Powerpoint Templates and Google slides for Secured Data
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Information System Security And Risk Administration Plandashboard For Data Security Risk Management
Information System Security And Risk Administration Plandashboard For Data Security Risk ManagementThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Present the topic in a bit more detail with this Information System Security And Risk Administration Plandashboard For Data Security Risk Management. Use it as a tool for discussion and navigation on Enterprise Risk, Risks By Objectives, Data Protection Findings. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams
Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt DiagramsThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Deliver an outstanding presentation on the topic using this Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams. Dispense information and present a thorough explanation of Data Breaches, Consequences, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
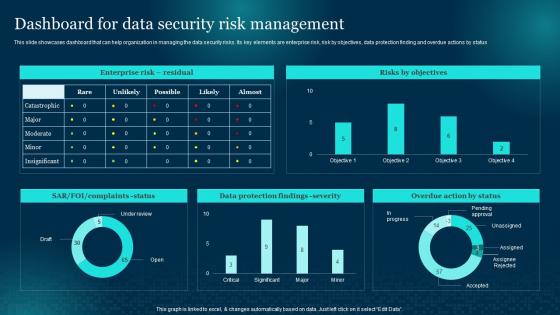 Dashboard For Data Security Risk Management Cybersecurity Risk Analysis And Management Plan
Dashboard For Data Security Risk Management Cybersecurity Risk Analysis And Management PlanThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status Present the topic in a bit more detail with this Dashboard For Data Security Risk Management Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Dashboard, Security, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard For Data Security Risk Management Formulating Cybersecurity Plan
Dashboard For Data Security Risk Management Formulating Cybersecurity PlanThis slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Present the topic in a bit more detail with this Dashboard For Data Security Risk Management Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Data Protection, Dashboard, Data Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber Security
Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Deliver an outstanding presentation on the topic using this Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Current State, Email, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber Security
Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present the topic in a bit more detail with this Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Online Criminals, Foreign Government Officials, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Statistics Showing The Impact Of Security Awarenesspreventing Data Breaches Through Cyber Security
Key Statistics Showing The Impact Of Security Awarenesspreventing Data Breaches Through Cyber SecurityPresent the topic in a bit more detail with this Key Statistics Showing The Impact Of Security Awarenesspreventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Employees, Security, Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Kpi Dashboard To Monitor Cyber Security Performance Preventing Data Breaches Through Cyber Security
Kpi Dashboard To Monitor Cyber Security Performance Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. Deliver an outstanding presentation on the topic using this Kpi Dashboard To Monitor Cyber Security Performance Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Control Review Status, Management, Cyber Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security
Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Risk By Threats, Threat Report, Current Risk Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Measuring The Impact Of Security Awareness Training Preventing Data Breaches Through Cyber Security
Measuring The Impact Of Security Awareness Training Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. Present the topic in a bit more detail with this Measuring The Impact Of Security Awareness Training Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Security Awareness, Social Engineering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Common Cyber Attack Faced By Our Employees Preventing Data Breaches Through Cyber Security
Most Common Cyber Attack Faced By Our Employees Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Introducing Most Common Cyber Attack Faced By Our Employees Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Ransomware, Password Attack, Cryptojacking, using this template. Grab it now to reap its full benefits.
