Powerpoint Templates and Google slides for Secure
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Dashboard For Tracking Visualization Security In Softwares
Dashboard For Tracking Visualization Security In SoftwaresThis slides showcases KPI tracking dashboard for visualization security. The main purpose of this template is to showcase various threats and detection. This includes detection threat, threat per day, files, blocked, risk, etc. Introducing our Dashboard For Tracking Visualization Security In Softwares set of slides. The topics discussed in these slides are Detection Threat, Threat Per Day, Service Running. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Endpoint Cyber Security Market Insights
Endpoint Cyber Security Market InsightsThis slide presents key insights of endpoint cyber security market. The purpose of this slide is to assist businesses in prioritizing IT security for establishing a strong risk management policy. It covers trends such as market share, deployment, components, global market value and key insights. Introducing our Endpoint Cyber Security Market Insights set of slides. The topics discussed in these slides are Endpoint Cyber Security, Market Insights This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Application Security Implementation Plan Application Security Performance Monitoring Dashboard
Application Security Implementation Plan Application Security Performance Monitoring DashboardThis slide showcases the performance tracking dashboard for application security to analyze and monitor security of application. Present the topic in a bit more detail with this Application Security Implementation Plan Application Security Performance Monitoring Dashboard. Use it as a tool for discussion and navigation on Application Security, Performance, Monitoring Dashboard, Monitor Security Of Application. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Application Security Vulnerability Scanning Dashboard
Application Security Implementation Plan Application Security Vulnerability Scanning DashboardThis slide depicts the threat scanning dashboard for application security to analyze and monitor vulnerabilities of application. Present the topic in a bit more detail with this Application Security Implementation Plan Application Security Vulnerability Scanning Dashboard. Use it as a tool for discussion and navigation on Application Security Vulnerability, Scanning Dashboard, Monitor Vulnerabilities Of Application. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
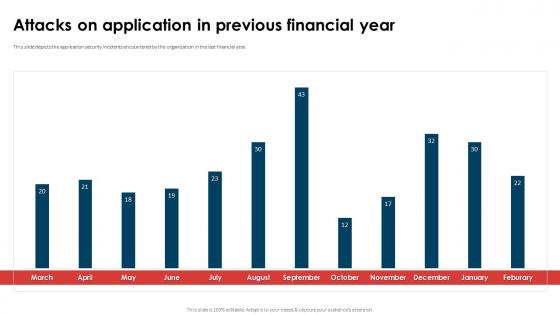 Application Security Implementation Plan Attacks On Application In Previous Financial Year
Application Security Implementation Plan Attacks On Application In Previous Financial YearThis slide depicts the threat scanning dashboard for application security to analyze and monitor vulnerabilities of application. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Attacks On Application In Previous Financial Year. Dispense information and present a thorough explanation of Attacks On Application, Previous Financial Year, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Budget Allocation For Application Security Training
Application Security Implementation Plan Budget Allocation For Application Security TrainingThis slide showcases the training cost breakdown for different components such as instructor, training cost, etc. Present the topic in a bit more detail with this Application Security Implementation Plan Budget Allocation For Application Security Training. Use it as a tool for discussion and navigation on Budget Allocation, Application Security Training, Training Cost Breakdown, Training Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Hids Cyber Security Dashboard To Identify Network Threats
Hids Cyber Security Dashboard To Identify Network ThreatsThis slide represents HIDS cyber security dashboard to identify network issues and monitor malicious activity in host devices which could lead to serious breaches. It includes key components such as number of alerts, summary of alerts, etc Introducing our Hids Cyber Security Dashboard To Identify Network Threats set of slides. The topics discussed in these slides are Security, Dashboard, Network Threats. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Hids Dashboard For Cyber Security And Real Time Monitoring
