Powerpoint Templates and Google slides for Secured
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Analyzing High Risk Employees And Departments IT Security Awareness Training Cybersecurity SS
Analyzing High Risk Employees And Departments IT Security Awareness Training Cybersecurity SSThis slide represents report for analyzing high risk participants and departments that requires continuous IT security awareness training. It includes details related to high risk participants etc. Present the topic in a bit more detail with this Analyzing High Risk Employees And Departments IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Analyzing High Risk, Employees And Departments, Marketing Team, Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Awareness Training Program Outline IT Security Awareness Training Cybersecurity SS
Cloud Security Awareness Training Program Outline IT Security Awareness Training Cybersecurity SSThis slide represents overview of training program highlighting set of measures which protects data stored online from theft, leakage and detection. It includes details related to program overview, skills etc. Introducing Cloud Security Awareness Training Program Outline IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Security Awareness, Training Program Outline, Cloud Architecture And Design, Cloud Infrastructure Security, using this template. Grab it now to reap its full benefits.
-
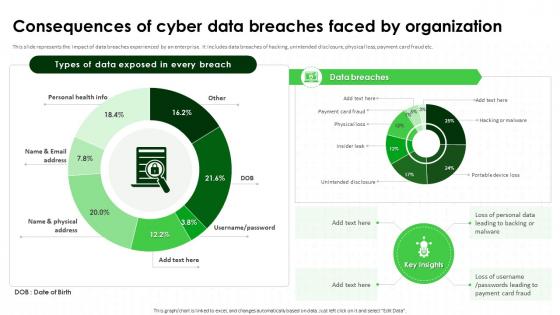 Consequences Of Cyber Data Breaches Faced IT Security Awareness Training Cybersecurity SS
Consequences Of Cyber Data Breaches Faced IT Security Awareness Training Cybersecurity SSThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Present the topic in a bit more detail with this Consequences Of Cyber Data Breaches Faced IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Consequences Of Cyber Data Breaches, Unintended Disclosure, Physical Loss, Payment Card Fraud. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Gap Analysis Representing Current Situation Of Cyber IT Security Awareness Training Cybersecurity SS
Gap Analysis Representing Current Situation Of Cyber IT Security Awareness Training Cybersecurity SSThis slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. Deliver an outstanding presentation on the topic using this Gap Analysis Representing Current Situation Of Cyber IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Gap Analysis Representing, Current Situation Of Cyber Attacks, Employee Productivity Rates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact Of IT Security Awareness Program On Organizational Kpis Cybersecurity SS
Impact Of IT Security Awareness Program On Organizational Kpis Cybersecurity SSThis slide represents impact of strategy deployed by IT and security professionals for preventing and mitigating cyber security risks on organizational KPIs such as annual revenue etc. Present the topic in a bit more detail with this Impact Of IT Security Awareness Program On Organizational Kpis Cybersecurity SS. Use it as a tool for discussion and navigation on Increase In Potential Annual Revenue, Increase In Employee Productivity Rates, Increase In Customer Satisfaction Rates. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
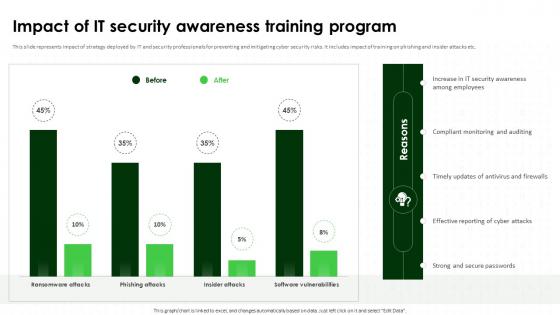 Impact Of IT Security Awareness Training Program Cybersecurity SS
