Powerpoint Templates and Google slides for Security Management
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident Management
Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident ManagementThis slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident Management. Dispense information and present a thorough explanation of Cyber Security Incident, Management On Organization, Software Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Best Practices For Cybersecurity Incident Management
Cyber Security Attacks Response Plan Best Practices For Cybersecurity Incident ManagementThis slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Introducing Cyber Security Attacks Response Plan Best Practices For Cybersecurity Incident Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management Process, Incident Management Plan, Responsibilities, Team Members, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Plan Cyber Security Crisis Management Action Plan Timeline
Cyber Security Attacks Response Plan Cyber Security Crisis Management Action Plan TimelineThis slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Security Crisis Management Action Plan Timeline. Use it as a tool for discussion and navigation on Incident Response, Business Continuity, Review And Recovery, Management Action, Plan Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Five Phases Of Cybersecurity Incident Management
Cyber Security Attacks Response Plan Five Phases Of Cybersecurity Incident ManagementThis slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Introducing Cyber Security Attacks Response Plan Five Phases Of Cybersecurity Incident Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Plan And Prepare, Post Incident Activity, Assess And Design, Incident Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks Response
Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks ResponseThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks Response. This template helps you present information on one stages. You can also present information on Cyber Security, Incident Management, Checklist After An Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Team Structure Cyber Security Attacks Response Plan
Cyber Security Incident Management Team Structure Cyber Security Attacks Response PlanThis slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team. Deliver an outstanding presentation on the topic using this Cyber Security Incident Management Team Structure Cyber Security Attacks Response Plan. Dispense information and present a thorough explanation of Cyber Security, Incident Management, Team Structure, Human Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan
Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response PlanThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Monitor And Manage Security Storage Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Monitor And Manage Security Storage Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Monitor and manage security storage colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Monitor And Manage Security Storage Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Monitor And Manage Security Storage Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Monitor and manage security storage monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Managing Cyber Security In Manufacturing 30 Days Plan Automation In Manufacturing IT
Managing Cyber Security In Manufacturing 30 Days Plan Automation In Manufacturing ITThis slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time and teams who are responsible and details. Present the topic in a bit more detail with this Managing Cyber Security In Manufacturing 30 Days Plan Automation In Manufacturing IT. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing Cyber Security In Manufacturing 60 Days Plan Automation In Manufacturing IT
Managing Cyber Security In Manufacturing 60 Days Plan Automation In Manufacturing ITThis slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Deliver an outstanding presentation on the topic using this Managing Cyber Security In Manufacturing 60 Days Plan Automation In Manufacturing IT. Dispense information and present a thorough explanation of Policy Violations, Data Loss Incidents, Infected Computers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing Cyber Security In Manufacturing 90 Days Plan Automation In Manufacturing IT
Managing Cyber Security In Manufacturing 90 Days Plan Automation In Manufacturing ITThis slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Present the topic in a bit more detail with this Managing Cyber Security In Manufacturing 90 Days Plan Automation In Manufacturing IT. Use it as a tool for discussion and navigation on Training Completion, Communication Methods, Policy Sign Off. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Framework To Manage IT Dashboard To Track IT Security Incidents Prevailing Across Strategy SS
Strategic Framework To Manage IT Dashboard To Track IT Security Incidents Prevailing Across Strategy SSThis slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Introducing Strategic Framework To Manage IT Dashboard To Track IT Security Incidents Prevailing Across Strategy SS to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Dashboard, Track IT Security Incidents, Prevailing Across Firm, using this template. Grab it now to reap its full benefits.
