Powerpoint Templates and Google slides for Secure Blockchain
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementing Blockchain Cybersecurity Risks Mitigation Hands On Blockchain Security Risk BCT SS V
Implementing Blockchain Cybersecurity Risks Mitigation Hands On Blockchain Security Risk BCT SS VThe following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc. Present the topic in a bit more detail with this Implementing Blockchain Cybersecurity Risks Mitigation Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Reduce, Accept, Avoid. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Importance Of Cybersecurity In Blockchain Technology Hands On Blockchain Security Risk BCT SS V
Importance Of Cybersecurity In Blockchain Technology Hands On Blockchain Security Risk BCT SS VThe following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc. Introducing Importance Of Cybersecurity In Blockchain Technology Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Decentralized Architecture, Public Key Cryptography, Smart Contracts, using this template. Grab it now to reap its full benefits.
-
 Key Approaches To Protect From Honeypot Scams Hands On Blockchain Security Risk BCT SS V
Key Approaches To Protect From Honeypot Scams Hands On Blockchain Security Risk BCT SS VThe following slide illustrates some methods to protect blockchain network users from honeypot scams and implement defensive actions. It includes elements such as no dead coins, audits, check social media, scrutinize website, etc. Increase audience engagement and knowledge by dispensing information using Key Approaches To Protect From Honeypot Scams Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Audits, Check Social Media, Scrutinize Website using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Scenarios Of Sybil Attack On Blockchain Network Hands On Blockchain Security Risk BCT SS V
Key Scenarios Of Sybil Attack On Blockchain Network Hands On Blockchain Security Risk BCT SS VThe following slide showcases major scenarios of sybil attack to minimize the impact and manage operations. It includes elements such as attack on bitcoin network, tor network, peer-to-peer model, etc. Introducing Key Scenarios Of Sybil Attack On Blockchain Network Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Attack On Bitcoin Network, Attack On Tor Network, using this template. Grab it now to reap its full benefits.
-
 Key Statistics Associated With Blockchain Scams Hands On Blockchain Security Risk BCT SS V
Key Statistics Associated With Blockchain Scams Hands On Blockchain Security Risk BCT SS VThe following slide depicts key facts related with blockchain frauds to ensure secure transactions. It includes elements such as hacking of decentralized finance, stolen funds, fraudulent schemes, cryptocurrency scams, etc. Increase audience engagement and knowledge by dispensing information using Key Statistics Associated With Blockchain Scams Hands On Blockchain Security Risk BCT SS V. This template helps you present information on six stages. You can also present information on Digital Assets, Cybersecurity Violations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Leverage Cryptography To Boost Privacy And Confidentiality Hands On Blockchain Security Risk BCT SS V
Leverage Cryptography To Boost Privacy And Confidentiality Hands On Blockchain Security Risk BCT SS VThe following slide showcases how cryptography assists in securing blockchain transactions and maintaining confidentiality. It includes elements such as data confidentiality, data integrity, digital signatures, consensus mechanism, etc. Introducing Leverage Cryptography To Boost Privacy And Confidentiality Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Confidentiality, Data Integrity, Digital Signatures, using this template. Grab it now to reap its full benefits.
-
 Major Cryptocurrency And Blockchain Cybersecurity Scams Hands On Blockchain Security Risk BCT SS V
Major Cryptocurrency And Blockchain Cybersecurity Scams Hands On Blockchain Security Risk BCT SS VThe following slide showcases major cryptocurrency and blockchain cybersecurity scams throughout the globe. It includes elements such as decentralized autonomous organization DAO attack, GOX attack, plus token scams, etc. Increase audience engagement and knowledge by dispensing information using Major Cryptocurrency And Blockchain Cybersecurity Scams Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Attack Hack, Attack, Plus Token Scam using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
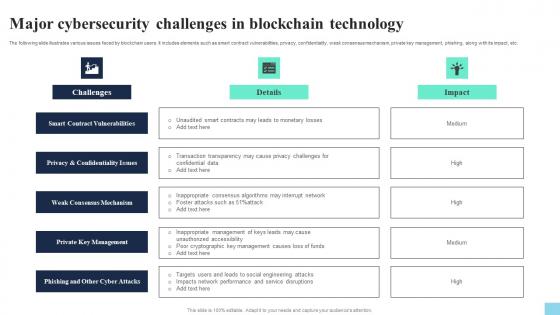 Major Cybersecurity Challenges In Blockchain Technology Hands On Blockchain Security Risk BCT SS V
Major Cybersecurity Challenges In Blockchain Technology Hands On Blockchain Security Risk BCT SS VThe following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc. Introducing Major Cybersecurity Challenges In Blockchain Technology Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Smart Contract Vulnerabilities, Weak Consensus Mechanism, Private Key Management, using this template. Grab it now to reap its full benefits.
