Powerpoint Templates and Google slides for Secure.
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
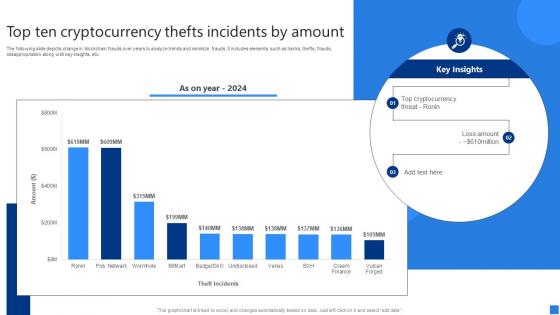 Top Ten Cryptocurrency Thefts Securing Blockchain Transactions A Beginners Guide BCT SS V
Top Ten Cryptocurrency Thefts Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc. Deliver an outstanding presentation on the topic using this Top Ten Cryptocurrency Thefts Securing Blockchain Transactions A Beginners Guide BCT SS V. Dispense information and present a thorough explanation of Top Cryptocurrency Threat, Loss Amount, Incidents Amount using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
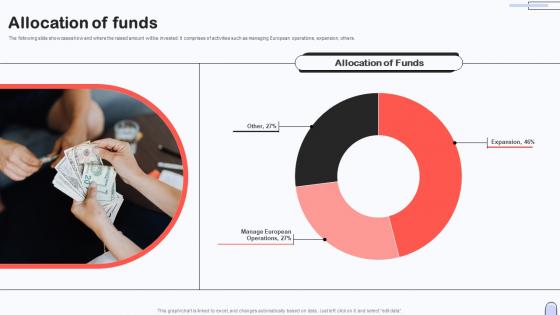 Allocation Of Funds Investor Capital Pitch Deck For Secure Digital Payment Platform
Allocation Of Funds Investor Capital Pitch Deck For Secure Digital Payment PlatformThe following slide showcases how and where the raised amount will be invested. It comprises of activities such as managing European operations, expansion, others. Present the topic in a bit more detail with this Allocation Of Funds Investor Capital Pitch Deck For Secure Digital Payment Platform. Use it as a tool for discussion and navigation on Allocation, Funds. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Performance Investor Capital Pitch Deck For Secure Digital Payment Platform
Financial Performance Investor Capital Pitch Deck For Secure Digital Payment PlatformThe following slide depicts previous financial performance of payment infrastructure company to grab investors interest towards business growth. It comprises of yearly revenue trends. Present the topic in a bit more detail with this Financial Performance Investor Capital Pitch Deck For Secure Digital Payment Platform Use it as a tool for discussion and navigation on Financial Performance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
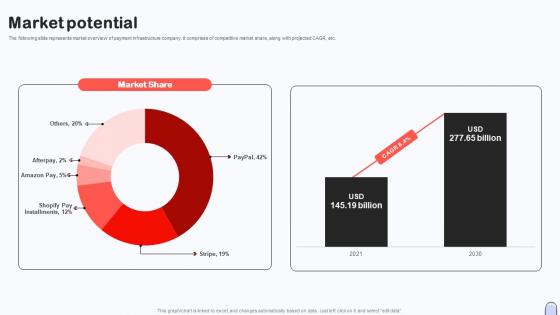 Market Potential Investor Capital Pitch Deck For Secure Digital Payment Platform
Market Potential Investor Capital Pitch Deck For Secure Digital Payment PlatformThe following slide represents market overview of payment infrastructure company. It comprises of competitive market share, along with projected CAGR, etc. Present the topic in a bit more detail with this Market Potential Investor Capital Pitch Deck For Secure Digital Payment Platform Use it as a tool for discussion and navigation on Market Share, Market Potential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
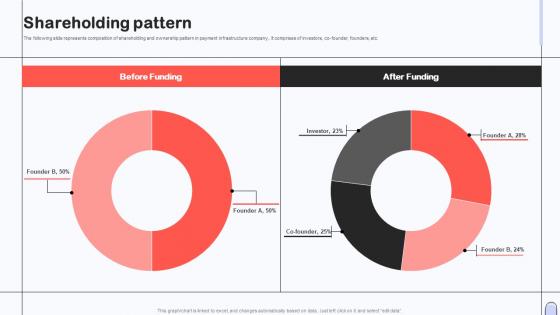 Shareholding Pattern Investor Capital Pitch Deck For Secure Digital Payment Platform
Shareholding Pattern Investor Capital Pitch Deck For Secure Digital Payment PlatformThe following slide represents composition of shareholding and ownership pattern in payment infrastructure company,. It comprises of investors, co-founder, founders, etc. Deliver an outstanding presentation on the topic using this Shareholding Pattern Investor Capital Pitch Deck For Secure Digital Payment Platform Dispense information and present a thorough explanation of Shareholding Pattern using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Infrastructure As Code Security Tracking Dashboard Infrastructure As Code Adoption Strategy
Infrastructure As Code Security Tracking Dashboard Infrastructure As Code Adoption StrategyThis slide represents the security in Infrastructure as Code tracking dashboard. The key components include container image, misconfigured workload, risk assets, failed codes by credentials, transit, valuable public interface, etc. Deliver an outstanding presentation on the topic using this Infrastructure As Code Security Tracking Dashboard Infrastructure As Code Adoption Strategy. Dispense information and present a thorough explanation of Security In Infrastructure, Code Tracking Dashboard, Misconfigured Workload, Risk Assets, Valuable Public Interface using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
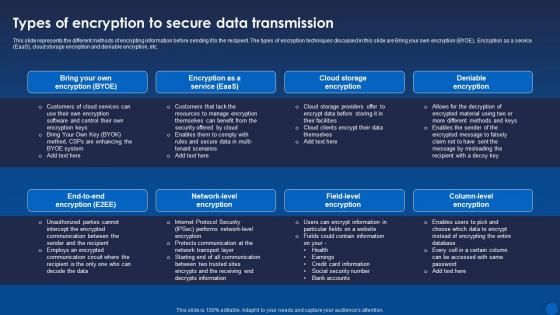 Types Of Encryption To Secure Data Transmission Encryption For Data Privacy In Digital Age It
Types Of Encryption To Secure Data Transmission Encryption For Data Privacy In Digital Age ItThis slide represents the different methods of encrypting information before sending it to the recipient. The types of encryption techniques discussed in this slide are Bring your own encryption BYOE, Encryption as a service EaaS, cloud storage encryption and deniable encryption, etc. Present the topic in a bit more detail with this Types Of Encryption To Secure Data Transmission Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Data Transmission, Encryption, Deniable Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attack Incident Tracking Dashboard Creating Cyber Security Awareness
