Powerpoint Templates and Google slides for Security Analysis
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Analysing The Impact On Assets Information Breach Information System Security And Risk Administration
Analysing The Impact On Assets Information Breach Information System Security And Risk AdministrationThis slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets. Deliver an outstanding presentation on the topic using this Analysing The Impact On Assets Information Breach Information System Security And Risk Administration. Dispense information and present a thorough explanation of Cost To Protect, Sales Records, Products Database using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Swot Analysis Information System Security And Risk Administration Plan Ppt Styles Clipart
Swot Analysis Information System Security And Risk Administration Plan Ppt Styles ClipartIncrease audience engagement and knowledge by dispensing information using Swot Analysis Information System Security And Risk Administration Plan Ppt Styles Clipart. This template helps you present information on four stages. You can also present information on SWOT Analysis using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparative Analysis Of Cyber Security Incident Mitigation Software Ppt Graphics
Comparative Analysis Of Cyber Security Incident Mitigation Software Ppt GraphicsThis slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Introducing Comparative Analysis Of Cyber Security Incident Mitigation Software Ppt Graphics to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Comparative Analysis, Cyber Security, Mitigation Software, using this template. Grab it now to reap its full benefits.
-
 Comparative Analysis Of Web Application Firewall Products Implementing Cyber Security Ppt Themes
Comparative Analysis Of Web Application Firewall Products Implementing Cyber Security Ppt ThemesThis slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Present the topic in a bit more detail with this Comparative Analysis Of Web Application Firewall Products Implementing Cyber Security Ppt Themes. Use it as a tool for discussion and navigation on Cookie Tampering, Comparative Analysis, Firewall Products. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Asset Identification For Information Security Cybersecurity Risk Analysis And Management Plan
Asset Identification For Information Security Cybersecurity Risk Analysis And Management PlanThis slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack Introducing Asset Identification For Information Security Cybersecurity Risk Analysis And Management Plan to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identification, Information, Management, using this template. Grab it now to reap its full benefits.
-
 Budget For Information Security Risk Management Cybersecurity Risk Analysis And Management Plan
Budget For Information Security Risk Management Cybersecurity Risk Analysis And Management PlanThis slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup Deliver an outstanding presentation on the topic using this Budget For Information Security Risk Management Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Training Of Employees, Software Implementation, Risk Monitoring using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist For Information Security Risk Management Cybersecurity Risk Analysis And Management Plan
Checklist For Information Security Risk Management Cybersecurity Risk Analysis And Management PlanThis slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status Introducing Checklist For Information Security Risk Management Cybersecurity Risk Analysis And Management Plan to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Management, Information, Different Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Current Information And Data Security Cybersecurity Risk Analysis And Management Plan
Current Information And Data Security Cybersecurity Risk Analysis And Management PlanThis slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating Present the topic in a bit more detail with this Current Information And Data Security Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Information, Capabilities, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Analysis And Management Plan Analysing The Impact Of Security Threats
Cybersecurity Risk Analysis And Management Plan Analysing The Impact Of Security ThreatsPresent the topic in a bit more detail with this Cybersecurity Risk Analysis And Management Plan Analysing The Impact Of Security Threats. Use it as a tool for discussion and navigation on Analysing, Organization, Security Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Analysis And Management Plan Current Information Security Issues Faced
Cybersecurity Risk Analysis And Management Plan Current Information Security Issues FacedDeliver an outstanding presentation on the topic using this Cybersecurity Risk Analysis And Management Plan Current Information Security Issues Faced. Dispense information and present a thorough explanation of Untrained Employees, Frequent Data Breaches, Complex Risk Management Policy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Analysis And Management Plan Identifying Employees For Information Security
Cybersecurity Risk Analysis And Management Plan Identifying Employees For Information SecurityThis slide showcases plan that can help organization to conduct training for employees for information security risk management. It will enable employees to monitor risks and resolve them in timely manner Deliver an outstanding presentation on the topic using this Cybersecurity Risk Analysis And Management Plan Identifying Employees For Information Security. Dispense information and present a thorough explanation of Identifying, Information, Training Programme using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Estimated Impact Of Information Security Risk Cybersecurity Risk Analysis And Management Plan