-
 Methods To Avoid Sybil Attack For Protecting Tokens Hands On Blockchain Security Risk BCT SS V
Methods To Avoid Sybil Attack For Protecting Tokens Hands On Blockchain Security Risk BCT SS VThe following slide illustrates various ways to minimize and prevent sybil attacks and ensure safe blockchain transactions. It includes elements such as identity validation, hierarchical, defense system, cost of new nodes, social trust graphs, etc. Increase audience engagement and knowledge by dispensing information using Methods To Avoid Sybil Attack For Protecting Tokens Hands On Blockchain Security Risk BCT SS V. This template helps you present information on five stages. You can also present information on Identity Validation, Defense System, Cost Of New Node using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Methods To Ensure Smart Contract Security Hands On Blockchain Security Risk BCT SS V
Methods To Ensure Smart Contract Security Hands On Blockchain Security Risk BCT SS VThe following slide showcases some tips and practices to ensure smart contract security. It includes elements such as careful rollouts, keeping them simple, updating and monitoring new developments, reviewing fundamental tradeoffs, etc. Introducing Methods To Ensure Smart Contract Security Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Careful Rollouts, Contracts Simple, Review Fundamental Tradeoffs, using this template. Grab it now to reap its full benefits.
-
 Methods To Identify Crypto Phishing Scams Hands On Blockchain Security Risk BCT SS V
Methods To Identify Crypto Phishing Scams Hands On Blockchain Security Risk BCT SS VThe following slide illustrates various methods to determine blockchain phishing attack and safeguard confidential information. It includes elements such as copycatting, spellings, ambiguous links, using public email ID, disordered content etc. Increase audience engagement and knowledge by dispensing information using Methods To Identify Crypto Phishing Scams Hands On Blockchain Security Risk BCT SS V. This template helps you present information on five stages. You can also present information on Copycatting, Spelling, Ambiguous Links using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview And Categories Of Sybil Attack On Blockchain Network Hands On Blockchain Security Risk BCT SS V
Overview And Categories Of Sybil Attack On Blockchain Network Hands On Blockchain Security Risk BCT SS VThe following slide illustrates brief introduction of sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc. Introducing Overview And Categories Of Sybil Attack On Blockchain Network Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Direct Sybil Attack, Indirect Sybil Attack, using this template. Grab it now to reap its full benefits.
-
 Overview And Impact Of Blockchain Routing Attacks Hands On Blockchain Security Risk BCT SS V
Overview And Impact Of Blockchain Routing Attacks Hands On Blockchain Security Risk BCT SS VThe following slide illustrates the brief introduction of routing attacks to reduce leakage of information. It includes elements such as interrupting communication between nodes, delaying blockchain delivery, breaking network into two or more parts, etc. Increase audience engagement and knowledge by dispensing information using Overview And Impact Of Blockchain Routing Attacks Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Interrupts Communication, Breaks Blockchain, Delays Blockchain Delivery using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview And Key Levels Of Honeypot Crypto Frauds Hands On Blockchain Security Risk BCT SS V
Overview And Key Levels Of Honeypot Crypto Frauds Hands On Blockchain Security Risk BCT SS VThe following slide illustrates brief introduction of honeypot scams to determine malicious activities and mitigate risks. It includes elements such as Ethereum virtual machine, solidity compiler, Ethers can blockchain explorer, etc. Introducing Overview And Key Levels Of Honeypot Crypto Frauds Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Virtual Machine, Solidity Compiler, Etherscan Blockchain Explorer, using this template. Grab it now to reap its full benefits.