Cyber Attack Incident Tracking Dashboard Creating Cyber Security AwarenessThe following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Tracking Dashboard Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Infected Hosts, Cyber Attack Trends This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Trend Analysis With Kpi Dashboard Creating Cyber Security Awareness
Data Breach Trend Analysis With Kpi Dashboard Creating Cyber Security AwarenessThe following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. Deliver an outstanding presentation on the topic using this Data Breach Trend Analysis With Kpi Dashboard Creating Cyber Security Awareness Dispense information and present a thorough explanation of Systems And Passwords, Phishing Exercise, Penetration Test using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Expenditure Summary Dashboard Creating Cyber Security Awareness
Information Technology Expenditure Summary Dashboard Creating Cyber Security AwarenessThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Deliver an outstanding presentation on the topic using this Information Technology Expenditure Summary Dashboard Creating Cyber Security Awareness Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Security Failure By Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Major Causes Of Cyber Crimes And Attacks Creating Cyber Security Awareness
Major Causes Of Cyber Crimes And Attacks Creating Cyber Security AwarenessThe following slide highlights the key reasons of cyber-attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Present the topic in a bit more detail with this Major Causes Of Cyber Crimes And Attacks Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Mean Time To Detect, Mean Time To Resolve This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Decision Making Dashboard
Cyber Security Decision Making DashboardThis slide depicts cyber security dashboard that helps to improve situational awareness and enhance decision-making of organization. It includes elements such as phishing, ransomware, mobile security attacks, remote working risks and identity-based cloud security threats. Introducing our Cyber Security Decision Making Dashboard set of slides. The topics discussed in these slides are Cyber Security, Decision Making Dashboard. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Breakdown Of IoT Threats To Enhance Security IoT Security And Privacy Safeguarding IoT SS
Breakdown Of IoT Threats To Enhance Security IoT Security And Privacy Safeguarding IoT SSThis slide highlights top internet of things security breaches to enhance understanding and enable proactive threat mitigation. It includes various threats such as malware attacks, exploits, and user practices related threats. Present the topic in a bit more detail with this Breakdown Of IoT Threats To Enhance Security IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Scanning Network Connected, Attacks Exploit, Device Weaknesses. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Of Things Security Global Market Size IoT Security And Privacy Safeguarding IoT SS
Internet Of Things Security Global Market Size IoT Security And Privacy Safeguarding IoT SSThis slide showcases a graphical representation of IoT securitys global market size. It includes various growth drivers such as the growing number of IoT devices in market and rise in malware attacks to infect enterprise IoT devices.Deliver an outstanding presentation on the topic using this Internet Of Things Security Global Market Size IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Security Global Market, American Region, Rise Malware Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Stats Associated With Connected Devices IoT Security And Privacy Safeguarding IoT SS
Key Stats Associated With Connected Devices IoT Security And Privacy Safeguarding IoT SSThis slide showcases year on year growth of connected devices globally. It includes stats data related to connected devise growth, sensors and actuators market size, and China as a largest contributor to consumer IoT devices. Present the topic in a bit more detail with this Key Stats Associated With Connected Devices IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Largest Contributor, Associated Connected, Devices Expected. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents IoT Security And Privacy Safeguarding The Digital Ecosystem IoT SS
Table Of Contents IoT Security And Privacy Safeguarding The Digital Ecosystem IoT SSIncrease audience engagement and knowledge by dispensing information using Table Of Contents IoT Security And Privacy Safeguarding The Digital Ecosystem IoT SS. This template helps you present information on five stages. You can also present information on Introduction Iot Security, Need Iot, Security Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Allocation Of Funds Secure Email Solution Investor Funding Elevator Pitch Deck By Paubox
