Powerpoint Templates and Google slides for Secured
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Extensive Business Strategy Overview Of Key KPMG Cyber Security Considerations Strategy SS V
Extensive Business Strategy Overview Of Key KPMG Cyber Security Considerations Strategy SS VThis slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights Present the topic in a bit more detail with this Extensive Business Strategy Overview Of Key KPMG Cyber Security Considerations Strategy SS V. Use it as a tool for discussion and navigation on Cyber Security Considerations, Description, Insights. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Quarterly Loss Incurred Due To Blockchain Frauds Hands On Blockchain Security Risk BCT SS V
Quarterly Loss Incurred Due To Blockchain Frauds Hands On Blockchain Security Risk BCT SS VThe following slide depicts the amount of loss incurred due to blockchain frauds and scams to securely encrypt financial transactions. It includes elements such as loss amount, number of incidents along with key insights, etc. Present the topic in a bit more detail with this Quarterly Loss Incurred Due To Blockchain Frauds Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Quarterly Loss Incurred Due. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Top Ten Cryptocurrency Thefts Incidents By Amount Hands On Blockchain Security Risk BCT SS V
Top Ten Cryptocurrency Thefts Incidents By Amount Hands On Blockchain Security Risk BCT SS VThe following slide represents the number of cryptocurrencies theft incidents by total amount to prevent attackers from unauthorized access. It includes elements such as Ronin, poly network, wormhole, BITMART, Venus, cream finance, along with key insights, etc. Present the topic in a bit more detail with this Top Ten Cryptocurrency Thefts Incidents By Amount Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Top Ten Cryptocurrency, Thefts Incidents By Amount. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Total Cryptocurrency Stolen By Victim Type Hands On Blockchain Security Risk BCT SS V
Total Cryptocurrency Stolen By Victim Type Hands On Blockchain Security Risk BCT SS VThe following slide depicts the total amount of cryptocurrencies stolen. It includes elements such as centralized exchange, decentralized finance protocol, etc. Deliver an outstanding presentation on the topic using this Total Cryptocurrency Stolen By Victim Type Hands On Blockchain Security Risk BCT SS V. Dispense information and present a thorough explanation of Total Cryptocurrency, Stolen By Victim Type using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Types Of Honeypot Technologies In Blockchain Hands On Blockchain Security Risk BCT SS V
Various Types Of Honeypot Technologies In Blockchain Hands On Blockchain Security Risk BCT SS VThe following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Honeypot Technologies In Blockchain Hands On Blockchain Security Risk BCT SS V. This template helps you present information on two stages. You can also present information on Client Honeyspot, Malware Honeypots using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Year Over Year Blockchain Fraud Trends Hands On Blockchain Security Risk BCT SS V
Year Over Year Blockchain Fraud Trends Hands On Blockchain Security Risk BCT SS VThe following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc. Present the topic in a bit more detail with this Year Over Year Blockchain Fraud Trends Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Year Over Year, Blockchain Fraud Trends. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Management Market Snapshot
Network Security Management Market SnapshotThis slide showcases the network security management referable for users, investors and business owners for making relevant industry decisions. It include details such as rising cyber threats at network point to improve demand for security solutions, etc. Presenting our well structured Network Security Management Market Snapshot. The topics discussed in this slide are Driving Factors, Juniper Networks, Improve Demand. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Statistics Showcasing Network Security Management Challenges
Statistics Showcasing Network Security Management ChallengesThis slide showcases the statistics showcasing security management challenges which help an organization to find solutions for them and avoid further attacks. It include details such as communicate effectively, negotiate and compromise, etc. Introducing our Statistics Showcasing Network Security Management Challenges set of slides. The topics discussed in these slides are Communicate Effectively, Negotiate And Compromise, Learn Improve. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Infrastructure As Code Iac Infrastructure As Code Security Tracking Dashboard
