Powerpoint Templates and Google slides for Secure Data Cloud
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cloud Security Icon Security Computing Data Protection Digital Access
Cloud Security Icon Security Computing Data Protection Digital AccessKeep your audience glued to their seats with professionally designed PPT slides. This deck comprises of total of twelve slides. It has PPT templates with creative visuals and well researched content. Not just this, our PowerPoint professionals have crafted this deck with appropriate diagrams, layouts, icons, graphs, charts and more. This content ready presentation deck is fully editable. Just click the DOWNLOAD button below. Change the colour, text and font size. You can also modify the content as per your need. Get access to this well crafted complete deck presentation and leave your audience stunned.
-
 Statistics Of Cloud Data Security Attacks In Organization Cloud Data Encryption
Statistics Of Cloud Data Security Attacks In Organization Cloud Data EncryptionThis slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc. Deliver an outstanding presentation on the topic using this Statistics Of Cloud Data Security Attacks In Organization Cloud Data Encryption. Dispense information and present a thorough explanation of Data Interception, Unauthorized Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data security it best practices for cloud security ppt slides portfolio
Data security it best practices for cloud security ppt slides portfolioThis slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver an outstanding presentation on the topic using this Data Security IT Best Practices For Cloud Security Ppt Slides Portfolio. Dispense information and present a thorough explanation of Operations Management, Building Controls And Processes, Data Encryption, Security And Compliance Monitoring using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data security it elements of data security cloud security
Data security it elements of data security cloud securityThis slide defines the cloud security element of data security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Increase audience engagement and knowledge by dispensing information using Data Security IT Elements Of Data Security Cloud Security. This template helps you present information on seven stages. You can also present information on Data Breaches, Malware Injections, Distributed Denial Service Ddos, Malicious Insiders, Account Hijacking, Advanced Persistent Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data security it security framework in cloud computing
Data security it security framework in cloud computingThis slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. Increase audience engagement and knowledge by dispensing information using Data Security IT Security Framework In Cloud Computing. This template helps you present information on five stages. You can also present information on Identify, Protect, Detect, Respond, Recover using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Security Cloud Database Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Cloud Database Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a visual representation of a cloud database. It is designed to help you easily identify and access your cloud-based data storage. It is a great way to store and manage your data securely and efficiently.
-
 Data Security Cloud Database Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Cloud Database Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon is a perfect visual representation of a cloud database. It is a simple, yet powerful design that conveys the concept of data storage in the cloud. It is a great choice for presentations and other projects.
-
 Data Security Cloud Upload Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Cloud Upload Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is perfect for quickly and easily uploading to the NFT Cloud. It is easy to use and helps make the process of uploading files to the cloud simple and efficient.
-
 Data Security Cloud Upload Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Cloud Upload Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint icon is perfect for NFT Cloud Uploads. It is a simple and elegant design with a modern look, making it ideal for professional presentations. It is easy to use and can be quickly downloaded and uploaded to the cloud.
-
 Cloud Data Security Warning Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Data Security Warning Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon features a warning cloud with an exclamation mark, perfect for adding to presentations to warn viewers of potential risks or issues. It is a simple yet effective way to draw attention and communicate important information.
-
 Cloud Data Security Warning Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Data Security Warning Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Cloud Warning is a perfect visual aid for presentations and documents. It is a simple yet effective design that conveys the message of a warning in the cloud. It is easy to use, and can be easily customized to fit your needs.
-
 Impact Of Encryption Implementation On Cloud Security Cloud Data Encryption
Impact Of Encryption Implementation On Cloud Security Cloud Data EncryptionThis slide represents the various factors that showcase the improvement of application security after adopting encryption. The parameters discussed are unauthorized access, data breaches, malware and ransomware, phishing attacks, etc. Deliver an outstanding presentation on the topic using this Impact Of Encryption Implementation On Cloud Security Cloud Data Encryption. Dispense information and present a thorough explanation of Unauthorized Access, Data Breaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Timeline For Cloud Data Security Implementation Cloud Data Encryption
Timeline For Cloud Data Security Implementation Cloud Data EncryptionThis slide represents the timeline to implement cloud data encryption in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc. Introducing Timeline For Cloud Data Security Implementation Cloud Data Encryption to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Test Encryption Solutions, Implement Encryptions Solution, using this template. Grab it now to reap its full benefits.