Hids Dashboard For Cyber Security And Real Time MonitoringThis slide represents HIDS dashboard for cyber security which assists to collect, aggregate and analyse security data. It includes key components such as alerts evolution, top tactics, authentication failures, etc Introducing our Hids Dashboard For Cyber Security And Real Time Monitoring set of slides. The topics discussed in these slides are Dashboard, Monitoring, Cyber Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Infrastructure As Code Security Monitoring Dashboard
Infrastructure As Code Security Monitoring DashboardThis slide represents the dashboard of Infrastructure as Code for monitoring and tracking security, the components include compliance status, etc. Presenting our well structured Infrastructure As Code Security Monitoring Dashboard. The topics discussed in this slide are Compliance Severity, Violations By Severity, IAC Resources. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Military And Security Robotics Market Segmentation
Military And Security Robotics Market SegmentationThe purpose of this slide is to segment the military and security robotics market, categorizing robots based on their applications in military and security operations such as surveillance, reconnaissance, etc. Elements include market size by components, platforms, etc. Presenting our well structured Military And Security Robotics Market Segmentation The topics discussed in this slide are Explosive Ordnance Disposal, Autonomous Solutions, Agility RoboticsThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Encryption For Data Encrypted Email Practices For Secure Messaging Cybersecurity SS
Encryption For Data Encrypted Email Practices For Secure Messaging Cybersecurity SSThis slide showcases public key cryptography deployment which can help employees increased speed and user experience of their platforms. It provides details about private key, key generation, decryption, etc. Present the topic in a bit more detail with this Encryption For Data Encrypted Email Practices For Secure Messaging Cybersecurity SS. Use it as a tool for discussion and navigation on Reduced Data Breaches, Reduced Email Compromises, Create Strong Passwords. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Major Types Of Encryption For Data Security Cybersecurity SS
Encryption For Data Major Types Of Encryption For Data Security Cybersecurity SSThis slide major types of encryption technology, focused on improving data privacy and security of todays business. It provides details about symmetric, asymmetric, RSA, data encryption standard, etc. Introducing Encryption For Data Major Types Of Encryption For Data Security Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Symmetric Encryption, Asymmetric Encryption, RSA Encryption, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data SSL Protocol Deployment For Secure Communication Cybersecurity SS
Encryption For Data SSL Protocol Deployment For Secure Communication Cybersecurity SSThis slide showcases secure socket layer SSL deployment which can help employees perform secure communication within businesses. It provides details about certificate authority, webmaster, etc. Present the topic in a bit more detail with this Encryption For Data SSL Protocol Deployment For Secure Communication Cybersecurity SS. Use it as a tool for discussion and navigation on Reduced Message Forgery, Reduced Data Theft, Less Eavesdropping. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Kpi Dashboard To Measure Security Vulnerabilities Software Performance
Kpi Dashboard To Measure Security Vulnerabilities Software PerformanceFollowing slide showcases security vulnerabilities measutequal toring KPI dashboard to assess software performance. It further covers vulnerability status, days awaiting approval, days awaiting execution, days to close alongside vulnerabilities per stage, etc. Presenting our well structured Kpi Dashboard To Measure Security Vulnerabilities Software Performance The topics discussed in this slide are Days Awaiting Execution, Awaiting Execution, Awaiting ApprovalThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Survey Analysis Of Major Network Security Vulnerabilities
Survey Analysis Of Major Network Security VulnerabilitiesFollowing slide represents vulnerabilities to network security with survey. It further includes survey on 50 companies showcasing results such as broken access control, broken authentication, sensitive data exposure, etc. Presenting our well structured Survey Analysis Of Major Network Security Vulnerabilities The topics discussed in this slide are Users Web Applications, Data Breach, High SeverityThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Physical Security System Dashboard To Track Potential Threat
