Powerpoint Templates and Google slides for Secure Environment
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Security Architecture Review Of A Cloud Native Environment Powerpoint Presentation Slides
Security Architecture Review Of A Cloud Native Environment Powerpoint Presentation SlidesThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Security Architecture Review Of A Cloud Native Environment Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of Twenty Four slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Physical Security And Environmental Controls In Cybersecurity Training Ppt
Physical Security And Environmental Controls In Cybersecurity Training PptPresenting Physical Security and Environmental Controls in Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Objectives Of Physical Security And Environmental Controls Training Ppt
Objectives Of Physical Security And Environmental Controls Training PptPresenting Objectives of Physical Security and Environmental Controls. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Protect Icon Financial Investment Business Insurance Environment Security
Protect Icon Financial Investment Business Insurance Environment SecurityDeliver a credible and compelling presentation by deploying this Protect Icon Financial Investment Business Insurance Environment Security. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twelve slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Protect Icon Financial Investment Business Insurance Environment Security PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
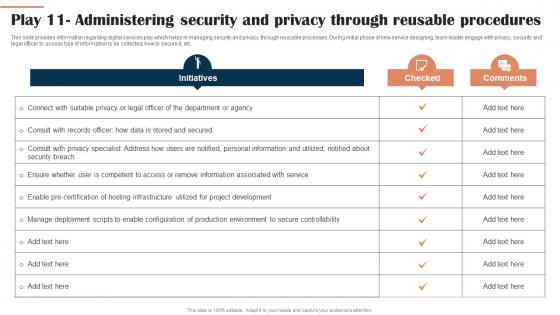 Play 11 Administering Security And Privacy Through Digital Hosting Environment Playbook
Play 11 Administering Security And Privacy Through Digital Hosting Environment PlaybookThis slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. Deliver an outstanding presentation on the topic using this Play 11 Administering Security And Privacy Through Digital Hosting Environment Playbook. Dispense information and present a thorough explanation of Deployment, Configuration, Environment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Step 3 Assess The Environment Zero Trust Security Model
Step 3 Assess The Environment Zero Trust Security ModelThis slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Deliver an outstanding presentation on the topic using this Step 3 Assess The Environment Zero Trust Security Model. Dispense information and present a thorough explanation of Knowledge, Categorizations, Structures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Devsecops Best Practices For Secure Environment And Data Security For Devsecops Process
Devsecops Best Practices For Secure Environment And Data Security For Devsecops ProcessThis slide discusses the environment and data security for DevSecOps. The purpose of this slide is to highlight the process, including standardizing and automating the environment, centralizing user identity and access control, isolating containers for security, and so on. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Environment And Data Security For Devsecops Process. Use it as a tool for discussion and navigation on Standardize And Automate Environment, Isolate Containers For Security, Encrypt Data Transmission. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Network Security Attacks In IoT Environment IoT Security And Privacy Safeguarding IoT SS
Overview Of Network Security Attacks In IoT Environment IoT Security And Privacy Safeguarding IoT SSThis slide presents an overview and types of network security threats, helpful in identifying potential risks in IoT networked environments. It includes attacks such as man in middle attacks, RFIS spoofing, sinkhole attacks, and traffic analysis attacks. Introducing Overview Of Network Security Attacks In IoT Environment IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Communication Nodes, Mimics Legitimate, Malicious Destination, using this template. Grab it now to reap its full benefits.
-
 Different Security Layers In Sql Server Environments
Different Security Layers In Sql Server EnvironmentsFollowing slide showcases SQL server security layers, also including layers such as physical security, network security, database security, application security and operating system security, etc. Introducing our premium set of slides with Different Security Layers In Sql Server Environments. Ellicudate the fivestages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Physical Security, Network Security, Operating System Security. So download instantly and tailor it with your information.
-
 Hypervisor security considerations to maintain virtualized environment
Hypervisor security considerations to maintain virtualized environmentThis slide covers security considerations for hypervisor such as hypervisor vulnerabilities, access control, network security etc. to manage virtualization process.Presenting our set of slides with Hypervisor security considerations to maintain virtualized environment This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Hypervisor Vulnerabilities, Secure Management Interfaces, Network Security.
