Powerpoint Templates and Google slides for Security Access
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Mobile Access Control Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Mobile Access Control Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon will provide a visually engaging representation of Mobile Security. It is a great addition to any presentation and can be used to demonstrate the importance of mobile security and the various measures that can be taken to protect mobile devices.
-
 Mobile Access Control Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Mobile Access Control Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Mobile Security is perfect for presentations on the importance of mobile security. It is a simple yet effective way to illustrate the need for secure mobile practices.
-
 Cyber Security Policy Access Authorization Modification And Identity Access Management
Cyber Security Policy Access Authorization Modification And Identity Access ManagementThis slide represents the access authorization, modification, and identity access management based on polp, including the departments involved in creating this policy, such as HR and IT. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Access Authorization Modification And Identity Access Management. This template helps you present information on seven stages. You can also present information on Management, Authorization, Modification using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Policy Overview Of Remote Access Policy For Employees
Cyber Security Policy Overview Of Remote Access Policy For EmployeesThis slide represents the remote access policy to connect to the companys network from any other host. Its goal is to mitigate the threat of losses resulting from illegal access to resources. Introducing Cyber Security Policy Overview Of Remote Access Policy For Employees to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Resources, Procedures, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Policy Privacy And Company Access To Personal Devices
Cyber Security Policy Privacy And Company Access To Personal DevicesThis slide depicts privacy and company access to workers personal devices. It is stated that organizations have the right to analyze personal and work-related data during an emergency. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Privacy And Company Access To Personal Devices. This template helps you present information on six stages. You can also present information on Management, Government, Authorities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN And Secure Access Service Edge SASE Ppt Icon Graphics
SD WAN And Secure Access Service Edge SASE Ppt Icon GraphicsThis slide represents the relationship between secure access service edge and software defined wide area network. It also includes the benefits of SASE and its security features, such as software defined WAN, firewall as a service, zero trust network access, cloud access security broker, secure web gateway, and unified management. Present the topic in a bit more detail with this SD WAN And Secure Access Service Edge SASE Ppt Icon Graphics. Use it as a tool for discussion and navigation on Devices, IoT Sensors, Edge Locations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN IT Secure Access Service Edge Vs SD WAN Ppt Summary Guide
SD WAN IT Secure Access Service Edge Vs SD WAN Ppt Summary GuideThis slide compares secure access service edge and software defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Introducing SD WAN IT Secure Access Service Edge Vs SD WAN Ppt Summary Guide to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Deployment And Architecture, Traffic And Connectivity, Security, using this template. Grab it now to reap its full benefits.
-
 It Infra Security Model To Eliminate Unauthorized User Access
It Infra Security Model To Eliminate Unauthorized User AccessThe following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defence. It presents information related to perimeter, endpoint, visibility, etc. Introducing It Infra Security Model To Eliminate Unauthorized User Access to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Perimeter, Application, Identify, using this template. Grab it now to reap its full benefits.
-
 SDN Security IT Role Of SDN In Edge Computing IOT And Remote Access
SDN Security IT Role Of SDN In Edge Computing IOT And Remote AccessThis slide represents the role of software defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. Introducing SDN Security IT Role Of SDN In Edge Computing IOT And Remote Access to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Role, Computing, Remote, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Access Control Policy Icon
Cyber Security Access Control Policy IconPresenting our set of slides with Cyber Security Access Control Policy Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security, Access Control Policy Icon.
-
 Systems Access Control Security Policy
Systems Access Control Security PolicyThis slide shows Access Control Policy for computer system and laptops of firm to ensure security of business data. It include sections such as Policy risks, Policy Key points, Information and security standards etc. Introducing our Systems Access Control Security Policy set of slides. The topics discussed in these slides are Systems, Security, Policy. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Unauthorized Computer Access Icon Causing Cyber Security Threat
Unauthorized Computer Access Icon Causing Cyber Security ThreatPresenting our set of slides with Unauthorized Computer Access Icon Causing Cyber Security Threat. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Unauthorized, Computer Access.
