Powerpoint Templates and Google slides for Secure Business
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Components Of Business Security Incident Response Plans
Components Of Business Security Incident Response PlansThis slide highlights the components of business security incident response plan. The purpose of this slide is to help the business develop effective security incident response plans through the use of components use as incident taxonomy, data classification frameworks, etc. Introducing our premium set of slides with Components Of Business Security Incident Response Plans. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Operating Models, Performance Objectives, Incident Taxonomy. So download instantly and tailor it with your information.
-
 Storage Facility Security Solutions For Businesses
Storage Facility Security Solutions For BusinessesThe purpose of this slide is to implement comprehensive security measures such as advanced access control systems, surveillance cameras, and alarm systems to safeguard business storage facilities such as perimeter security, access control, etc. Introducing our Storage Facility Security Solutions For Businesses set of slides. The topics discussed in these slides are Insurance And Legal Protection, Individual Unit Alarms, Access Control, Perimeter Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Security Audit Checklist For Businesses
Cloud Security Audit Checklist For BusinessesThis slide showcases checklist for cloud security audit to fix loopholes including checkpoints such as identifying cloud providers and services, access level management in cloud, etc. Introducing our Cloud Security Audit Checklist For Businesses set of slides. The topics discussed in these slides are Identify Cloud Providers And Services, Encrypt Data In Transit, Detecting Unusual Or Suspicious Activity. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security Threats
Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the negative impact of cyber crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Introducing Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Rising Cost, Reputational Damage, Operational Disruption using this template. Grab it now to reap its full benefits.
-
 Different Encryption Methods To Secure Business Data
Different Encryption Methods To Secure Business DataThis slide represents various types of encryption method which assists businesses to protect data and maintain regulatory compliances. It includes different encryption methods to secure business data such as advance encryption standards, rivest shamir adleman, etc. Introducing our premium set of slides with name Different Encryption Methods To Secure Business Data. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Format Preserving Encryption, Blowfish, Advance Encryption Standards. So download instantly and tailor it with your information.
-
 Business Model Smart Farming Technology Pitch Deck For Food Security
Business Model Smart Farming Technology Pitch Deck For Food SecurityFollowing slide showcases business and operational model of company. It includes elements such as key partners, resources, channels, value preposition, customer relationships, segments etc. Deliver an outstanding presentation on the topic using this Business Model Smart Farming Technology Pitch Deck For Food Security Dispense information and present a thorough explanation of Value Propositions, Customer Relationship, Customer Segments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Why CASB Is Important For Businesses CASB Cloud Security
Why CASB Is Important For Businesses CASB Cloud SecurityThis slide outlines the importance of CASB for different organizations. The purpose of this slide is to showcase the various reasons for businesses to invest in the cloud access security broker model, including increased cloud adoption, better security, compliance, and cost-effective and centralized management. Introducing Why CASB Is Important For Businesses CASB Cloud Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker Model, Cloud Adoption, Better Security, Compliance, using this template. Grab it now to reap its full benefits.
-
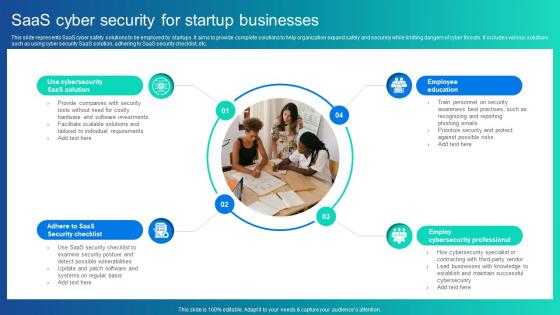 Saas Cyber Security For Startup Businesses
Saas Cyber Security For Startup BusinessesThis slide represents SaaS cyber safety solutions to be employed by startups. It aims to provide complete solutions to help organization expand safely and securely while limiting dangers of cyber threats. It includes various solutions such as using cyber security SaaS solution, adhering to SaaS security checklist, etc. Presenting our set of slides with Saas Cyber Security For Startup Businesses This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Checklist, Employ Cybersecurity Professional, Employee Education
-
 Cyber Security Measures To Protect Business Data
Cyber Security Measures To Protect Business DataThe highlighted slide underscores essential measures, including robust passwords, regular software updates, antivirus protection, multi factor authentication, and access control. These steps collectively enhance cybersecurity, fortifying defenses to safeguard critical business data against potential threats. Presenting our set of slides with Cyber Security Measures To Protect Business Data. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Strong And Complex Passwords, Software Updates, Enhance Security.