Impact Of IT Security Awareness Training Program Cybersecurity SSThis slide represents impact of strategy deployed by IT and security professionals for preventing and mitigating cyber security risks. It includes impact of training on phishing and insider attacks etc. Deliver an outstanding presentation on the topic using this Impact Of IT Security Awareness Training Program Cybersecurity SS. Dispense information and present a thorough explanation of Compliant Monitoring And Auditing, Security Awareness Training Program, Strong And Secure Passwords using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
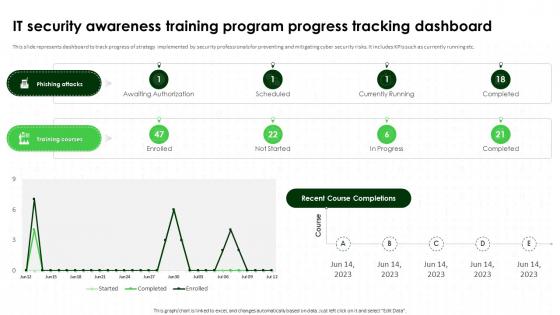 IT Security Awareness Training Program Progress Tracking Dashboard Cybersecurity SS
IT Security Awareness Training Program Progress Tracking Dashboard Cybersecurity SSThis slide represents dashboard to track progress of strategy implemented by security professionals for preventing and mitigating cyber security risks. It includes KPIs such as currently running etc. Deliver an outstanding presentation on the topic using this IT Security Awareness Training Program Progress Tracking Dashboard Cybersecurity SS. Dispense information and present a thorough explanation of Dashboard To Track Progress, Strategy Implemented, Security Professionals using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Security Awareness Training Statistical Data Highlighting It Security Unawareness Cybersecurity SS
IT Security Awareness Training Statistical Data Highlighting It Security Unawareness Cybersecurity SSThis slide represents statistical insights highlighting importance of implementing strategy adopted by IT teams and security professionals for preventing and mitigating security risks. Present the topic in a bit more detail with this IT Security Awareness Training Statistical Data Highlighting It Security Unawareness Cybersecurity SS. Use it as a tool for discussion and navigation on Implementing Strategy, Security Professionals, Mitigating Security Risks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
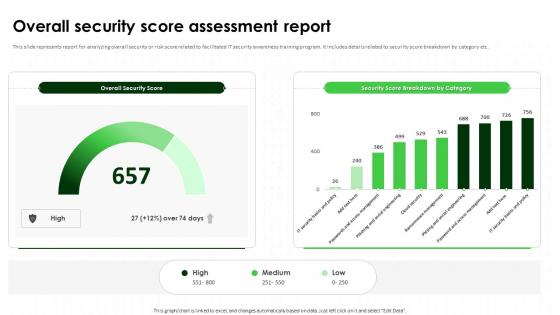 Overall Security Score Assessment Report IT Security Awareness Training Cybersecurity SS
Overall Security Score Assessment Report IT Security Awareness Training Cybersecurity SSThis slide represents report for analyzing overall security or risk score related to facilitated IT security awareness training program. It includes details related to security score breakdown by category etc. Deliver an outstanding presentation on the topic using this Overall Security Score Assessment Report IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Overall Security Score, Assessment Report, Security Or Risk Score, Awareness Training Program using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Training Awareness And Defense IT Security Awareness Training Cybersecurity SS
Social Engineering Training Awareness And Defense IT Security Awareness Training Cybersecurity SSThis slide represents overview of training course for mitigating cybercrime which involves tracking a target into giving money or data. It includes details related to training program overview, target audience etc. Introducing Social Engineering Training Awareness And Defense IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering Training, Awareness And Defense Course Outline, Training Program Overview, Target Audience, using this template. Grab it now to reap its full benefits.