-
 Key Access Security Control Models Implementation Of ICT Strategic Plan Strategy SS
Key Access Security Control Models Implementation Of ICT Strategic Plan Strategy SSThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role based access control and attributes based access control.Deliver an outstanding presentation on the topic using this Key Access Security Control Models Implementation Of ICT Strategic Plan Strategy SS. Dispense information and present a thorough explanation of Discretionary Access, Mandatory Access, Access Granted using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE IT Benefits Of Secure Access Service Edge SASE IT Ppt Powerpoint Guidelines
SASE IT Benefits Of Secure Access Service Edge SASE IT Ppt Powerpoint GuidelinesThis slide outlines the key benefits of secure access service edge. The purpose of this slide is to showcase the advantages of the SASE model, such as flexibility, cost savings, reduced complexity, increased performance, threat and data protection and increased network performance. Present the topic in a bit more detail with this SASE IT Benefits Of Secure Access Service Edge SASE IT Ppt Powerpoint Guidelines. Use it as a tool for discussion and navigation on Reduced Complexity, Cost Savings, Threat Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE IT Best Practices To Implement Cloud Access Security Broker Ppt Powerpoint Microsoft
SASE IT Best Practices To Implement Cloud Access Security Broker Ppt Powerpoint MicrosoftThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this SASE IT Best Practices To Implement Cloud Access Security Broker Ppt Powerpoint Microsoft. Dispense information and present a thorough explanation of Build Visibility, Forecast Risk, Release CASB using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE IT Budget To Implement Secure Access Service Edge Ppt Powerpoint Designs
SASE IT Budget To Implement Secure Access Service Edge Ppt Powerpoint DesignsThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD-WAN, SWG, ZTNA, CASB, and FWaaS. Present the topic in a bit more detail with this SASE IT Budget To Implement Secure Access Service Edge Ppt Powerpoint Designs. Use it as a tool for discussion and navigation on Secure Web Gateway, Zero Trust Network Access, Cloud Access Security Broker. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE IT Checklist To Implement Secure Access Service Edge Ppt Powerpoint Demonstration
SASE IT Checklist To Implement Secure Access Service Edge Ppt Powerpoint DemonstrationPresent the topic in a bit more detail with this SASE IT Checklist To Implement Secure Access Service Edge Ppt Powerpoint Demonstration. Use it as a tool for discussion and navigation on Test And Troubleshoot, Incorporate Zero Trust Solutions, SASE Goals And Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE IT Cloud Access Security Broker CASB Overview Ppt Powerpoint Professional
SASE IT Cloud Access Security Broker CASB Overview Ppt Powerpoint ProfessionalThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Deliver an outstanding presentation on the topic using this SASE IT Cloud Access Security Broker CASB Overview Ppt Powerpoint Professional. Dispense information and present a thorough explanation of Risk Visibility, Threat Prevention, Granular Cloud Usage Control using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE IT Cloud Access Security Broker Implementation Models Ppt Powerpoint Template
SASE IT Cloud Access Security Broker Implementation Models Ppt Powerpoint TemplateThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing SASE IT Cloud Access Security Broker Implementation Models Ppt Powerpoint Template to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on API Scanning, Forward Proxy, Reverse Proxy, using this template. Grab it now to reap its full benefits.