-
 Integrate Cyber Security Into Business Continuity And Disaster Recovery
Integrate Cyber Security Into Business Continuity And Disaster RecoveryThis slide depicts to integrate cyber security system into business continuity and disaster recovery process. Its aim is to improve operational efficiency and protect against any future threats. This slide includes planning, technology, policy, etc. Introducing our premium set of slides with Integrate Cyber Security Into Business Continuity And Disaster Recovery. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Planning, Technology, Policy. So download instantly and tailor it with your information.
-
 Essential Crisis Management Security Tips For Businesses
Essential Crisis Management Security Tips For BusinessesThe purpose of this slide is to outline essential crisis management security tips for businesses, offering proactive strategies to mitigate risks, safeguard assets, and ensure operational resilience in the face of unforeseen challenges. Introducing our premium set of slides with Essential Crisis Management Security Tips For Businesses. Ellicudate the nine stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Learn From Experience, Backup And Recovery Systems, Emergency Response Team, Conduct Risk Assessment.So download instantly and tailor it with your information.
-
 Cyber Security Mesh Applications For Business
Cyber Security Mesh Applications For BusinessThe following slide features key elements like IAM support, MSSPS, identity-proofing tools, standards, and demographic bias in illustrating the diverse applications of cybersecurity mesh for business. This aids in understanding its potential impact on security and operations. Presenting our set of slides with Cyber Security Mesh Applications For Business This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Mesh Supporting Iam Requests, Identity Life Cycle, Decentralized Identity Standards
-
 Cyber Security Mesh Benefits For Business
Cyber Security Mesh Benefits For BusinessThe following slide emphasizes IAM support, MSSPS, identity-proofing tools, standards, and addressing demographic bias to illustrate the business benefits of cybersecurity mesh. It aids in recognizing the advantages it offers to businesses in enhancing security and inclusivity. Presenting our set of slides with Cyber Security Mesh Benefits For Business This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Iam Support, Identity Standards, Identity Proofing
-
 Best Practices For Security Gap In Network Business
Best Practices For Security Gap In Network BusinessThis slide showcases strategies for visualization security. The main purpose of this template is to showcase various methods used for visualization security. This includes establishing clear data access, prioritizing data encryption, regular security audits, etc. Presenting our set of slides with name Best Practices For Security Gap In Network Business. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Prioritize Data Encryption, Regular Security Audits, Ensure Compliance.
-
 Security Gap Report Analysis For Business
Security Gap Report Analysis For BusinessThis slide covers security gap analysis report for companies to To identify vulnerabilities and weaknesses in the current security infrastructure, enabling proactive measures to safeguard business assets and sensitive information. Introducing our Security Gap Report Analysis For Business set of slides. The topics discussed in these slides are Improvement Required, Improvement Recommended, Improvement Available, Improvement Completed. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 ACH Payment Application Impact On Business Enhancing Transaction Security With E Payment
ACH Payment Application Impact On Business Enhancing Transaction Security With E PaymentMentioned slide provides insights into ACH payment method impact on business transactions. It includes key points such as pay recurring bills, lower transaction costs, easy remote payment, and improve sales conversion. Introducing ACH Payment Application Impact On Business Enhancing Transaction Security With E Payment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Pay Recurring Bills, Lower Transaction Cost, Easy Remote Payment using this template. Grab it now to reap its full benefits.
-
 Cashless Payments Methods Offered By Business Enhancing Transaction Security With E Payment
Cashless Payments Methods Offered By Business Enhancing Transaction Security With E PaymentMentioned slide provides information about various cashless payment methods which can be adopted by businesses to increase organizational revenue. It includes various payments such as cheque and demand draft, net banking, cards, mobile wallet, QR codes, ACH, cryptocurrency, etc. Introducing Cashless Payments Methods Offered By Business Enhancing Transaction Security With E Payment to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Cheque, Credit And Debit Card, Mobile Wallet using this template. Grab it now to reap its full benefits.