Estimated Impact Of Information Security Risk Cybersecurity Risk Analysis And Management PlanThis slide showcases capabilities of organization regarding information and data security after risk management plan. Its key component are risk management functions, required standard rating and actual standard rating Deliver an outstanding presentation on the topic using this Estimated Impact Of Information Security Risk Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Information, Management Plan, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F856 Information Security And Risk Management User Cybersecurity Risk Analysis And Management Plan
F856 Information Security And Risk Management User Cybersecurity Risk Analysis And Management PlanThis slide showcases expenses done by organization in different segments of information security and risk management. Key segments include - application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc Deliver an outstanding presentation on the topic using this F856 Information Security And Risk Management User Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Information, Management, Application using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Financial Impact Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan
Financial Impact Of Information Security Attacks Cybersecurity Risk Analysis And Management PlanThis slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type Present the topic in a bit more detail with this Financial Impact Of Information Security Attacks Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Financial, Information, Organizations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Framework For Information Security Risk Management Cybersecurity Risk Analysis And Management Plan
Framework For Information Security Risk Management Cybersecurity Risk Analysis And Management PlanThis slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyse risks, evaluate and treat risks Deliver an outstanding presentation on the topic using this Framework For Information Security Risk Management Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Framework, Management, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Gap Assessment Of Organization Information Security Cybersecurity Risk Analysis And Management Plan
Gap Assessment Of Organization Information Security Cybersecurity Risk Analysis And Management PlanThis slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like frequent malware attacks and lack of awareness among employees Present the topic in a bit more detail with this Gap Assessment Of Organization Information Security Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Assessment, Organization, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identifying Information Security Threats And Impact Cybersecurity Risk Analysis And Management Plan
Identifying Information Security Threats And Impact Cybersecurity Risk Analysis And Management PlanThis slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization Present the topic in a bit more detail with this Identifying Information Security Threats And Impact Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Identifying, Information, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Information Security Loss On Organization Cybersecurity Risk Analysis And Management Plan
Impact Of Information Security Loss On Organization Cybersecurity Risk Analysis And Management PlanIntroducing Impact Of Information Security Loss On Organization Cybersecurity Risk Analysis And Management Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Organization, Companies, using this template. Grab it now to reap its full benefits.
-
 Information Security Attacks Faced By Organization Cybersecurity Risk Analysis And Management Plan
Information Security Attacks Faced By Organization Cybersecurity Risk Analysis And Management PlanThis slide showcases most common information attacks faced by organization. It includes - malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack Increase audience engagement and knowledge by dispensing information using Information Security Attacks Faced By Organization Cybersecurity Risk Analysis And Management Plan. This template helps you present information on six stages. You can also present information on Information, Organization, Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Kpis To Measure Information Security Risk Management Cybersecurity Risk Analysis And Management Plan
Kpis To Measure Information Security Risk Management Cybersecurity Risk Analysis And Management PlanThis slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan Deliver an outstanding presentation on the topic using this Kpis To Measure Information Security Risk Management Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Measure, Information, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mitigation Strategies To Tackle Information Security Cybersecurity Risk Analysis And Management Plan
Mitigation Strategies To Tackle Information Security Cybersecurity Risk Analysis And Management PlanThis slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and main reputation of business Introducing Mitigation Strategies To Tackle Information Security Cybersecurity Risk Analysis And Management Plan to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Mitigation, Strategies, Information, using this template. Grab it now to reap its full benefits.
-
 Process For Information Security Risk Assessment Cybersecurity Risk Analysis And Management Plan
Process For Information Security Risk Assessment Cybersecurity Risk Analysis And Management PlanThis slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Introducing Process For Information Security Risk Assessment Cybersecurity Risk Analysis And Management Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Process, Assessment, Information, using this template. Grab it now to reap its full benefits.