-
 Cloud Data Security Software In Powerpoint And Google Slides Cpb
Cloud Data Security Software In Powerpoint And Google Slides CpbPresenting Cloud Data Security Software In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cloud Data Security Software. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cloud Access Security Broker CASB V2 Pillar Data Security Ppt Icon Backgrounds
Cloud Access Security Broker CASB V2 Pillar Data Security Ppt Icon BackgroundsThis slide talks about the data security pillar of the Cloud Access Security Broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Pillar Data Security Ppt Icon Backgrounds. This template helps you present information on four stages. You can also present information on Document Fingerprinting, Data Security Pillar, Cloud Access Security Broker Pillar using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cryptographic Algorithms Used In Data Security Cloud Cryptography
Cryptographic Algorithms Used In Data Security Cloud CryptographyThis slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. Deliver an outstanding presentation on the topic using this Cryptographic Algorithms Used In Data Security Cloud Cryptography. Dispense information and present a thorough explanation of Cryptographic, Algorithms, Data Encryption Standard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Security In Cloud Computing Architecture Cloud Cryptography
Data Security In Cloud Computing Architecture Cloud CryptographyThis slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues. Present the topic in a bit more detail with this Data Security In Cloud Computing Architecture Cloud Cryptography. Use it as a tool for discussion and navigation on Architecture, Cryptographic, Data Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Pillar Data Security Next Generation CASB
Cloud Access Security Broker Pillar Data Security Next Generation CASBThis slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Pillar Data Security Next Generation CASB This template helps you present information on five stages. You can also present information on Complex Cloud, Sensitive Material, Risk Assessments using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Software Defined Virtual Infrastructure For Cloud Management And Data Security
Software Defined Virtual Infrastructure For Cloud Management And Data SecurityThis slide represents the virtual infrastructure framework assisting companies to enhance data security and maintain business continuity. It includes various key components such as cloud management layer, physical layer, storage, etc. Presenting our well structured Software Defined Virtual Infrastructure For Cloud Management And Data Security. The topics discussed in this slide are Service Management, Business Continuity, Security Compliance. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Emerging Trends In Cryptographic Cloud Security Encryption For Data Privacy In Digital Age It
Emerging Trends In Cryptographic Cloud Security Encryption For Data Privacy In Digital Age ItThis slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc. Introducing Emerging Trends In Cryptographic Cloud Security Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Homomorphic Encryption, Quantum Safe Cryptography, Secure Multi Party Computation, using this template. Grab it now to reap its full benefits.
-
 Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age It
Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc. Introducing Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Data Protection, Poor Key Management, Software Engineers, using this template. Grab it now to reap its full benefits.
-
 Cloud Virtualization Icon Showcasing Data Security
Cloud Virtualization Icon Showcasing Data SecurityPresenting our set of slides with name Cloud Virtualization Icon Showcasing Data Security This exhibits information on Threestages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Virtualization Icon, Showcasing Data Security
-
 Virtual Private Cloud Icon Representing Data Security
Virtual Private Cloud Icon Representing Data SecurityPresenting our set of slides with Virtual Private Cloud Icon Representing Data Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Security, Representing, Cloud Icon.
-
 Cloud Access Security Broker Pillar Data Security CASB Cloud Security
Cloud Access Security Broker Pillar Data Security CASB Cloud SecurityThis slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Introducing Cloud Access Security Broker Pillar Data Security CASB Cloud Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Business Operations, Risk Assessments, using this template. Grab it now to reap its full benefits.
-
 Comparison Between CASB And Data Loss Prevention DLP CASB Cloud Security
Comparison Between CASB And Data Loss Prevention DLP CASB Cloud SecurityThis slide describes the difference between cloud access security broker and data loss prevention. This slide highlights the main comparisons between CASB and DLP systems based on their purpose, focus area, use cases, key features, implementation and relationship. Present the topic in a bit more detail with this Comparison Between CASB And Data Loss Prevention DLP CASB Cloud Security. Use it as a tool for discussion and navigation on Cloud Access Security Broker, Data Loss Prevention, Focus Area, Implementation And Relationship. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Big Data Cloud Cyber Security Icon
Big Data Cloud Cyber Security IconIntroducing our premium set of slides with Big Data Cloud Cyber Security Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud, Cyber, Security. So download instantly and tailor it with your information.