-
 Challenges Faced By Business In Adopting Cashless Payment Enhancing Transaction Security With E Payment
Challenges Faced By Business In Adopting Cashless Payment Enhancing Transaction Security With E PaymentMentioned slide showcases various challenges in implementation of cashless payment system in business. It includes challenges such as customer restrain, high processing fees, security issues, difficulty to adopt cashless technology and regular internet services. Increase audience engagement and knowledge by dispensing information using Challenges Faced By Business In Adopting Cashless Payment Enhancing Transaction Security With E Payment This template helps you present information on five stages. You can also present information on Customer Resistance, High Processing Fees, Security Issues using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cheque Payment Impact On Business Transactions Enhancing Transaction Security With E Payment
Cheque Payment Impact On Business Transactions Enhancing Transaction Security With E PaymentMentioned slide provides insights into impact of leveraging cheque payment methods in business to control money transfer process. It includes key impacts such as security, records, flexibility, and convenience. Introducing Cheque Payment Impact On Business Transactions Enhancing Transaction Security With E Payment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Security, Flexibility, Record Management using this template. Grab it now to reap its full benefits.
-
 Gift Card Adoption Practices For Business Enhancing Transaction Security With E Payment
Gift Card Adoption Practices For Business Enhancing Transaction Security With E PaymentFollowing slide provides insights into best practices to be followed by businesses while leveraging gift cards and vouchers as payment options. It includes best practices such as create different landing page, section for gift card status checks, gift card amount selection, customer information, and customize gift card code. Increase audience engagement and knowledge by dispensing information using Gift Card Adoption Practices For Business Enhancing Transaction Security With E Payment This template helps you present information on five stages. You can also present information on Customize Gift Card Code, Create Different Landing Page, Selection Of Gift Card Amount using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Impact Of Accepting Cryptocurrency Payments On Business Sales Enhancing Transaction Security With E Payment
Impact Of Accepting Cryptocurrency Payments On Business Sales Enhancing Transaction Security With E PaymentMentioned slide showcases statistics associates with impact of cryptocurrency implementation in business. It includes key metrics such as transaction cost, merchant protection, customer convenience and business sales. Present the topic in a bit more detail with this Impact Of Accepting Cryptocurrency Payments On Business Sales Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Transaction Cost, Merchant Protection Level, Customer Convenience This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Multiple Cashless Payment Systems Leveraged By Business Enhancing Transaction Security With E Payment
Multiple Cashless Payment Systems Leveraged By Business Enhancing Transaction Security With E PaymentMentioned slide provides information about various payment systems which can be leveraged by businesses to increase cashless transactions. It includes payment systems such as virtual terminal, card reader, payment terminal and invoicing software. Increase audience engagement and knowledge by dispensing information using Multiple Cashless Payment Systems Leveraged By Business Enhancing Transaction Security With E Payment This template helps you present information on four stages. You can also present information on Virtual Terminal, Card Reader, Payment Terminal using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategies To Implement Cashless Payment In Business Enhancing Transaction Security With E Payment
Strategies To Implement Cashless Payment In Business Enhancing Transaction Security With E PaymentMentioned slide provides information about strategies which can be implemented by businesses before going cashless. It includes strategies such as determine customer preferences, select payment processor, offer payment options, implement CRM software. Present the topic in a bit more detail with this Strategies To Implement Cashless Payment In Business Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Determine Customer Preference, Select Payment Processor, Implement CRM Tool This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Types Of Cryptocurrency Tokens For Business Growth Enhancing Transaction Security With E Payment
Types Of Cryptocurrency Tokens For Business Growth Enhancing Transaction Security With E PaymentFollowing slide includes various types of cryptocurrency present in market which can be used by businesses for going global. It includes types such as utility, payment, security, and exchange. Introducing Types Of Cryptocurrency Tokens For Business Growth Enhancing Transaction Security With E Payment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Utility Token, Payment Token, Security Token using this template. Grab it now to reap its full benefits.
-
 Types Of Gift Card Offered By Businesses To Customers Enhancing Transaction Security With E Payment
Types Of Gift Card Offered By Businesses To Customers Enhancing Transaction Security With E PaymentFollowing slide provides insights into two types of gift cards used by businesses for cashless transaction which can be leveraged by companies to attract customers. It includes gift cards such as open loop gift cards and closed loop gift cards. Present the topic in a bit more detail with this Types Of Gift Card Offered By Businesses To Customers Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Types, Open Loop Gift Cards, Closed Loop Gift Cards This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Zero Trust Architecture ZTA Role Of ZTNA To Improve Business Operations And Security
Zero Trust Architecture ZTA Role Of ZTNA To Improve Business Operations And SecurityThis slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Introducing Zero Trust Architecture ZTA Role Of ZTNA To Improve Business Operations And Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Traditional Method, ZTNA Approach, Login Capability, using this template. Grab it now to reap its full benefits.