-
 Reporting Structure For Information Security Cybersecurity Risk Analysis And Management Plan
Reporting Structure For Information Security Cybersecurity Risk Analysis And Management PlanThis slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact Deliver an outstanding presentation on the topic using this Reporting Structure For Information Security Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Structure, Information, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Selecting Suitable Software For Information Security Cybersecurity Risk Analysis And Management Plan
Selecting Suitable Software For Information Security Cybersecurity Risk Analysis And Management PlanThis slide showcases software that can help organization to monitor and manage the information security risk. It provides information about cyber risk quantification, vulnerability management, centralized repository for assets etc. Present the topic in a bit more detail with this Selecting Suitable Software For Information Security Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Software, Information, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps For Information Security Risk Management Cybersecurity Risk Analysis And Management Plan
Steps For Information Security Risk Management Cybersecurity Risk Analysis And Management PlanThis slide steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond Deliver an outstanding presentation on the topic using this Steps For Information Security Risk Management Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Information, Management, Awareness And Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Timeline For Information Security Risk Management Cybersecurity Risk Analysis And Management Plan
Timeline For Information Security Risk Management Cybersecurity Risk Analysis And Management PlanThis slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress Present the topic in a bit more detail with this Timeline For Information Security Risk Management Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Timeline, Information, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Project Investment Analysis With Goals
Cyber Security Project Investment Analysis With GoalsThis slide signifies the budget distribution table on developing business objectives. It includes stages like goals, investment, analysis, strategies to implement and key result. Presenting our well structured Cyber Security Project Investment Analysis With Goals. The topics discussed in this slide are Project Goals, Investment, Analysis, Strategies To Implement. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Artificial Intelligence Security Challenges And Solutions Analysis
Artificial Intelligence Security Challenges And Solutions AnalysisThe purpose of this template is to provide details of artificial intelligence AI security analysis based on the challenges faced and solutions available. It covers different applications used in AI for maintaining security and privacy. Presenting our well structured Artificial Intelligence Security Challenges And Solutions Analysis. The topics discussed in this slide are Multisensory Extended Reality, Connected Robotics, Autonomous Systems. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Analysing The Impact Of Security Threats On Organization Formulating Cybersecurity Plan
Analysing The Impact Of Security Threats On Organization Formulating Cybersecurity PlanPresent the topic in a bit more detail with this Analysing The Impact Of Security Threats On Organization Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Organization, Average Financial, Analysing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icon For Traditional Vs Cloud Analysis It Security
Icon For Traditional Vs Cloud Analysis It SecurityPresenting our set of slides with Icon For Traditional Vs Cloud Analysis It Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon Traditional,Cloud It Security .
-
 Annual It Security Investment Analysis And Projection
Annual It Security Investment Analysis And ProjectionThe following slide depicts the key areas of investment in IT security to safeguard business from risks and cyber attacks. It includes the current and the previous year spending along with the estimated growth. Introducing our Annual It Security Investment Analysis And Projection set of slides. The topics discussed in these slides are Application Security, Cloud Security, Data Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 It Security Assurance And Analysis Icon
It Security Assurance And Analysis IconIntroducing our premium set of slides with It Security Assurance And Analysis Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security, Assurance, Analysis. So download instantly and tailor it with your information.
-
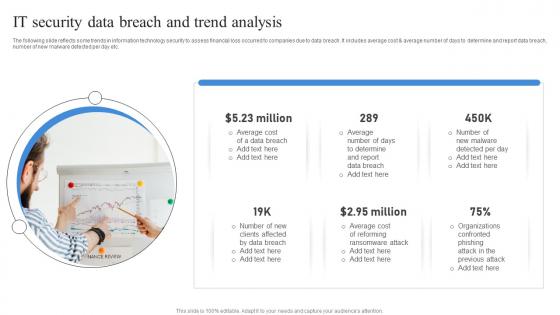 It Security Data Breach And Trend Analysis
It Security Data Breach And Trend AnalysisThe following slide reflects some trends in information technology security to assess financial loss occurred to companies due to data breach. It includes average cost and average number of days to determine and report data breach, number of new malware detected per day etc. Presenting our set of slides with It Security Data Breach And Trend Analysis. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Data, Breach, Analysis.
-
 It Security Gap Analysis With Risk Level
It Security Gap Analysis With Risk LevelThe following slide highlights the gaps in the IT security system to determine the opportunities for improvement. It also reflects the level of risk low, moderate, high and extreme if the gap are not fulfilled. Presenting our well structured It Security Gap Analysis With Risk Level. The topics discussed in this slide are Organization Network, Security Training Sessions, Gap Assessment. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 It Security Threat And Weakness Analysis
It Security Threat And Weakness AnalysisThe following slide highlights the IT security assessment to verify the safety status of assets and networks. It includes elements such as threats, weakness, impact and level of risk, current and proposed controls etc. Introducing our premium set of slides with It Security Threat And Weakness Analysis. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk, Threats, Weakness. So download instantly and tailor it with your information.