-
 Edr Cybersecurity Dashboard To Track Threats Building Next Generation Endpoint Security Cybersecurity SS
Edr Cybersecurity Dashboard To Track Threats Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint detection and response EDR dashboard which can help analyze malicious operations Malops and provide information about scans, investigations, activities, etc.Deliver an outstanding presentation on the topic using this Edr Cybersecurity Dashboard To Track Threats Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Affected, Affected Users, Recent Activity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Endpoint Cyber Security Budget Plan Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Cyber Security Budget Plan Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases security budget plan for endpoint operations. It provides details about secure data transmission, frontline defense, external network threats, etc.Present the topic in a bit more detail with this Endpoint Cyber Security Budget Plan Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Endpoint Operations, Secure Data Transmission, Frontline Defense, External Network Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Endpoint Security Issues With Compromised Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Issues With Compromised Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases organizational survey highlighting endpoint security issues with compromised devices. It includes details about desktops, laptops, online servers, etc.Present the topic in a bit more detail with this Endpoint Security Issues With Compromised Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Key Insights, Survey Question, Reasons. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Endpoint Security Market Size Analysis Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Market Size Analysis Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint security market size analysis, referable for related businesses and investors. It provides details about bring your own device BYOD, smart sensors, etc.Present the topic in a bit more detail with this Endpoint Security Market Size Analysis Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Market Projection, Factors Driving Growth, Smart Sensors. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Impact Of Endpoint Security Attacks Building Next Generation Endpoint Security Cybersecurity SS
Financial Impact Of Endpoint Security Attacks Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases financial impact of endpoint attacks, which can help organizations assess their costs and plan recovery strategies of system downtime, information assets, etc.Deliver an outstanding presentation on the topic using this Financial Impact Of Endpoint Security Attacks Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Zero Day, Polymorphic Malware, Malicious Code using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SS
Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases managing endpoint security access management through just in time method. It provides details about access request, permission duration, etc.Present the topic in a bit more detail with this Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Access Request, Our Process, Potential Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web Security Upgradation Cost Distribution For Web Security Training
Web Security Upgradation Cost Distribution For Web Security TrainingThis slide showcases the training cost breakdown for different components such as instructor, training cost, etc. Present the topic in a bit more detail with this Web Security Upgradation Cost Distribution For Web Security Training. Use it as a tool for discussion and navigation on Instructor Cost, Training Cost, Hiring Staff. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
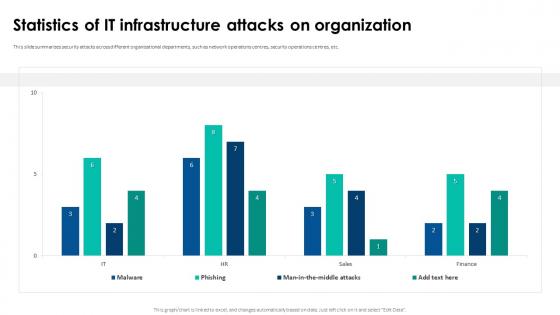 Web Security Upgradation Statistics Of It Infrastructure Attacks On Organization
Web Security Upgradation Statistics Of It Infrastructure Attacks On OrganizationThis slide summarizes security attacks across different organizational departments, such as network operations centres, security operations centres, etc. Present the topic in a bit more detail with this Web Security Upgradation Statistics Of It Infrastructure Attacks On Organization. Use it as a tool for discussion and navigation on Statistics Of IT Infrastructure, Attacks On Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web Security Upgradation Web Attacks Experienced By Company In Previous Financial Year
Web Security Upgradation Web Attacks Experienced By Company In Previous Financial YearThis slide depicts the web security incidents encountered by the organization in the last financial year. Present the topic in a bit more detail with this Web Security Upgradation Web Attacks Experienced By Company In Previous Financial Year. Use it as a tool for discussion and navigation on Web Attacks Experienced By Company, Previous Financial Year. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Chatbot Security Solutions Market Size
Chatbot Security Solutions Market SizeThis slide shows a graph that can be used to highlight or represent the current and expected future market share of chatbot security solutions. It includes information regarding compound annual growth rate and growth drivers. Introducing our Chatbot Security Solutions Market Size set of slides. The topics discussed in these slides are Chatbot Security Solutions, Market Size, 2024 To 2034. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Chatbot Security Survey Results Graph