-
 SASE IT Cloud Access Security Broker Use Cases Ppt Powerpoint Diagrams
SASE IT Cloud Access Security Broker Use Cases Ppt Powerpoint DiagramsThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Present the topic in a bit more detail with this SASE IT Cloud Access Security Broker Use Cases Ppt Powerpoint Diagrams. Use it as a tool for discussion and navigation on Protection Against Threats, Govern Usage, Secure Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE IT Cloud Access Security Broker Working Process Ppt Powerpoint Demonstration
SASE IT Cloud Access Security Broker Working Process Ppt Powerpoint DemonstrationThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using SASE IT Cloud Access Security Broker Working Process Ppt Powerpoint Demonstration. This template helps you present information on one stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE IT Comparison Between Secure Access Service Edge And SD WAN Ppt Download
SASE IT Comparison Between Secure Access Service Edge And SD WAN Ppt DownloadThis slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Deliver an outstanding presentation on the topic using this SASE IT Comparison Between Secure Access Service Edge And SD WAN Ppt Download. Dispense information and present a thorough explanation of Deployment And Architecture, Traffic And Connectivity, Security, Remote Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE IT Introduction To Secure Access Service Edge SASE Ppt Powerpoint Graphics
SASE IT Introduction To Secure Access Service Edge SASE Ppt Powerpoint GraphicsThis slide represents the introduction of SASE cloud security technology. The purpose of this slide is to demonstrate the core capabilities, benefits and key components of SASE. The key components include SD-WAN, FWaaS, ZTNA, CASB, SWG, and unified management. Present the topic in a bit more detail with this SASE IT Introduction To Secure Access Service Edge SASE Ppt Powerpoint Graphics. Use it as a tool for discussion and navigation on Core Capabilities, Key Components, Benefits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE IT Pillars Of Cloud Access Security Broker Ppt Powerpoint Inspiration
SASE IT Pillars Of Cloud Access Security Broker Ppt Powerpoint InspirationThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Increase audience engagement and knowledge by dispensing information using SASE IT Pillars Of Cloud Access Security Broker Ppt Powerpoint Inspiration. This template helps you present information on four stages. You can also present information on Compliance, Visibility, Threat Prevention, Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
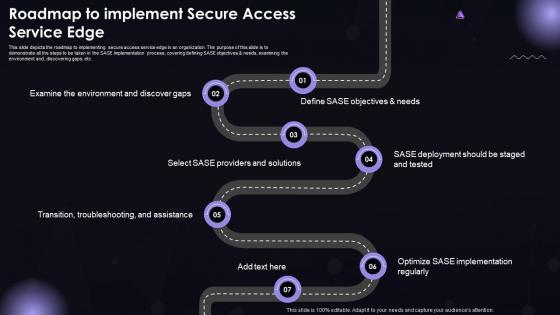 SASE IT Roadmap To Implement Secure Access Service Edge Ppt Powerpoint Formats
SASE IT Roadmap To Implement Secure Access Service Edge Ppt Powerpoint FormatsThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Introducing SASE IT Roadmap To Implement Secure Access Service Edge Ppt Powerpoint Formats to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Transition, Troubleshooting, And Assistance, SASE Providers And Solutions, using this template. Grab it now to reap its full benefits.
-
 SASE IT Secure Access Service Edge Architecture Characteristics Ppt Powerpoint Background
SASE IT Secure Access Service Edge Architecture Characteristics Ppt Powerpoint BackgroundThis slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity-driven, cloud-native, support for all edges, and global distribution. Introducing SASE IT Secure Access Service Edge Architecture Characteristics Ppt Powerpoint Background to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identity Driven, Cloud Native, Support For All Edges, Globally Distributed, using this template. Grab it now to reap its full benefits.
-
 SASE IT Secure Access Service Edge Implementation Steps Ppt Powerpoint Guidelines
SASE IT Secure Access Service Edge Implementation Steps Ppt Powerpoint GuidelinesThis slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD-WAN backbone, incorporating zero-trust solutions, etc. Increase audience engagement and knowledge by dispensing information using SASE IT Secure Access Service Edge Implementation Steps Ppt Powerpoint Guidelines. This template helps you present information on five stages. You can also present information on SASE Goals And Requirements, Select SD-WAN Backbone, Incorporate Zero Trust Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE IT Secure Access Service Edge Importance Ppt Powerpoint Guidelines
SASE IT Secure Access Service Edge Importance Ppt Powerpoint GuidelinesThis slide represents the importance of secure access service edge. This slides purpose is to demonstrate why businesses need the SASE model. The main reasons include scaling with business needs, encouraging work from anywhere environment, standing up for cyber threats, and offering a base for IoT adoption. Introducing SASE IT Secure Access Service Edge Importance Ppt Powerpoint Guidelines to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Scales With Business, Encourage Work-From-Anywhere, Cyberthreat Evolution, using this template. Grab it now to reap its full benefits.