-
 Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber Security
Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Present the topic in a bit more detail with this Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Finished Training, Awareness Factors, Training Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Practices To Improve Security Awareness Level Amongst The Preventing Data Breaches Through Cyber Security
Practices To Improve Security Awareness Level Amongst The Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Increase audience engagement and knowledge by dispensing information using Practices To Improve Security Awareness Level Amongst The Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Get Management Involved, Develop Robust Policies, Set Guidelines using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Awareness Training Program Challenges Preventing Data Breaches Through Cyber Security
Security Awareness Training Program Challenges Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Increase audience engagement and knowledge by dispensing information using Security Awareness Training Program Challenges Preventing Data Breaches Through Cyber Security. This template helps you present information on five stages. You can also present information on Outdated Content, Employees Lose Interest, Burden On Administrators using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security
Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Limit Public Information, Verify The Source, No Sharing Of Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Preventing Data Breaches Through Cyber Security Awareness
Table Of Contents For Preventing Data Breaches Through Cyber Security AwarenessDeliver an outstanding presentation on the topic using this Table Of Contents For Preventing Data Breaches Through Cyber Security Awareness. Dispense information and present a thorough explanation of Cyber Security Awareness, Online Courses, Automation Tools using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 How To Overcome The Security Awareness Training Program Preventing Data Breaches Through Cyber Security
How To Overcome The Security Awareness Training Program Preventing Data Breaches Through Cyber SecurityThe purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program. Deliver an outstanding presentation on the topic using this How To Overcome The Security Awareness Training Program Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Outdated Content, Burden On Administrators, Low Employee Participation Rate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Consequences Of Data Breaches Faced By Organization Development And Implementation Of Security
Consequences Of Data Breaches Faced By Organization Development And Implementation Of SecurityThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Deliver an outstanding presentation on the topic using this Consequences Of Data Breaches Faced By Organization Development And Implementation Of Security. Dispense information and present a thorough explanation of Payment Card Fraud, Physical Loss, Insider Leak using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By Organization
Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By OrganizationThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By Organization. Use it as a tool for discussion and navigation on Consequences, Data Breaches, Unintended Disclosure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
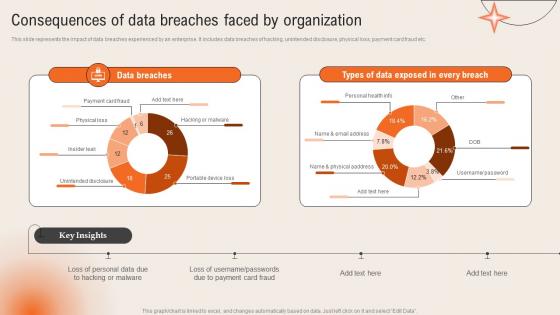 Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident Management
Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident ManagementThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc.Present the topic in a bit more detail with this Consequences Of Data Breaches Faced By Organization Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Unintended Disclosure, Portable Device, Hacking Malware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Process To Manage Firms Sensitive Data Defense Plan To Protect Firm Assets
Information Security Process To Manage Firms Sensitive Data Defense Plan To Protect Firm AssetsThis slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Present the topic in a bit more detail with this Information Security Process To Manage Firms Sensitive Data Defense Plan To Protect Firm Assets. Use it as a tool for discussion and navigation on Privileged Password Management, Network Administrator. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Top Vulnerable Industries To Cyber Security Threats And Data Breaches
Top Vulnerable Industries To Cyber Security Threats And Data BreachesThis slide provides useful insights about most vulnerable industries to cyber security attacks and data breaches. The major industries are government, banking, communications, healthcare, e commerce, shipping and logistics and cryptocurrency Introducing our Top Vulnerable Industries To Cyber Security Threats And Data Breaches set of slides. The topics discussed in these slides are Government, Department. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Breach Trend Generating Security Awareness Among Employees To Reduce
Data Breach Trend Generating Security Awareness Among Employees To ReduceThe following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. Deliver an outstanding presentation on the topic using this Data Breach Trend Generating Security Awareness Among Employees To Reduce Dispense information and present a thorough explanation of Data Breach Trend, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Business Data Security And Privacy Assessment Survey Form Survey SS