-
 Overview And Workflow Of Blockchain Cybersecurity Technology Hands On Blockchain Security Risk BCT SS V
Overview And Workflow Of Blockchain Cybersecurity Technology Hands On Blockchain Security Risk BCT SS VThe following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Increase audience engagement and knowledge by dispensing information using Overview And Workflow Of Blockchain Cybersecurity Technology Hands On Blockchain Security Risk BCT SS V. This template helps you present information on seven stages. You can also present information on Transaction Requested, Created Transaction, Existing Blockchain using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS V
Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS VThe following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer-to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. Introducing Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Enabled Attack, Achieve Control, Incoming And Outgoing, using this template. Grab it now to reap its full benefits.
-
 Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS V
Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS VThe following slide illustrates brief introduction of distributed denial of service DDOS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. Increase audience engagement and knowledge by dispensing information using Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Website Hostage, Close The Attack, Inability To Resolve using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of Blockchain 51 Percent Attack With Workflow Hands On Blockchain Security Risk BCT SS V
Overview Of Blockchain 51 Percent Attack With Workflow Hands On Blockchain Security Risk BCT SS VThe following slide showcases brief introduction of 51percentage attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc. Introducing Overview Of Blockchain 51 Percent Attack With Workflow Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain Network, Public Network, using this template. Grab it now to reap its full benefits.
-
 Overview Of Phishing Attack In Blockchain Technology Hands On Blockchain Security Risk BCT SS V
Overview Of Phishing Attack In Blockchain Technology Hands On Blockchain Security Risk BCT SS VThe following slide illustrates brief introduction of phishing attacks impacting Blockchain to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Increase audience engagement and knowledge by dispensing information using Overview Of Phishing Attack In Blockchain Technology Hands On Blockchain Security Risk BCT SS V. This template helps you present information on five stages. You can also present information on Fake Links, Investment Opportunities, Towards Fake Website using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Performing Threat Assessment For Cause Identification Hands On Blockchain Security Risk BCT SS V
Performing Threat Assessment For Cause Identification Hands On Blockchain Security Risk BCT SS VThe following slide illustrates brief introduction of phishing attacks impacting Blockchain to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Introducing Performing Threat Assessment For Cause Identification Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Security Threats, Attack Vectors, Causes, using this template. Grab it now to reap its full benefits.
-
 Remediation Comparative Analysis Of Various Penetration Hands On Blockchain Security Risk BCT SS V
Remediation Comparative Analysis Of Various Penetration Hands On Blockchain Security Risk BCT SS VThe following slide depicts comparative analysis of penetration tools to remediate cybersecurity vulnerabilities. It includes elements such as services, features, reviews, security audits, compliance reporting, website and network security, etc. Deliver an outstanding presentation on the topic using this Remediation Comparative Analysis Of Various Penetration Hands On Blockchain Security Risk BCT SS V. Dispense information and present a thorough explanation of Platforms, Services, Features using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Reporting Analyzing Vulnerabilities Through Penetration Hands On Blockchain Security Risk BCT SS V
Reporting Analyzing Vulnerabilities Through Penetration Hands On Blockchain Security Risk BCT SS VThe following slide depicts brief summary of penetration testing report. it includes elements such as vulnerabilities, status, severity, risk score, unpatched operating system, cross site scripting, SQL injection, weak private key policies, misconfigured firewall rules, etc. Present the topic in a bit more detail with this Reporting Analyzing Vulnerabilities Through Penetration Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Vulnerabilities, Description, Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Reviewing Consensus Mechanism To Manage Hands On Blockchain Security Risk BCT SS V
Reviewing Consensus Mechanism To Manage Hands On Blockchain Security Risk BCT SS VThe following slide showcases some tips for consensus mechanism to ensure record of legitimate transactions. It includes elements such as proof of work pow, proof of stake pos, delegated pos, resolving complicated puzzles, verifying transactions, sharing monetary risks, etc. Introducing Reviewing Consensus Mechanism To Manage Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Proof Of Work, Proof Of Stake, Delegated Pos, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Hands On Blockchain Security Risk Management And Best Practices BCT SS V
Table Of Contents Hands On Blockchain Security Risk Management And Best Practices BCT SS VIncrease audience engagement and knowledge by dispensing information using Table Of Contents Hands On Blockchain Security Risk Management And Best Practices BCT SS V. This template helps you present information on one stages. You can also present information on Industry Overview, Blockchain Cybersecurity, Blockchain Cyber Security Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Techniques To Prevent Eclipse Attack And Secure Funds Hands On Blockchain Security Risk BCT SS V
Techniques To Prevent Eclipse Attack And Secure Funds Hands On Blockchain Security Risk BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Introducing Techniques To Prevent Eclipse Attack And Secure Funds Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Random Node Selection, Deterministic Node Selection, New Node Restrictions, using this template. Grab it now to reap its full benefits.
