Powerpoint Templates and Google slides for Secured Data
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Authorization In Application Security For Data Privacy
Authorization In Application Security For Data PrivacyThis slide discusses the overview of authorization in application security for authorized access of resource. Increase audience engagement and knowledge by dispensing information using Authorization In Application Security For Data Privacy. This template helps you present information on five stages. You can also present information on Application Security, Data Privacy, Helps Servers Identify Clients using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Encryption Features In Application Security
Data Encryption Features In Application SecurityThis slide outlines the characteristics of encryption in application security such as security, easy-to-use, document support, etc. Introducing Data Encryption Features In Application Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implement Strict Input Validation, Employ Bot Detection Mechanisms, Application Security Deployment, using this template. Grab it now to reap its full benefits.
-
 Data Encryption Method In Application Security
Data Encryption Method In Application SecurityThis slide outlines the characteristics of encryption in application security such as security, easy-to-use, document support, etc. Increase audience engagement and knowledge by dispensing information using Data Encryption Method In Application Security. This template helps you present information on five stages. You can also present information on Encodes Plaintext To Ciphertext, Decryption Needs Specific Keys, Create Cryptographic Models using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introduction Of Application Security For Data Privacy
Introduction Of Application Security For Data PrivacyThis slide discusses the overview of application security which includes its objectives such as protecting data, minimize risk, etc. Increase audience engagement and knowledge by dispensing information using Introduction Of Application Security For Data Privacy. This template helps you present information on four stages. You can also present information on Covers Post Deployment Protection, Protects Data And Code, Application Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Additional Blockchain Data Security Tips And Best Comprehensive Approach To Privacy BCT SS
Additional Blockchain Data Security Tips And Best Comprehensive Approach To Privacy BCT SSThis slide covers essential guidance on safeguarding blockchain data to ensure integrity and confidentiality such as keeping private key confidential, utilizing VPN, use of link checker, opting for trusted crypto wallets. Introducing Additional Blockchain Data Security Tips And Best Comprehensive Approach To Privacy BCT SS to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Private Key Confidential, Security, Blockchain, Prevent Phishing Attacks, using this template. Grab it now to reap its full benefits.
-
 Data Server Security Updates Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Server Security Updates Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon represents data server preventive maintenance. It features a server with a wrench and gear symbol, indicating the importance of regular maintenance for optimal performance. Use this icon to visually communicate the need for proactive measures to prevent data server issues and ensure smooth operations.
-
 Data Server Security Updates Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Server Security Updates Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents Data server preventive maintenance. It features a simple design with a server symbol and a wrench, indicating the importance of regular maintenance to keep data servers running smoothly. Use this icon to visually communicate the need for proactive maintenance in your presentations or documents.
-
 Security Audit Procedure Icon To Verify Company Data Protection
Security Audit Procedure Icon To Verify Company Data ProtectionPresenting our set of slides with Security Audit Procedure Icon To Verify Company Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Audit Procedure, Verify Company, Data Protection.
-
 Icon For Data Loss Prevention In Information Security
Icon For Data Loss Prevention In Information SecurityPresenting our set of slides with Icon For Data Loss Prevention In Information Security. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon For Data Loss, Prevention In Information Security
-
 Ways To Overcome Cloud Data Security Challenges
Ways To Overcome Cloud Data Security ChallengesThis slide highlights solutions for cloud data security issues. The purpose of this template is assist organizations in balancing data protection and accessibility for addressing multiple problems. It includes elements such as data breaches, lack of control, etc. Introducing our premium set of slides with Ways To Overcome Cloud Data Security Challenges. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Breaches, Insufficient Cloud Provider Security, Lack Of Control. So download instantly and tailor it with your information.
-
 Data Privacy Training Icon For Securing Information
Data Privacy Training Icon For Securing InformationIntroducing our premium set of slides with Data Privacy Training Icon For Securing Information. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Privacy Training, Securing Information. So download instantly and tailor it with your information.
-
 Data Analytics And Integration Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Analytics And Integration Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentations with our vibrant PowerPoint icon on big data storage solutions. This eye-catching icon features a bold color scheme and represents the latest advancements in data storage technology. Perfect for showcasing your expertise in big data management and storage solutions.