-
 Strategic Framework To Manage IT How Management Enables Effective Corporate Security Strategy SS
Strategic Framework To Manage IT How Management Enables Effective Corporate Security Strategy SSThis slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Deliver an outstanding presentation on the topic using this Strategic Framework To Manage IT How Management Enables Effective Corporate Security Strategy SS. Dispense information and present a thorough explanation of Management, Effective Corporate, Security Governance, Security Resources Effectiveness using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Framework To Manage IT Information Security And Governance Management Strategy SS
Strategic Framework To Manage IT Information Security And Governance Management Strategy SSThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this Strategic Framework To Manage IT Information Security And Governance Management Strategy SS. Use it as a tool for discussion and navigation on Information Security, Governance, Management, Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Framework To Manage IT Risk Management Framework To Manage Security Threats Strategy SS
Strategic Framework To Manage IT Risk Management Framework To Manage Security Threats Strategy SSThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy. Deliver an outstanding presentation on the topic using this Strategic Framework To Manage IT Risk Management Framework To Manage Security Threats Strategy SS. Dispense information and present a thorough explanation of Implement Enterprise Security Program, Implement Control Environment, Implement Security Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 K55 Cyber Security Attacks Response Cyber Security Incident Management Checklist Before
K55 Cyber Security Attacks Response Cyber Security Incident Management Checklist BeforeThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using K55 Cyber Security Attacks Response Cyber Security Incident Management Checklist Before. This template helps you present information on one stages. You can also present information on Cyber Security, Incident Management, Checklist Before An Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda Deploying Computer Security Incident Management
Agenda Deploying Computer Security Incident ManagementIntroducing Agenda Deploying Computer Security Incident Management to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Agenda, using this template. Grab it now to reap its full benefits.
-
 B98 Table Of Contents For Deploying Computer Security Incident Management
B98 Table Of Contents For Deploying Computer Security Incident ManagementPresent the topic in a bit more detail with this B98 Table Of Contents For Deploying Computer Security Incident Management . Use it as a tool for discussion and navigation on Best Practices, Cyber Security, Incident Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices For Cybersecurity Incident Management Deploying Computer Security Incident
Best Practices For Cybersecurity Incident Management Deploying Computer Security IncidentThis slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc.Increase audience engagement and knowledge by dispensing information using Best Practices For Cybersecurity Incident Management Deploying Computer Security Incident. This template helps you present information on five stages. You can also present information on Incident Management, Management Process, Responsibilities Members using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Common Sources Of Precursors And Indicators Deploying Computer Security Incident Management
Common Sources Of Precursors And Indicators Deploying Computer Security Incident ManagementThis slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc.Present the topic in a bit more detail with this Common Sources Of Precursors And Indicators Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Antivirus Software, Based Guarantee, Operating System. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Crisis Management Action Plan Timeline Deploying Computer Security Incident Management
Cyber Security Crisis Management Action Plan Timeline Deploying Computer Security Incident ManagementThis slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery.Present the topic in a bit more detail with this Cyber Security Crisis Management Action Plan Timeline Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Business Continuity, Incident Response, Review Recovery. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Event And Incident Flow Diagram Deploying Computer Security Incident Management
Cyber Security Event And Incident Flow Diagram Deploying Computer Security Incident ManagementThis slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation.Present the topic in a bit more detail with this Cyber Security Event And Incident Flow Diagram Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Information Collection, Confirmed Security Incident, Categorize Incidents. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Communication Strategy Deploying Computer Security Incident Management
Cyber Security Incident Communication Strategy Deploying Computer Security Incident ManagementThis slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders.Introducing Cyber Security Incident Communication Strategy Deploying Computer Security Incident Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Senior Management, Impacted Business, Incident Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Handler Contact Information Deploying Computer Security Incident Management
Cyber Security Incident Handler Contact Information Deploying Computer Security Incident ManagementThis slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler.Present the topic in a bit more detail with this Cyber Security Incident Handler Contact Information Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Incident Response Management, Forensic Expert, Law Enforcement. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Handling Checklist Deploying Computer Security Incident Management
Cyber Security Incident Handling Checklist Deploying Computer Security Incident ManagementThis slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post incident activity.Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Handling Checklist Deploying Computer Security Incident Management. This template helps you present information on one stage. You can also present information on Containment Eradication, Acquisition Preservation, Incident Containment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Checklist After An Incident Deploying Computer Security