Infrastructure As Code Iac Infrastructure As Code Security Tracking DashboardThis slide represents the security in Infrastructure as Code tracking dashboard. The key components include container image, misconfigured workload, risk assets, failed codes by credentials, transit, valuable public interface, etc. Deliver an outstanding presentation on the topic using this Infrastructure As Code Iac Infrastructure As Code Security Tracking Dashboard. Dispense information and present a thorough explanation of Infrastructure As Code, Security Tracking Dashboard, Misconfigured Workload, Risk Assets using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Graph Showing Cyber Security Threats In Various Industries
Graph Showing Cyber Security Threats In Various IndustriesThis slide demonstrates cybersecurity threats for deploying AUP to leverage techniques and determine safety of personal identifiable information. It includes various sectors such as financial institutions, healthcare, manufacturing, public administration, retail trade, etc. Introducing our Graph Showing Cyber Security Threats In Various Industries set of slides. The topics discussed in these slides are Business Services, Financial Institutions, Software Service This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key Approaches To Collaboration Tools Security
Key Approaches To Collaboration Tools SecurityThe purpose of this slide is to enhance security posture of their collaboration tools and better protect sensitive information from unauthorized access or breaches. Introducing our Key Approaches To Collaboration Tools Security set of slides. The topics discussed in these slides are Key Approaches, Collaboration, Tools Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Secure Your Digital Assets Application Of Different Sectors In Crypto Wallets
Secure Your Digital Assets Application Of Different Sectors In Crypto WalletsThis slide showcases business sectors, including cryptocurrency, in daily functions. This slide aims to highlight sectors such as travel, entertainment, gaming, education, trading, healthcare, banking, etc. Introducing Secure Your Digital Assets Application Of Different Sectors In Crypto Wallets to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Entertainment Industry, Businesses And Corporations, Gaming Industry, Travel Sector, using this template. Grab it now to reap its full benefits.
-
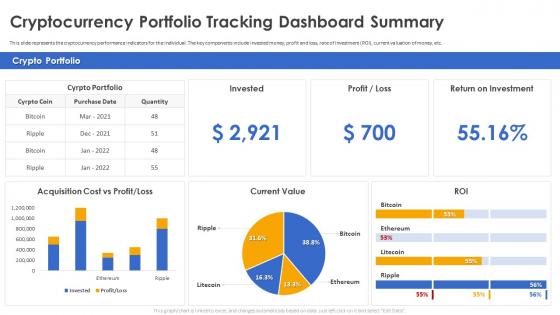 Secure Your Digital Assets Cryptocurrency Portfolio Tracking Dashboard Summary
Secure Your Digital Assets Cryptocurrency Portfolio Tracking Dashboard SummaryThis slide represents the cryptocurrency performance indicators for the individual. The key components include invested money, profit and loss, rate of investment ROI, current valuation of money, etc. Deliver an outstanding presentation on the topic using this Secure Your Digital Assets Cryptocurrency Portfolio Tracking Dashboard Summary. Dispense information and present a thorough explanation of Cryptocurrency Portfolio, Tracking Dashboard Summary, Rate Of Investment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Your Digital Assets Global Market Analysis Of Crypto Wallets
Secure Your Digital Assets Global Market Analysis Of Crypto WalletsThis slide demonstrated the market analysis of crypto wallets. The purpose of this slide is to provide a market summary of crypto wallets. The key components include US market CAGR, region-wise most used wallet, and market share. Present the topic in a bit more detail with this Secure Your Digital Assets Global Market Analysis Of Crypto Wallets. Use it as a tool for discussion and navigation on Market Analysis Of Crypto Wallets, Crypto Wallet Market Size, Market Forecast To Grow. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
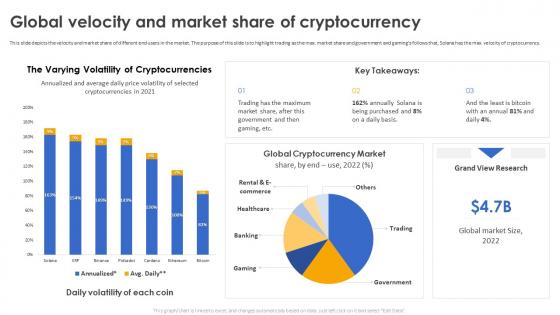 Secure Your Digital Assets Global Velocity And Market Share Of Cryptocurrency
Secure Your Digital Assets Global Velocity And Market Share Of CryptocurrencyThis slide depicts the velocity and market share of different end users in the market. The purpose of this slide is to highlight trading as the max. market share and government and gamings follows that, Solana has the max. velocity of cryptocurrency. Deliver an outstanding presentation on the topic using this Secure Your Digital Assets Global Velocity And Market Share Of Cryptocurrency. Dispense information and present a thorough explanation of Velocity And Market Share, Government And Gaming Follows, Solana Has The Max, Velocity Of Cryptocurrency using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
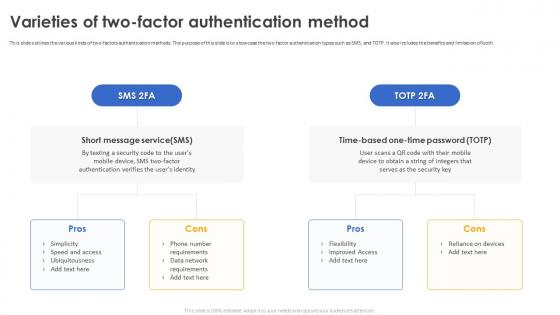 Secure Your Digital Assets Varieties Of Two Factor Authentication Method