Business Data Security And Privacy Assessment Survey Form Survey SSFollowing slides illustrates business data security survey form which can be used by data analyst to identify best data security tools. It includes key elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Introducing our Business Data Security And Privacy Assessment Survey Form Survey SS set of slides. The topics discussed in these slides are Security Tools Used, Allocated For Tools, Security Software Solutions. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Benchmark Comparison Analysis For Data Security Software
Benchmark Comparison Analysis For Data Security SoftwareThis slide shows comparison analysis of different data security software in order to choose the most suitable one. It include benchmarks like data privacy, data integrity and authentication etc. Introducing our Benchmark Comparison Analysis For Data Security Software set of slides. The topics discussed in these slides are Research And Development, Marketing, Human Resources. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data security management ppt powerpoint presentation layouts slideshow cpb
Data security management ppt powerpoint presentation layouts slideshow cpbPresenting this set of slides with name - Data Security Management Ppt Powerpoint Presentation Layouts Slideshow Cpb. This is an editable three stages graphic that deals with topics like Data Security Management to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Data security management ppt powerpoint presentation infographics icon cpb
Data security management ppt powerpoint presentation infographics icon cpbPresenting this set of slides with name - Data Security Management Ppt Powerpoint Presentation Infographics Icon Cpb. This is an editable five stages graphic that deals with topics like Data Security Management to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Enabling data security risk management action plan key initiatives for project safety it
Enabling data security risk management action plan key initiatives for project safety itThis slide provide details about data security risk management action plan which will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an outstanding presentation on the topic using this NAMEEEE. Dispense information and present a thorough explanation of Required Resources, Risk, Communication, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information security process to manage firms sensitive data key initiatives for project safety it
Information security process to manage firms sensitive data key initiatives for project safety itThis slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an outstanding presentation on the topic using this Information Security Process To Manage Firms Sensitive Data Key Initiatives For Project Safety It. Dispense information and present a thorough explanation of Management, Network, Security, Performed using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
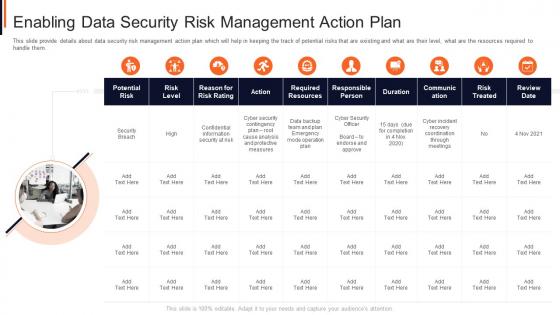 Enabling data security risk management action plan project safety management it
Enabling data security risk management action plan project safety management itThis slide provide details about data security risk management action plan which will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Introducing Enabling Data Security Risk Management Action Plan Project Safety Management It to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Analysis, Measures, Plan, Security, Risk, using this template. Grab it now to reap its full benefits.
-
 Information security process to manage firms sensitive data project safety management it
Information security process to manage firms sensitive data project safety management itThis slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an outstanding presentation on the topic using this Information Security Process To Manage Firms Sensitive Data Project Safety Management It. Dispense information and present a thorough explanation of Management, Network, Systems, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Wireless security icon of cloud servers to secure data
Wireless security icon of cloud servers to secure dataPresenting our set of slides with Wireless Security Icon Of Cloud Servers To Secure Data. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Wireless Security Icon Of Cloud Servers To Secure Data.
-
 Ways to set up an advanced cybersecurity monitoring plan ways through which security data
Ways to set up an advanced cybersecurity monitoring plan ways through which security dataThis slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Present the topic in a bit more detail with this Ways To Set Up An Advanced Cybersecurity Monitoring Plan Ways Through Which Security Data. Use it as a tool for discussion and navigation on Attack Description, Ways To Mitigate Attack, External Attacks, Insider Attacks, Supply Chain Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data flow home security system ppt powerpoint presentation infographic cpb
Data flow home security system ppt powerpoint presentation infographic cpbPresenting Data Flow Home Security System Ppt Powerpoint Presentation Infographic Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Data Flow Home Security System. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Electronic information security prepare data backup sensitive information
Electronic information security prepare data backup sensitive informationThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Introducing Electronic Information Security Prepare Data Backup Sensitive Information to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Data Backup, Natural Disasters, Provide Cloud Services, Data Backups Offline, using this template. Grab it now to reap its full benefits.
