Powerpoint Templates and Google slides for Secure internet
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Internet Gateway Security IT Powerpoint Presentation Slides
Internet Gateway Security IT Powerpoint Presentation SlidesThis complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of eighty five slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
-
 Internet Of Things IoT Security Powerpoint Presentation Slides Cybersecurity CD
Internet Of Things IoT Security Powerpoint Presentation Slides Cybersecurity CDDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Internet Of Things IoT Security Powerpoint Presentation Slides Cybersecurity CD is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fifty nine slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Wireless Internet Security Powerpoint Ppt Template Bundles
Wireless Internet Security Powerpoint Ppt Template BundlesEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Wireless Internet Security Powerpoint Ppt Template Bundles is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With fifteen this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
 Security Lock Internet Safety Desktop Monitor Network Through Financial
Security Lock Internet Safety Desktop Monitor Network Through FinancialEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Security Lock Internet Safety Desktop Monitor Network Through Financial is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With fourteen slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
 Internet Of Things Security Global Market Size IoT Security And Privacy Safeguarding IoT SS
Internet Of Things Security Global Market Size IoT Security And Privacy Safeguarding IoT SSThis slide showcases a graphical representation of IoT securitys global market size. It includes various growth drivers such as the growing number of IoT devices in market and rise in malware attacks to infect enterprise IoT devices.Deliver an outstanding presentation on the topic using this Internet Of Things Security Global Market Size IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Security Global Market, American Region, Rise Malware Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
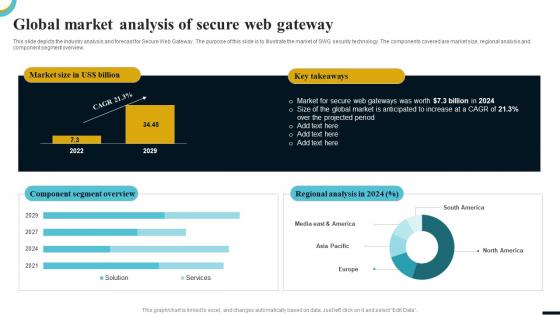 Internet Gateway Security IT Global Market Analysis Of Secure Web Gateway
Internet Gateway Security IT Global Market Analysis Of Secure Web GatewayThis slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview. Present the topic in a bit more detail with this Internet Gateway Security IT Global Market Analysis Of Secure Web Gateway. Use it as a tool for discussion and navigation on Component Segment Overview, Regional Analysis, Market Size. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
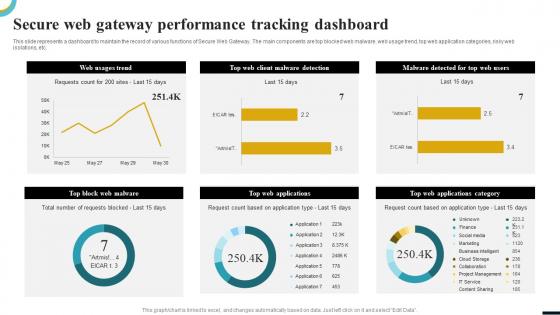 Internet Gateway Security IT Secure Web Gateway Performance Tracking
Internet Gateway Security IT Secure Web Gateway Performance TrackingThis slide represents a dashboard to maintain the record of various functions of Secure Web Gateway. The main components are top blocked web malware, web usage trend, top web application categories, risky web isolations, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Secure Web Gateway Performance Tracking. Use it as a tool for discussion and navigation on Web Usages Trend, Top Block Web Malware, Top Web Applications, Top Web Applications Category, Top Web Client Malware Detection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Wireless Internet Security Us Market Size By Deployment
Wireless Internet Security Us Market Size By DeploymentThe following slide presents data on expected CAGR, deployment methods cloud, on-premise, security adoption trends, and more to depict the size and dynamics of the wireless internet security market in the United States, aiding in market analysis and decision-making. Presenting our well structured Wireless Internet Security Us Market Size By Deployment. The topics discussed in this slide are Deployment, Professional, Growth. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Avoid Unnecessary Data Access Storage And Transmission Internet Of Things IoT Security Cybersecurity SS
Avoid Unnecessary Data Access Storage And Transmission Internet Of Things IoT Security Cybersecurity SSThis slide showcases avoiding unnecessary resources on internet of things IoT devices, helping developers avoid transmission and storage costs. It provides details about data classification, compliance, etc. Deliver an outstanding presentation on the topic using this Avoid Unnecessary Data Access Storage And Transmission Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Privacy And Compliance Considerations, Data Privacy And Compliance, Data Access Storage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Business Survey Highlighting Common IoT Security Threats Internet Of Things IoT Security Cybersecurity SS