Chatbot Security Survey Results GraphThis slide shows information that organizations can use to understand or evaluate customers confidence in chatbot security, specifically in banking and shopping activities. It includes information regarding customers privacy concerns. Presenting our well structured Chatbot Security Survey Results Graph. The topics discussed in this slide are Key Insights, Online Privacy, Chatbots Banking, Online Shopping. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 A60 Email Security Best Practices And Email Security Vendor Market Share
A60 Email Security Best Practices And Email Security Vendor Market ShareThis slide represents the market of different email security service providers available in the market. The purpose of this slide is to depict the market share of each of the service providers, such as Symantec, Microsoft, Google, Mimecast, etc. Present the topic in a bit more detail with this A60 Email Security Best Practices And Email Security Vendor Market Share. Use it as a tool for discussion and navigation on Microsoft Accounts, Email Security Market. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Advanced Email Security Management Dashboard
Email Security Best Practices Advanced Email Security Management DashboardThis slide represents the dashboard to track email security incident management process. The purpose of this slide is to provide a graphical representation of email traffic, mitigation summary, unsolicited emails, advanced threat prevention, etc. Present the topic in a bit more detail with this Email Security Best Practices Advanced Email Security Management Dashboard. Use it as a tool for discussion and navigation on Email Traffic, Blocked Summary, Mitigation Summary, Advanced Threat Prevention, Data Loss Prevention, Unsolicited Emails. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Benefits Of Using Email Security Technologies
Email Security Best Practices Benefits Of Using Email Security TechnologiesThis slide outlines the advantages of email security. These include control device access, identify suspicious user behaviour, improve spam and phishing protection, maintain communication confidentiality, protection against zero-day threats, real-time threat protection, etc. Present the topic in a bit more detail with this Email Security Best Practices Benefits Of Using Email Security Technologies. Use it as a tool for discussion and navigation on Control Device Access, Identify Suspicious User Behaviour, Real-Time Threat Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Common Types Of Email Security Attacks
Email Security Best Practices Common Types Of Email Security AttacksThe purpose of this slide is to discuss the different types of email security threats in current digital era. These email security attacks are phishing, social engineering, spear phishing, ransomware, malware and spoofing. Introducing Email Security Best Practices Common Types Of Email Security Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Phishing, Social Engineering, Spear Phishing, Ransomware, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Estimated Cost For Email Security Training Program
Email Security Best Practices Estimated Cost For Email Security Training ProgramThis slide shows the cost breakup of email security training program for beginners. The purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc. Present the topic in a bit more detail with this Email Security Best Practices Estimated Cost For Email Security Training Program. Use it as a tool for discussion and navigation on Training Cost Distribution, Instructors Cost, Training Material Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Global Email Security Market Forecast
Email Security Best Practices Global Email Security Market ForecastThis slide demonstrates the global market share of email security. The key components of this slide are email security market size, regional analysis, component segment overview of products and services, etc. Present the topic in a bit more detail with this Email Security Best Practices Global Email Security Market Forecast. Use it as a tool for discussion and navigation on Market Size, Overview, Regional Analysis, Component Segment Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
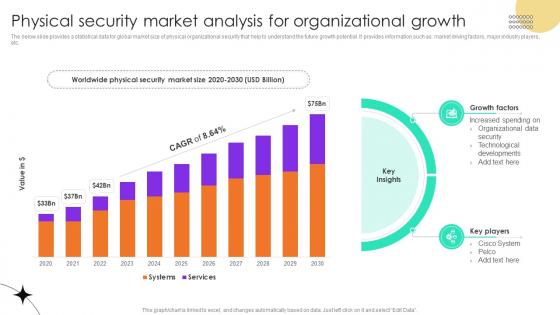 Physical Security Market Analysis For Organizational Growth
Physical Security Market Analysis For Organizational GrowthThe below slide provides a statistical data for global market size of physical organizational security that help to understand the future growth potential. It provides information such as market driving factors, major industry players, etc. Introducing our Physical Security Market Analysis For Organizational Growth set of slides. The topics discussed in these slides are Growth Factors, Key Players, Organizational Data. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Beneficial Impact Of IOT Security On Business
Beneficial Impact Of IOT Security On BusinessThis slide showcases benefits of implementing IoT security solutions in company. Major benefits covered are reduced malicious attacks, increased cost savings, improved customer trust and enhanced system reliability. Introducing our Beneficial Impact Of IOT Security On Business set of slides. The topics discussed in these slides are Key Insights, Encryption, Application Security, Compliance. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 IOT Security Dashboard To Track Attack Status
IOT Security Dashboard To Track Attack StatusThis provides an overview of the dashboard to determine number of potential threats. It includes events triggered, new and unique devices, DDoS threats, ransomware and miners threat. Introducing our IOT Security Dashboard To Track Attack Status set of slides. The topics discussed in these slides are New Device, Hotspot Active, Insecure Device. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 IOT Security Market Size And Insights