-
 Strategic Approach For Effective Data Migration Case Study Data Security And Compliance In Cloud Migration
Strategic Approach For Effective Data Migration Case Study Data Security And Compliance In Cloud MigrationThe following slide showcases a case study on data security and compliance in cloud migration. It includes various elements such as company details, challenges, and solutions. Increase audience engagement and knowledge by dispensing information using Strategic Approach For Effective Data Migration Case Study Data Security And Compliance In Cloud Migration. This template helps you present information on three stages. You can also present information on Data Security, Cloud Migration, Security And Confidentiality, Customer Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Storage Practices For Data Security And Management
Cloud Storage Practices For Data Security And ManagementThis slide highlights ways for managing cloud storage to ensure data protection. The purpose of this slide is to aid businesses in implementing measures for protecting sensitive information from potential threats. It includes elements such as encryption, access control, etc. Presenting our set of slides with Cloud Storage Practices For Data Security And Management. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Encryption, Access Control, Security Training.
-
 Ways To Overcome Cloud Data Security Challenges
Ways To Overcome Cloud Data Security ChallengesThis slide highlights solutions for cloud data security issues. The purpose of this template is assist organizations in balancing data protection and accessibility for addressing multiple problems. It includes elements such as data breaches, lack of control, etc. Introducing our premium set of slides with Ways To Overcome Cloud Data Security Challenges. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Breaches, Insufficient Cloud Provider Security, Lack Of Control. So download instantly and tailor it with your information.
-
 Tokenization For Improved Data Security Basic Tokenization Service For Cloud Based Operations
Tokenization For Improved Data Security Basic Tokenization Service For Cloud Based OperationsThis slide represents the fundamental tokenization service designed for cloud-based solutions. The purpose of this slide is to showcase the basic tokenization service for cloud-based services. Present the topic in a bit more detail with this Tokenization For Improved Data Security Basic Tokenization Service For Cloud Based Operations. Use it as a tool for discussion and navigation on Sensitive Or Personal Information Sources, Tokenization Database, Tokenization Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems
Tokenization For Improved Data Security Governance And Risk Management In Cloud Based SystemsThis slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems. Dispense information and present a thorough explanation of Governance And Risk Management, Cloud Based Systems, During Categorization Organization Must using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Optimal Practices For Incorporating Tokenization Into Cloud
Tokenization For Improved Data Security Optimal Practices For Incorporating Tokenization Into CloudThis slide discusses the utilization of tokenization in the context of cloud-based services. The purpose of this slide is to discuss the overview of implementing tokenization for cloud based services. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Optimal Practices For Incorporating Tokenization Into Cloud. This template helps you present information on six stages. You can also present information on Incorporating Tokenization, Cloud Based Services, Protect Sensitive Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Tokenization Process Activities In A Cloud Based System
Tokenization For Improved Data Security Tokenization Process Activities In A Cloud Based SystemThis slide highlights the key functions within a cloud-based system in data security. The purpose of this slide is to outline the Process activities in a cloud-based system which include gathering, creating, retrieving data, etc. Introducing Tokenization For Improved Data Security Tokenization Process Activities In A Cloud Based System to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Tokenization Process Activities, Cloud Based System, Retrieving Data, using this template. Grab it now to reap its full benefits.
-
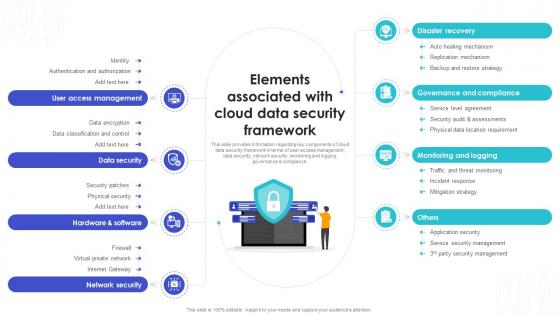 Elements Associated With Cloud Data Security Safeguarding Business With Data Loss Cybersecurity SS
Elements Associated With Cloud Data Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding key components of cloud data security framework in terms of user access management, data security, network security, monitoring and logging, governance and compliance.Increase audience engagement and knowledge by dispensing information using Elements Associated With Cloud Data Security Safeguarding Business With Data Loss Cybersecurity SS. This template helps you present information on eight stages. You can also present information on Disaster Recovery, User Access Management, Data Security, Network Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Data Migration Security Risks And Solutions
Cloud Data Migration Security Risks And SolutionsThe below slide highlights the multiple security risks associated with cloud data migration along with the potential solutions to eliminate them. The various risks mentioned are unauthorized access, data breaches, weak data encryption, etc. Introducing our Cloud Data Migration Security Risks And Solutions set of slides. The topics discussed in these slides are Unauthorized Access, Data Breaches, Weak Data Encryption. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Security Mechanism To Protect Data Gathered From IOT Devices
Cloud Security Mechanism To Protect Data Gathered From IOT DevicesThis slide showcases AWS IoT security diagram for secure data transfer. It includes user, IoT devices, Cognito ID, lambda, DynamicDB and kinesis. Presenting our well structured Cloud Security Mechanism To Protect Data Gathered From IOT Devices. The topics discussed in this slide are Security Credentials, Identity And Access, Management Policies. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Practices To Ensure Secure Cloud Data Migration
Practices To Ensure Secure Cloud Data MigrationThis slide provides the best practices for effective monitoring of cloud data migration that helps to eliminate the potential risks associated with data deployment. Key steps are use of native solutions, compliance audit, etc. Presenting our set of slides with Practices To Ensure Secure Cloud Data Migration. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Security Architect, Track And Automate, Implement Compliance.