Secure Your Digital Assets Varieties Of Two Factor Authentication MethodThis slide outlines the various kinds of two-factors authentication methods. The purpose of this slide is to showcase the two factor authentication types such as SMS, and TOTP. It also includes the benefits and limitation of both. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Varieties Of Two Factor Authentication Method. This template helps you present information on two stages. You can also present information on Phone Number Requirements, Data Network Requirements, Time Based One Time Password using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Allocation Of Funds Investor Capital Pitch Deck For Pauboxs Secure Email Platform
Allocation Of Funds Investor Capital Pitch Deck For Pauboxs Secure Email PlatformThis slide covers graphical representation of raised funds allocation for various reasons such as business expansion, team expansion and research and development. Present the topic in a bit more detail with this Allocation Of Funds Investor Capital Pitch Deck For Pauboxs Secure Email Platform Use it as a tool for discussion and navigation on Raised Funds, Allocation Of Funds This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Performance Investor Capital Pitch Deck For Pauboxs Secure Email Platform
Financial Performance Investor Capital Pitch Deck For Pauboxs Secure Email PlatformThis slide covers the graphical representation monthly recurring revenue of the company. It depicts the continues revenue growth of email security. Present the topic in a bit more detail with this Financial Performance Investor Capital Pitch Deck For Pauboxs Secure Email Platform Use it as a tool for discussion and navigation on Financial Performance, Monthly Recurring Revenue This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Projections Investor Capital Pitch Deck For Pauboxs Secure Email Platform
Financial Projections Investor Capital Pitch Deck For Pauboxs Secure Email PlatformThis slide covers a graphical representation of the forecasted financial growth of the company. It depicts that the company is expected to grow at continuous rate. Deliver an outstanding presentation on the topic using this Financial Projections Investor Capital Pitch Deck For Pauboxs Secure Email Platform Dispense information and present a thorough explanation of Annual Revenue Growth, Annual Revenue using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Smart Water Management Security And Privacy Challenges Associated With Iot Water Management IoT SS
Smart Water Management Security And Privacy Challenges Associated With Iot Water Management IoT SSThe following slide showcases various security challenges which can be faced by companies while deploying Internet of Things IoT water management system. The PPT covers information about data privacy, third-party integrations, physical security, and software update. Introducing Smart Water Management Security And Privacy Challenges Associated With Iot Water Management IoT SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Smart Water Management Key Benefits Of Using Iot In Water Management IoT SS using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Use Cases Next Generation CASB
Cloud Access Security Broker Use Cases Next Generation CASBThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Use Cases Next Generation CASB Dispense information and present a thorough explanation of Protection Against Threats, Govern Usage, Secure Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Steps To Integrate Next Generation Firewall In Network
Firewall Network Security Steps To Integrate Next Generation Firewall In NetworkThis slide highlights the various steps organizations should take while implementing Next Generation Firewall in a network. The steps include defining security requirements, determining NGFW placements, selecting an NGFW solution, planning network segmentation, and designing firewall policies. Introducing Firewall Network Security Steps To Integrate Next Generation Firewall In Network to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Define Security Requirements, Determine Ngfw Placement using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Timeline For Firewall Network Security Evolution
Firewall Network Security Timeline For Firewall Network Security EvolutionThis slide gives an overview of the firewall evolution timeline. The purpose of this slide is to showcase the different stages and enhancements in firewall security over time. It also includes the launch of firewall technology and a list of improvements in the technology from 1989 to 2019. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Timeline For Firewall Network Security Evolution This template helps you present information on Seven stages. You can also present information on Firewall Born, Mainstream Growth, Ngfw Introduction using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Working Process Of Firewall In Networking Domain