IOT Security Market Size And InsightsThis slide showcases Internet of things technology market size. It also includes market factors that are increased data breaches and smart cities development. Presenting our well structured IOT Security Market Size And Insights. The topics discussed in this slide are Key Insights, Increased Data Breaches, Smart City Development. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Key Statistics For IOT Security System
Key Statistics For IOT Security SystemThis slide showcases key statistics regarding IoT security. it includes stats regarding use of IoT devices for attacks, supporting business goals through IoT and OT, etc. Introducing our Key Statistics For IOT Security System set of slides. The topics discussed in these slides are Businesses, Increase, Practitioners. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Major IOT Security Threats And Its Negative Effects
Major IOT Security Threats And Its Negative EffectsThis slide showcases major security threats that disrupt the operations. Threats covered are buffer overflow, SQL injection, worm, botnet, ransomware, password, phishing, crypto jacking, etc. Presenting our well structured Major IOT Security Threats And Its Negative Effects. The topics discussed in this slide are Negative Effective, Lack Visibility, Poor Testing. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Global Market Growth Of Wireless Lan Security
Global Market Growth Of Wireless Lan SecurityThis slide graphically represents the growth of wireless LAN security global market to reduce growing cases of cybercrime and security. It includes various key drivers such as increasing wireless network deployment, BYOD trends, etc. Introducing our Global Market Growth Of Wireless Lan Security set of slides. The topics discussed in these slides are Security Market, Projected CAGR GrowthThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Building Access Control Security Market Snapshot
Building Access Control Security Market SnapshotThis slide showcases the building access control security market size referable for users,investors and business owners for making relevant decisions. It include details such as increase in the demand for advanced technologies and rise of 5g networks. Introducing our Building Access Control Security Market Snapshot set of slides. The topics discussed in these slides are Market Size,Projections USD Bn,Top Companies. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Building Security Dashboard Illustrating Vulnerability Status
Building Security Dashboard Illustrating Vulnerability StatusThis slide showcases the building security dashboard representing vulnerability status which helps an organization to improve customer service by offering quick response time. It include details such as per stage vulnerabilities,awaiting execution average days,etc. Introducing our Building Security Dashboard Illustrating Vulnerability Status set of slides. The topics discussed in these slides are Vulnerability Status,Awaiting Attention,Per Stage Vulnerabilities. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Statistical Graph Illustrating Building Enterprise Security Architecture
Statistical Graph Illustrating Building Enterprise Security ArchitectureThis slide showcases the statistical graph highlighting creating enterprise security architecture which helps an organization to create better,secure and safer environment. It include details such as enhances security support,improves team collaboration,etc. Introducing our Statistical Graph Illustrating Building Enterprise Security Architecture set of slides. The topics discussed in these slides are Devops Security,Building Securitys Success,Key Reasons. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 A248 Web Security Performance Monitoring Dashboard
A248 Web Security Performance Monitoring DashboardThis slide showcases the performance tracking dashboard for web security based on various parameters such as open cases, event status, etc. Present the topic in a bit more detail with this A248 Web Security Performance Monitoring Dashboard. Use it as a tool for discussion and navigation on Web Security Performance, Monitoring Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
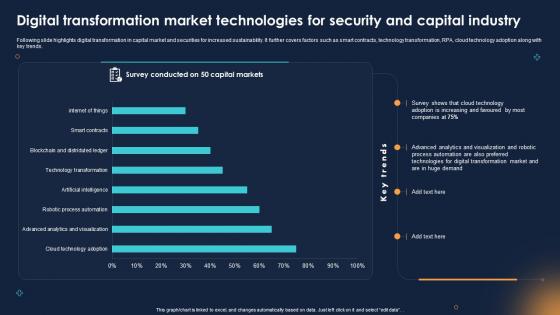 Digital Transformation Market Technologies For Security And Capital Industry
Digital Transformation Market Technologies For Security And Capital IndustryFollowing slide highlights digital transformation in capital market and securities for increased sustainability. It further covers factors such as smart contracts, technology transformation, RPA, cloud technology adoption along with key trends. Presenting our well structured Digital Transformation Market Technologies For Security And Capital Industry. The topics discussed in this slide are Digital Transformation Market Technologies, Security And Capital Industry, Visualization And Robotic Process. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Client Testimonials For Endpoint Security Upgradation Proposal
Client Testimonials For Endpoint Security Upgradation ProposalIntroducing Client Testimonials For Endpoint Security Upgradation Proposal to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Client Testimonials, using this template. Grab it now to reap its full benefits.
-
 Our Team For Endpoint Security Upgradation Proposal
Our Team For Endpoint Security Upgradation ProposalThis slide represents an overview of the team structure for the endpoint security upgradation proposal including the names and designations of each member. Introducing Our Team For Endpoint Security Upgradation Proposal to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Our Team, using this template. Grab it now to reap its full benefits.