-
 Data Analytics And Integration Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Analytics And Integration Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents the efficient and reliable storage solutions for big data. With its sleek design and bold color, it conveys the message of simplicity and effectiveness in managing large volumes of data. Perfect for presentations on data storage and management in the modern era.
-
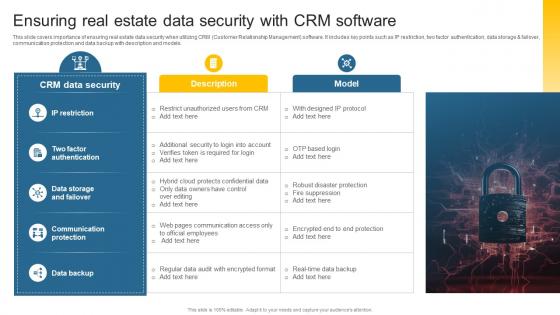 Ensuring Real Estate Data Security With CRM Leveraging Effective CRM Tool In Real Estate Company
Ensuring Real Estate Data Security With CRM Leveraging Effective CRM Tool In Real Estate CompanyThis slide covers importance of ensuring real estate data security when utilizing CRM Customer Relationship Management software. It includes key points such as IP restriction, two factor authentication, data storage and failover, communication protection and data backup with description and models. Introducing Ensuring Real Estate Data Security With CRM Leveraging Effective CRM Tool In Real Estate Company to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Data Storage And Failover, Communication Protection, Data Backup, using this template. Grab it now to reap its full benefits.
-
 SaaS Security Icon For Protecting Confidential Data
SaaS Security Icon For Protecting Confidential DataPresenting our set of slides with SaaS Security Icon For Protecting Confidential Data. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on SaaS Security, Protecting Confidential Data.
-
 Applications For Big Data Analytics In Cyber Security
Applications For Big Data Analytics In Cyber SecurityThis slide represents big data analytics in cybersecurity applications. This includes algorithms for anomalies, boost security intelligence, detect potential frauds, statistical parameter calculations. Presenting our set of slides with name Applications For Big Data Analytics In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Detect Potential Frauds, Algorithms For Anomalies, Statistical Parameter Calculation .
-
 Big Data Analytics Technologies In Cyber Security
Big Data Analytics Technologies In Cyber SecurityThis slide showcases cyber security technologies in big data analytics. This includes encryptions, user access control and centralizsed key management systems. Presenting our set of slides with name Big Data Analytics Technologies In Cyber Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Big Data Analytics, Centralized Key Management, Technologies In Cyber Security.
-
 Different Types Of Visualization Security For Protecting Data
Different Types Of Visualization Security For Protecting DataThis slides showcases various types of visualization data. The main purpose of this template is to showcase data encryption for shared data. This includes role based access control, encrypted file sharing, regular security audits, etc. Introducing our premium set of slides with Different Types Of Visualization Security For Protecting Data. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Methods, Regular Security Audits, Encrypted File Sharing. So download instantly and tailor it with your information.
-
 Role Of Visualization Security For Understanding Complex Data
Role Of Visualization Security For Understanding Complex DataThis slides showcase ways of simplifying data through visualization security. The main purpose of this template is to showcase ways in which data can be protected and gain insights from customers. This includes simplifying complex data, identification trends, real time monitoring, etc. Presenting our set of slides with Role Of Visualization Security For Understanding Complex Data. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Simplifying Complex, Identification Trends, Driving Innovation.
-
 Visualization Security Icon For Data Protection
Visualization Security Icon For Data ProtectionPresenting our set of slides with Visualization Security Icon For Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Visualization Security, Data Protection.