Physical Security System Dashboard To Track Potential ThreatThis slide showcases the dashboard of physical security system to ensure real-time monitoring and tracking of potential threats. The dashboard includes cyber and physical threats. Introducing our Physical Security System Dashboard To Track Potential Threat set of slides. The topics discussed in these slides are Vulnerabilities Select Threat, Insider Threats, Cyber Attack. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Impact On Business Expenses Business Recovery Plan To Overcome Cyber Security Threat
Cyber Impact On Business Expenses Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the impact of cyber response plan impact on business finances over the years. It includes key reasons of reduced cyber-attack costing such as Deliver an outstanding presentation on the topic using this Cyber Impact On Business Expenses Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Business, Finances, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Monitoring Dashboard Business Recovery Plan To Overcome Cyber Security Threat
Cyber Monitoring Dashboard Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide demonstrates cyber incident tracking dashboard. It showcase number of open cases, resolved incidents, open tickets, resolved tickets, number of incidents per incident type and incidents by cyber attack type. Deliver an outstanding presentation on the topic using this Cyber Monitoring Dashboard Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Monitoring, Dashboard, Demonstrates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Post Incident Review Checklist Business Recovery Plan To Overcome Cyber Security Threat
Cyber Post Incident Review Checklist Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the incident assessment checklist. It includes key assessment areas such as incident documentation, communication, incident response team activation, containment of threats, etc. Present the topic in a bit more detail with this Cyber Post Incident Review Checklist Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Communication, Response Team, Contain Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard For Tracking Cyber Security Attack Business Recovery Plan To Overcome Cyber Security Threat
Dashboard For Tracking Cyber Security Attack Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides a graphical presentation of cyber attacks and costs per incident. It includes key elements such as cost per incident, attack rate by month, cost of incident by assets, and time taken to detect and resolve the attack. Deliver an outstanding presentation on the topic using this Dashboard For Tracking Cyber Security Attack Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Dashboard, Reported Incidents, Graphical Presentation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Designated Team Roles And Responsibilities Business Recovery Plan To Overcome Cyber Security Threat
Designated Team Roles And Responsibilities Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about key roles, responsibilities, and accountability across the different team in the recovery plan. It includes key team such as executive, crisis management, business continuity experts, etc. Deliver an outstanding presentation on the topic using this Designated Team Roles And Responsibilities Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Executive Team, Crisis Management, Business Continuity Expert using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
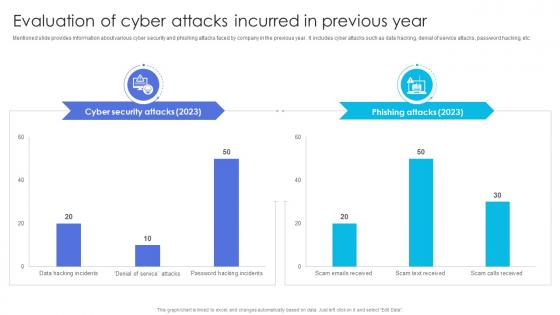 Evaluation Attacks Incurred In Previous Year Business Recovery Plan To Overcome Cyber Security Threat
Evaluation Attacks Incurred In Previous Year Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various cyber security and phishing attacks faced by company in the previous year. It includes cyber attacks such as data hacking, denial of service attacks, password hacking, etc. Deliver an outstanding presentation on the topic using this Evaluation Attacks Incurred In Previous Year Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Information, Service, Evaluation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Incident Status Page For Internal Stakeholders Business Recovery Plan To Overcome Cyber Security Threat