-
 SASE IT Secure Access Service Edge SASE Architecture Ppt Powerpoint Information
SASE IT Secure Access Service Edge SASE Architecture Ppt Powerpoint InformationThis slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE architecture include SWG, CASB, ZTNA, FWaaS, SD-WAN, Thin Edge, and so on. Deliver an outstanding presentation on the topic using this SASE IT Secure Access Service Edge SASE Architecture Ppt Powerpoint Information. Dispense information and present a thorough explanation of Goals Of Architecture, Incorporate Business, Cloud-Based Security Solution using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE IT Secure Access Service Edge Training Program Ppt Powerpoint Rules
SASE IT Secure Access Service Edge Training Program Ppt Powerpoint RulesThis slide represents the training program for the secure access service edge model. The purpose of this slide is to demonstrate the teams eligible for training, the modules to be covered during the training, the schedule and venue of the training. Present the topic in a bit more detail with this SASE IT Secure Access Service Edge Training Program Ppt Powerpoint Rules. Use it as a tool for discussion and navigation on Secure Access Service, Edge Training Program. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE IT Secure Access Service Edge Use Cases Ppt Powerpoint Summary
SASE IT Secure Access Service Edge Use Cases Ppt Powerpoint SummaryThis slide represents the use cases of secure access service edge within an organization. The purpose of this slide is to demonstrate the various use cases of the SASE model, including rapid response to network demand, support for IoT and edge computing, VPN replacement, performance assurance and so on. Increase audience engagement and knowledge by dispensing information using SASE IT Secure Access Service Edge Use Cases Ppt Powerpoint Summary. This template helps you present information on six stages. You can also present information on VPN Replacement, Performance Assurance, Support For Multiple Operating Systems, Controlled Move To Cloud Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE IT Timeline To Implement Cloud Access Security Broker Ppt Powerpoint Portrait
SASE IT Timeline To Implement Cloud Access Security Broker Ppt Powerpoint PortraitThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using SASE IT Timeline To Implement Cloud Access Security Broker Ppt Powerpoint Portrait. This template helps you present information on seven stages. You can also present information on Hybrid Settings, Organizations Users, Cloud Apps using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE IT Timeline To Implement Secure Access Service Edge Ppt Powerpoint Brochure
SASE IT Timeline To Implement Secure Access Service Edge Ppt Powerpoint BrochureThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing SASE IT Timeline To Implement Secure Access Service Edge Ppt Powerpoint Brochure to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on SASE Objectives And Needs, SASE Providers And Solutions,Transition, Troubleshooting, And Assistance, using this template. Grab it now to reap its full benefits.
-
 SASE IT Working Of Secure Access Service Edge Ppt Powerpoint Graphics
SASE IT Working Of Secure Access Service Edge Ppt Powerpoint GraphicsThis slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. Deliver an outstanding presentation on the topic using this SASE IT Working Of Secure Access Service Edge Ppt Powerpoint Graphics. Dispense information and present a thorough explanation of Traditional Network Security Model, SASE Network Security Model using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Services Accessible Via Mobile Banking For Convenient And Secure Online Payments Fin SS
Various Services Accessible Via Mobile Banking For Convenient And Secure Online Payments Fin SSThis slide shows various services which can be availed by customers through mobile banking. It includes services such as account management, funds transfer, bills payment, mobile check deposits, ATM and branch locators, cards management, etc. Present the topic in a bit more detail with this Various Services Accessible Via Mobile Banking For Convenient And Secure Online Payments Fin SS. Use it as a tool for discussion and navigation on Account Management, Remote Deposit Capture, Funds Transfer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Access Code Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Security Access Code Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is a visual representation of Access Code. It is an eye-catching and vibrant graphic that can be used to indicate a secure access code or to highlight a specific area of a presentation.