-
 Different Modes Of IP Security For Securing Data
Different Modes Of IP Security For Securing DataThis slide showcases various modes of IP security. The main purpose of this template is to secure communication between two endpoints. This includes Point-to-point security, tunnel mode, remote access, etc. Introducing our Different Modes Of IP Security For Securing Data set of slides. The topics discussed in these slides are IP Security, Secure Communication, Point To Point Security, Tunnel Mode. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 IP Security Model For Integrating Data
IP Security Model For Integrating DataThis slide showcase process of IP security. This includes data source, applications, devices, clients, activities, sensors, digital assets, integration of data, streaming data, data warehousing, storage pf object, etc. Introducing our IP Security Model For Integrating Data set of slides. The topics discussed in these slides are Data Warehouse Autonomous, Streaming Data, Services Of Big Data, Integration Of Data. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Major Components Of IP Security To Protect Sensitive Data
Major Components Of IP Security To Protect Sensitive DataThis slide showcases key elements of IP security for protecting data. The main purpose of this template is to showcase protection and trustworthiness of data. This includes encapsulating security payload, authentication header, and internet key exchange. Presenting our set of slides with name Major Components Of IP Security To Protect Sensitive Data. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Internet Key Exchange, Authentication Header, Encapsulating Security Payload.
-
 Comparison Analysis Of Data Masking Tools For Information Security
Comparison Analysis Of Data Masking Tools For Information SecurityThis slide represents comparison analysis of data masking tools that assist companies to enhance their sensitive information security. It includes various tools such as K2View data masking, DATPROF data masking tool, Oracle data masking and subsetting, etc. Presenting our well structured Comparison Analysis Of Data Masking Tools For Information Security. The topics discussed in this slide are Virtualization, Synthetic Data Generation, Tokenization. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Data Mapping Icon For Securing Online Customer Information
Data Mapping Icon For Securing Online Customer InformationPresenting our set of slides with Data Mapping Icon For Securing Online Customer Information. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Mapping Icon, Securing Online Customer Information.
-
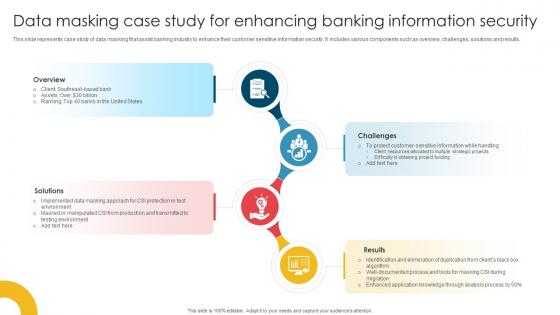 Data Masking Case Study For Enhancing Banking Information Security
Data Masking Case Study For Enhancing Banking Information SecurityThis slide represents case study of data masking that assist banking industry to enhance their customer sensitive information security. It includes various components such as overview, challenges, solutions and results. Introducing our premium set of slides with Data Masking Case Study For Enhancing Banking Information Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Overview, Solutions, Challenges.So download instantly and tailor it with your information.
-
 Data Masking Icon To Enhance Information Security
Data Masking Icon To Enhance Information SecurityPresenting our set of slides with Data Masking Icon To Enhance Information Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Masking Icon, Enhance Information Security.
-
 Data Encryption And Authentication In Automotive Cyber Security
Data Encryption And Authentication In Automotive Cyber SecurityThis slide highlights data privacy and encryption in automotive cybersecurity. The purpose of this slide is to aid organizations in implementing measures for securing sensitive data from possible manipulation. It includes various measures for authentication and data encryption. Presenting our set of slides with Data Encryption And Authentication In Automotive Cyber Security This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication, Data Encryption, Authenticity Of Software
-
 Agenda For Tokenization For Improved Data Security
Agenda For Tokenization For Improved Data SecurityIntroducing Agenda For Tokenization For Improved Data Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Tokenization Training Program, Budget Allocation And Roadmap, Governance, Security, using this template. Grab it now to reap its full benefits.