Incident Status Page For Internal Stakeholders Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about incident status page leverage to communicate with internal stakeholders. It includes key elements such as target audience, incident page sample, and best practices. Present the topic in a bit more detail with this Incident Status Page For Internal Stakeholders Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Communication, Stakeholders, Resolution Adopted. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Cyber Threats Management Strategies Business Recovery Plan To Overcome Cyber Security Threat
Major Cyber Threats Management Strategies Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various strategies adopted by company for preventing cyber attacks. It includes key threats such as ransomware, malware, phishing, and denial of service. Deliver an outstanding presentation on the topic using this Major Cyber Threats Management Strategies Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Management, Strategies, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
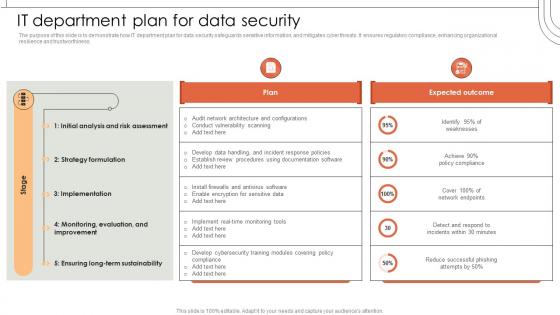 It Department Plan For Data Security
It Department Plan For Data SecurityThe purpose of this slide is to demonstrate how IT department plan for data security safeguards sensitive information, and mitigates cyber threats. It ensures regulatory compliance, enhancing organizational resilience and trustworthiness. Present the topic in a bit more detail with this It Department Plan For Data Security. Use it as a tool for discussion and navigation on Department, Organizational, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Food Safety In Online Budget Allocation For Integrating Advanced System
Securing Food Safety In Online Budget Allocation For Integrating Advanced SystemThis slide covers budget allocation for effective utilization of resources on third party integration, cyber security software and packaging and quality control system. Present the topic in a bit more detail with this Securing Food Safety In Online Budget Allocation For Integrating Advanced System. Use it as a tool for discussion and navigation on Packaging And Quality Control, Cyber Security Systems, Online Order Management Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Food Safety In Online Cloud Based Cyber Security For Third Party Applications
Securing Food Safety In Online Cloud Based Cyber Security For Third Party ApplicationsThis slide covers cloud based cyber security strategies such as vendor ecosystem, security compliance and role based access controls. Present the topic in a bit more detail with this Securing Food Safety In Online Cloud Based Cyber Security For Third Party Applications. Use it as a tool for discussion and navigation on Vendor Ecosystem, Security Compliance, Role Based Access Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Food Safety In Online Statistics To Assess Need Of Outsourcing Food Delivery App
Securing Food Safety In Online Statistics To Assess Need Of Outsourcing Food Delivery AppThis slide covers statistics to assess need of integrating third party platform for delivering food. It involves features such as free and fast delivery or discounts. Present the topic in a bit more detail with this Securing Food Safety In Online Statistics To Assess Need Of Outsourcing Food Delivery App. Use it as a tool for discussion and navigation on Statistics To Assess, Need Outsourcing Food Delivery App. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 US Cyber Security Solution Market Trend For Data Protection
US Cyber Security Solution Market Trend For Data ProtectionThis slide graphically represents market trend of US cyber security solutions for enhancing data protection and mitigating cyber attacks. It includes various growth drivers of solutions such as rising remote work culture, increasing cyber threats, etc. Introducing our US Cyber Security Solution Market Trend For Data Protection set of slides. The topics discussed in these slides are Key Insights, Market Size, Cybersecurity Solutions. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ai Network Security Kpi Dashboard Of Organisation