-
 Best Practices To Secure GAN Generated Data Generative Adversarial Network AI SS
Best Practices To Secure GAN Generated Data Generative Adversarial Network AI SSThis slide provides information regarding best practices to enable the security of GAN-generated data through the use of encryption, application of watermarking, and deployment of access control. Introducing Best Practices To Secure GAN-Generated Data Generative Adversarial Network AI SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Usage Of Encryption, Application Of Watermarking, Deploy Access Control, using this template. Grab it now to reap its full benefits.
-
 Analyzing Security Token Market Size And Growth Rate Ultimate Guide Smart BCT SS V
Analyzing Security Token Market Size And Growth Rate Ultimate Guide Smart BCT SS VThe following slide focusses on security token market size to foster crowd funding. It includes elements such as total private asset market, security token market, key drivers, market size, etc. Deliver an outstanding presentation on the topic using this Analyzing Security Token Market Size And Growth Rate Ultimate Guide Smart BCT SS V. Dispense information and present a thorough explanation of Security Token, Market Size, Total Private, Assets Market using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assessing Number Of Security Tokens Launched By Ultimate Guide Smart BCT SS V
Assessing Number Of Security Tokens Launched By Ultimate Guide Smart BCT SS VThe following slide depicts the type of funds raised from security token offerings STOs to invest in digital assets. It includes elements such as company equity, participation rate, equity funds, real estate investment, bonds, masternode funds, etc. Present the topic in a bit more detail with this Assessing Number Of Security Tokens Launched By Ultimate Guide Smart BCT SS V. Use it as a tool for discussion and navigation on Fast Deal Closing, Automated Compliance, Large Audience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS V
Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS VThe following slide depicts the percentage of funds raised through security token offerings STOs launched by region. It includes middle east, eastern and western Europe, north America, Oceania, sub Saharan Africa, etc. Present the topic in a bit more detail with this Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS V. Use it as a tool for discussion and navigation on Funds Raised, Sub Saharan, Africa Region. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Statistical Representation Of Risk Level In Application Security
Statistical Representation Of Risk Level In Application SecurityPresenting our well structured Statistical Representation Of Risk Level In Application Security The topics discussed in this slide are Assessment Phase, Establish Security PoliciesThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Budget Share For Implementing Mobile Security Solutions Mobile Device Security Cybersecurity SS
Budget Share For Implementing Mobile Security Solutions Mobile Device Security Cybersecurity SSBudget Share For Implementing Mobile Security Solutions Mobile Device Security Cybersecurity SS This slide showcases expenses share to implement mobile device threat management solutions. Its key elements are biometric solutions, VPN, software upgradation, mobile device management Present the topic in a bit more detail with this Biometric Solutions, Security Awareness Use it as a tool for discussion and navigation on Biometric Solutions, Security Awareness This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks On Employee Mobile Devices Mobile Device Security Cybersecurity SS
Cyber Attacks On Employee Mobile Devices Mobile Device Security Cybersecurity SSThis slide showcases cyber threats faced by workforce on mobile devices. It highlights data regarding malware, phishing attacks, ransomware etc. Present the topic in a bit more detail with this Cyber Attacks On Employee Mobile Devices Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Awareness Training, Weak Security Measures This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SS
Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SSThis slide showcases decrease in cyber attacks after implementation of mobile security. Its key elements are malware, phishing attacks and ransomware Deliver an outstanding presentation on the topic using this Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Advanced Persistent Threats, Diverse Cyber Threat Landscape using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Dashboard To Track Cyber Threats In Organization Mobile Device Security Cybersecurity SS
Dashboard To Track Cyber Threats In Organization Mobile Device Security Cybersecurity SSThis slides showcases dashboard that can help to track number of cyber threats in organization. Its key elements are hacker attacks, spyware, viruses and zero day attacks Present the topic in a bit more detail with this Dashboard To Track Cyber Threats In Organization Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Track Cyber Threats, Attacks Types This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Decrease In Cyber Attacks On Different Mobile Devices Mobile Device Security Cybersecurity SS