-
 Best Practices Of Information Security For Small Businesses
Best Practices Of Information Security For Small BusinessesThis slide highlights information security strategies for small enterprises. The purpose of this slide is to help managers in safeguarding users data from breaches and theft for building their reputation in the market. It includes elements such as employee training, backup, etc. Presenting our set of slides with Best Practices Of Information Security For Small Businesses. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Employee Training, Regular Updates, Network Security
-
 Cyber Security Controls Checklist For Business
Cyber Security Controls Checklist For BusinessThis slide highlights the checklist for cyber security controls to prevent business from cyber attacks and protect company confidential data. It includes various KPIs such as password management, privacy and security of sensitive data. Presenting our well structured Cyber Security Controls Checklist For Business The topics discussed in this slide are Password Management, Security Awareness This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 NIST Cyber Security Control Framework For Business
NIST Cyber Security Control Framework For BusinessThis slide represents cyber security control NIST framework to help business in identifying potential threats of attacks or data breach. It includes various steps such as identify, protect, detect, respond and recover. Introducing our premium set of slides with NIST Cyber Security Control Framework For Business Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify, Protect, Detect So download instantly and tailor it with your information.
-
 Impact Of Web Security On Business Operations
Impact Of Web Security On Business OperationsThis template presents benefits and impact of ensuring web security. The purpose of this slide is to minimize organizational security risks by detecting and preventing cyber threats. It covers functional impact and various benefits such as improvement of security posture, protecting IT infrastructure, enhancement of security training programs, etc. Introducing our Impact Of Web Security On Business Operations set of slides. The topics discussed in these slides are Monitors Data Flow Security, Protects IT Infrastructure, Improves Security Posture This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Current IoT Security Business Challenges Internet Of Things IoT Security Cybersecurity SS
Current IoT Security Business Challenges Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security challenges faced by businesses. It provides details about IoT malware and ransomware, user privacy risks, insecure interfaces, remove work environments, etc. Deliver an outstanding presentation on the topic using this Current IoT Security Business Challenges Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of IoT Security Business Challenges, Internet Of Things, IoT Malware And Ransomware, User Privacy Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
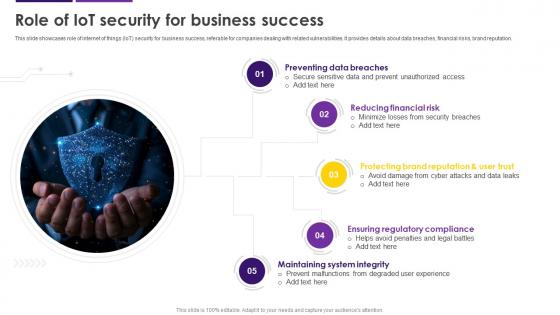 Role Of IoT Security For Business Success Internet Of Things IoT Security Cybersecurity SS
Role Of IoT Security For Business Success Internet Of Things IoT Security Cybersecurity SSThis slide showcases role of internet of things IoT security for business success, referable for companies dealing with related vulnerabilities. It provides details about data breaches, financial risks, brand reputation. Increase audience engagement and knowledge by dispensing information using Role Of IoT Security For Business Success Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on five stages. You can also present information on Preventing Data Breaches, Reducing Financial Risk, Ensuring Regulatory Compliance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security System Icon For Business Management
Information Security System Icon For Business ManagementIntroducing our premium set of slides with Information Security System Icon For Business Management. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Security System, Business Management. So download instantly and tailor it with your information.
-
 Application Security Implementation Plan Major Impact Of Application Security On Business
Application Security Implementation Plan Major Impact Of Application Security On BusinessThis slide showcases the after application security impact on business along with factors that have improved the overall performance. Introducing Application Security Implementation Plan Major Impact Of Application Security On Business to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threats Surge, Security Increase, Reduced Attacks On Applications, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Visualization Security In Business
Best Practices For Visualization Security In BusinessThis slide showcases strategies for visualization security. The main purpose of this template is to showcase various methods used for visualization security. This includes establishing clear data access, prioritizing data encryption, regular security audits, etc. Presenting our set of slides with Best Practices For Visualization Security In Business. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Trends, Ensure Compliance, Security Awareness.
-
 Benefits Related To IP Security In Business
Benefits Related To IP Security In BusinessThis slide showcases benefits of IP security in business. The main purpose of this template is to showcase essential strategic investment that contributes in success and organization growth. This includes data protection, trust and reputation, cost saving, etc. Presenting our set of slides with name Benefits Related To IP Security In Business. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Compliance Assurance, Secure Remote Network, Reduced Downtime, Trust And Reputation.