Ai Network Security Kpi Dashboard Of OrganisationThis slide shows the KPI dashboard after deploying Artificial intelligence in network security to track threat detection and risk compliance. The major KPIs are risk rating breakdown, top threats, and top vulnerabilities. Introducing our Ai Network Security Kpi Dashboard Of Organisation set of slides. The topics discussed in these slides are Dashboard, Organization, Network Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ai Network Security Market In Asia Pacific Region
Ai Network Security Market In Asia Pacific RegionThis slide shows the graphical presentation of the market size of the Asia region using AI advanced technology in network security to overcome the vulnerabilities faced by the organization. Presenting our well structured Ai Network Security Market In Asia Pacific Region. The topics discussed in this slide are Network Security, Rapid Digital Transformation, Growing Cyber Threat Landscape. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Ai Network Security Vulnerabilities By Country
Ai Network Security Vulnerabilities By CountryThis slide shows various countries using AI-driven technology for security through, which they have to favor multiple vulnerabilities.Some vulnerabilities are manipulation of algorithms, stealing confidential information of clients or customers Presenting our well structured Ai Network Security Vulnerabilities By Country. The topics discussed in this slide are Growing Vulnerabilities, Manipulation Of AI Algorithms, Information Of Registered Clients. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Global Artificial Intelligence Network Security Market
Global Artificial Intelligence Network Security MarketThis slide shows the graphical presentation of how overall companies using AI advanced technology in network security to overcome the vulnerabilities faced by the organization Presenting our well structured Global Artificial Intelligence Network Security Market. The topics discussed in this slide are Artificial, Intelligence, Network. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
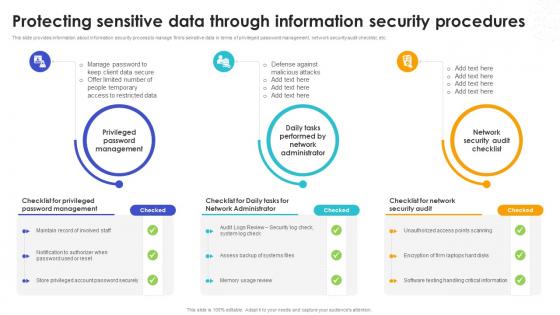 Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SS
Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information about information security process to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc.Introducing Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Audit, Privileged Password Management, Network Administrator, using this template. Grab it now to reap its full benefits.
-
 Dashboard To Monitor OT Cyber Security Parameters
Dashboard To Monitor OT Cyber Security ParametersThis slide represents dashboard that assist companies to trach and monitor their OT cyber security for enhancing data protection. It includes various OT cyber security indicators such as intrusion detection system alert, prohibited traffic allowed, etc. Introducing our Dashboard To Monitor OT Cyber Security Parameters set of slides. The topics discussed in these slides are Restricted Traffic, Over Time By DestinationThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Global Market Size Of OT Cyber Security Solutions
Global Market Size Of OT Cyber Security SolutionsThis slide graphically represents global market size of operating technology OT security solutions to protect them from multiple cyber-risks. It includes various key drivers such as increasing cyber threats, enhancing remote work culture, etc. Presenting our well structured Global Market Size Of OT Cyber Security Solutions The topics discussed in this slide are Cloud Adoption, Global OT Security, Solution Market ValueThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Budget For Identity And Access Management Training Securing Systems With Identity
Budget For Identity And Access Management Training Securing Systems With IdentityThis slide showcases the breakdown cost for the IAM installation and management training for the customers. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor cost, training cost, etc. Present the topic in a bit more detail with this Budget For Identity And Access Management Training Securing Systems With Identity Use it as a tool for discussion and navigation on Components, Training Cost Distribution This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Insights Reporting Dashboard Securing Systems With Identity