Cyber Security Incident Management Checklist After An Incident Deploying Computer SecurityThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident.Introducing Cyber Security Incident Management Checklist After An Incident Deploying Computer Security to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Reporting Requirements, Quantify Financial, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Team Structure Deploying Computer Security Incident Management
Cyber Security Incident Management Team Structure Deploying Computer Security Incident ManagementThis slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team.Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Team Structure Deploying Computer Security Incident Management. This template helps you present information on five stages. You can also present information on Systems Analyst, Network Analyst, Firewall Administration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Response Lifecycle Deploying Computer Security Incident Management
Cyber Security Incident Response Lifecycle Deploying Computer Security Incident ManagementThis slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc.Introducing Cyber Security Incident Response Lifecycle Deploying Computer Security Incident Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Eradication Recovery, Post Incident Activity, Remove Malwares, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Response Plan Timeline Deploying Computer Security Incident Management
Cyber Security Incident Response Plan Timeline Deploying Computer Security Incident ManagementThis slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow.Present the topic in a bit more detail with this Cyber Security Incident Response Plan Timeline Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Cyber Incident, Verification Incident, Dispatch Incident. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident Management
Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident ManagementThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery.Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident Management. This template helps you present information on Two stages. You can also present information on Agency Reporting, Investigation Scope Determination, Collection Preservation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incidents Follow Up Report Deploying Computer Security Incident Management
Cyber Security Incidents Follow Up Report Deploying Computer Security Incident ManagementThis slide represents the follow up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer.Present the topic in a bit more detail with this Cyber Security Incidents Follow Up Report Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Confidential Information, Training Employees, Organizational Projects. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Threats Detection Techniques Deploying Computer Security Incident Management
Cyber Security Threats Detection Techniques Deploying Computer Security Incident ManagementThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc.Present the topic in a bit more detail with this Cyber Security Threats Detection Techniques Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Threat Intelligence, Access Regularly, Undercovers Intruders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
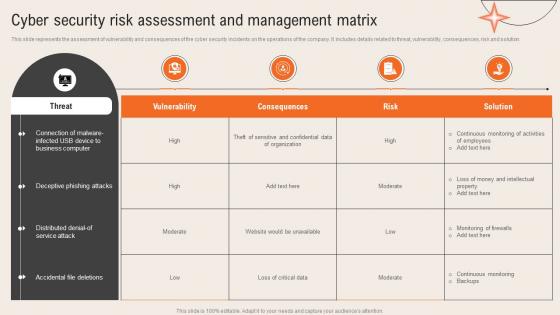 Deploying Computer Security Incident Cyber Security Risk Assessment And Management Matrix
Deploying Computer Security Incident Cyber Security Risk Assessment And Management MatrixThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution.Present the topic in a bit more detail with this Deploying Computer Security Incident Cyber Security Risk Assessment And Management Matrix. Use it as a tool for discussion and navigation on Deceptive Phishing, Business Computer, Accidental File Deletions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Five Phases Of Cybersecurity Incident Management Deploying Computer Security Incident Management
Five Phases Of Cybersecurity Incident Management Deploying Computer Security Incident ManagementThis slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc.Introducing Five Phases Of Cybersecurity Incident Management Deploying Computer Security Incident Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Sharing Information, Establish Policies, Response Process, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Implementing Cyber Security Incident Management
Icons Slide Implementing Cyber Security Incident ManagementIntroducing our well researched set of slides titled Icons Slide Implementing Cyber Security Incident Management. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Impact Of Cybersecurity Incidents On Organization Deploying Computer Security Incident Management
Impact Of Cybersecurity Incidents On Organization Deploying Computer Security Incident ManagementThis slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc.Increase audience engagement and knowledge by dispensing information using Impact Of Cybersecurity Incidents On Organization Deploying Computer Security Incident Management. This template helps you present information on five stages. You can also present information on Increased Costs, Operational Disruption, Reputational Damage using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents For Deploying Computer Security Incident Management
Table Of Contents For Deploying Computer Security Incident ManagementPresent the topic in a bit more detail with this Table Of Contents For Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Key Issues Faced, Cyber Security Incident, Incident Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ways To Detect Cyber Security Incidents Deploying Computer Security Incident Management
Ways To Detect Cyber Security Incidents Deploying Computer Security Incident ManagementThis slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc.Increase audience engagement and knowledge by dispensing information using Ways To Detect Cyber Security Incidents Deploying Computer Security Incident Management. This template helps you present information on four stages. You can also present information on Unusual Behavior, Privileged Accounts, Anomalies Outbound using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Success For Cyber Security Risk Management
Steps To Success For Cyber Security Risk ManagementThe following slide provides a cyber risk management framework to help an organisation monitor and eliminate risk effectively. Key steps are identify, protect, detect, respond and recover.Presenting our set of slides with Steps To Success For Cyber Security Risk Management. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identity, Protect, Detect, Respond.