-
 Types database security mechanisms ppt powerpoint presentation diagram lists cpb
Types database security mechanisms ppt powerpoint presentation diagram lists cpbPresenting our Types Database Security Mechanisms Ppt Powerpoint Presentation Diagram Lists Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Types Database Security Mechanisms. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Secure offsite data storage ppt powerpoint presentation outline demonstration cpb
Secure offsite data storage ppt powerpoint presentation outline demonstration cpbPresenting Secure Offsite Data Storage Ppt Powerpoint Presentation Outline Demonstration Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Offsite Data Storage. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Secure exchange electronic data ppt powerpoint presentation ideas gridlines cpb
Secure exchange electronic data ppt powerpoint presentation ideas gridlines cpbPresenting our Secure Exchange Electronic Data Ppt Powerpoint Presentation Ideas Gridlines Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Secure Exchange Electronic Data. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Payroll system security data protection ppt powerpoint presentation infographic template cpb
Payroll system security data protection ppt powerpoint presentation infographic template cpbPresenting our Payroll System Security Data Protection Ppt Powerpoint Presentation Infographic Template Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Payroll System Security Data Protection. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Availability database security ppt powerpoint presentation model vector cpb
Availability database security ppt powerpoint presentation model vector cpbPresenting Availability Database Security Ppt Powerpoint Presentation Model Vector Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Availability Database Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Database recovery security techniques ppt powerpoint presentation infographic template slides cpb
Database recovery security techniques ppt powerpoint presentation infographic template slides cpbPresenting our Database Recovery Security Techniques Ppt Powerpoint Presentation Infographic Template Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Database Recovery Security Techniques This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Implementing advanced analytics system at workplace enabling data security risk management action plan
Implementing advanced analytics system at workplace enabling data security risk management action planThe data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an outstanding presentation on the topic using this Implementing Advanced Analytics System At Workplace Enabling Data Security Risk Management Action Plan. Dispense information and present a thorough explanation of Management, Resources, Enabling using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 3 layer secure database server icon
3 layer secure database server iconPresenting our set of slides with 3 Layer Secure Database Server Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on 3 Layer Secure Database Server Icon.
-
 6 step process to implement data availability security
6 step process to implement data availability securityThis slide represents 6 step process to implement data availability security illustrating simplified recording, on-site maintenance and online security, training, record disposal and plan. Presenting our set of slides with 6 Step Process To Implement Data Availability Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Management, Implement, Organization.
-
 Cia triad of information security in data availability
Cia triad of information security in data availabilityThis slide represents CIA triad of information security in data availability such as confidentiality, integrity and availability for securing data from breach and thefts in an organization. Presenting our set of slides with Cia Triad Of Information Security In Data Availability. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Confidentiality, Integrity, Availability.
-
 Icon showcasing data availability security against risks and threats
Icon showcasing data availability security against risks and threatsPresenting our set of slides with Icon Showcasing Data Availability Security Against Risks And Threats. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon Showcasing Data Availability Security Against Risks And Threats.
-
 Addressing internal and external sources of threat data corporate security management
Addressing internal and external sources of threat data corporate security managementThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Introducing Addressing Internal And External Sources Of Threat Data Corporate Security Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Targeted Intelligence, Malware Intelligence, Reputation Intelligence, using this template. Grab it now to reap its full benefits.
-
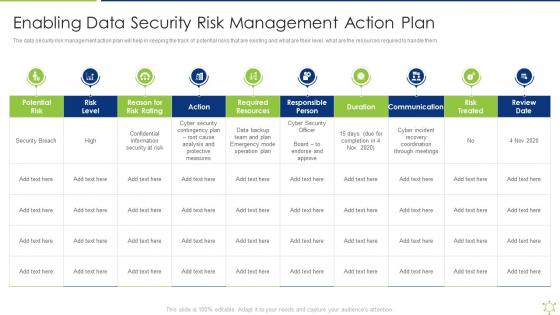 Enabling Data Security Risk Management Action Plan Enabling It Intelligence Framework
Enabling Data Security Risk Management Action Plan Enabling It Intelligence FrameworkThe data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them.Present the topic in a bit more detail with this Enabling Data Security Risk Management Action Plan Enabling It Intelligence Framework Use it as a tool for discussion and navigation on Required Resources, Responsible Person, Communication This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Program Icon For Protecting Client Data
Security Program Icon For Protecting Client DataPresenting our set of slides with name Security Program Icon For Protecting Client Data. This exhibits information on one stage of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Program Icon For Protecting Client Data.