Business Survey Highlighting Common IoT Security Threats Internet Of Things IoT Security Cybersecurity SSThis slide showcases common internet of things IoT threats in the company, referable for related businesses. It provides details about network scan, command injection, SQL, zero-day, etc. Present the topic in a bit more detail with this Business Survey Highlighting Common IoT Security Threats Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on Cyber Security Awareness, Quality Threat Modeling Tools, Weak Passwords, Authentication Practices. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard Showcasing Security Status Of IoT Devices Internet Of Things IoT Security Cybersecurity SS
Dashboard Showcasing Security Status Of IoT Devices Internet Of Things IoT Security Cybersecurity SSThis slide showcases dashboard for security status of deployed internet of things IoT devices. It provides details about connected sites, IP address, vulnerabilities, critical firmware, etc. Deliver an outstanding presentation on the topic using this Dashboard Showcasing Security Status Of IoT Devices Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Dashboard, Security Status, IoT Devices, Vulnerabilities, Critical Firmware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact Analysis Of IoT Security Strategies Internet Of Things IoT Security Cybersecurity SS
Impact Analysis Of IoT Security Strategies Internet Of Things IoT Security Cybersecurity SSThis slide showcases impact analysis for deployed internet of things IoT security tools and strategies. It provides details about IoT ransomware, user privacy, insecure interfaces, remote work attacks, etc. Present the topic in a bit more detail with this Impact Analysis Of IoT Security Strategies Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on Internet Of Things, Security Tools And Strategies, IoT Ransomware, Remote Work Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Cyber Security Budget Plan Internet Of Things IoT Security Cybersecurity SS
IoT Cyber Security Budget Plan Internet Of Things IoT Security Cybersecurity SSThis slide showcases security budget plan for internet of things IoT operations. It provides details about secure data transmission, reduce attack surface, add features from gateways, understand data, etc. Present the topic in a bit more detail with this IoT Cyber Security Budget Plan Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on IoT Cyber Security, Budget Plan, Reduce Attack Surface, Internet Of Things. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Security Market Size Analysis Internet Of Things IoT Security Cybersecurity SS
IoT Security Market Size Analysis Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security market analysis snapshot, referable for related businesses and investors. It provides details about industry 4.0, vulnerabilities, cyber resilience, etc. Present the topic in a bit more detail with this IoT Security Market Size Analysis Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on IoT Security, Market Size Analysis, Internet Of Things, Vulnerabilities, Cyber Resilience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Minimize The Attack Surface Of Your IoT Ecosystem Internet Of Things IoT Security Cybersecurity SS
Minimize The Attack Surface Of Your IoT Ecosystem Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of attack surface minimization on internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about unused points, configuration, etc. Deliver an outstanding presentation on the topic using this Minimize The Attack Surface Of Your IoT Ecosystem Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Eliminate Unused Points, System Security, Exploitation Opportunities, Probability Of Unauthorized Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Career internet security ppt powerpoint presentation visual aids pictures cpb
Career internet security ppt powerpoint presentation visual aids pictures cpbPresenting Career Internet Security Ppt Powerpoint Presentation Visual Aids Pictures Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Career Internet Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Iot Ecosystem Security Challenges With Example Introduction To Internet Of Things IoT SS
Iot Ecosystem Security Challenges With Example Introduction To Internet Of Things IoT SSThis slide highlights common security challenges that may arise in the internet of things ecosystem. It includes challenges related to IoT devices, cloud services, and connections. Present the topic in a bit more detail with this Iot Ecosystem Security Challenges With Example Introduction To Internet Of Things IoT SS. Use it as a tool for discussion and navigation on Challenges, Categories. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Iot Gateway Security Best Practices Introduction To Internet Of Things IoT SS
Iot Gateway Security Best Practices Introduction To Internet Of Things IoT SSThis slide highlights ways to secure IoT gateway to eliminate data breach and leakage. Some of the best practices include edge based security, decentralised infrastructure, performance assessment, and gateway updates. Introducing Iot Gateway Security Best Practices Introduction To Internet Of Things IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Edge Based Security, Decentralised Infrastructure, using this template. Grab it now to reap its full benefits.