-
 Security Access Code Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Security Access Code Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon features a keyhole with a lock and an access code. It is perfect for presentations about security, access control, and restricted areas. It is a simple yet effective way to communicate your message.
-
 Physical Access Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Physical Access Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis PowerPoint icon features a bright blue image of a keypad with a green checkmark, representing physical access security. It is a great visual tool for presentations about security systems and access control.
-
 Physical Access Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Physical Access Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon is a great way to illustrate physical access security. It features a padlock with a keyhole, representing the need for secure access to physical locations. Perfect for presentations on security protocols and best practices.
-
 Access Control Security Risks Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Access Control Security Risks Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis PowerPoint icon depicts a shield with a red warning sign, representing the security risks associated with digital data. It is a great visual aid for presentations on cyber security, risk management, and data protection.
-
 Access Control Security Risks Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Access Control Security Risks Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon on Security Risks is a great visual aid for presentations on cyber security and data protection. It features a silhouette of a person in a protective stance, illustrating the need to be aware of potential risks.
-
 Cloud Access Security Broker Pillar Threat Protection Ppt Infographics Slide Download
Cloud Access Security Broker Pillar Threat Protection Ppt Infographics Slide DownloadThis slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Pillar Threat Protection Ppt Infographics Slide Download. This template helps you present information on five stages. You can also present information on Organizations, Necessary, Safeguards using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Pillar Visibility Ppt Icon Sample
Cloud Access Security Broker Pillar Visibility Ppt Icon SampleThis slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Pillar Visibility Ppt Icon Sample. Dispense information and present a thorough explanation of Overview, Casb Visibility Topography, Working Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Use Cases Ppt Styles Master Slide
Cloud Access Security Broker Use Cases Ppt Styles Master SlideThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Present the topic in a bit more detail with this Cloud Access Security Broker Use Cases Ppt Styles Master Slide. Use it as a tool for discussion and navigation on Use Case, Description, Benefits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Working Process Ppt Ideas Grid
Cloud Access Security Broker Working Process Ppt Ideas GridThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Cloud Access Security Broker Working Process Ppt Ideas Grid. to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Discovery, Classification, Remediation, using this template. Grab it now to reap its full benefits.
-
 Future Of Cloud Access Security Broker CASB 2 0 Ppt Inspiration Infographics
Future Of Cloud Access Security Broker CASB 2 0 Ppt Inspiration InfographicsThis slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Introducing Future Of Cloud Access Security Broker CASB 2 0 Ppt Inspiration Infographics. to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Web Security, Data Loss Prevention, User Authentication, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Cloud Access Security Broker CASB Ppt Model Guidelines
Icons Slide For Cloud Access Security Broker CASB Ppt Model GuidelinesPresenting our well crafted Icons Slide For Cloud Access Security Broker CASB Ppt Model Guidelines set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Leading Cloud Access Security Broker Platforms Ppt File Slideshow
Leading Cloud Access Security Broker Platforms Ppt File SlideshowThis slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms. Increase audience engagement and knowledge by dispensing information using Leading Cloud Access Security Broker Platforms Ppt File Slideshow. This template helps you present information on three stages. You can also present information on G Suite, Office 365, Amazon Web Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of CASB Deployment Models Cloud Access Security Broker CASB
Overview Of CASB Deployment Models Cloud Access Security Broker CASBThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out of band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing Overview Of CASB Deployment Models Cloud Access Security Broker CASB. to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Deployment Models, Api Scanning, Forward Proxy, using this template. Grab it now to reap its full benefits.