-
 Evaluating It System Security Using Swot Analysis Preventing Data Breaches Through Cyber Security
Evaluating It System Security Using Swot Analysis Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Increase audience engagement and knowledge by dispensing information using Evaluating It System Security Using Swot Analysis Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Strength, Threats, Weaknesses using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 F625 Opening Retail Store In The Untapped Market Increase Sales Comparative Analysis Various Banks Secure
F625 Opening Retail Store In The Untapped Market Increase Sales Comparative Analysis Various Banks SecureThe following slide showcases the comparison of different banks offering term loans to businesses. The comparison is drawn on the basis of interest rate, processing fees and equated monthly installment EMI. Deliver an outstanding presentation on the topic using this F625 Opening Retail Store In The Untapped Market Increase Sales Comparative Analysis Various Banks Secure. Dispense information and present a thorough explanation of Comparative, Analysis, Installment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Competitive Matrix Analysis Of Security Software
Competitive Matrix Analysis Of Security SoftwareThis slide provides an overview of the comparison among various software. The comparison is done on the basis of features that are antivirus, firewall, system cleansing, anti-spyware and parental control. Introducing our Competitive Matrix Analysis Of Security Software set of slides. The topics discussed in these slides are Antivirus, Firewall. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis Of Various Cloud Security Tools
Comparative Analysis Of Various Cloud Security ToolsThis slide shows comparison amongst various cloud security tools which can be used by the organization to select the best suitable tool. it also includes details about features, price and ratings. Introducing our Comparative Analysis Of Various Cloud Security Tools set of slides. The topics discussed in these slides are Comparative Analysis, Various, Cloud Security Tools. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis Of Tools To Overcome Iot Security Challenges
Comparative Analysis Of Tools To Overcome Iot Security ChallengesThis slide highlights tools that help to solve security challenges in IoT devices and help to provide better customer services. Some of the elements of comparative analysis include tools, features, pricing, and additional comments. Presenting our well structured Comparative Analysis Of Tools To Overcome Iot Security Challenges. The topics discussed in this slide are Features, Sternum Iot.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Incident Response Analysis Icon
Cyber Security Incident Response Analysis IconPresenting our well structured Cyber Security Incident Response Analysis Icon. The topics discussed in this slide are Cyber Security, Incident Response, Analysis Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Healthcare Security Measures And Assessment Analysis
Healthcare Security Measures And Assessment AnalysisThis slide covers the details related to the measures for healthcare security and its assessment analysis. The purpose of this template is to define privacy and security of healthcare organization. It includes information related to physical, administrative and technical safeguards. Presenting our well structured Healthcare Security Measures And Assessment Analysis. The topics discussed in this slide are Security Areas, Details, Potential Security Measures. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparative Analysis Of Various Banks To Secure Best Funding Offer Launching Retail Company
Comparative Analysis Of Various Banks To Secure Best Funding Offer Launching Retail CompanyThe following slide showcases the comparison of different banks offering term loans to businesses. The comparison is drawn on the basis of interest rate, processing fees and equated monthly installment EMI. Present the topic in a bit more detail with this Comparative Analysis Of Various Banks To Secure Best Funding Offer Launching Retail Company. Use it as a tool for discussion and navigation on Interest Rate, Processing Fees, Best Funding Offer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Software Supply Chain Security Comparative Analysis
Software Supply Chain Security Comparative AnalysisThe following slide highlights comparative analysis of software supply chain security to track vulnerabilities, risk prevention etc. It includes elements such as software, capabilities, budget, free trial and rating. Presenting our well structured Software Supply Chain Security Comparative Analysis The topics discussed in this slide are Vulnerability Mitigation, Security Strategy Assessment This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Secured Childcare Industry Strategic Analysis Icon
Secured Childcare Industry Strategic Analysis IconPresenting our set of slides with Secured Childcare Industry Strategic Analysis Icon. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secured Childcare Industry, Strategic Analysis Icon.
-
 Ultimate Guide For Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS
Ultimate Guide For Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SSThe following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 247 availability, etc. Deliver an outstanding presentation on the topic using this Ultimate Guide For Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS Dispense information and present a thorough explanation of Experience, Detect Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Analysis Of Cyber Security Incident Mitigation Incident Response Strategies Deployment
Comparative Analysis Of Cyber Security Incident Mitigation Incident Response Strategies DeploymentThis slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Introducing Comparative Analysis Of Cyber Security Incident Mitigation Incident Response Strategies Deployment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Mobile, Customizable, Price, using this template. Grab it now to reap its full benefits.