Allocation Of Funds Secure Email Solution Investor Funding Elevator Pitch Deck By PauboxThis slide covers graphical representation of raised funds allocation for various reasons such as business expansion, team expansion and research and development. Present the topic in a bit more detail with this Allocation Of Funds Secure Email Solution Investor Funding Elevator Pitch Deck By Paubox. Use it as a tool for discussion and navigation on Allocation Of Funds. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Performance Secure Email Solution Investor Funding Elevator Pitch Deck By Paubox
Financial Performance Secure Email Solution Investor Funding Elevator Pitch Deck By PauboxThis slide covers the graphical representation monthly recurring revenue of the company. It depicts the continues revenue growth of email security. Present the topic in a bit more detail with this Financial Performance Secure Email Solution Investor Funding Elevator Pitch Deck By Paubox. Use it as a tool for discussion and navigation on Monthly Recurring Revenue, This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Projections Secure Email Solution Investor Funding Elevator Pitch Deck By Paubox
Financial Projections Secure Email Solution Investor Funding Elevator Pitch Deck By PauboxThis slide covers a graphical representation of the forecasted financial growth of the company. It depicts that the company is expected to grow at continuous rate. Deliver an outstanding presentation on the topic using this Financial Projections Secure Email Solution Investor Funding Elevator Pitch Deck By Paubox. Dispense information and present a thorough explanation of Financial Projections using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Importance Of Firewall As A Service In Network Security Firewall Virtualization
Importance Of Firewall As A Service In Network Security Firewall VirtualizationThis slide outlies the various reasons which enhance the adoption of FWaaS by organizations. The purpose of this slide is to explain the limitations of traditional firewall services which can be overcame by using FWaaS. These are location and scalability. Increase audience engagement and knowledge by dispensing information using Importance Of Firewall As A Service In Network Security Firewall Virtualization. This template helps you present information on two stages. You can also present information on Problems Faced, Organizations, Traditional Firewalls, using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
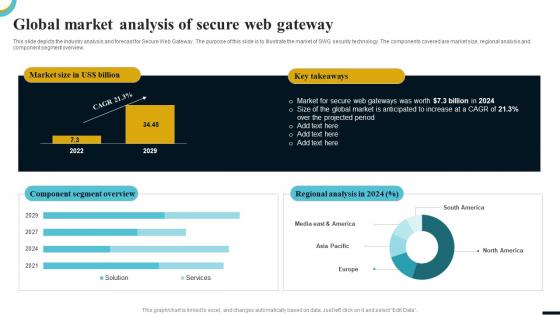 Internet Gateway Security IT Global Market Analysis Of Secure Web Gateway
Internet Gateway Security IT Global Market Analysis Of Secure Web GatewayThis slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview. Present the topic in a bit more detail with this Internet Gateway Security IT Global Market Analysis Of Secure Web Gateway. Use it as a tool for discussion and navigation on Component Segment Overview, Regional Analysis, Market Size. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
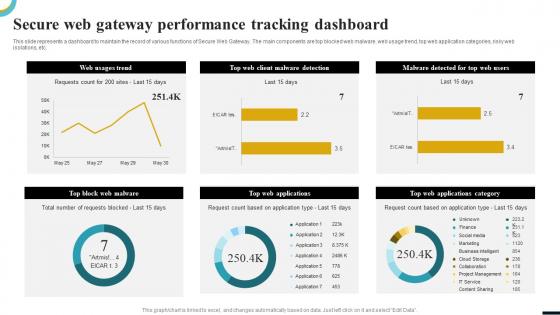 Internet Gateway Security IT Secure Web Gateway Performance Tracking
Internet Gateway Security IT Secure Web Gateway Performance TrackingThis slide represents a dashboard to maintain the record of various functions of Secure Web Gateway. The main components are top blocked web malware, web usage trend, top web application categories, risky web isolations, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Secure Web Gateway Performance Tracking. Use it as a tool for discussion and navigation on Web Usages Trend, Top Block Web Malware, Top Web Applications, Top Web Applications Category, Top Web Client Malware Detection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
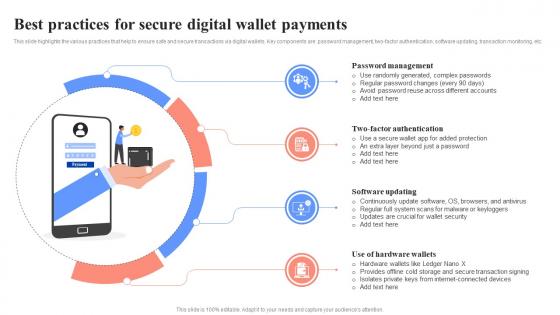 Best Practices For Secure Digital Wallet Payments Unlocking Digital Wallets All You Need Fin SS
Best Practices For Secure Digital Wallet Payments Unlocking Digital Wallets All You Need Fin SSThis slide highlights the various practices that help to ensure safe and secure transactions via digital wallets. Key components are password management, two-factor authentication, software updating, transaction monitoring, etc. Introducing Best Practices For Secure Digital Wallet Payments Unlocking Digital Wallets All You Need Fin SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Password Management, Two-Factor Authentication, Software Updating, using this template. Grab it now to reap its full benefits.