-
 Iot Security Architecture Principles On Device Layer Introduction To Internet Of Things IoT SS
Iot Security Architecture Principles On Device Layer Introduction To Internet Of Things IoT SSThis slide exhibits security architecture principles on device and communication layer. It showcases iot ecosystem elements such as user, devices, gateway, connection, cloud, and applications. Present the topic in a bit more detail with this Iot Security Architecture Principles On Device Layer Introduction To Internet Of Things IoT SS. Use it as a tool for discussion and navigation on Iot Solution Elements, Important Security Principles. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Iot Security Best Practices To Secure Connected Introduction To Internet Of Things IoT SS
Iot Security Best Practices To Secure Connected Introduction To Internet Of Things IoT SSThis slide includes best practices to secure overall infrastructure from potential threats. These best practices include device authentication, data encryption, firmware updates, and network segmentation. Introducing Iot Security Best Practices To Secure Connected Introduction To Internet Of Things IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Device Authentication, Data Encryption, using this template. Grab it now to reap its full benefits.
-
 Iot Security Overview And Key Statistics Introduction To Internet Of Things IoT SS
Iot Security Overview And Key Statistics Introduction To Internet Of Things IoT SSThis slide exhibits a brief introduction to IoT security and major statistics showcasing the rising need for security in connected devices. It covers detailed information about market size, number of cyber attacks, and cyber attack duration. Increase audience engagement and knowledge by dispensing information using Iot Security Overview And Key Statistics Introduction To Internet Of Things IoT SS. This template helps you present information on three stages. You can also present information on Security Market, Experience Cyber using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security And Privacy Concerns In Internet Of Things Introduction To Internet Of Things IoT SS
Security And Privacy Concerns In Internet Of Things Introduction To Internet Of Things IoT SSThis slide exhibits data security and privacy concerns with the adoption of IoT enabled devices. These concerns include inadequate password defense, limited compliance, absence of secure interfaces, a large amount of data, eavesdropping, and involuntary public exposure. Introducing Security And Privacy Concerns In Internet Of Things Introduction To Internet Of Things IoT SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Inadequate Password Defence, Limited Compliance, using this template. Grab it now to reap its full benefits.
-
 Top Internet Security Programs In Powerpoint And Google Slides Cpb
Top Internet Security Programs In Powerpoint And Google Slides CpbPresenting our Top Internet Security Programs In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Technologies Data Intensive Computing. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Internet Security ETF In Powerpoint And Google Slides Cpb
Internet Security ETF In Powerpoint And Google Slides CpbPresenting our Internet Security ETF In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Internet Security ETF. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Internet Security Attack Targets In Powerpoint And Google Slides Cpb
Internet Security Attack Targets In Powerpoint And Google Slides CpbPresenting Internet Security Attack Targets In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Internet Security Attack Targets. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Encryption Implementation Strategies Key Components Of Internet Protocol Security
Encryption Implementation Strategies Key Components Of Internet Protocol SecurityThe purpose of this slide is to discuss the main components of internet protocol security IPsec architecture. These three components are encapsulating security payload ESP, authentication header AH, and internet key exchange IKE. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Key Components Of Internet Protocol Security. Dispense information and present a thorough explanation of Data Integrity, Encryption, Anti Replay, Payload Authentication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Steps Followed By Internet Protocol Security Connections
Encryption Implementation Strategies Steps Followed By Internet Protocol Security ConnectionsThe purpose of this slide is to outline the working steps of internet protocol security connections. These are key exchange, packet headers and trailers, packet authentication, encryption, data transmission and decryption of data packets. Present the topic in a bit more detail with this Encryption Implementation Strategies Steps Followed By Internet Protocol Security Connections. Use it as a tool for discussion and navigation on Protocol Security Connections, Packet Authentication, Encryption, Data Transmission, Decryption Of Data Packets. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Issues Internet Things Encryption In Powerpoint And Google Slides Cpb
Security Issues Internet Things Encryption In Powerpoint And Google Slides CpbPresenting Security Issues Internet Things Encryption In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Issues Internet Things Encryption. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber Security Internet Computer In Powerpoint And Google Slides Cpb
Cyber Security Internet Computer In Powerpoint And Google Slides CpbPresenting our Cyber Security Internet Computer In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cyber Security Internet Computer. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Industrial Internet Of Things Iiot Security Architecture Guide Of Integrating Industrial Internet