Identity And Access Management Insights Reporting Dashboard Securing Systems With IdentityThis slide represents the reporting dashboard of the Identity and Access Management process. The purpose of this slide is to showcase the IAM insights reporting dashboard, and the components include syslog errors, system checks, failed task results, etc. Deliver an outstanding presentation on the topic using this Identity And Access Management Insights Reporting Dashboard Securing Systems With Identity Dispense information and present a thorough explanation of Failed Task Results, Syslog Errors, Certifications Trends using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Us Identity And Access Management Market Size Securing Systems With Identity
Us Identity And Access Management Market Size Securing Systems With IdentityThis slide depicts the US IAM market size in global market. The purpose of this slide is to highlight the US market size of the IAM process in terms of revenue generation and compound annual growth rate. Deliver an outstanding presentation on the topic using this Us Identity And Access Management Market Size Securing Systems With Identity Dispense information and present a thorough explanation of Provisioning Access, Compromising Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Losses Due To Ecommerce Payment Security Frauds
Losses Due To Ecommerce Payment Security FraudsThis slide shows the graphical presentation of ecommerce payment frauds prevails in the world wide enivirment.It is increasing day by day due to lack of strong passwords, data breaches ,etc Presenting our well structured Losses Due To Ecommerce Payment Security Frauds. The topics discussed in this slide are Security Frauds, Ecommerce, Presentation. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Global Security Operation Center Market Size By Region
Global Security Operation Center Market Size By RegionThis slide represents the statistical data for worldwide security operations center market by geographical segmentation that helps to understand the rising potential. It provides insights such as growth factors and market players. Introducing our Global Security Operation Center Market Size By Region set of slides. The topics discussed in these slides are Key Market Players, Growth Factors. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Operation Center Risk Assessment Dashboard
Security Operation Center Risk Assessment DashboardThe following slide illustrates a risk assessment dashboard helps to understand the risk rating breakdown, action plan, top vulnerabilities, etc. of a business. Introducing our Security Operation Center Risk Assessment Dashboard set of slides. The topics discussed in these slides are Risk Assessment Progress, Solved, Action Plan, Risk Rating Breakdown. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Q143 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS V
Q143 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS VThe following slide depicts the percentage of funds raised through security token offerings STOs launched by region. It includes middle east, eastern and western Europe, north America, Oceania, sub Saharan Africa, etc. Present the topic in a bit more detail with this Q143 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS V. Use it as a tool for discussion and navigation on Funds Raised, Sub Saharan, Africa Region. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Training Budget For Seamless Mobile Security Awareness Mobile Security
Training Budget For Seamless Mobile Security Awareness Mobile SecurityThis slide showcases the breakdown cost for mobile security training for the testers which include costs like instructors cost and training materials cost. Deliver an outstanding presentation on the topic using this Training Budget For Seamless Mobile Security Awareness Mobile Security Dispense information and present a thorough explanation of Strengthens Access, Password Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
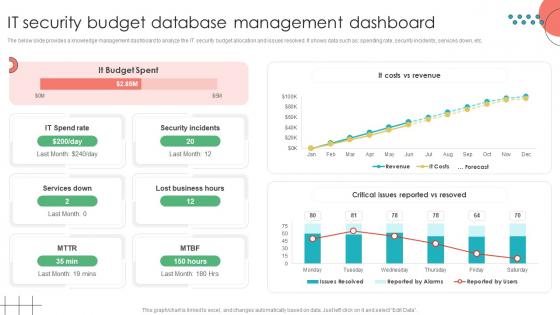 IT Security Budget Database Management Dashboard
IT Security Budget Database Management DashboardThe below slide provides a knowledge management dashboard to analyze the IT security budget allocation and issues resolved. It shows data such as spending rate, security incidents, services down, etc. Presenting our well structured IT Security Budget Database Management Dashboard The topics discussed in this slide are Security Incidents, Lost Business HoursThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Application Security Performance Monitoring And Tracking Dashboard