-
 Cloud Data Management Virtualization Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Data Management Virtualization Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon represents the importance of data security in cloud virtualization. With a vibrant design, it visually conveys the significance of protecting sensitive information in a virtual environment. Use it to enhance your presentations on cloud computing and data protection.
-
 Cloud Data Management Virtualization Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Data Management Virtualization Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is the perfect addition to your presentation on Cloud virtualization data security. With a sleek design and clear imagery, it effectively represents the topic of data security in the cloud. Use it to enhance your slides and make a lasting impression on your audience.
-
 Methods Of Cloud Data Network Security
Methods Of Cloud Data Network SecurityThis slide focuses on cloud data network security techniques including methods, strategic actions, and illustrations. Introducing our Methods Of Cloud Data Network Security set of slides. The topics discussed in these slides are Strategic Actions, Illustrations, Methods. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Encryption Essentials For Robust Data Security
Cloud Encryption Essentials For Robust Data SecurityThe purpose of this slide is to highlight how cloud encryption essentials bolster robust data security. It safeguard sensitive information stored in cloud environments through cryptographic techniques. Presenting our set of slides with name Cloud Encryption Essentials For Robust Data Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Insider Threat Defense, Secure Data Transfers, Organizational Integrity.
-
 Sales CRM Cloud Implementation Securing Our Data With CRM Ppt Slides Image
Sales CRM Cloud Implementation Securing Our Data With CRM Ppt Slides ImageThis slide illustrates the issues that trigger poor relationship with customers which includes no real time support, no innovative product launched, bad after sale service and lack of engagement. Present the topic in a bit more detail with this Sales CRM Cloud Implementation Poor Relationship With Customers Ppt Slides Picture. Use it as a tool for discussion and navigation on Weak Relationship Building, Poor Customer Service, Product Launched. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Wireless security icon of cloud servers to secure data
Wireless security icon of cloud servers to secure dataPresenting our set of slides with Wireless Security Icon Of Cloud Servers To Secure Data. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Wireless Security Icon Of Cloud Servers To Secure Data.
-
 Secure data storage cloud computings ppt powerpoint presentation example cpb
Secure data storage cloud computings ppt powerpoint presentation example cpbPresenting Secure Data Storage Cloud Computings Ppt Powerpoint Presentation Example Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Data Storage Cloud Computings. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Data Cloud Security Ppt Powerpoint Presentation Gallery Sample Cpb
Data Cloud Security Ppt Powerpoint Presentation Gallery Sample CpbPresenting Data Cloud Security Ppt Powerpoint Presentation Gallery Sample Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase ten stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Data Cloud Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Data Cloud Security Ppt Powerpoint Presentation Model Pictures Cpb
Data Cloud Security Ppt Powerpoint Presentation Model Pictures CpbPresenting our Data Cloud Security Ppt Powerpoint Presentation Model Pictures Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Data Cloud Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
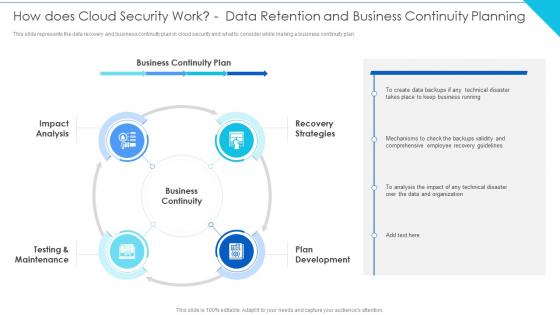 Cloud Information Security How Does Cloud Security Work Data Planning
Cloud Information Security How Does Cloud Security Work Data PlanningThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan.Increase audience engagement and knowledge by dispensing information using Cloud Information Security How Does Cloud Security Work Data Planning This template helps you present information on five stages. You can also present information on Implement Information, Authentication Process, Data Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Backup And Data Recovery Cloud Information Security
Cloud Security Checklist Backup And Data Recovery Cloud Information SecurityThis slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them.Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Backup And Data Recovery Cloud Information Security This template helps you present information on five stages. You can also present information on Sensitive Information, Encode Sensitive, Encrypted Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Data Encryption Cloud Information Security