Firewall Network Security Working Process Of Firewall In Networking DomainThis slide represents how a firewall system works in a network. The purpose of this slide is to showcase the architecture, working, and different technologies used in a firewall mechanism to protect the network from malicious activities. The technologies include real-time monitoring, IP packet filtering, and so on. Deliver an outstanding presentation on the topic using this Firewall Network Security Working Process Of Firewall In Networking Domain Dispense information and present a thorough explanation of Working, Technologies Used, Firewall Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Firewall Network Security
Table Of Contents For Firewall Network SecurityIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Firewall Network Security This template helps you present information on Seven stages. You can also present information on Firewall Overview, Stateful Inspection Firewalls, Deployment Techniques using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Best Practices For Firewall Security Management
Firewall Network Security Best Practices For Firewall Security ManagementThis slide outlines the checklist for managing firewall protection effectively. The purpose of this slide is to showcase the different best practices that businesses should keep in mind while managing a firewall, including automating firewall updates, regular firewall security audits, creating and optimizing network-based firewall policies, etc. Present the topic in a bit more detail with this Firewall Network Security Best Practices For Firewall Security Management Use it as a tool for discussion and navigation on Automate Firewall Updates, Security Audits This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Checklist For Firewall Rules Configuration
Firewall Network Security Checklist For Firewall Rules ConfigurationThis slide outlines the best practices for firewall regulation configurations. The purpose of this slide is to showcase the different measures that businesses should keep in mind while performing firewall rules configuration, including planning firewall deployment, setting firewall rules, setting explicitly drop regulations, etc. Present the topic in a bit more detail with this Firewall Network Security Checklist For Firewall Rules Configuration Use it as a tool for discussion and navigation on Plan Firewall Deployment, Keep Audit Logs This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Comparison Between Network And Host Based Firewalls
Firewall Network Security Comparison Between Network And Host Based FirewallsThis slide compares network firewalls and host-based firewalls. The purpose of this slide is to highlight the critical difference between network firewalls and host-based firewalls based on deployment, traffic monitoring, traffic blocking, management, and scalability. Deliver an outstanding presentation on the topic using this Firewall Network Security Comparison Between Network And Host Based Firewalls Dispense information and present a thorough explanation of Network Firewalls, Host-Based Firewalls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Dashboard For Threat Tracking By Firewall System
Firewall Network Security Dashboard For Threat Tracking By Firewall SystemThis slide represents the dashboard for threat tracking in a firewall-protected network. The purpose of this slide is to showcase the various threats based on categories such as threats by owners, risk by threats, threat report, monthly threat status, current risk status, and threats based on user role. Present the topic in a bit more detail with this Firewall Network Security Dashboard For Threat Tracking By Firewall System Use it as a tool for discussion and navigation on Threats By Owners, Current Risk Status, Threats Based On Role This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Evolution Of Firewall Network Security Generations
Firewall Network Security Evolution Of Firewall Network Security GenerationsThis slide describes the overview of three generations of firewall network security. The purpose of this slide is to showcase the three generations of firewalls, including the first generation as connection-oriented, the second generation as content-oriented, and the third generation as intent-oriented. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Evolution Of Firewall Network Security Generations This template helps you present information on Three stages. You can also present information on TCP Handshake Verification, Hides Networks Information, Security Functionality using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Firewall Network Traffic Monitoring Dashboard
Firewall Network Security Firewall Network Traffic Monitoring DashboardPresent the topic in a bit more detail with this Firewall Network Security Firewall Configuration Challenges And Solutions Use it as a tool for discussion and navigation on Management Essential, Unauthorized Changes, Industry Data Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Firewall Protected Network Performance Tracking Dashboard