Application Security Performance Monitoring And Tracking DashboardThis slide showcases the performance tracking dashboard for application security to analyze and monitor security of application. Introducing our Application Security Performance Monitoring And Tracking Dashboard set of slides. The topics discussed in these slides are Discovered Apps, Risk LevelsThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Fintech Cyber Security Tool Investment By Process
Fintech Cyber Security Tool Investment By ProcessThis slide showcases the investment in tools to protect against cyber security. Its aim is to monitor and invest in best tools for securing fintech. This slide includes monitoring, policy, hiring, software, firewall, authentication and encryption. Introducing our Fintech Cyber Security Tool Investment By Process set of slides. The topics discussed in these slides are Fintech, Cyber Security Tool, Investment By Process. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Technological Use Cases Of Fintech Cyber Security
Technological Use Cases Of Fintech Cyber SecurityThis slide graphically represent the best technologies of fintech cyber security industry. Its aim is to manage the best available method for securing the industry. This slide includes cloud, data analytics, cyber security, mobile banking, AI, payments, etc. Introducing our Technological Use Cases Of Fintech Cyber Security set of slides. The topics discussed in these slides are . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Current Frauds Attacks Faced By Ecommerce Business Implementing E Commerce Security Measures
Current Frauds Attacks Faced By Ecommerce Business Implementing E Commerce Security MeasuresThis slide portrays the common types of fraud attacks experienced by ecommerce businesses in recent years. It include frauds such as card testing, phishing, account takeover and the reason of attacks. Deliver an outstanding presentation on the topic using this Current Frauds Attacks Faced By Ecommerce Business Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Poor Website Security, In Frequent Monitoring, Secure Payment Verification using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
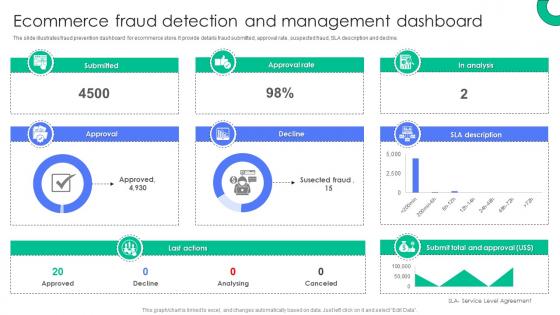 Ecommerce Fraud Detection And Management Dashboard Implementing E Commerce Security Measures
Ecommerce Fraud Detection And Management Dashboard Implementing E Commerce Security MeasuresThe slide illustrates fraud prevention dashboard for ecommerce store. It provide details fraud submitted, approval rate, suspected fraud, SLA description and decline. Present the topic in a bit more detail with this Ecommerce Fraud Detection And Management Dashboard Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Submitted, Approval, Approval Rate, Decline, Last Actions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
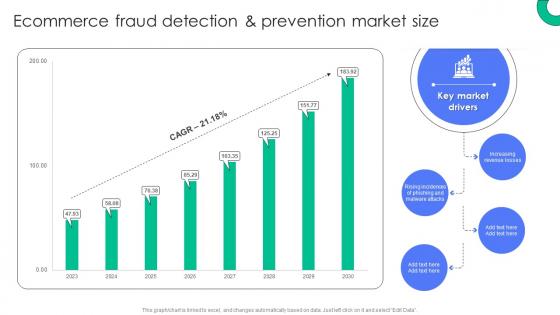 Ecommerce Fraud Detection And Prevention Market Size Implementing E Commerce Security Measures
Ecommerce Fraud Detection And Prevention Market Size Implementing E Commerce Security MeasuresDeliver an outstanding presentation on the topic using this Ecommerce Fraud Detection And Prevention Market Size Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Increasing Revenue Losses, Key Market, Drivers, Malware Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
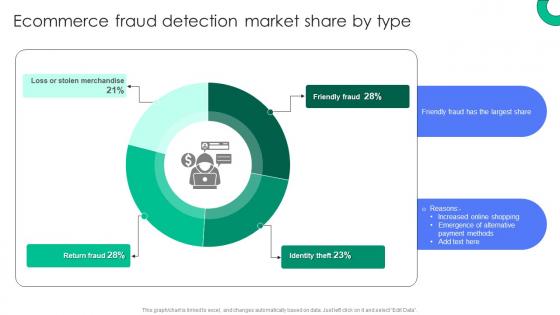 Ecommerce Fraud Detection Market Share By Type Implementing E Commerce Security Measures
Ecommerce Fraud Detection Market Share By Type Implementing E Commerce Security MeasuresPresent the topic in a bit more detail with this Ecommerce Fraud Detection Market Share By Type Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Identity Theft, Friendly Fraud, Return Fraud. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ecommerce Fraud Impact On Business Operations Implementing E Commerce Security Measures
Ecommerce Fraud Impact On Business Operations Implementing E Commerce Security MeasuresThis slide represents the impact of fraud attacks on ecommerce companies. It provide information about chargeback fee, high network fee, delayed expansion or investment. Deliver an outstanding presentation on the topic using this Ecommerce Fraud Impact On Business Operations Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Card Payment, Manage Fraud, Businesses Delay Investment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Effective Ways To Monitor Transaction Patterns Implementing E Commerce Security Measures