-
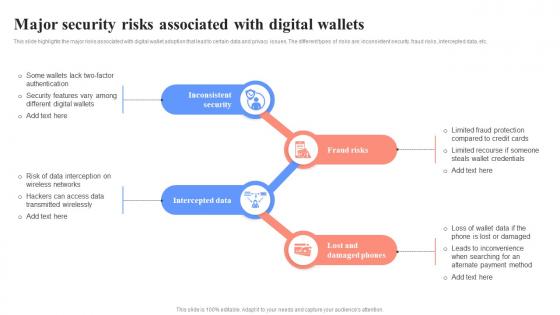 Major Security Risks Associated With Digital Wallets Unlocking Digital Wallets All You Need Fin SS
Major Security Risks Associated With Digital Wallets Unlocking Digital Wallets All You Need Fin SSThis slide highlights the major risks associated with digital wallet adoption that lead to certain data and privacy issues. The different types of risks are inconsistent security, fraud risks, intercepted data, etc. Introducing Major Security Risks Associated With Digital Wallets Unlocking Digital Wallets All You Need Fin SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Inconsistent Security, Intercepted Data, Lost And Damaged Phones, using this template. Grab it now to reap its full benefits.
-
 Challenges Faced By Network Media Teams In Managing Security Issues
Challenges Faced By Network Media Teams In Managing Security IssuesThis slide depicts challenges faced by network media in solving security issues to safeguard digital assets and ensure the integrity, confidentiality, and availability of media content. Introducing our Challenges Faced By Network Media Teams In Managing Security Issues set of slides. The topics discussed in these slides are Measures, Performance, Functionality. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
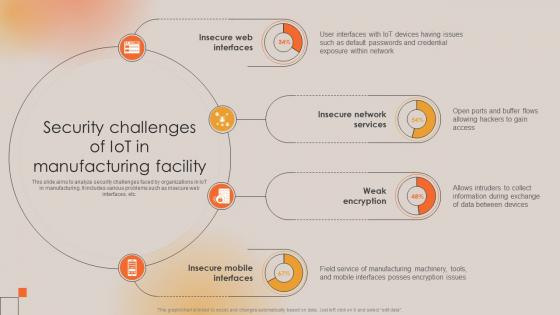 Security Challenges Of IoT In Manufacturing Facility Boosting Manufacturing Efficiency With IoT
Security Challenges Of IoT In Manufacturing Facility Boosting Manufacturing Efficiency With IoTThis slide aims to analyze security challenges faced by organizations in IoT in manufacturing. It includes various problems such as insecure web interfaces, etc. Deliver an outstanding presentation on the topic using this Security Challenges Of IoT In Manufacturing Facility Boosting Manufacturing Efficiency With IoT. Dispense information and present a thorough explanation of Web Interfaces, Network Services, Weak Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Web Security Performance Monitoring Dashboard
Web Security Performance Monitoring DashboardThis slide showcases the performance tracking dashboard for web security based on various parameters such as attack types, event status, etc. Presenting our well structured Web Security Performance Monitoring Dashboard. The topics discussed in this slide are Web Security, Performance Monitoring, Dashboard, Event Status. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Wireless Internet Security Us Market Size By Deployment
Wireless Internet Security Us Market Size By DeploymentThe following slide presents data on expected CAGR, deployment methods cloud, on-premise, security adoption trends, and more to depict the size and dynamics of the wireless internet security market in the United States, aiding in market analysis and decision-making. Presenting our well structured Wireless Internet Security Us Market Size By Deployment. The topics discussed in this slide are Deployment, Professional, Growth. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
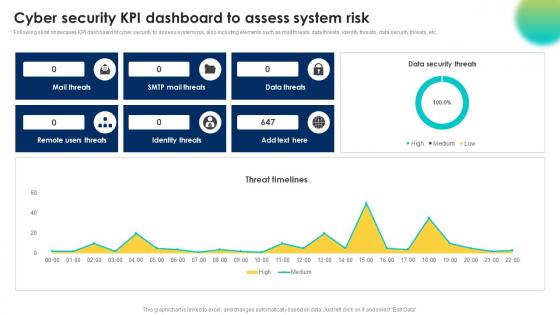 Cyber Security Kpi Dashboard To Assess System Risk
Cyber Security Kpi Dashboard To Assess System RiskFollowing slide showcases KPI dashboard of cyber security to assess system risk, also including elements such as mail threats, data threats, identity threats, data security threats, etc. Presenting our well structured Cyber Security Kpi Dashboard To Assess System Risk. The topics discussed in this slide are Identity Threats, Remote Users Threats, Data Threats. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Triage Cyber Security Dashboard To Response Phishing Threats
Triage Cyber Security Dashboard To Response Phishing ThreatsThis slide represents triage cyber security dashboard to response phishing threats which assists to analyse and response to phishing attacks. It includes key components such as active clusters, processed reports, etc Presenting our well structured Triage Cyber Security Dashboard To Response Phishing Threats The topics discussed in this slide are Active Clusters, Categorized Reports. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Triage Cyber Security For Vulnerability Management Dashboard