Industrial Internet Of Things Iiot Security Architecture Guide Of Integrating Industrial InternetThis slide covers industrial internet of things security architecture. It involves key technologies such as integrity scanning, machine learning, behavior analysis, anti malware and risk detection. Present the topic in a bit more detail with this Industrial Internet Of Things Iiot Security Architecture Guide Of Integrating Industrial Internet. Use it as a tool for discussion and navigation on Integration, Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Players Of Internet Of Things Security Improving IoT Device Cybersecurity IoT SS
Key Players Of Internet Of Things Security Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase top companies of Internet of Things IoT cybersecurity market. The companies are classified on the basis of well established and startups. The major industry leaders are Cisco, Microsoft Corporation, Amazon Web Services AWS, Trend Micro, Splunk, etc. Deliver an outstanding presentation on the topic using this Key Players Of Internet Of Things Security Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Microsoft, Services, Companies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Internet Things Security Policy In Powerpoint And Google Slides Cpb
Internet Things Security Policy In Powerpoint And Google Slides CpbPresenting Internet Things Security Policy In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Internet Things Security Policy. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Budget Securing Tips For Public Relations Internet Marketing Strategies MKT SS V
Budget Securing Tips For Public Relations Internet Marketing Strategies MKT SS VThis slide shows various tips which can be used by organizations to while developing marketing budget. It includes aligning marketing outcome with organizational goals, strategic insights Deliver an outstanding presentation on the topic using this Budget Securing Tips For Public Relations Internet Marketing Strategies MKT SS V. Dispense information and present a thorough explanation of Budget Considering, Connect Outcomes, Impacts Allocating using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Establish Effective Internet Security Protocols In Network Layer
Establish Effective Internet Security Protocols In Network LayerThis slide exhibits network layer security architecture for providing virtual private network between two locations. It includes protocols such as encapsulating security payload, authentication header and internet key exchange. Presenting our set of slides with Establish Effective Internet Security Protocols In Network Layer. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication Header, Authentication Methods, Encapsulating Security Payload.
-
 Firewall Network Security IP Internet Protocol Reputation Function In NGFW
Firewall Network Security IP Internet Protocol Reputation Function In NGFWThis slide outlines the overview of the IP Reputation function used in Next Generation Firewalls. The purpose of this slide is to introduce the Internet Protocol IP reputation, including its features and limitations. This function blocks network traffic based on the reputation score of Ips. Introducing Firewall Network Security IP Internet Protocol Reputation Function In NGFW to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Policy Enforcement, Network Visibility, Streamlined Adaptability using this template. Grab it now to reap its full benefits.
-
 Various Types Of DDoS Attacks Impacting Internet Traffic Hands On Blockchain Security Risk BCT SS V
Various Types Of DDoS Attacks Impacting Internet Traffic Hands On Blockchain Security Risk BCT SS VThe following slide showcases various types of denial of service DDOS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc. Introducing Various Types Of DDoS Attacks Impacting Internet Traffic Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Volumetric Attacks, Protocol Attacks, Application Attacks, using this template. Grab it now to reap its full benefits.
-
 About Internet Protocol Security Overview And Uses Encryption For Data Privacy In Digital Age It
About Internet Protocol Security Overview And Uses Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the role and functionality of IPsec Internet Protocol Security in securing connections between devices. This slide also outlines the uses of IPsec such as protecting data during transmission over open networks, use in building VPNs, etc. Deliver an outstanding presentation on the topic using this About Internet Protocol Security Overview And Uses Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Overview, Protocol Security, Destination using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Benefits Of Internet Protocol Security Encryption For Data Privacy In Digital Age It
Benefits Of Internet Protocol Security Encryption For Data Privacy In Digital Age ItThis slide demonstrates the advantages and disadvantages of Internet protocol Security IPsec technology. The various benefits explained in this slide are strong security, broad compatibility, flexibility, scalability and efficient network performance. Deliver an outstanding presentation on the topic using this Benefits Of Internet Protocol Security Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Key Management, Performance Impact, Compatibility Issues using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Characteristics Of Internet Protocol Security Technique Encryption For Data Privacy In Digital Age It
Characteristics Of Internet Protocol Security Technique Encryption For Data Privacy In Digital Age ItThis slide demonstrates the various features of Internet Protocol Security IPsec mechanism. The properties of IPsec include authentication, privacy, integrity, key management, tunnelling, flexibility and interoperability. Introducing Characteristics Of Internet Protocol Security Technique Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Key Management, Interoperability, using this template. Grab it now to reap its full benefits.