-
 Comparative Analysis Of Security And Utility Token Tokenization For Improved Data Security
Comparative Analysis Of Security And Utility Token Tokenization For Improved Data SecurityThis slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc. Present the topic in a bit more detail with this Comparative Analysis Of Security And Utility Token Tokenization For Improved Data Security. Use it as a tool for discussion and navigation on Comparative Analysis, Security And Utility Token, Expectations, Scam Potential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide For Tokenization For Improved Data Security
Icons Slide For Tokenization For Improved Data SecurityIntroducing our well researched set of slides titled Icons Slide For Tokenization For Improved Data Security. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents Of Tokenization For Improved Data Security
Table Of Contents Of Tokenization For Improved Data SecurityIncrease audience engagement and knowledge by dispensing information using Table Of Contents Of Tokenization For Improved Data Security. This template helps you present information on twelve stages. You can also present information on Data Security, Tokenization Market And Trends, Comparative Analysis, Training And Budget using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security 30 60 90 Days Plan To Implement Tokenization
Tokenization For Improved Data Security 30 60 90 Days Plan To Implement TokenizationThis slide depicts the 30 60 90 days plan for implementing tokenization. The plan includes the activities and goals such as assessment, planning, selecting tokenization solutions, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security 30 60 90 Days Plan To Implement Tokenization. Dispense information and present a thorough explanation of Assessment And Planning, Select Tokenization Solution, Test Tokenization Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security About Non Fungible Tokenization In Crypto Currency
Tokenization For Improved Data Security About Non Fungible Tokenization In Crypto CurrencyThis slide highlights the concept of non-fungible tokenization. The purpose of this slide is to showcase the characteristics of non-fungible tokenization which include risking crypto trend, digital ownership, etc. Introducing Tokenization For Improved Data Security About Non Fungible Tokenization In Crypto Currency to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Rising Crypto Trend, Exclusive Digital Ownership, Diverse Assets, Safeguarding Digital Creations, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Basic Tokenization Service For Cloud Based Operations
Tokenization For Improved Data Security Basic Tokenization Service For Cloud Based OperationsThis slide represents the fundamental tokenization service designed for cloud-based solutions. The purpose of this slide is to showcase the basic tokenization service for cloud-based services. Present the topic in a bit more detail with this Tokenization For Improved Data Security Basic Tokenization Service For Cloud Based Operations. Use it as a tool for discussion and navigation on Sensitive Or Personal Information Sources, Tokenization Database, Tokenization Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Before Vs After Implementing Tokenization In Data Security
Tokenization For Improved Data Security Before Vs After Implementing Tokenization In Data SecurityThis slide showcases the comparative analysis of the before versus after tokenization. The purpose of this slide is to showcase the different performance metrics and how tokenization has improved these metrics. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Before Vs After Implementing Tokenization In Data Security. Dispense information and present a thorough explanation of Compliance With Regulations, Reduced Insider Threats, Exposure Of Sensitive Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Best Practices For Tokenization In Data Security
Tokenization For Improved Data Security Best Practices For Tokenization In Data SecurityThe purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Best Practices For Tokenization In Data Security. This template helps you present information on four stages. You can also present information on Effective Cybersecurity And Compliance, Broaden Data Tokenization Scope, Regularly Revise Tokenization Policies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In Business
Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In BusinessThis slide showcases the breakdown cost for conducting tokenization for data security. The purpose of this slide is to showcase the technology cost breakdown for different components such as test infrastructure, staff training, etc. Present the topic in a bit more detail with this Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In Business. Use it as a tool for discussion and navigation on Tokenization Solution, Integration And Customization, Infrastructure And Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Challenges And Related Solutions In Utility Tokens
Tokenization For Improved Data Security Challenges And Related Solutions In Utility TokensThis slide outlines the issues faced by utility tokens in data security. The purpose of this slide is to showcase utility token challenges which include absence of inherent mechanism, inadequate promotion, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Challenges And Related Solutions In Utility Tokens. Dispense information and present a thorough explanation of Regularly Remove From Circulation, Inadequate Promotion, Cryptocurrency Adoption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Characteristics Of Utility Tokenization In Data Security