-
 Threats Imposed By Sybil Attack On Blockchain Network Hands On Blockchain Security Risk BCT SS V
Threats Imposed By Sybil Attack On Blockchain Network Hands On Blockchain Security Risk BCT SS VThe following slide highlights major issues faced by users due to sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percentage attack, etc. Increase audience engagement and knowledge by dispensing information using Threats Imposed By Sybil Attack On Blockchain Network Hands On Blockchain Security Risk BCT SS V. This template helps you present information on three stages. You can also present information on Block Users From Network, Attack, Breach Of Privacy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Types Of Crypto Phishing Attacks Contd Hands On Blockchain Security Risk BCT SS V
Various Types Of Crypto Phishing Attacks Contd Hands On Blockchain Security Risk BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as pharming attack, evil twin, voice and SMS phishing, etc. Introducing Various Types Of Crypto Phishing Attacks Contd Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Pharming Attack, Evil Twin, Sms Phishing, using this template. Grab it now to reap its full benefits.
-
 Various Types Of Crypto Phishing Attacks Hands On Blockchain Security Risk BCT SS V
Various Types Of Crypto Phishing Attacks Hands On Blockchain Security Risk BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Crypto Phishing Attacks Hands On Blockchain Security Risk BCT SS V. This template helps you present information on three stages. You can also present information on Spear Phishing, Whaling Phishing, Clone Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ways To Minimize 51 Percent Attacks And Optimize Hash Rate Hands On Blockchain Security Risk BCT SS V
Ways To Minimize 51 Percent Attacks And Optimize Hash Rate Hands On Blockchain Security Risk BCT SS VThe following slide illustrates various methods to reduce the impact of 51percentage attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc. Introducing Ways To Minimize 51 Percent Attacks And Optimize Hash Rate Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Constant Updates, Leverage Proof Of Stake, Perform Security Audits, using this template. Grab it now to reap its full benefits.
-
 Ways To Prevent Blockchain Routing Attacks Hands On Blockchain Security Risk BCT SS V
Ways To Prevent Blockchain Routing Attacks Hands On Blockchain Security Risk BCT SS VThe following slide illustrates some methods to minimize blockchain routing attacks to safeguard network from wrong routing table. It includes elements such as strong passwords, updating firmware, managing access control lists, monitoring logs, etc. Increase audience engagement and knowledge by dispensing information using Ways To Prevent Blockchain Routing Attacks Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Strong Passwords, Update Firmware, Monitor using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ways To Prevent Crypto Phishing And Sensitive Hands On Blockchain Security Risk BCT SS V
Ways To Prevent Crypto Phishing And Sensitive Hands On Blockchain Security Risk BCT SS VThe following slide illustrates some methods to minimize crypto phishing attacks and. it includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Introducing Ways To Prevent Crypto Phishing And Sensitive Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Factor Authentication, Avoid Usage, Cross Check Emails, using this template. Grab it now to reap its full benefits.
