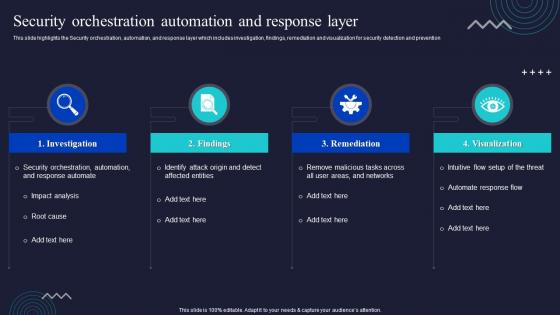 Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security Operations
Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security OperationsThis slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention Deliver an outstanding presentation on the topic using this Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Investigation, Remediation, Visualization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Measure Security Automation Metrics For Operations Security Automation To Investigate And Remediate Cyberthreats
Measure Security Automation Metrics For Operations Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Present the topic in a bit more detail with this Measure Security Automation Metrics For Operations Security Automation To Investigate And Remediate Cyberthreats. Use it as a tool for discussion and navigation on Measure, Automation, Operations Efficiency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Security Operation Center Team Roles And Responsibilities
Enterprise Security Operation Center Team Roles And ResponsibilitiesThis slide covers enterprise security operation center team roles and responsibilities. It involves key roles such as incident responder, security investigator, advanced security analyst and SOC manager. Introducing our Enterprise Security Operation Center Team Roles And Responsibilities set of slides. The topics discussed in these slides are Security Investigator, Incident Responder, Advanced Security Analyst. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Operational Technology Cyber Security In Powerpoint And Google Slides Cpb
Operational Technology Cyber Security In Powerpoint And Google Slides CpbPresenting our Operational Technology Cyber Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Operational Technology Cyber Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Roles And Responsibilities Of Security Operations Center Team Ppt Professional
Roles And Responsibilities Of Security Operations Center Team Ppt ProfessionalThis slide outlines the roles and responsibilities of the security operations center team. The purpose of this slide is to showcase the roles as well as duties of the SOC team. The prominent roles include incident responder, security investigator, advanced security analyst, SOC manager, and security engineer. Increase audience engagement and knowledge by dispensing information using Roles And Responsibilities Of Security Operations Center Team Ppt Professional. This template helps you present information on five stages. You can also present information on Incident Responder, Security Investigator using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SecOps Challenges And Solutions Of Security Operations Centres Ppt Download
SecOps Challenges And Solutions Of Security Operations Centres Ppt DownloadThis slide outlines the key challenges and solutions of security operations centers. The purpose of this slide is to highlight the problems faced by SOC teams and methods to overcome those problems. The main challenges include talent gaps, sophisticated attackers, increased data and network traffic, etc. Deliver an outstanding presentation on the topic using this SecOps Challenges And Solutions Of Security Operations Centres Ppt Download. Dispense information and present a thorough explanation of Talent Gap, Sophisticated Attackers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SecOps Security Operations Model And Incidents Management Ppt Diagrams
SecOps Security Operations Model And Incidents Management Ppt DiagramsThis slide represents the security operations model, covering the incidents managed by the security operations center. The model includes three teams such as hunters, investigators, and triage. The incidents include multi stage incidents, known campaign tracking, and high volume incidents. Deliver an outstanding presentation on the topic using this SecOps Security Operations Model And Incidents Management Ppt Diagrams. Dispense information and present a thorough explanation of Threat Intelligence, External Intelligence Sources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SecOps Tools And Technologies Used In Security Operations Center Ppt Summary
SecOps Tools And Technologies Used In Security Operations Center Ppt SummaryThis slide highlights the crucial tools and technologies used in the SecOps environment. The purpose of this slide is to showcase the various tools and techniques a SOC requires. The main tools include log collection and management, vulnerability management, security information, and event management, etc. Deliver an outstanding presentation on the topic using this SecOps Tools And Technologies Used In Security Operations Center Ppt Summary. Dispense information and present a thorough explanation of Features, Technologies, Description using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 ZTNA Role Of ZTNA To Improve Business Operations And Security
ZTNA Role Of ZTNA To Improve Business Operations And SecurityThis slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Increase audience engagement and knowledge by dispensing information using ZTNA Role Of ZTNA To Improve Business Operations And Security. This template helps you present information on four stages. You can also present information on Traditional Method, Ztna Approach, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Five years cyber security roadmap to assess and manage operational risk
Five years cyber security roadmap to assess and manage operational riskPresenting Five Years Cyber Security Roadmap To Assess And Manage Operational Risk PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
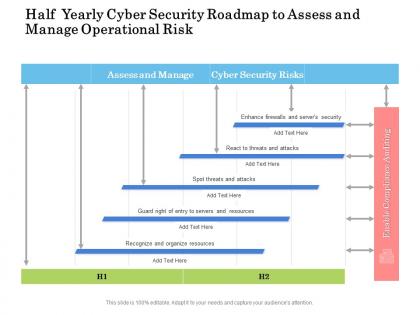 Half yearly cyber security roadmap to assess and manage operational risk
Half yearly cyber security roadmap to assess and manage operational riskPresenting Half Yearly Cyber Security Roadmap To Assess And Manage Operational Risk PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
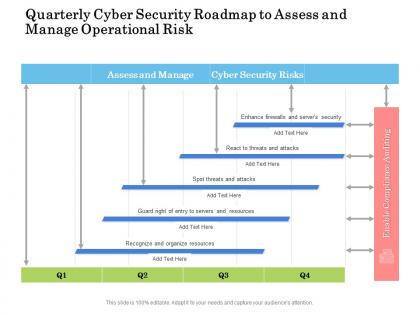 Quarterly cyber security roadmap to assess and manage operational risk
Quarterly cyber security roadmap to assess and manage operational riskPresenting Quarterly Cyber Security Roadmap To Assess And Manage Operational Risk PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
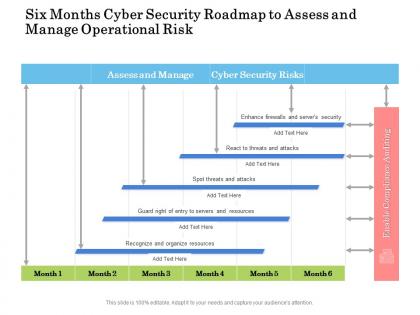 Six months cyber security roadmap to assess and manage operational risk
Six months cyber security roadmap to assess and manage operational riskPresenting Six Months Cyber Security Roadmap To Assess And Manage Operational Risk PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
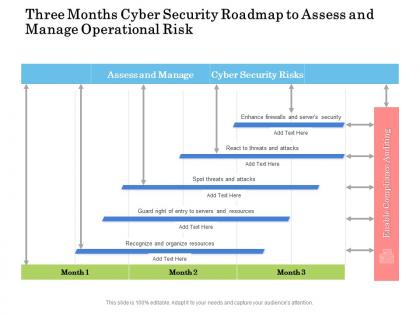 Three months cyber security roadmap to assess and manage operational risk
Three months cyber security roadmap to assess and manage operational riskPresenting Three Months Cyber Security Roadmap To Assess And Manage Operational Risk PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.