-
 Containerization Technology Security Best Practices To Protect Containerized Environments
Containerization Technology Security Best Practices To Protect Containerized EnvironmentsThis slide outlines the best practices for securing containerized environments. The purpose of this slide is to define the security best practices for organizations to protect containerized environments, and these are securing images, securing registries, securing deployments, and so on. Deliver an outstanding presentation on the topic using this Containerization Technology Security Best Practices To Protect Containerized Environments. Dispense information and present a thorough explanation of Securing Registries, Securing Deployment, Securing Container Runtime, Securing Kubernetes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Infrastructure Security Testing In Multiple Environment
Infrastructure Security Testing In Multiple EnvironmentThis slide showcases the security infrastructure in different environment. Its aim is to manage the services for better security system with saas. This slide includes cloud service, mobile worker, data center and office. Introducing our premium set of slides with Infrastructure Security Testing In Multiple Environment. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Service, Worker, Center. So download instantly and tailor it with your information.
-
 Security Vulnerabilities In Smart Home Environment
Security Vulnerabilities In Smart Home EnvironmentFollowing slide represents smart home environment security vulnerabilities for prevention of breaches. It further covers internet gateway, smart lightning, remote access, video surveillance camera, access panel, etc. Introducing our Security Vulnerabilities In Smart Home Environment set of slides. The topics discussed in these slides are Internet Gateway, Video Surveillance Camera, Access PanelThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Secure trading environment ppt images
Secure trading environment ppt imagesPresenting secure trading environment ppt images. This is a secure trading environment ppt images. This is a two stage process. The stages in this process are sell routes, multiple customers, secured payments, single contract, multiple suppliers, one interconnect, buy routes, tel trade.
-
 Environments best suited for efficient and secure supply chains ppt rules
Environments best suited for efficient and secure supply chains ppt rulesThis slide shows the environment best suited for efficient and secure supply chain which includes various factors such as operations strategy, investment lead time, etc. Present the topic in a bit more detail with this Environments Best Suited For Efficient And Secure Supply Chains Ppt Rules. Use it as a tool for discussion and navigation on Supply Chains, Operations Strategy, Inventory Investment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Roles and responsibilities to ensure work environment with corporate security management
Roles and responsibilities to ensure work environment with corporate security managementThis slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. Increase audience engagement and knowledge by dispensing information using Roles And Responsibilities To Ensure Work Environment With Corporate Security Management. This template helps you present information on four stages. You can also present information on Employee Responsibilities, Manager Responsibilities, Unit Responsibilities, Human Resources Responsibilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Safe And Secure Banking Environment For Payments Icon
Safe And Secure Banking Environment For Payments IconIntroducing our premium set of slides with Safe And Secure Banking Environment For Payments Icon. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Safe And Secure Banking Environment For Payments Icon. So download instantly and tailor it with your information.
-
 Cyber security risk management roles and responsibilities ensure work environment
Cyber security risk management roles and responsibilities ensure work environmentThis slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Roles And Responsibilities Ensure Work Enviro. This template helps you present information on four stages. You can also present information on Employee Responsibilities, Unit Supervisor, Manager Responsibilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enhancing overall project security it roles and responsibilities to ensure work environment
Enhancing overall project security it roles and responsibilities to ensure work environmentThis slide provides information regarding roles and responsibilities assigned to ensure minimum violence work environment. Introducing Enhancing Overall Project Security It Roles And Responsibilities To Ensure Work Environment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Environment, Responsibilities, Resources, using this template. Grab it now to reap its full benefits.
-
 Cloud Architecture And Security Multi Cloud It Environments After Implementing Solutions
Cloud Architecture And Security Multi Cloud It Environments After Implementing SolutionsThis slide covers the running all the workloads on a variety of clouds including public cloud, third party public clouds, hosted private clouds, and colocation servers while managing them. Increase audience engagement and knowledge by dispensing information using Cloud Architecture And Security Multi Cloud It Environments After Implementing Solutions. This template helps you present information on seven stages. You can also present information on Colocation, Hosted Private Cloud, Migration Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Architecture And Security Review Managing Compliance In Multi Cloud Environment
Cloud Architecture And Security Review Managing Compliance In Multi Cloud EnvironmentThis slide covers the policies for managing compliance in multi cloud such as Securing Cloud User Information, Optimizing Resource Usage and Value, Optimizing System and Resource Usage etc. Increase audience engagement and knowledge by dispensing information using Cloud Architecture And Security Review Managing Compliance In Multi Cloud Environment. This template helps you present information on five stages. You can also present information on Utilization Policy, Capacity Policy, Security Policy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Architecture And Security Review Requirement Of Policy Management In Multi Cloud Environment
Cloud Architecture And Security Review Requirement Of Policy Management In Multi Cloud EnvironmentThis slide covers the following requirements which explains the importance or need of Centralized policy management in multi cloud environment. Increase audience engagement and knowledge by dispensing information using Cloud Architecture And Security Review Requirement Of Policy Management In Multi Cloud Environment. This template helps you present information on four stages. You can also present information on Requirement, Policy Management, Multi Cloud Environment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Environment In Powerpoint And Google Slides Cpb
Cyber Security Environment In Powerpoint And Google Slides CpbPresenting Cyber Security Environment In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Security Environment. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Data Security And Storage Environment Icon
Data Security And Storage Environment IconPresenting our set of slides with Data Security And Storage Environment Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Security, Storage Environment Icon.