Tokenization For Improved Data Security Characteristics Of Utility Tokenization In Data SecurityThis slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Characteristics Of Utility Tokenization In Data Security. This template helps you present information on seven stages. You can also present information on Utility Tokenization, Data Security, Platforms Economic Activity, Blockchain Powered Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Checklist To Conduct Tokenization In Data Security
Tokenization For Improved Data Security Checklist To Conduct Tokenization In Data SecurityThis slide showcases the checklist for performing tokenization. The purpose of this slide is to highlight the actions performed while conducting regression testing, person responsible, status and comments for the same. Present the topic in a bit more detail with this Tokenization For Improved Data Security Checklist To Conduct Tokenization In Data Security. Use it as a tool for discussion and navigation on Data Classification, Tokenization Algorithm Selection, Key Management, Access Control. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Common Use Cases Of Tokenization In Data Security
Tokenization For Improved Data Security Common Use Cases Of Tokenization In Data SecurityThis slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc. Introducing Tokenization For Improved Data Security Common Use Cases Of Tokenization In Data Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Restricting Access To Sensitive Data, Reducing Compliance Scope, Tokenization In Data Security, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Comparative Analysis Of Encryption And Tokenization In Ds
Tokenization For Improved Data Security Comparative Analysis Of Encryption And Tokenization In DsThis slide represents the comparison of encryption and tokenization. The purpose of this slide is to highlight different components of comparison such as definition, importance, objective, and so on. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Comparative Analysis Of Encryption And Tokenization In Ds. Dispense information and present a thorough explanation of Comparative Analysis, Encryption And Tokenization, Safeguards Private Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Critical Challenges Of Tokenization Implementation In Ds
Tokenization For Improved Data Security Critical Challenges Of Tokenization Implementation In DsThis slide highlights the disadvantages of carrying out tokenization. The purpose of this slide is to showcase the drawbacks and its implications which include increased IT complexity, limited adoption, etc. Present the topic in a bit more detail with this Tokenization For Improved Data Security Critical Challenges Of Tokenization Implementation In Ds. Use it as a tool for discussion and navigation on Critical Challenges, Tokenization Implementation, Alters Transaction Process, Compatibility Concerns. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Data Security Benefits Of Adopting Tokenization
Tokenization For Improved Data Security Data Security Benefits Of Adopting TokenizationThis slide discusses the cons of tokenization. The purpose of this slide is to showcase the advantages of tokenization such as utilizing less resources, decreases risk, stimulates innovation, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Data Security Benefits Of Adopting Tokenization. Dispense information and present a thorough explanation of Builds Customer Trust, Data Security Benefits, Adopting Tokenization, Fostering Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Data Tokenization Tools Key Capabilities
Tokenization For Improved Data Security Data Tokenization Tools Key CapabilitiesPresent the topic in a bit more detail with this Tokenization For Improved Data Security Data Tokenization Tools Key Capabilities. Use it as a tool for discussion and navigation on Data Tokenization Tools, Key Capabilities, Operational And Analytical Purposes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Difference Between Tokenization And Masking Technology
Tokenization For Improved Data Security Difference Between Tokenization And Masking TechnologyThis slide represents the comparison between tokenization and masking. The purpose of this slide is to represent a comparative analysis on the basis of various components such as process, purpose, use cases, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Difference Between Tokenization And Masking Technology. Dispense information and present a thorough explanation of Data Preservation, Masking Technology, Maintains Data Format using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Different Phases Of Implementing Tokenization In Ds
Tokenization For Improved Data Security Different Phases Of Implementing Tokenization In DsThis slide highlights the steps for working of tokenization. The purpose of this slide is to outline the various ways of creating token and the phases which include initiating card transaction, producing tokens, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Different Phases Of Implementing Tokenization In Ds. This template helps you present information on six stages. You can also present information on Mathematically Reversible, Cryptographic Function, Producing Tokens using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Evolution Of Tokenization From Ancient Times To Modern Era
Tokenization For Improved Data Security Evolution Of Tokenization From Ancient Times To Modern EraThis slide outlines the history of tokenization. The purpose of this slide is to showcase the years of evolution such as 1970s digital tokenization, data compliance in 2001, etc. Present the topic in a bit more detail with this Tokenization For Improved Data Security Evolution Of Tokenization From Ancient Times To Modern Era. Use it as a tool for discussion and navigation on Evolution Of Tokenization, Tokenization Recently Secured, Payment Card Data Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Factors To Consider While Choosing Tokenization Over Encryption