-
 Role Of Management In Security Governance Across Firm Winning Corporate Strategy For Boosting Firms
Role Of Management In Security Governance Across Firm Winning Corporate Strategy For Boosting FirmsThis slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Present the topic in a bit more detail with this Role Of Management In Security Governance Across Firm Winning Corporate Strategy For Boosting Firms. Use it as a tool for discussion and navigation on Senior Executives, Steering Committees, Information Security Officer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Importance Of Secure Ecommerce Payment Deploying Effective Ecommerce Management
Importance Of Secure Ecommerce Payment Deploying Effective Ecommerce ManagementThis slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. Present the topic in a bit more detail with this Importance Of Secure Ecommerce Payment Deploying Effective Ecommerce Management. Use it as a tool for discussion and navigation on Meets Digital Needs, Customer Retention, Multiple Payment Modes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 360 Security Manager Colored Icon In Powerpoint Pptx Png And Editable Eps Format
360 Security Manager Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable 360 Security Manager Colored Icon In Powerpoint Pptx Png And Editable Eps Format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 360 Security Manager Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
360 Security Manager Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable 360 Security Manager Monotone Icon In Powerpoint Pptx Png And Editable Eps Format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Online Security Manager Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Online Security Manager Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Online Security Manager Colored Icon In Powerpoint Pptx Png And Editable Eps Format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Online Security Manager Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Online Security Manager Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Online Security Manager Monotone Icon In Powerpoint Pptx Png And Editable Eps Format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Security And Risk Manager Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Security And Risk Manager Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Security And Risk Manager Colored Icon In Powerpoint Pptx Png And Editable Eps Format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Security And Risk Manager Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Security And Risk Manager Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Security And Risk Manager Monotone Icon In Powerpoint Pptx Png And Editable Eps Format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Essential Initiatives To Safeguard Role Of Management In Effective Corporate Security Governance
Essential Initiatives To Safeguard Role Of Management In Effective Corporate Security GovernanceThis slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief security office in order to ensure the effective corporate security governance. Deliver an outstanding presentation on the topic using this Essential Initiatives To Safeguard Role Of Management In Effective Corporate Security Governance. Dispense information and present a thorough explanation of Measuring Performance, Risk Management, Strategic Alignment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
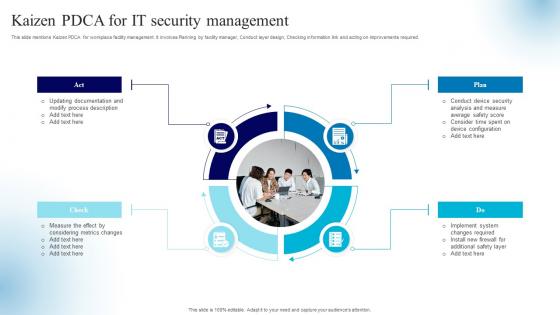 Kaizen PDCA For IT Security Management
Kaizen PDCA For IT Security ManagementThis slide mentions Kaizen PDCA for workplace facility management. It involves Planning by facility manager, Conduct layer design, Checking information link and acting on improvements required. Presenting our set of slides with name Kaizen PDCA For IT Security Management. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Considering Metrics, Changes Required, Device Security.