Firewall Network Security Firewall Protected Network Performance Tracking DashboardThis slide outlines the overall performance of a firewall-protected network. The purpose of this slide is to showcase the total traffic, traffic by application, URLs by actions, threats by severity, traffic by source IP, traffic by application, blocked URLs by category, threats by severity, and so on. Deliver an outstanding presentation on the topic using this Firewall Network Security Firewall Protected Network Performance Tracking Dashboard Dispense information and present a thorough explanation of Software, Features, Providers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Global Firewall Market Segmentation By Deployment And Solution
Firewall Network Security Global Firewall Market Segmentation By Deployment And SolutionThis slide provides an overview of global firewall market categorization based on deployment and solution type. The purpose of this slide is to showcase the firewall market share based on deployment types and solution type, such as software and hardware services. Deliver an outstanding presentation on the topic using this Firewall Network Security Global Firewall Market Segmentation By Deployment And Solution Dispense information and present a thorough explanation of Oragnisation Size Segment Overview, Regional Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Global Market Summary Of Firewall Network Security
Firewall Network Security Global Market Summary Of Firewall Network SecurityThis slide illustrates the worldwide market analysis for firewall network security. The purpose of this slide is to give an overview of the global firewall network security market, including CAGR rate, regional analysis, organization size segment, and key players. Present the topic in a bit more detail with this Firewall Network Security Global Market Summary Of Firewall Network Security Use it as a tool for discussion and navigation on Workflow, Working This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Challenges Associated With IoT Inventory How IoT In Inventory Management Streamlining IoT SS
Security Challenges Associated With IoT Inventory How IoT In Inventory Management Streamlining IoT SSThe following slide outlines various safety and security issues which are associated with Internet of Things IoT inventory management. It covers detailed information about data privacy, third-party integrations, physical security, and software update. Introducing Security Challenges Associated With IoT Inventory How IoT In Inventory Management Streamlining IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Privacy, Physical Security, Software Update, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Requirement Of Ethical Hackers In Different Sectors
Ethical Hacking And Network Security Requirement Of Ethical Hackers In Different SectorsThis slide depicts the requirement of ethical hackers in different sectors such as the medical, military, government sector, and corporate sectors. Present the topic in a bit more detail with this Ethical Hacking And Network Security Requirement Of Ethical Hackers In Different Sectors. Use it as a tool for discussion and navigation on Requirement Of Ethical Hackers, Military, Government Sector, Corporate Sectors. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security Skills And Certifications Required For Ethical Hacker
Ethical Hacking And Network Security Skills And Certifications Required For Ethical HackerThis slide describes the skills and certifications required for ethical hacker, such as computer networking skills, computer skills, Linux skills, and so on. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security Skills And Certifications Required For Ethical Hacker. Dispense information and present a thorough explanation of Skills And Certifications, Ethical Hacker, Computer Networking Skills, Computer Skills, Linux Skills using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ethical Hacking And Network Security White Hat Hacker Vs Black Hat Hacker
Ethical Hacking And Network Security White Hat Hacker Vs Black Hat HackerThis slide represents a comparison between white hat hackers and black hat hackers based on the factors such as legality, ownership, and motive. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security White Hat Hacker Vs Black Hat Hacker. Dispense information and present a thorough explanation of Hacker Vs Black Hat Hacker, Legality, Ownership, Tactics And Methodologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Ethical Hacking And Network Security Ppt Ideas Background Images
Table Of Contents For Ethical Hacking And Network Security Ppt Ideas Background ImagesIntroducing Table Of Contents For Ethical Hacking And Network Security Ppt Ideas Background Images to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Problems Ethical Hackers Can Solve, Ethical Hacking Training Program, Hacking And Ethical Hacking, Benefits And Limitations Of Ethical Hacking, using this template. Grab it now to reap its full benefits.