Tokenization For Improved Data Security Factors To Consider While Choosing Tokenization Over EncryptionThis slide showcases the aspects to consider while choosing tokenization over encryption. The purpose of this slide is to outline the aspects such as reduction of compliance scope, format attributes, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Factors To Consider While Choosing Tokenization Over Encryption. Dispense information and present a thorough explanation of Elimination Of Encryption Key Management, Format Attributes, Reduction Of Compliance Scope using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security For Table Of Contents
Tokenization For Improved Data Security For Table Of ContentsPresent the topic in a bit more detail with this Tokenization For Improved Data Security For Table Of Contents. Use it as a tool for discussion and navigation on Overview And Process, Areas Of Application, Reasons For Conducting. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Future Trends Of Tokenization On Business And Technology
Tokenization For Improved Data Security Future Trends Of Tokenization On Business And TechnologyThis slide highlights the anticipated developments in tokenizations impact on the realms of business and technology. The purpose of this slide is to outline the future trends of tokenization. Introducing Tokenization For Improved Data Security Future Trends Of Tokenization On Business And Technology to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Anticipated Developments, Business And Technology, Future Trends Of Tokenization, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems
Tokenization For Improved Data Security Governance And Risk Management In Cloud Based SystemsThis slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems. Dispense information and present a thorough explanation of Governance And Risk Management, Cloud Based Systems, During Categorization Organization Must using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Impact Of Tokenization On Different Industries
Tokenization For Improved Data Security Impact Of Tokenization On Different IndustriesThis slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Impact Of Tokenization On Different Industries. This template helps you present information on six stages. You can also present information on Tokenization, Data Security, Rapid Defect Detection, Ensuring Trust And Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Introduction Of Utility Token In Data Security
Tokenization For Improved Data Security Introduction Of Utility Token In Data SecurityThis slide showcases the overview of utility tokens in data security. The purpose of this slide is to discuss the introduction of utility tokens required for data security and preventing thefts. Introducing Tokenization For Improved Data Security Introduction Of Utility Token In Data Security to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Data Security, Utility Tokens, Preventing Thefts, Unique To Each Platform, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Key Applications And Use Cases Of Tokenization
Tokenization For Improved Data Security Key Applications And Use Cases Of TokenizationThis slide discusses various application fields of tokenization. The purpose of this slide is to highlight the areas of application which include mobile wallet services, online retail platforms, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Key Applications And Use Cases Of Tokenization. This template helps you present information on three stages. You can also present information on Mobile Wallet Services, Online Retail Platforms, Businesses Storing Customer, Card Data Securely using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Main Data Security Tokenization Techniques
Tokenization For Improved Data Security Main Data Security Tokenization TechniquesThis slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc. Introducing Tokenization For Improved Data Security Main Data Security Tokenization Techniques to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Transactional, Governance Tokenization, Utility Tokenization, Platform Tokenization, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Optimal Practices For Incorporating Tokenization Into Cloud
Tokenization For Improved Data Security Optimal Practices For Incorporating Tokenization Into CloudThis slide discusses the utilization of tokenization in the context of cloud-based services. The purpose of this slide is to discuss the overview of implementing tokenization for cloud based services. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Optimal Practices For Incorporating Tokenization Into Cloud. This template helps you present information on six stages. You can also present information on Incorporating Tokenization, Cloud Based Services, Protect Sensitive Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Overview And Benefits Of Encryption For Data Security
Tokenization For Improved Data Security Overview And Benefits Of Encryption For Data SecurityThis slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc. Present the topic in a bit more detail with this Tokenization For Improved Data Security Overview And Benefits Of Encryption For Data Security. Use it as a tool for discussion and navigation on Employing Mathematical Algorithms, Transform Sensitive Data, Unstructured Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Overview And Process Of Tokenization In Data Security
Tokenization For Improved Data Security Overview And Process Of Tokenization In Data SecurityThis slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc. Introducing Tokenization For Improved Data Security Overview And Process Of Tokenization In Data Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Tokenization In Data Security, While Ensuring Security, Small And Midsize Enterprises, using this template. Grab it now to reap its full benefits.