Decrease In Cyber Attacks On Different Mobile Devices Mobile Device Security Cybersecurity SSThis slide showcases decline in cyber attacks after implementation of mobile security techniques. It highlights decrease in cyber attacks on android and iOS devices Deliver an outstanding presentation on the topic using this Decrease In Cyber Attacks On Different Mobile Devices Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Security Attacks, Mobile Devices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Distribution Of Spyware Threats By Geographical Region Mobile Device Security Cybersecurity SS
Distribution Of Spyware Threats By Geographical Region Mobile Device Security Cybersecurity SSThis slide showcases impact of mobile threats on organization. It highlights impact in terms of company financial loss, operational distribution, cybersecurity expenses, data breach etc. Present the topic in a bit more detail with this Distribution Of Spyware Threats By Geographical Region Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Support And Maintenance, Device Troubleshooting, Access Control This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Faced By Organization Due To Mobile Threats Mobile Device Security Cybersecurity SS
Impact Faced By Organization Due To Mobile Threats Mobile Device Security Cybersecurity SSThis slide showcases impact of mobile threats on organization. It highlights impact in terms of company financial loss, operational distribution, cybersecurity expenses, data breach etc. Present the topic in a bit more detail with this Impact Faced By Organization Due To Mobile Threats Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Before Mobile Security, Management Plan This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mobile Cyber Attacks Occurrence Globally Mobile Device Security Cybersecurity SS
Mobile Cyber Attacks Occurrence Globally Mobile Device Security Cybersecurity SSThis slide showcases number of cyber attacks faced by mobile users around the world. It highlights data regarding attacks faced in last three years Deliver an outstanding presentation on the topic using this Mobile Cyber Attacks Occurrence Globally Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Fingerprint Scanner, Facial Recognition, Voice Recognition using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mobile Malware Attacks By Country Share Mobile Device Security Cybersecurity SS
Mobile Malware Attacks By Country Share Mobile Device Security Cybersecurity SSThis slide showcases percentage share of mobile malware attacks faced in different countries. It highlights share of China, Iran, Yemen, Switzerland, Kenya etc. Present the topic in a bit more detail with this Mobile Malware Attacks By Country Share Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Purpose, Scope, Loss And Theft This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mobile Security Initiatives Tracking Dashboard Mobile Device Security Cybersecurity SS
Mobile Security Initiatives Tracking Dashboard Mobile Device Security Cybersecurity SSThis slide showcases dashboard that can help organization to track mobile device security initiatives. Its key elements are incident management, compliance, patches and vulnerabilities management Deliver an outstanding presentation on the topic using this Mobile Security Initiatives Tracking Dashboard Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Mobile Malware, Country Share using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Number Of Phishing Sites Exploiting Mobile Devices Mobile Device Security Cybersecurity SS
Number Of Phishing Sites Exploiting Mobile Devices Mobile Device Security Cybersecurity SSThis slide showcases percentage of phishing websites that are exploiting the mobile users. It highlights monthly phishing attack data of last year Present the topic in a bit more detail with this Number Of Phishing Sites Exploiting Mobile Devices Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Decrease In Company Loses, Decrease In Operational Disruption This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Volume Of Mobile Malware Detected Globally Mobile Device Security Cybersecurity SS
Volume Of Mobile Malware Detected Globally Mobile Device Security Cybersecurity SSThis slide showcases mobile malware threats globally faced by the users. It also sites key reasons for mobile malware that are lack of security awareness, inadequate security practices etc. Present the topic in a bit more detail with this Volume Of Mobile Malware Detected Globally Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Security Awareness, Exploitation Of Vulnerabilities, Inadequate Security Practices This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Challenges And Solutions Of Enterprise Network Security
Challenges And Solutions Of Enterprise Network SecurityThis slide focuses on enterprise network security challenging solutions including phishing attacks, insider threats, and data breaches. Introducing our Challenges And Solutions Of Enterprise Network Security set of slides. The topics discussed in these slides are Challenges, Phishing Attacks, Insider Threats, Data Breaches. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Network Security Dashboard For Threat Detection And Response
Network Security Dashboard For Threat Detection And ResponseThis slide illustrates KPI Dashboard of network security including attack type, authentication, firewall events, and attack rates. Introducing our Network Security Dashboard For Threat Detection And Response set of slides. The topics discussed in these slides are Attack Type, Authentication, Firewall Events. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.