-
 Analyzing Key Security Breaches Faced By Retail Comprehensive Retail Transformation DT SS
Analyzing Key Security Breaches Faced By Retail Comprehensive Retail Transformation DT SSThis slide analyses the key vvulnerabilities that lead to cybersecurity breaches at retailers. It includes integration of new technologies, weak segregation of duties, outdated infrastructure, outdated anti malware systems leveraging AI, etc. Deliver an outstanding presentation on the topic using this Analyzing Key Security Breaches Faced By Retail Comprehensive Retail Transformation DT SS. Dispense information and present a thorough explanation of Outdated Infrastructure, Anti Malware Systems, New Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Global Market Of Secure Access Service Edge
SD WAN Model Global Market Of Secure Access Service EdgeThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work-from-anywhere culture, and so on. Present the topic in a bit more detail with this SD WAN Model Global Market Of Secure Access Service Edge. Use it as a tool for discussion and navigation on Rapid Adoption Of Cloud Native, Strong Security Framework Requirements, Cloud Computing Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Automated Saas Compliance Audit Framework For Data Security
Automated Saas Compliance Audit Framework For Data SecurityThis slide shows automated compliance audit framework for building scalable security practices in SaaS businesses. The purpose of this slide is to assist businesses in gaining competitive advantage by simplifying SaaS compliance processes. It covers components such as deadline, controls implemented, compliance status, etc. Introducing our Automated Saas Compliance Audit Framework For Data Security set of slides. The topics discussed in these slides are Automated Saas Compliance, Audit Framework For Data Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ethical Hacking And Network Security Dashboard For Ethical Hacking
Ethical Hacking And Network Security Dashboard For Ethical HackingThis slide depicts the dashboard for ethical hacking by covering the details of top priorities issues, exposure time, problems discovered, and critical threat level. Present the topic in a bit more detail with this Ethical Hacking And Network Security Dashboard For Ethical Hacking. Use it as a tool for discussion and navigation on Dashboard For Ethical Hacking, Top Priorities Issues, Exposure Time, Problems Discovered, Critical Threat Level. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security Growth Of Ethical Hacking Profession
Ethical Hacking And Network Security Growth Of Ethical Hacking ProfessionThis slide represents the growth of the ethical hacking profession, including annual salary, hiring companies, and designation such as information security officer, computer forensics engineer, ethical hacker, and network security engineer. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security Growth Of Ethical Hacking Profession. Dispense information and present a thorough explanation of Growth Of Ethical Hacking Profession, Computer Forensics Engineer, Ethical Hacker, Network Security Engineer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks
Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber AttacksThis slide represents the different types of cyber-attacks throughout the year, including the percentage of total loss caused by these attacks. Present the topic in a bit more detail with this Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks. Use it as a tool for discussion and navigation on Cyber Attacks Throughout, Online Or Web Based Attacks, Malware Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security And Privacy Challenges Associated With IoT Transforming Future Of Gaming IoT SS
Security And Privacy Challenges Associated With IoT Transforming Future Of Gaming IoT SSThe following slide showcases various security issues which are associated with Internet of Things IoT gaming. Data privacy, third-party integrations, physical security, and software update are some of the major challenges which are mentioned in slide. Introducing Security And Privacy Challenges Associated With IoT Transforming Future Of Gaming IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Privacy, Physical Security, Software Update, using this template. Grab it now to reap its full benefits.