Triage Cyber Security For Vulnerability Management DashboardThis slide represents triage cyber security for vulnerability management dashboard which assist to identify and prevent system vulnerabilities. It includes key components such as latest scans, tracker, etc Introducing our Triage Cyber Security For Vulnerability Management Dashboard set of slides. The topics discussed in these slides are Most Vulnerable Hosts, Vulnerabilities Status This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Triage Security Dashboard To Detect Cybersecurity Issues
Triage Security Dashboard To Detect Cybersecurity IssuesThis slide represents triage cyber security dashboard to detect cybersecurity issues which is utilized by organizations to investigate its endpoints and detect cyber threats. It includes key components such as total incidents count, level of threat, etc Introducing our Triage Security Dashboard To Detect Cybersecurity Issues set of slides. The topics discussed in these slides are Incident Trend By Level, Classification Of Incidents, Top Attackers. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Attack Incident Tracking Dashboard Implementing Strategies To Mitigate Cyber Security Threats
Cyber Attack Incident Tracking Dashboard Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the number of cyber attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Tracking Dashboard Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Prevented Attacks, Cyber Attack Trends This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Trend Analysis With KPI Dashboard Implementing Strategies To Mitigate Cyber Security Threats
Data Breach Trend Analysis With KPI Dashboard Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. Present the topic in a bit more detail with this Data Breach Trend Analysis With KPI Dashboard Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Current And Future Goal Analysis, Breach Risk Trend This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats
Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Deliver an outstanding presentation on the topic using this Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Cyber Security Budget Spent, It Costs And Revenue, Issue Status Summary using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security Threats
Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights the key reasons of cyber attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Deliver an outstanding presentation on the topic using this Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Employees, Management, Training Courses using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Allocation Of Funds Smart Farming Technology Pitch Deck For Food Security
Allocation Of Funds Smart Farming Technology Pitch Deck For Food SecurityFollowing slide showcases company funds usage for various agriculture and farming development. It includes funds allocated for technology, marketing, food security etc. Present the topic in a bit more detail with this Allocation Of Funds Smart Farming Technology Pitch Deck For Food Security Use it as a tool for discussion and navigation on Funds Allocation, Crop Productivity, Overcome Operational This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Shareholding Pattern Smart Farming Technology Pitch Deck For Food Security
Shareholding Pattern Smart Farming Technology Pitch Deck For Food SecurityFollowing slide showcases shareholding pattern of company. It include details about company shareholders name, designation and percentage of shares holdings. Present the topic in a bit more detail with this Shareholding Pattern Smart Farming Technology Pitch Deck For Food Security Use it as a tool for discussion and navigation on Shareholding Pattern, Banking Company This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 CASB Performance Tracking Dashboard CASB Cloud Security
CASB Performance Tracking Dashboard CASB Cloud SecurityThis slide outlines the performance tracking dashboard for CASB deployment. The purpose of this slide is to showcase the status of various applications, IP addresses, users, machines, and web traffic. It also includes cloud discovery open alerts, risk levels, and top entities. Present the topic in a bit more detail with this CASB Performance Tracking Dashboard CASB Cloud Security. Use it as a tool for discussion and navigation on Performance Tracking Dashboard, Risk Levels, Cloud Discovery Alerts. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Use Cases CASB Cloud Security