-
 Internet Protocol Security Architecture And Working Encryption For Data Privacy In Digital Age It
Internet Protocol Security Architecture And Working Encryption For Data Privacy In Digital Age ItThis slide demonstrates the working of Internet Protocol Security. The main components of IPsec architecture are ESP protocol, AH protocol, encryption algorithm, authentication algorithm, key management, etc. Present the topic in a bit more detail with this Internet Protocol Security Architecture And Working Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Protocol Security, Architecture, Encryption Algorithm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Components Of Internet Protocol Security Encryption For Data Privacy In Digital Age It
Key Components Of Internet Protocol Security Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to discuss the main components of Internet Protocol Security IPsec architecture. These three components are Encapsulating Security Payload ESP, Authentication Header AH, and Internet Key Exchange IKE. Deliver an outstanding presentation on the topic using this Key Components Of Internet Protocol Security Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Authentication Header, Internet Key Exchange, Encapsulating Security Payload using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps Followed By Internet Protocol Security Connections Encryption For Data Privacy In Digital Age It
Steps Followed By Internet Protocol Security Connections Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to outline the working steps of Internet Protocol Security connections. These are key exchange, packet headers and trailers, packet authentication, encryption, data transmission and decryption of data packets. Deliver an outstanding presentation on the topic using this Steps Followed By Internet Protocol Security Connections Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Connections, Protocol Security, Data Transmission using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tunnel And Transport Modes Of Internet Protocol Security Encryption For Data Privacy In Digital Age It
Tunnel And Transport Modes Of Internet Protocol Security Encryption For Data Privacy In Digital Age ItThis slide talks about the distinction between the two methods of protecting information transmission. The purpose of this slide is to explain the concepts of transport mode and tunnel mode in the context of securing data during communication. Present the topic in a bit more detail with this Tunnel And Transport Modes Of Internet Protocol Security Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Transport Mode, Protocol Security, Transmission. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Issue Internet Account In Powerpoint And Google Slides Cpb
Security Issue Internet Account In Powerpoint And Google Slides CpbPresenting Security Issue Internet Account In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Issue Internet Account. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Agenda For Internet Gateway Security IT
Agenda For Internet Gateway Security ITIntroducing Agenda For Internet Gateway Security IT to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Global Market Analysis, Remote Worker Protection, Integrate Secure Web Gateway, Technologies, using this template. Grab it now to reap its full benefits.
-
 Comparison Between Secure Web Internet Gateway Security IT
Comparison Between Secure Web Internet Gateway Security ITThis slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. Present the topic in a bit more detail with this Comparison Between Secure Web Internet Gateway Security IT. Use it as a tool for discussion and navigation on Parameter, Scope, Deployment, Architecture, Features, Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide For Internet Gateway Security IT
Icons Slide For Internet Gateway Security ITIntroducing our well researched set of slides titled Icons Slide For Internet Gateway Security IT. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
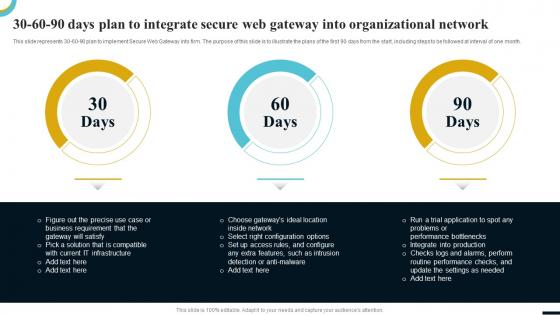 Internet Gateway Security IT 30 60 90 Days Plan To Integrate Secure Web
Internet Gateway Security IT 30 60 90 Days Plan To Integrate Secure WebThis slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Introducing Internet Gateway Security IT 30 60 90 Days Plan To Integrate Secure Web to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on 30 60 90 Days Plan, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Applications Of Secure Web Gateway In Various
Internet Gateway Security IT Applications Of Secure Web Gateway In VariousThis slide talks about how Secure Web Gateway is used in several industrial domains. The purpose of this slide is to explain how SWG is used in different sectors. The industries covered are financial services, healthcare, education, manufacturing, etc. Introducing Internet Gateway Security IT Applications Of Secure Web Gateway In Various to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Financial Services, Healthcare, Education, Manufacturing, Government, Retail, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Architecture Of Citrix Secure Web Gateway