-
 Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In Business
Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In BusinessThis slide showcases the breakdown cost for conducting tokenization for data security. The purpose of this slide is to showcase the technology cost breakdown for different components such as test infrastructure, staff training, etc. Present the topic in a bit more detail with this Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In Business. Use it as a tool for discussion and navigation on Tokenization Solution, Integration And Customization, Infrastructure And Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Future Trends Of Tokenization On Business And Technology
Tokenization For Improved Data Security Future Trends Of Tokenization On Business And TechnologyThis slide highlights the anticipated developments in tokenizations impact on the realms of business and technology. The purpose of this slide is to outline the future trends of tokenization. Introducing Tokenization For Improved Data Security Future Trends Of Tokenization On Business And Technology to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Anticipated Developments, Business And Technology, Future Trends Of Tokenization, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Selecting Appropriate Tokenization Solution For Business Needs
Tokenization For Improved Data Security Selecting Appropriate Tokenization Solution For Business NeedsThis slide discusses about choosing right tokenization solution for business needs. The purpose of this slide is to highlight the ways of selecting which include applicability to business, data elements, etc. Introducing Tokenization For Improved Data Security Selecting Appropriate Tokenization Solution For Business Needs to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Consistency Requirement, Data Elements For Tokenization, Applicability To Business, using this template. Grab it now to reap its full benefits.
-
 Business Impact Of Endpoint Cyber Security
Business Impact Of Endpoint Cyber SecurityThis slide shows impact of ensuring endpoint cyber security in an organization. The purpose of this slide is to help businesses in improving network security by ensuring defense against malware attacks. It covers various benefits such as centralized platform, dynamic support, better user experience and data encryption. Presenting our set of slides with Business Impact Of Endpoint Cyber Security This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Centralized Platform, Dynamic Support, Better User Experience
-
 Business Financial Projection Security Protocols
Business Financial Projection Security ProtocolsThe purpose of this slide is to showcase safety measures of financial projection such as hire experts and understand market which help in ensuring risk mitigation and safeguards business. Introducing our premium set of slides with Business Financial Projection Security Protocols Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Benefit Existing Businesses, Understand Market, Hire Experts So download instantly and tailor it with your information.
-
 Voice Recognition For Enhancing Security And Authentication Next Gen Business Transformation With Voice TC SS
Voice Recognition For Enhancing Security And Authentication Next Gen Business Transformation With Voice TC SSThis slide presents various use case of voice recognition technology for security and authentication in various areas. It includes mobile applications, call centers and IVR systems,and web applications. Increase audience engagement and knowledge by dispensing information using Voice Recognition For Enhancing Security And Authentication Next Gen Business Transformation With Voice TC SS. This template helps you present information on four stages. You can also present information on Mobile Applications, Web Applications, Voice Commands using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Business Physical Security System Icon
Business Physical Security System IconPresenting our set of slides with Business Physical Security System Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Business, Physical Security System, Icon.
-
 Access With Cloud Storage Solution Business Recovery Plan To Overcome Cyber Security Threat
Access With Cloud Storage Solution Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about access management with a cloud storage solution. It includes file sharing with cloud platforms and selection criteria such as storage space, privacy and security, and other benefits. Present the topic in a bit more detail with this Access With Cloud Storage Solution Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Storage Space, Privacy And Security, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda Business Recovery Plan To Overcome Cyber Security Threat
Agenda Business Recovery Plan To Overcome Cyber Security ThreatIntroducing Agenda Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Business, Financial, Operations, using this template. Grab it now to reap its full benefits.
-
 Alternative For Managing Cyber Threats Business Recovery Plan To Overcome Cyber Security Threat
Alternative For Managing Cyber Threats Business Recovery Plan To Overcome Cyber Security ThreatIncrease audience engagement and knowledge by dispensing information using Alternative For Managing Cyber Threats Business Recovery Plan To Overcome Cyber Security Threat. This template helps you present information on five stages. You can also present information on Staff Training, End Point Protection, Wifi Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security Threat
Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about system patch management to determine vulnerabilities after cyber attack. It includes key process of automated patch management and best practices such as schedule patching, prioritization, and patch testing. Deliver an outstanding presentation on the topic using this Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Management, Process, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Business Goals Achievement Duration Business Recovery Plan To Overcome Cyber Security Threat
Business Goals Achievement Duration Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about time-based goals achieved for cyber attack management. It includes goals such as mean time to detect incidents, containment time, resolution time, and recovery time. Present the topic in a bit more detail with this Business Goals Achievement Duration Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Mean Time To Recover, Mean Time To Resolve, Mean Time To Contain. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Plan Implementation Roadmap Business Recovery Plan To Overcome Cyber Security Threat
Business Plan Implementation Roadmap Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about business cyber security attack recovery plan. It includes key steps such as setting time based recovery goals, impact and risk assessment, build recovery team, communication plan, recovery strategies implementation, etc. Introducing Business Plan Implementation Roadmap Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Assessment, Communication Plan, Recovery Strategies Implementation, using this template. Grab it now to reap its full benefits.