Cloud Access Security Broker Use Cases CASB Cloud SecurityThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Present the topic in a bit more detail with this Cloud Access Security Broker Use Cases CASB Cloud Security. Use it as a tool for discussion and navigation on Protection Against Threats, Compliance Policies, Cloud Access Security Broker. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents CASB Cloud Security Ppt Infographic Template Gallery
Table Of Contents CASB Cloud Security Ppt Infographic Template GalleryIncrease audience engagement and knowledge by dispensing information using Table Of Contents CASB Cloud Security Ppt Infographic Template Gallery. This template helps you present information on six stages. You can also present information on Cloud Access Security Broker, Shadow IT Management Lifecycle, Emerging Cloud Security Risks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Asset Allocation Plan Based On Various Strategic Retirement Planning To Build Secure Future Fin SS
Asset Allocation Plan Based On Various Strategic Retirement Planning To Build Secure Future Fin SSThis slide covers process of diversifying investments by selecting a variety of different types of investments. It covers information about investors such as aggressive, moderate and conservative. Present the topic in a bit more detail with this Asset Allocation Plan Based On Various Strategic Retirement Planning To Build Secure Future Fin SS. Use it as a tool for discussion and navigation on Aggressive, Moderate, Conservative. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
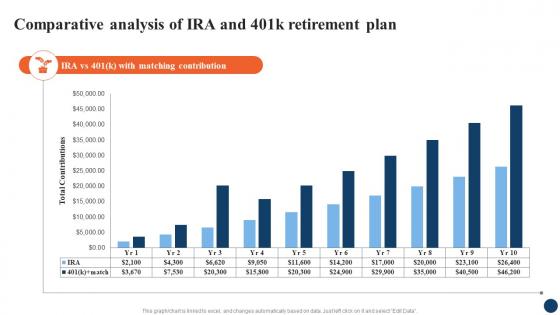 Comparative Analysis Of IRA Strategic Retirement Planning To Build Secure Future Fin SS
Comparative Analysis Of IRA Strategic Retirement Planning To Build Secure Future Fin SSPresent the topic in a bit more detail with this Comparative Analysis Of IRA Strategic Retirement Planning To Build Secure Future Fin SS. Use it as a tool for discussion and navigation on Comparative Analysis, IRA And 401k, Retirement Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
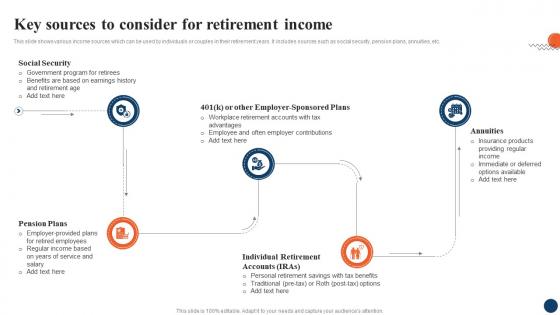 Key Sources To Consider Strategic Retirement Planning To Build Secure Future Fin SS
Key Sources To Consider Strategic Retirement Planning To Build Secure Future Fin SSThis slide shows various income sources which can be used by individuals or couples in their retirement years. It includes sources such as social security, pension plans, annuities, etc. Introducing Key Sources To Consider Strategic Retirement Planning To Build Secure Future Fin SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Social Security, Pension Plans, Annuities, using this template. Grab it now to reap its full benefits.
-
 KPI Dashboard To Track Strategic Retirement Planning To Build Secure Future Fin SS
KPI Dashboard To Track Strategic Retirement Planning To Build Secure Future Fin SSThis slide shows dashboard which can be used by individuals who are saving or investing money for retirement. It includes metrics such as total balance, contributions overtime, goal achievement, etc. Present the topic in a bit more detail with this KPI Dashboard To Track Strategic Retirement Planning To Build Secure Future Fin SS. Use it as a tool for discussion and navigation on KPI Dashboard, Track Retirement, Savings. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Retirement Planning To Save Strategic Retirement Planning To Build Secure Future Fin SS
Retirement Planning To Save Strategic Retirement Planning To Build Secure Future Fin SSThis slide shows detailed information which can be used by individuals or couples to plan retirement income. It includes overview of situation, key challenges, solutions and results. Introducing Retirement Planning To Save Strategic Retirement Planning To Build Secure Future Fin SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Retirement Accounts, Investments, Real Estate Holdings, using this template. Grab it now to reap its full benefits.