-
 Overview Of Cloud Access Security Broker Architecture Ppt Layouts Gridlines
Overview Of Cloud Access Security Broker Architecture Ppt Layouts GridlinesThis slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Deliver an outstanding presentation on the topic using this Overview Of Cloud Access Security Broker Architecture Ppt Layouts Gridlines. Dispense information and present a thorough explanation of Organization, Direct Cloud, Mobile Devices And Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Popular Cloud Access Security Broker Vendors Ppt Slides Format Ideas
Popular Cloud Access Security Broker Vendors Ppt Slides Format IdeasThis slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Present the topic in a bit more detail with this Popular Cloud Access Security Broker Vendors Ppt Slides Format Ideas. Use it as a tool for discussion and navigation on Vendor, Suitable, Features. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps To Deploy Cloud Access Security Broker Ppt Slides Clipart Images
Steps To Deploy Cloud Access Security Broker Ppt Slides Clipart ImagesThis slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. Deliver an outstanding presentation on the topic using this Steps To Deploy Cloud Access Security Broker Ppt Slides Clipart Images. Dispense information and present a thorough explanation of Deployment Location, Deployment Model, Release Model using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Timeline To Implement Cloud Access Security Broker Ppt Ideas Tips
Timeline To Implement Cloud Access Security Broker Ppt Ideas TipsThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Timeline To Implement Cloud Access Security Broker Ppt Ideas Tips. This template helps you present information on seven stages. You can also present information on Keep Records, Identify And Disable, Examine using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Training Program For Cloud Access Security Broker Ppt Layouts Picture
Training Program For Cloud Access Security Broker Ppt Layouts PictureThis slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Introducing Training Program For Cloud Access Security Broker Ppt Layouts Picture. to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Agenda, System Requirements, Mode, using this template. Grab it now to reap its full benefits.
-
 Use Cases Of Cloud Access Security Broker Ppt Ideas Influencers
Use Cases Of Cloud Access Security Broker Ppt Ideas InfluencersPresent the topic in a bit more detail with this Use Cases Of Cloud Access Security Broker Ppt Ideas Influencers. Use it as a tool for discussion and navigation on Unsanctioned Apps, Sanctioned Apps, Cloud Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Why CASB Is Important For Businesses Cloud Access Security Broker CASB
Why CASB Is Important For Businesses Cloud Access Security Broker CASBThis slide outlines the importance of CASB for different organizations. The purpose of this slide is to showcase the various reasons for businesses to invest in the cloud access security broker model, including increased cloud adoption, better security, compliance, and cost effective and centralized management. Increase audience engagement and knowledge by dispensing information using Why CASB Is Important For Businesses Cloud Access Security Broker CASB. This template helps you present information on one stages. You can also present information on Reasons, Description, Increased Cloud Adoption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 ZTNA Comparison Between ZTNA And Secure Access Service Edge
ZTNA Comparison Between ZTNA And Secure Access Service EdgeThis slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Present the topic in a bit more detail with this ZTNA Comparison Between ZTNA And Secure Access Service Edge. Use it as a tool for discussion and navigation on Deployment, Benefits, Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 ZTNA Features Of Zero Trust Network Access Security Model
ZTNA Features Of Zero Trust Network Access Security ModelThis slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Deliver an outstanding presentation on the topic using this ZTNA Features Of Zero Trust Network Access Security Model. Dispense information and present a thorough explanation of Security Controls, Location, Network Visibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 ZTNA Traditional Security Models Vs Zero Trust Network Access
ZTNA Traditional Security Models Vs Zero Trust Network AccessThis slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Deliver an outstanding presentation on the topic using this ZTNA Traditional Security Models Vs Zero Trust Network Access. Dispense information and present a thorough explanation of Traditional Security Model, Static Security, Changing Environment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agenda Cloud Access Security Broker CASB Ppt Slides Graphics Pictures
Agenda Cloud Access Security Broker CASB Ppt Slides Graphics PicturesIntroducing Agenda Cloud Access Security Broker CASB Ppt Slides Graphics Pictures. to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Pillars, Importance, Architecture And Working, using this template. Grab it now to reap its full benefits.