-
 Stages Involved In Data Security Management Program
Stages Involved In Data Security Management ProgramThis slide shows the stages involved in data security management program which also includes initiatives and activities such as develop data security team, analyze requirements, monitor policies periodically. Introducing our Stages Involved In Data Security Management Program set of slides. The topics discussed in these slides are Develop Data Security, Communicate, Communication Method. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Secure data storage cloud computings ppt powerpoint presentation example cpb
Secure data storage cloud computings ppt powerpoint presentation example cpbPresenting Secure Data Storage Cloud Computings Ppt Powerpoint Presentation Example Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Data Storage Cloud Computings. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Data security small businesses ppt powerpoint presentation pictures sample cpb
Data security small businesses ppt powerpoint presentation pictures sample cpbPresenting our Data Security Small Businesses Ppt Powerpoint Presentation Pictures Sample Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Data Security Small Businesses This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Agenda for advanced security monitoring plan to remove cybersecurity threat and data infraction
Agenda for advanced security monitoring plan to remove cybersecurity threat and data infractionIncrease audience engagement and knowledge by dispensing information using Agenda For Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. This template helps you present information on seven stages. You can also present information on Agenda using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons slide for advanced security monitoring plan to remove cybersecurity threat and data infraction
Icons slide for advanced security monitoring plan to remove cybersecurity threat and data infractionIntroducing our well researched set of slides titled Icons Slide For Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table of contents advanced security monitoring plan to remove cybersecurity threat and data infraction
Table of contents advanced security monitoring plan to remove cybersecurity threat and data infractionPresent the topic in a bit more detail with this Table Of Contents Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. Use it as a tool for discussion and navigation on Cybersecurity Monitoring Tools To Be Implemented, Essential Elements Of Security Monitoring Plan, Cybersecurity Monitoring Best Practices To Be Followed By The Company. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ways through which security data can be compromised and measures to deal with them
Ways through which security data can be compromised and measures to deal with themThis slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Present the topic in a bit more detail with this Ways Through Which Security Data Can Be Compromised And Measures To Deal With Them. Use it as a tool for discussion and navigation on Supply Chain Attacks, Insider Attacks, External Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Data Backup For Sensitive Information
Information Security Data Backup For Sensitive InformationThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Increase audience engagement and knowledge by dispensing information using Information Security Data Backup For Sensitive Information. This template helps you present information on three stages. You can also present information on Protect, Information, Manipulation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Dispose Data And Equipment Properly
Information Security Dispose Data And Equipment ProperlyThis slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Increase audience engagement and knowledge by dispensing information using Information Security Dispose Data And Equipment Properly. This template helps you present information on three stages. You can also present information on Dispose Data And Equipment Properly using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Content Delivery Network It Data Security Handled By Cdn
Content Delivery Network It Data Security Handled By CdnThis slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver an outstanding presentation on the topic using this Content Delivery Network It Data Security Handled By Cdn. Dispense information and present a thorough explanation of Data Security Handled By CDN using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enabling Data Security Risk Management Action Plan Building Business Analytics Architecture
Enabling Data Security Risk Management Action Plan Building Business Analytics ArchitectureThe data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Present the topic in a bit more detail with this Enabling Data Security Risk Management Action Plan Building Business Analytics Architecture. Use it as a tool for discussion and navigation on Potential Risk, Risk Level, Reason For Risk Rating, Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.