-
 Cyber Security Environment Vulnerability Assessment In Powerpoint And Google Slides Cpb
Cyber Security Environment Vulnerability Assessment In Powerpoint And Google Slides CpbPresenting our Cyber Security Environment Vulnerability Assessment In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases eight stages. It is useful to share insightful information on Cyber Security Environment Vulnerability Assessment. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Icons Slide For Security Architecture Review Of A Cloud Native Environment
Icons Slide For Security Architecture Review Of A Cloud Native EnvironmentIntroducing our well researched set of slides titled Icons Slide For Security Architecture Review Of A Cloud Native Environment. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents Security Architecture Review Of A Cloud Native Environment
Table Of Contents Security Architecture Review Of A Cloud Native EnvironmentIncrease audience engagement and knowledge by dispensing information using Table Of Contents Security Architecture Review Of A Cloud Native Environment. This template helps you present information on eleven stages. You can also present information on Establish Priorities, Conducting Root Cause Analysis, Business Objectives using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application environment security controls application development security information accuracy
Application environment security controls application development security information accuracyPresenting this set of slides with name - Application Environment Security Controls Application Development Security Information Accuracy. This is an editable seven stages graphic that deals with topics like Application Environment Security Controls, Application Development Security, Information Accuracy to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Determine security variances identify environment exceptions identify necessary roles
Determine security variances identify environment exceptions identify necessary rolesPresenting this set of slides with name - Determine Security Variances Identify Environment Exceptions Identify Necessary Roles. This is an editable eight stages graphic that deals with topics like Determine Security Variances, Identify Environment Exceptions, Identify Necessary Roles to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Application environment security controls configuration management malicious software
Application environment security controls configuration management malicious softwarePresenting this set of slides with name - Application Environment Security Controls Configuration Management Malicious Software. This is an editable three stages graphic that deals with topics like Application Environment Security Controls, Configuration Management, Malicious Software to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Application security effective web application environment strategic planning
Application security effective web application environment strategic planningPresenting this set of slides with name - Application Security Effective Web Application Environment Strategic Planning. This is an editable five stages graphic that deals with topics like Application Security Effective, Web Application Environment, Strategic Planning to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Release roadmap swimlane include flow of process such as environment setup and security improvements
Release roadmap swimlane include flow of process such as environment setup and security improvementsPresenting this set of slides with name - Release Roadmap Swimlane Include Flow Of Process Such As Environment Setup And Security Improvements. This is a three stage process. The stages in this process are Release Swimlane, Launch Swimlane, Deliver Swimlane.
-
 Security service model cloud environment effective staff meetings cpb
Security service model cloud environment effective staff meetings cpbThis is an editable five stages graphic that deals with topics like Security Service Model Cloud Environment Effective Staff Meetings to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security service model cloud environment ppt powerpoint presentation portfolio deck cpb
Security service model cloud environment ppt powerpoint presentation portfolio deck cpbPresenting this set of slides with name Security Service Model Cloud Environment Ppt Powerpoint Presentation Portfolio Deck Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Security Service Model Cloud Environment to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security data web environment ppt powerpoint presentation styles visuals cpb
Security data web environment ppt powerpoint presentation styles visuals cpbPresenting this set of slides with name Security Data Web Environment Ppt Powerpoint Presentation Styles Visuals Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Security Data Web Environment to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Best security measures in kubernetes production environment ppt presentation visuals
Best security measures in kubernetes production environment ppt presentation visualsThe slide consist of best Security measure which needs to follow in Kubernetes. Presenting this set of slides with name Best Security Measures In Kubernetes Production Environment Ppt Presentation Visuals. This is a ten stage process. The stages in this process are Best Security, Measures Kubernetes, Production Environment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Security service cloud environment framework ppt powerpoint presentation layouts skills cpb
Security service cloud environment framework ppt powerpoint presentation layouts skills cpbPresenting Security Service Cloud Environment Framework Ppt Powerpoint Presentation Layouts Skills Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Service Cloud Environment Framework. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Secure business environment ppt powerpoint presentation outline demonstration cpb
Secure business environment ppt powerpoint presentation outline demonstration cpbPresenting our Secure Business Environment Ppt Powerpoint Presentation Outline Demonstration Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Secure Business Environment This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.