-
 Most Secure Blockchain In Powerpoint And Google Slides Cpb
Most Secure Blockchain In Powerpoint And Google Slides CpbPresenting our Most Secure Blockchain In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Most Secure Blockchain. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Blockchain Security Token In Powerpoint And Google Slides Cpb
Blockchain Security Token In Powerpoint And Google Slides CpbPresenting our Blockchain Security Token In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Blockchain Security Token. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Blockchain And Cybersecurity Adopt Security Auditing Checklist To Verify Processes BCT SS V
Blockchain And Cybersecurity Adopt Security Auditing Checklist To Verify Processes BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Blockchain And Cybersecurity Adopt Security Auditing Checklist To Verify Processes BCT SS V Use it as a tool for discussion and navigation on Parameters, Description, Verify Processes This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain And Cybersecurity Backing Up Data To Enhance Security And Efficiency BCT SS V
Blockchain And Cybersecurity Backing Up Data To Enhance Security And Efficiency BCT SS VThe following slide illustrates some methods to regularly backing up data to prevent primary data failures. It includes elements such as regularly backing up, offsite, automated backup and constantly monitoring, etc. Introducing Blockchain And Cybersecurity Backing Up Data To Enhance Security And Efficiency BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Regularly Backup, Automated Backup, Track Backup using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS V
Blockchain And Cybersecurity Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS VThe following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 24 7 availability, etc. Deliver an outstanding presentation on the topic using this Blockchain And Cybersecurity Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS V Dispense information and present a thorough explanation of Experience, Services, Technical Capabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
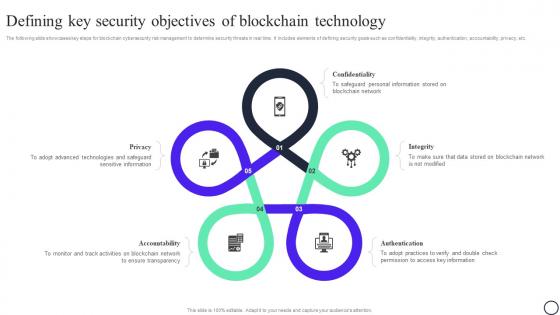 Blockchain And Cybersecurity Defining Key Security Objectives Of Blockchain Technology BCT SS V
Blockchain And Cybersecurity Defining Key Security Objectives Of Blockchain Technology BCT SS VThe following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Defining Key Security Objectives Of Blockchain Technology BCT SS V This template helps you present information on Five stages. You can also present information on Privacy, Confidentiality, Integrity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Methods To Ensure Smart Contract Security BCT SS V
Blockchain And Cybersecurity Methods To Ensure Smart Contract Security BCT SS VThe following slide showcases some tips and practices to ensure smart contract security. It includes elements such as careful rollouts, keeping them simple, updating and monitoring new developments, reviewing fundamental tradeoffs, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Methods To Ensure Smart Contract Security BCT SS V This template helps you present information on Four stages. You can also present information on New Advancements, Careful Rolloutsm Review Fundamental Tradeoffs using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V
Blockchain And Cybersecurity Techniques To Prevent Eclipse Attack And Secure Funds BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V This template helps you present information on Four stages. You can also present information on Increased Node Connections, Deterministic Node Selection, New Node Restrictions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V
Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V Dispense information and present a thorough explanation of Consensus Mechanism, Smart Contract Security, Data Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threats In Blockchain Backing Up Data To Enhance Security And Efficiency BCT SS V
Cyber Threats In Blockchain Backing Up Data To Enhance Security And Efficiency BCT SS VThe following slide illustrates some methods to regularly backing up data to prevent primary data failures. It includes elements such as regularly backing up, offsite, automated backup and constantly monitoring, etc. Introducing Cyber Threats In Blockchain Backing Up Data To Enhance Security And Efficiency BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Regularly Backup, Automated Backup, Track Backup using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS V
Cyber Threats In Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS VThe following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 247 availability, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS V Dispense information and present a thorough explanation of Experience, Services, Technical Capabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
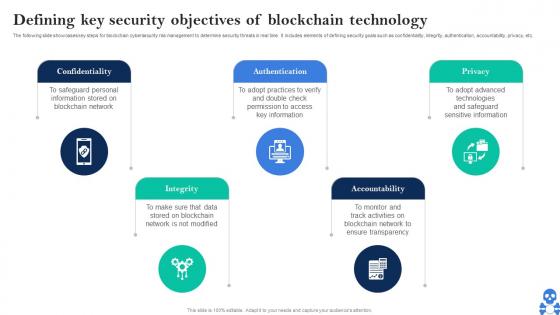 Cyber Threats In Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS V
Cyber Threats In Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS VThe following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Introducing Cyber Threats In Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, Authentication using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Methods To Ensure Smart Contract Security BCT SS V
Cyber Threats In Blockchain Methods To Ensure Smart Contract Security BCT SS VThe following slide showcases some tips and practices to ensure smart contract security. It includes elements such as careful rollouts, keeping them simple, updating and monitoring new developments, reviewing fundamental tradeoffs, etc. Introducing Cyber Threats In Blockchain Methods To Ensure Smart Contract Security BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Careful Rollouts, Contracts Simple, Monitor New Advancements using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V
Cyber Threats In Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Introducing Cyber Threats In Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Mining Capability, Mining Capabilities, Much Faster Rate using this template. Grab it now to reap its full benefits.