-
 Strategic IT Cost Optimization Role Of Management In Effective Information Security Governance
Strategic IT Cost Optimization Role Of Management In Effective Information Security GovernanceThis slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Present the topic in a bit more detail with this Strategic IT Cost Optimization Role Of Management In Effective Information Security Governance. Use it as a tool for discussion and navigation on Senior Executives, Steering Committees, Information Security Officer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies For Liquidity Risk Management To Secure Cash Flow
Strategies For Liquidity Risk Management To Secure Cash FlowThis slide mentions strategies for liquidity risk management to secure cash flow in the organizations. It includes improving company cash flow management, improving risk reporting abilities and undergo stress tests.Introducing our premium set of slides with Strategies For Liquidity Risk Management To Secure Cash Flow. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Improve Company, Reporting Abilities, Situations Unfolding. So download instantly and tailor it with your information.
-
 F1190 Managing Cyber Security In Manufacturing 30 Days Plan 3d Printing In Manufacturing
F1190 Managing Cyber Security In Manufacturing 30 Days Plan 3d Printing In ManufacturingThis slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Present the topic in a bit more detail with this F1190 Managing Cyber Security In Manufacturing 30 Days Plan 3d Printing In Manufacturing. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing,Reporting, Phishing Repeat Offenders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1191 Managing Cyber Security In Manufacturing 60 Days Plan 3d Printing In Manufacturing
F1191 Managing Cyber Security In Manufacturing 60 Days Plan 3d Printing In ManufacturingThis slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Deliver an outstanding presentation on the topic using this F1191 Managing Cyber Security In Manufacturing 60 Days Plan 3d Printing In Manufacturing. Dispense information and present a thorough explanation of Policy Violations, Data Loss Incidents, Infected Computers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing Cyber Security In Manufacturing 90 Days Plan 3d Printing In Manufacturing
Managing Cyber Security In Manufacturing 90 Days Plan 3d Printing In ManufacturingThis slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, andteams who are responsible and details. Deliver an outstanding presentation on the topic using this Managing Cyber Security In Manufacturing 90 Days Plan 3d Printing In Manufacturing. Dispense information and present a thorough explanation of Training Completion, Communication Methods, Manufacturing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Strategy Planning Guide How Management Enables Effective Corporate Security Governance Strategy SS V
IT Strategy Planning Guide How Management Enables Effective Corporate Security Governance Strategy SS VThis slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Deliver an outstanding presentation on the topic using this IT Strategy Planning Guide How Management Enables Effective Corporate Security Governance Strategy SS V. Dispense information and present a thorough explanation of Demonstrate Alignment Process, Management, Corporate Security Governance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Strategy Planning Guide Information Security And Governance Management Framework Strategy SS V
IT Strategy Planning Guide Information Security And Governance Management Framework Strategy SS VThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this IT Strategy Planning Guide Information Security And Governance Management Framework Strategy SS V. Use it as a tool for discussion and navigation on Information Security, Governance, Management Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Strategy Planning Guide IT Risk Management Framework To Manage Security Threats Strategy SS V
IT Strategy Planning Guide IT Risk Management Framework To Manage Security Threats Strategy SS VThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Deliver an outstanding presentation on the topic using this IT Strategy Planning Guide IT Risk Management Framework To Manage Security Threats Strategy SS V. Dispense information and present a thorough explanation of IT Risk Management, Framework To Manage, Security Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Governance Management Blueprint Develop Information It Roadmap Strategy Ss
Information Security And Governance Management Blueprint Develop Information It Roadmap Strategy SsThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this Information Security And Governance Management Blueprint Develop Information It Roadmap Strategy Ss. Use it as a tool for discussion and navigation on Evaluation And Direction, Identify Security, Infrastructure Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It Risk Management Framework To Manage Security Blueprint Develop Information It Roadmap Strategy Ss
It Risk Management Framework To Manage Security Blueprint Develop Information It Roadmap Strategy SsThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Present the topic in a bit more detail with this It Risk Management Framework To Manage Security Blueprint Develop Information It Roadmap Strategy Ss. Use it as a tool for discussion and navigation on Management, Framework, Environment. This template is free to edit as deemed fit for your organization. Therefore download it now.