-
 U S Pension Funds Strategic Retirement Planning To Build Secure Future Fin SS
U S Pension Funds Strategic Retirement Planning To Build Secure Future Fin SSPresent the topic in a bit more detail with this U S Pension Funds Strategic Retirement Planning To Build Secure Future Fin SS. Use it as a tool for discussion and navigation on Study Period, Market Size, Market Concentration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
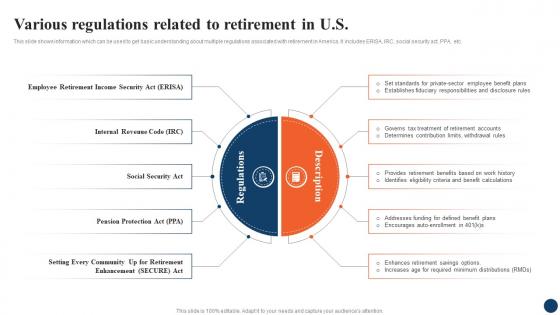 Various Regulations Related Strategic Retirement Planning To Build Secure Future Fin SS
Various Regulations Related Strategic Retirement Planning To Build Secure Future Fin SSThis slide shows information which can be used to get basic understanding about multiple regulations associated with retirement in America. It includes ERISA, IRC, social security act, PPA, etc.Increase audience engagement and knowledge by dispensing information using Various Regulations Related Strategic Retirement Planning To Build Secure Future Fin SS. This template helps you present information on two stages. You can also present information on Social Security Act, Pension Protection, Internal Revenue Code using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
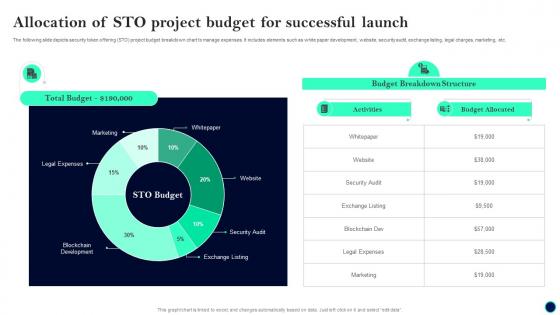 Allocation Of STO Project Budget Beginners Guide To Successfully Launch Security Token BCT SS V
Allocation Of STO Project Budget Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide depicts security token offering STO project budget breakdown chart to manage expenses. It includes elements such as white paper development, website, security audit, exchange listing, legal charges, marketing, etc. Present the topic in a bit more detail with this Allocation Of STO Project Budget Beginners Guide To Successfully Launch Security Token BCT SS V. Use it as a tool for discussion and navigation on Total Budget, Budget Breakdown Structure, Activities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
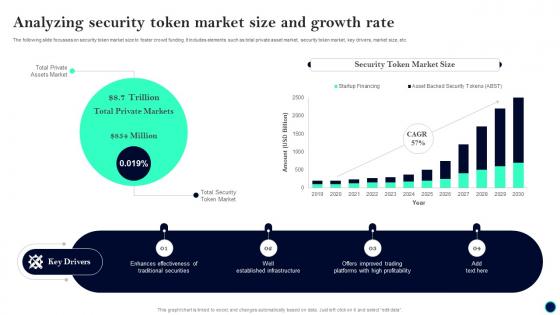 Analyzing Security Token Beginners Guide To Successfully Launch Security Token BCT SS V
Analyzing Security Token Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide focusses on security token market size to foster crowd funding. It includes elements such as total private asset market, security token market, key drivers, market size, etc. Deliver an outstanding presentation on the topic using this Analyzing Security Token Beginners Guide To Successfully Launch Security Token BCT SS V. Dispense information and present a thorough explanation of Security Token, Market Size, Key Drivers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assessing Number Of Security Beginners Guide To Successfully Launch Security Token BCT SS V
Assessing Number Of Security Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide depicts the number of security token offerings STOs launched by industry type. It includes elements such as finance, banking, blockchain, real estate, service, technology, healthcare, software, sports, art, energy, etc. Present the topic in a bit more detail with this Assessing Number Of Security Beginners Guide To Successfully Launch Security Token BCT SS V. Use it as a tool for discussion and navigation on Sto Per Industry, Banking Industry, Key Insights. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
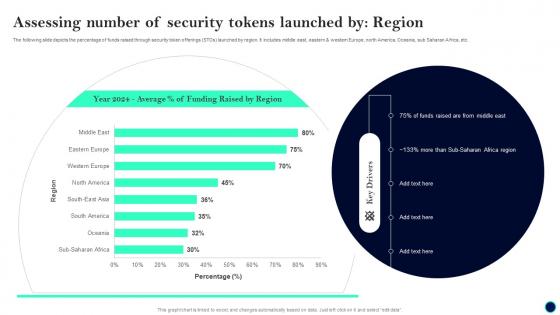 Assessing Number Of Security Tokens Beginners Guide To Successfully Launch Security Token BCT SS V
Assessing Number Of Security Tokens Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide depicts the percentage of funds raised through security token offerings STOs launched by region. It includes middle east, eastern and western Europe, north America, Oceania, sub Saharan Africa, etc. Deliver an outstanding presentation on the topic using this Assessing Number Of Security Tokens Beginners Guide To Successfully Launch Security Token BCT SS V. Dispense information and present a thorough explanation of Assessing Number, Security Tokens Launched, Region using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
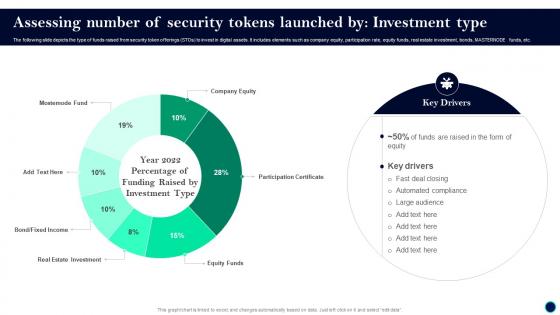 Beginners Guide To Successfully Launch Security Token Assessing Number Of Security BCT SS V