-
 Blockchain For Transparent And Secure Supply Chains Digital Transformation In E Commerce DT SS
Blockchain For Transparent And Secure Supply Chains Digital Transformation In E Commerce DT SSThis slide provides glimpse about process to use blockchain technology that can help ecommerce businesses to safeguard their supply chains. It includes suppliers, manufacturing, distributor, retailer, etc. Introducing Blockchain For Transparent And Secure Supply Chains Digital Transformation In E Commerce DT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Manufacturing, Distributor, Supplier, Retailer using this template. Grab it now to reap its full benefits.
-
 Adopt Security Auditing Checklist To Verify Processes Guide For Blockchain BCT SS V
Adopt Security Auditing Checklist To Verify Processes Guide For Blockchain BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Adopt Security Auditing Checklist To Verify Processes Guide For Blockchain BCT SS V Use it as a tool for discussion and navigation on Network Security, Node Security, Consensus Mechanism This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Backing Up Data To Enhance Security And Efficiency Guide For Blockchain BCT SS V
Backing Up Data To Enhance Security And Efficiency Guide For Blockchain BCT SS VThe following slide illustrates some methods to regularly backing up data to prevent primary data failures. It includes elements such as regularly backing up, offsite, automated backup and constantly monitoring, etc. Introducing Backing Up Data To Enhance Security And Efficiency Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Regularly Backup, Offsite Backup, Automated Backup using this template. Grab it now to reap its full benefits.
-
 Comparative Analysis Of Multiple Blockchain Security Vendors Guide For Blockchain BCT SS V
Comparative Analysis Of Multiple Blockchain Security Vendors Guide For Blockchain BCT SS VThe following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 24 or 7 availability, etc. Deliver an outstanding presentation on the topic using this Comparative Analysis Of Multiple Blockchain Security Vendors Guide For Blockchain BCT SS V Dispense information and present a thorough explanation of Experience, Services, Technical Capabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
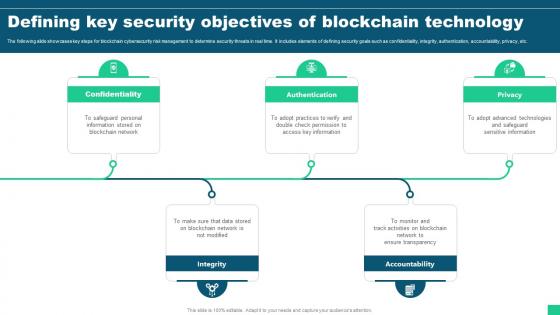 Defining Key Security Objectives Of Blockchain Technology Guide For Blockchain BCT SS V
Defining Key Security Objectives Of Blockchain Technology Guide For Blockchain BCT SS VThe following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Introducing Defining Key Security Objectives Of Blockchain Technology Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Authentication, Integrity, Accountability using this template. Grab it now to reap its full benefits.