-
 Data Breach Response Plan Security Breach Events Tracking Dashboard
Data Breach Response Plan Security Breach Events Tracking DashboardThis slide represents the dashboard to track data breach attacks. The purpose of this slide is to provide a graphical representation of cyber attacks that occurred in a specific period. It also depicts the overview of different types of attacks. Present the topic in a bit more detail with this Data Breach Response Plan Security Breach Events Tracking Dashboard. Use it as a tool for discussion and navigation on Security Breach Events, Tracking Dashboard, Track Data Breach Attacks, Inspection Of Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Challenges With Devsecops Implementation And Solutions
Devsecops Best Practices For Secure Challenges With Devsecops Implementation And SolutionsThis slide explain the various limitations with DevSecOps and its solution. The purpose of this slide is to discuss the solutions provided to different challenges associated with DevSecOps. These include late sage security integration, tool integration and complexity, security awareness and training, etc. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure Challenges With Devsecops Implementation And Solutions. Dispense information and present a thorough explanation of Security Awareness And Training, Continuous Monitoring And Compliance, Managing Security Debt using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Devsecops Best Practices For Secure Key Elements Of Successful Devsecops Implementation
Devsecops Best Practices For Secure Key Elements Of Successful Devsecops ImplementationThe slide discusses the critical elements for the successful implementation of DevSecOps. The purpose of this slide is to explain the various features that are integrated automated testing into a pipeline, automated deployment, infrastructure as code, etc. Introducing Devsecops Best Practices For Secure Key Elements Of Successful Devsecops Implementation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Infrastructure As Code, Integrate Security Testing Into Workflows, Automated Deployment, Devsecops Implementation, using this template. Grab it now to reap its full benefits.
-
 Devsecops Best Practices For Secure Key Processes Followed In Devsecops Model
Devsecops Best Practices For Secure Key Processes Followed In Devsecops ModelThis slide discusses the various processes followed in DevSecOps. The purpose of this slide is to highlight the processes, including code analysis, change management, compliance management, threat modelling and security training. Increase audience engagement and knowledge by dispensing information using Devsecops Best Practices For Secure Key Processes Followed In Devsecops Model. This template helps you present information on five stages. You can also present information on Code Analysis, Change Management, Compliance Managements, Threat Modelling using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devsecops Best Practices For Secure Training Budget Of Devsecops Process For Customers
Devsecops Best Practices For Secure Training Budget Of Devsecops Process For CustomersThis slide showcases the breakdown cost for the DevSecOps installation and management training for the customers. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor cost, training cost, etc. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Training Budget Of Devsecops Process For Customers. Use it as a tool for discussion and navigation on Training Budget, Devsecops Process For Customers, Instructor Cost, Training Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure World Wide Market Size Of Devsecops Process
Devsecops Best Practices For Secure World Wide Market Size Of Devsecops ProcessThis slide depicts the global market size of DevSecOps. The purpose of this slide is to highlight the holistic evolution of the market from 2022 to 2030 in terms of the estimated market value, projected market value, and compound annual growth rate. Present the topic in a bit more detail with this Devsecops Best Practices For Secure World Wide Market Size Of Devsecops Process. Use it as a tool for discussion and navigation on Global Market Size Devsecops, Holistic Evolution, Projected Market Value, Compound Annual Growth Rate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Content For Devsecops Best Practices For Secure Applications
Table Of Content For Devsecops Best Practices For Secure ApplicationsIntroducing Table Of Content For Devsecops Best Practices For Secure Applications to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Pipeline Security Stages, Devsecops Model Process, Continuous Process Improvement For Efficiency, Market Analysis, using this template. Grab it now to reap its full benefits.