-
 Impact Analysis For Effective Threat Management In Securing Managing IT Threats At Workplace Overview
Impact Analysis For Effective Threat Management In Securing Managing IT Threats At Workplace OverviewThis slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Present the topic in a bit more detail with this Impact Analysis For Effective Threat Management In Securing Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Analysis, Threat Management, Securing Workplace. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Architecture Review Of A Cloud Conducting Root Cause Analysis
Security Architecture Review Of A Cloud Conducting Root Cause AnalysisThis slide covers the need to conduct a cloud architecture review to address a specific issue in your cloud environment. Increase audience engagement and knowledge by dispensing information using Security Architecture Review Of A Cloud Conducting Root Cause Analysis. This template helps you present information on four stages. You can also present information on Cloud Environment, Vulnerability Pitfall, Analytical View, Conducting Root using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Policy Swot Analysis Ppt Show Background Image
Cyber Security Policy Swot Analysis Ppt Show Background ImageIncrease audience engagement and knowledge by dispensing information using Cyber Security Policy Swot Analysis Ppt Show Background Image. This template helps you present information on four stages. You can also present information on Strengths, Weaknesses, Opportunities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Security Analysis Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Analysis Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Data security analysis colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Data Security Analysis Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Analysis Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Data security analysis monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Comparative Analysis Of Cyber Security Incident Mitigation Development And Implementation Of Security
Comparative Analysis Of Cyber Security Incident Mitigation Development And Implementation Of SecurityThis slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Deliver an outstanding presentation on the topic using this Comparative Analysis Of Cyber Security Incident Mitigation Development And Implementation Of Security. Dispense information and present a thorough explanation of Incident Tool, User Rating, Price using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Cloud Computing Security Analysis Icon
Network Cloud Computing Security Analysis IconPresenting our set of slides with Network Cloud Computing Security Analysis Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network, Cloud Computing, Security Analysis Icon
-
 Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation Software
Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation SoftwareThis slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation Software. Use it as a tool for discussion and navigation on Comparative Analysis, Cyber Security Incident, Mitigation Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Gap Analysis Representing Current Situation Of Cybersecurity Incident
Cyber Security Attacks Response Gap Analysis Representing Current Situation Of Cybersecurity IncidentThis slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Present the topic in a bit more detail with this Cyber Security Attacks Response Gap Analysis Representing Current Situation Of Cybersecurity Incident. Use it as a tool for discussion and navigation on Gap Analysis, Representing Current Situation, Cybersecurity Incident, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Comparative Analysis Of Web Application Firewall Products
Cyber Security Attacks Response Plan Comparative Analysis Of Web Application Firewall ProductsThis slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Comparative Analysis Of Web Application Firewall Products. Dispense information and present a thorough explanation of Comparative Analysis, Web Application, Firewall Products using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Importance Of Secure Ecommerce Payment Systems Analysis And Deployment Of Efficient Ecommerce
Importance Of Secure Ecommerce Payment Systems Analysis And Deployment Of Efficient EcommerceThis slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. Increase audience engagement and knowledge by dispensing information using Importance Of Secure Ecommerce Payment Systems Analysis And Deployment Of Efficient Ecommerce. This template helps you present information on one stages. You can also present information on Meets Digital Needs, Customer Retention, Multiple Payment Modes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Stages Of Malware Analysis Utilized By Security Analysts
Key Stages Of Malware Analysis Utilized By Security AnalystsThis slide illustrates malware analysis phases which help security analysts in identifying and understanding depth of sources of threats. Stages covered in this slide are static properties, interactive behavior, full automated analysis and manual code reversing. Introducing our premium set of slides with name Key Stages Of Malware Analysis Utilized By Security Analysts. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Properties Analysis, Behavior Analysis, Automated Analysis. So download instantly and tailor it with your information.
-
 Security Software Testing Analysis Approach Icon
Security Software Testing Analysis Approach IconIntroducing our premium set of slides with name Security Software Testing Analysis Approach Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Software Testing, Analysis Approach Icon. So download instantly and tailor it with your information.