Internet Gateway Security IT Architecture Of Citrix Secure Web GatewayThis slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Architecture Of Citrix Secure Web Gateway. Use it as a tool for discussion and navigation on Citrix ADC Appliance, URL Filtering, Policies, Citrix Application Delivery Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Before Vs After Implementing Secure Web
Internet Gateway Security IT Before Vs After Implementing Secure WebThis slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Before Vs After Implementing Secure Web. Use it as a tool for discussion and navigation on Security, Visibility, Compliance, Productivity, Costs. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Best Practices For Secure Web Gateway
Internet Gateway Security IT Best Practices For Secure Web GatewayThis slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. Introducing Internet Gateway Security IT Best Practices For Secure Web Gateway to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Perform A Risk Assessment, Deploy Safe Setups, Monitor And Analyse Traffic, Keep Software Up To Date, Provide User Awareness Training, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Case Study Citrix Solutions To Safeguard
Internet Gateway Security IT Case Study Citrix Solutions To SafeguardThis slide depicts the services offered by Citrix solutions to protect networks from web-based threats. These are comprehensive SWG, more private architecture based on instances and cloud delivery. This slide also talks about the benefits of SWG to IT directors. Introducing Internet Gateway Security IT Case Study Citrix Solutions To Safeguard to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Comprehensive SWG, Cloud Delivery, Secure Web Gateway Services, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Checklist To Implement Secure Web Gateway
Internet Gateway Security IT Checklist To Implement Secure Web GatewayThis slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Present the topic in a bit more detail with this Internet Gateway Security IT Checklist To Implement Secure Web Gateway. Use it as a tool for discussion and navigation on Determine Use Case, Select Best Solution, Plan Deployment, Configure Solution, Test And Improve, Roll Out And Monitor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Comparison Between Secure Web Gateway
Internet Gateway Security IT Comparison Between Secure Web GatewayThis slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment. Present the topic in a bit more detail with this Internet Gateway Security IT Comparison Between Secure Web Gateway. Use it as a tool for discussion and navigation on Function, Scope, Granularity, Features, Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Current Trends Enhancing Performance
Internet Gateway Security IT Current Trends Enhancing PerformanceThis slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc. Introducing Internet Gateway Security IT Current Trends Enhancing Performance to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Based SWG, Advanced Threat Protection, User Behavior Analytics, Secure Access Service Edge, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Different Types Of Secure Web Gateway
Internet Gateway Security IT Different Types Of Secure Web GatewayThis slide demonstrates the various kinds of SWG deployments. The purpose of this slide is to explain the different types of Secure Web Gateway deployment methods such as on-premises deployment, cloud-based deployment and hybrid deployment. Introducing Internet Gateway Security IT Different Types Of Secure Web Gateway to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on On Premises Deployment, CLOUD Based Deployment, Hybrid Deployment, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Estimated Budget Of Secure Web Gateway
Internet Gateway Security IT Estimated Budget Of Secure Web GatewayThis slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Estimated Budget Of Secure Web Gateway. Use it as a tool for discussion and navigation on Hardware And Software, Maintenance And Support, Training, Third Party Services, Deployment Team. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Features Of Next Generation Secure Web
Internet Gateway Security IT Features Of Next Generation Secure WebThis slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc. Introducing Internet Gateway Security IT Features Of Next Generation Secure Web to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Based Architecture, More Visibility And Control, Advanced Threat Intelligence, Multi-Factor Authentication, Integrated Data Loss Prevention, Zero Trust Security, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Future Of Secure Web Gateway Technology
Internet Gateway Security IT Future Of Secure Web Gateway TechnologyThis slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. Introducing Internet Gateway Security IT Future Of Secure Web Gateway Technology to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Sales Are Predicted, SWG Market Anticipated, Security Solution, using this template. Grab it now to reap its full benefits.