Cloud Security Checklist Data Encryption Cloud Information SecurityThis slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys.Introducing Cloud Security Checklist Data Encryption Cloud Information Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Future Evaluation, Device Is Detected, Change Activities using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Loss Of Data Cloud Information Security
Cloud Security Threats Loss Of Data Cloud Information SecurityThis slide represents the data loss threat of cloud security it is essential to secure organization data and create backups.Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Loss Of Data Cloud Information Security This template helps you present information on four stages. You can also present information on Cloud Administrations, Protection Frameworks, Technology Advances using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does Cloud Security Work Data Security Cloud Information Security
How Does Cloud Security Work Data Security Cloud Information SecurityThis slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security.Introducing How Does Cloud Security Work Data Security Cloud Information Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Accessibility, Knowledge, Organized Documented using this template. Grab it now to reap its full benefits.
-
 Securing Data Over Google Cloud Ppt Powerpoint Presentation Summary Slides
Securing Data Over Google Cloud Ppt Powerpoint Presentation Summary SlidesThis slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock. Present the topic in a bit more detail with this Securing Data Over Google Cloud Ppt Powerpoint Presentation Summary Slides. Use it as a tool for discussion and navigation on Access Management, Data Encryption, Authentication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Google Cloud Platform Securing Data Over Google Cloud Ppt Template
Google Cloud Platform Securing Data Over Google Cloud Ppt TemplateThis slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock. Introducing Google Cloud Platform Securing Data Over Google Cloud Ppt Template to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Access Management, Data Encryption, Authentication, using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security How Does Cloud Security Work Data Retention And Business
Cloud Computing Security How Does Cloud Security Work Data Retention And BusinessThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security How Does Cloud Security Work Data Retention And Business. This template helps you present information on four stages. You can also present information on Impact Analysis, Recovery Strategies, Testing And Maintenance, Plan Development using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security How Does Cloud Security Work Data Security
Cloud Computing Security How Does Cloud Security Work Data SecurityThis slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. Introducing Cloud Computing Security How Does Cloud Security Work Data Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Application Security, Physical Security, Internet Security, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Backup And Data Recovery Cloud Computing Security
Cloud Security Checklist Backup And Data Recovery Cloud Computing SecurityThis slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Backup And Data Recovery Cloud Computing Security. This template helps you present information on three stages. You can also present information on Cyber Attacks, Physical Location, Backup And Recovery Plans using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Data Encryption Cloud Computing Security
Cloud Security Checklist Data Encryption Cloud Computing SecurityThis slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. Introducing Cloud Security Checklist Data Encryption Cloud Computing Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Public Keys, Private Keys, Data Servers, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Loss Of Data Cloud Computing Security
Cloud Security Threats Loss Of Data Cloud Computing SecurityThis slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Loss Of Data Cloud Computing Security. This template helps you present information on four stages. You can also present information on Service Providers, Organization, Backup Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Data Cloud Ppt Powerpoint Presentation Slides Designs Cpb
Secure Data Cloud Ppt Powerpoint Presentation Slides Designs CpbPresenting our Secure Data Cloud Ppt Powerpoint Presentation Slides Designs Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Secure Data Cloud This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Approaches Of Cloud Disaster Recovery For Data Security
Approaches Of Cloud Disaster Recovery For Data SecurityThis slide shows four approaches of cloud disaster recovery that can be used by an organization to create a data secure environment. It includes backup and restore, warm study, pilot light and multi site active or active approach. Introducing our premium set of slides with Approaches Of Cloud Disaster Recovery For Data Security. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Backup And Restore, Warm Standby, Pilot Light. So download instantly and tailor it with your information.