-
 Business Plan To Overcome Cyber Security Threat Table Of Contents
Business Plan To Overcome Cyber Security Threat Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Business Plan To Overcome Cyber Security Threat Table Of Contents. This template helps you present information on one stages. You can also present information on Business, Communication, External Stakeholders using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Case Study Construction Management Company Business Recovery To Overcome Cyber Security Threat
Case Study Construction Management Company Business Recovery To Overcome Cyber Security ThreatMentioned slide provides information about a case study related to a ransomware attack on the construction company. It includes key elements such as situation detail, adopted strategies, and outcomes. Deliver an outstanding presentation on the topic using this Case Study Construction Management Company Business Recovery To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Construction, Management, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Case Study Continuity Disaster Recovery Business Recovery Plan To Overcome Cyber Security Threat
Case Study Continuity Disaster Recovery Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about case study related to business recovery by Automotive company after a water outbreak. It includes challenges faced, goals, adopted approaches, and results. Present the topic in a bit more detail with this Case Study Continuity Disaster Recovery Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Business Continuity, Disaster Recovery, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security Threat
Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about a case study related to data breach recovery. It includes key elements such as incident date, challenges faced, LinkedIn response plan, and results. Deliver an outstanding presentation on the topic using this Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Regain Customer Trust, Rebuilding Business Reputation, Linkedin Response using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Conducting Of Business Recovery Plan Business Recovery Plan To Overcome Cyber Security Threat
Conducting Of Business Recovery Plan Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about cybercrime cost growth and various cybercrime attacks on leading companies such as LinkedIn, Facebook, Microsoft Exchange email servers, and real estate wealth networks. Present the topic in a bit more detail with this Conducting Of Business Recovery Plan Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Assessment, Business, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attack Restriction Plan Checklist Business Recovery Plan To Overcome Cyber Security Threat
Cyber Attack Restriction Plan Checklist Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information on various cyber attack containment strategies that can be implemented to prevent further data breaches such as restraining lateral movements, and data breach evident collection. Deliver an outstanding presentation on the topic using this Cyber Attack Restriction Plan Checklist Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Containment, Strategies, Implemented using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Communication Different Stakeholders Business Recovery Plan To Overcome Cyber Security Threat
Cyber Communication Different Stakeholders Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various stakeholders to be taken care of during and after the business recovery periods such as customers, internal stakeholders, external agencies, and recovery team. Introducing Cyber Communication Different Stakeholders Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Customer, Government, Recovery Team, using this template. Grab it now to reap its full benefits.
-
 Cyber Containment Action Plan Checklist Business Recovery Plan To Overcome Cyber Security Threat
Cyber Containment Action Plan Checklist Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information various cyber-attack containment strategies that can be implemented to prevent further data breach such as affected system isolation, and securing credential and accounts. Deliver an outstanding presentation on the topic using this Cyber Containment Action Plan Checklist Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Affected System Isolation, Secure Credential And Accounts, Determine Compromised Devices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security Threat
Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the cyber security attack risk assessment matrix which can be leveraged to determine the severity of cyber threats, the likelihood of occurrence, and future action plan. Present the topic in a bit more detail with this Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Assessment Matrix, Occurrence, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Incident Channels For Customers Business Recovery Plan To Overcome Cyber Security Threat
Cyber Incident Channels For Customers Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various communication channels that can be used by company to inform customers about cyber security such as social media, website blogs, and text message. Present the topic in a bit more detail with this Cyber Incident Channels For Customers Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Communication, Incident Information, Grammatical. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Incident Response Budget Allocation Business Recovery Plan To Overcome Cyber Security Threat
Cyber Incident Response Budget Allocation Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide demonstrates business cyber security management budget plan. It includes key allocation areas such as software and hardware solutions, managed services, training, and education. Deliver an outstanding presentation on the topic using this Cyber Incident Response Budget Allocation Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Antivirus Solution, Intrusion Prevention System, Encryption Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