Beginners Guide To Successfully Launch Security Token Assessing Number Of Security BCT SS VThe following slide depicts the type of funds raised from security token offerings STOs to invest in digital assets. It includes elements such as company equity, participation rate, equity funds, real estate investment, bonds, MASTERNODE funds, etc. Present the topic in a bit more detail with this Beginners Guide To Successfully Launch Security Token Assessing Number Of Security BCT SS V. Use it as a tool for discussion and navigation on Key Drivers, Deal Closing, Automated Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Budget Allocation For Big Data Cyber Security Application
Budget Allocation For Big Data Cyber Security ApplicationThis slide showcases the budget allocation for various activities in big data cyber security. Its purpose is to understand the budgetary plan for cyber security. This slide includes authentication, monitoring, incident response, malware protection, network traffic, log management, data protection, etc. Introducing our Budget Allocation For Big Data Cyber Security Application set of slides. The topics discussed in these slides are Allocation, Cyber, Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Internal And External Sources Of Big Data In Cyber Security
Internal And External Sources Of Big Data In Cyber SecurityThis slide showcases the sources of the big data in cyber security. Its aim is to define the various sources of data internal and external. This slide includes transactions, log data, emails, social media, audio, photos, etc. Introducing our Internal And External Sources Of Big Data In Cyber Security set of slides. The topics discussed in these slides are Generate, Focused, Companies. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Percentage Usage Of Big Data In Cyber Security
Percentage Usage Of Big Data In Cyber SecurityThis slide depicts percentage use of big data in cyber security companies. Its purpose is to show how many companies are using this technology or want to implement to secure cyber network. This slide includes the companies which are ready to use big data, not ready, still thinking Introducing our Percentage Usage Of Big Data In Cyber Security set of slides. The topics discussed in these slides are Security, Cyber, Percentage. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Yearly Growth Of Cyber Security Big Data Market
Yearly Growth Of Cyber Security Big Data MarketThis slide depicts the yearly growth of cyber security big data market. Its aim is to show the year on year growth for the big data market to show the industries relevance. This slide includes the constant growth of industry growth in billions. Introducing our Yearly Growth Of Cyber Security Big Data Market set of slides. The topics discussed in these slides are Growth, Security, Market. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Dashboard For Tracking Data Breach Intelligence
Cyber Security Dashboard For Tracking Data Breach IntelligenceThe highlighted slide focuses on key elements such as threat intelligence, activity trends, malware sightings, and the identification of active and most active vulnerabilities. This data is essential for a cybersecurity dashboard, providing valuable insights and intelligence to proactively address and mitigate potential data breaches. Presenting our well structured Cyber Security Dashboard For Tracking Data Breach Intelligence. The topics discussed in this slide are Digital Threat Monitoring, File Analysis, Threat Intelligence. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Score Metrics Evaluation Of Cybersecurity Training Dashboard
Security Score Metrics Evaluation Of Cybersecurity Training DashboardThis slide demonstrates cybersecurity training metrics KPI dashboard to measure risk rating and include security score, security score category breakdown, high risk participants, etc. Introducing our Security Score Metrics Evaluation Of Cybersecurity Training Dashboard set of slides. The topics discussed in these slides are Security Score Metrics Evaluation, Cybersecurity Training Dashboard This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Dashboard For Tracking Security Gap In Software
Dashboard For Tracking Security Gap In SoftwareThis slides showcase a KPI tracking dashboard for analysing security gaps. The main purpose of this template is to showcase various threats and detection. This includes detection threat, threat per day, files, blocked, risk, etc. Introducing our Dashboard For Tracking Security Gap In Software set of slides. The topics discussed in these slides are Detection Threat, Threat Per Day, Service Compliance, Installed Software Compliance. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.