-
 Total Cryptocurrency Stolen Securing Blockchain Transactions A Beginners Guide BCT SS V
Total Cryptocurrency Stolen Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide depicts the total amount of cryptocurrencies stolen. It includes elements such as centralized exchange, decentralized finance protocol, etc. Present the topic in a bit more detail with this Total Cryptocurrency Stolen Securing Blockchain Transactions A Beginners Guide BCT SS V. Use it as a tool for discussion and navigation on Major Instances, Errors Smart Contracts Code, Stealing Funds. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various Types Of Crypto Phishing Attacks Securing Blockchain Transactions A Beginners Guide BCT SS V
Various Types Of Crypto Phishing Attacks Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Crypto Phishing Attacks Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on three stages. You can also present information on Spear Phishing, Whaling Phishing, Clone Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
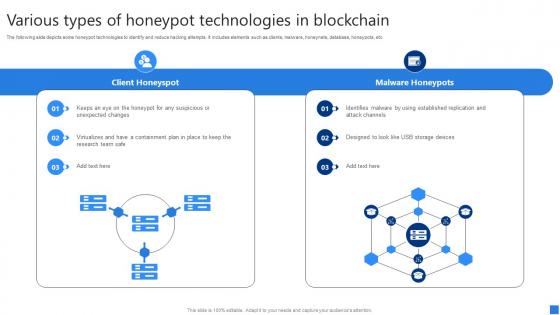 Various Types Of Honeypot Technologies Securing Blockchain Transactions A Beginners Guide BCT SS V
Various Types Of Honeypot Technologies Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc. Deliver an outstanding presentation on the topic using this Various Types Of Honeypot Technologies Securing Blockchain Transactions A Beginners Guide BCT SS V. Dispense information and present a thorough explanation of Client Honeyspot, Malware Honeypots, Honeypot Suspicious using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Year Over Year Blockchain Fraud Trends Securing Blockchain Transactions A Beginners Guide BCT SS V
Year Over Year Blockchain Fraud Trends Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc. Present the topic in a bit more detail with this Year Over Year Blockchain Fraud Trends Securing Blockchain Transactions A Beginners Guide BCT SS V. Use it as a tool for discussion and navigation on Stolen Keys, Code Exploitation, Hacked Computer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Global Market Of Secure Access Service Edge
Sase Model Global Market Of Secure Access Service EdgeThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work-from-anywhere culture, and so on. Present the topic in a bit more detail with this Sase Model Global Market Of Secure Access Service Edge. Use it as a tool for discussion and navigation on Secure Access Service Edge. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Secure Access Service Edge Performance Tracking Dashboard
Sase Model Secure Access Service Edge Performance Tracking DashboardThis slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Present the topic in a bit more detail with this Sase Model Secure Access Service Edge Performance Tracking Dashboard. Use it as a tool for discussion and navigation on Critical Network Alarms, Risky Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
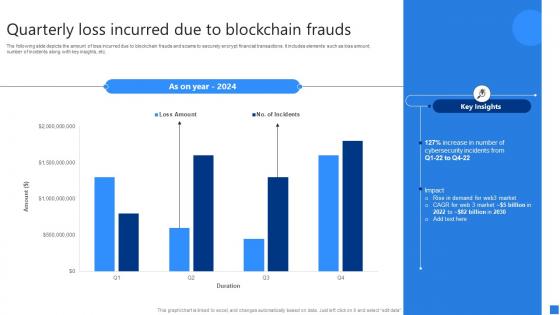 Quarterly Loss Incurred Due Securing Blockchain Transactions A Beginners Guide BCT SS V
Quarterly Loss Incurred Due Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide depicts the amount of loss incurred due to blockchain frauds and scams to securely encrypt financial transactions. It includes elements such as loss amount, number of incidents along with key insights, etc.Present the topic in a bit more detail with this Quarterly Loss Incurred Due Securing Blockchain Transactions A Beginners Guide BCT SS V. Use it as a tool for discussion and navigation on Cybersecurity Incidents, Rise Demand, Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.