Effective Ways To Monitor Transaction Patterns Implementing E Commerce Security MeasuresThe slide highlights the ways to track and analyze transaction patterns and log in attempts. It provide details about risk scoring, real time monitoring, account monitoring and behavioral analytics.Present the topic in a bit more detail with this Effective Ways To Monitor Transaction Patterns Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Account Monitoring, Behavioral Analytics, Real Time Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Impact Of Ecommerce Fraud On Business Implementing E Commerce Security Measures
Financial Impact Of Ecommerce Fraud On Business Implementing E Commerce Security MeasuresThis slide showcases financial challenges faced by the company related to cybersecurity attacks, referable for businesses facing similar situation. It cover losses caused due to lack of awareness about attacks. Present the topic in a bit more detail with this Financial Impact Of Ecommerce Fraud On Business Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Key Insights, Ecommerce Business, Key Reasons. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Fraud Prevention Strategies Impact On Financial Losses Implementing E Commerce Security Measures
Fraud Prevention Strategies Impact On Financial Losses Implementing E Commerce Security MeasuresThe slide showcases post impact of ecommerce fraud prevention strategy on buisness losses. It include reasons for decreasing losses such as compliant monitoring and auditing.Deliver an outstanding presentation on the topic using this Fraud Prevention Strategies Impact On Financial Losses Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Ecommerce Business, Key Insights, Compliant Monitoring using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Multifactor Authentication Methods To Prevent Fraud Implementing E Commerce Security Measures
Key Multifactor Authentication Methods To Prevent Fraud Implementing E Commerce Security MeasuresThe slide outlines major multifactor authentication methods to safeguard ecommerce stores. It include details about knowledge factors, possession factor along with potential impact. Present the topic in a bit more detail with this Key Multifactor Authentication Methods To Prevent Fraud Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Information Inherent, Potential Impact, Reduced Suspicious Logins. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Post Impact Analysis Of Ecommerce Fraud Strategies Implementing E Commerce Security Measures
Post Impact Analysis Of Ecommerce Fraud Strategies Implementing E Commerce Security MeasuresThis slide depicts the fraud prevention strategies impact on ecommerce company. It covers frauds such as phishing, friendly fraud, identify theft, account takeover etc. Deliver an outstanding presentation on the topic using this Post Impact Analysis Of Ecommerce Fraud Strategies Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Poor Website Security, In Frequent Monitoring, Secure Payment Verification using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Areas Contributing To Data Breach In Banking Cyber Security
Areas Contributing To Data Breach In Banking Cyber SecurityThis slide represents areas where banks are most vulnerable to cyber security breach. It aims toincrease need for cyber security as part of design architecture aiming to detect emerging attacks in real-time. It includes various constituents such as web apps, card skimmers, etc. Presenting our well structured Areas Contributing To Data Breach In Banking Cyber Security. The topics discussed in this slide are Vectors Of Attack, Key Insights, Avoid Public. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Dashboard To Enhance Cyber Security In Banking Sector
Dashboard To Enhance Cyber Security In Banking SectorThis slide represents dashboard to improve cyber security in financial industry. This slide aims to proactively address security threats and vulnerabilities in banking sector. It includes various elements such as banking health risk, secured payments by year, etc. Introducing our Dashboard To Enhance Cyber Security In Banking Sector set of slides. The topics discussed in these slides are Attacks, Cyber Security Risks, Recent Campaigns. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.