-
 Methods To Ensure Smart Contract Security Guide For Blockchain BCT SS V
Methods To Ensure Smart Contract Security Guide For Blockchain BCT SS VThe following slide showcases some tips and practices to ensure smart contract security. It includes elements such as careful rollouts, keeping them simple, updating and monitoring new developments, reviewing fundamental tradeoffs, etc. Increase audience engagement and knowledge by dispensing information using Methods To Ensure Smart Contract Security Guide For Blockchain BCT SS V This template helps you present information on four stages. You can also present information on Careful Rollouts, Contracts Simple, Fundamental Tradeoffs using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Techniques To Prevent Eclipse Attack And Secure Funds Guide For Blockchain BCT SS V
Techniques To Prevent Eclipse Attack And Secure Funds Guide For Blockchain BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Introducing Techniques To Prevent Eclipse Attack And Secure Funds Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Random Node Selection, Deterministic Node Selection using this template. Grab it now to reap its full benefits.
-
 Y196 Hands On Blockchain Security Risk Management And Best Practices Table Of Contents BCT SS V
Y196 Hands On Blockchain Security Risk Management And Best Practices Table Of Contents BCT SS VIntroducing Y196 Hands On Blockchain Security Risk Management And Best Practices Table Of Contents BCT SS V to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain Cyber Security, Risk Management Process, using this template. Grab it now to reap its full benefits.
-
 Impact Of DDoS Attack On Targeted Servers Hands On Blockchain Security Risk BCT SS V
Impact Of DDoS Attack On Targeted Servers Hands On Blockchain Security Risk BCT SS VThe following slide depicts the adverse impact of denial of service DDOS attack to determine malicious attempt to hamper targeted server. It includes elements such as software crashes, node failure, network congestion, bloated ledger, etc. Increase audience engagement and knowledge by dispensing information using Impact Of Impact Of DDoS Attack On Targeted Servers Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Software Crashes, Node Failures, Network Congestion using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Types Of DDoS Attacks Impacting Internet Traffic Hands On Blockchain Security Risk BCT SS V
Various Types Of DDoS Attacks Impacting Internet Traffic Hands On Blockchain Security Risk BCT SS VThe following slide showcases various types of denial of service DDOS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc. Introducing Various Types Of DDoS Attacks Impacting Internet Traffic Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Volumetric Attacks, Protocol Attacks, Application Attacks, using this template. Grab it now to reap its full benefits.
-
 Various Types Of DDoS Attacks Securing Blockchain Transactions A Beginners Guide BCT SS V
Various Types Of DDoS Attacks Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases various types of denial of service DDoS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc. Introducing Various Types Of DDoS Attacks Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Volumetric Attacks, Protocol Attacks, Fragmentation Attacks, using this template. Grab it now to reap its full benefits.
-
 Ways To Minimize 51 Percent Attacks Securing Blockchain Transactions A Beginners Guide BCT SS V
Ways To Minimize 51 Percent Attacks Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates various methods to reduce the impact of 51percent attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc. Increase audience engagement and knowledge by dispensing information using Ways To Minimize 51 Percent Attacks Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on five stages. You can also present information on Constant Updates, Establish Strong Network System, Leverage Proof Stake using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ways To Prevent Blockchain Securing Blockchain Transactions A Beginners Guide BCT SS V
Ways To Prevent Blockchain Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates some methods to minimize blockchain routing attacks to safeguard network from wrong routing table. It includes elements such as strong passwords, updating firmware, managing access control lists, monitoring logs, etc. Introducing Ways To Prevent Blockchain Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strong Passwords, Update Firmware, Manage Access Control List, using this template. Grab it now to reap its full benefits.
-
 Ways To Prevent Crypto Phishing Securing Blockchain Transactions A Beginners Guide BCT SS V
Ways To Prevent Crypto Phishing Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates some methods to minimize crypto phishing attacks and . It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi fi networks, etc. Increase audience engagement and knowledge by dispensing information using Ways To Prevent Crypto Phishing Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on five stages. You can also present information on Use VPN, Cross Check Browsers URL, Cross Check Emails using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Adopt Security Auditing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS V
Adopt Security Auditing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Adopt Security Auditing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS V. Use it as a tool for discussion and navigation on Parameters, Comments, Comply Safe Communication Protocols. This template is free to edit as deemed fit for your organization. Therefore download it now.





