Powerpoint Templates and Google slides for Protection Of Data
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Datafication Of HR Measures Taken For Data Protection In Cloud Globally
Datafication Of HR Measures Taken For Data Protection In Cloud GloballyThis slide represents the measures taken for data protection in the cloud worldwide, covering multi-factor authentication, cloud backup, encryption, employee training, auditing of user activity, review of access rights, data classification, and removing sensitive data from the cloud. Deliver an outstanding presentation on the topic using this Datafication Of HR Measures Taken For Data Protection In Cloud Globally. Dispense information and present a thorough explanation of Measures, Protection, Authentication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
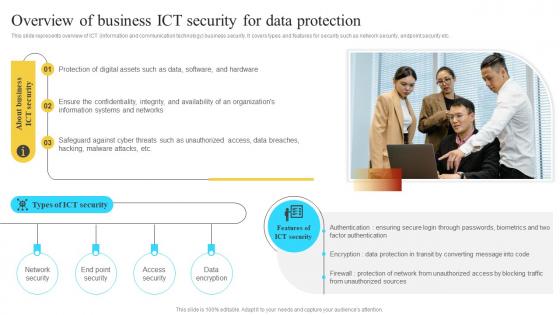 Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V
Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Protection Of Digital, Safeguard Against Cyber, using this template. Grab it now to reap its full benefits.
-
 Impact Of Digital Therapeutics On Data Protection Digital Therapeutics Regulatory
Impact Of Digital Therapeutics On Data Protection Digital Therapeutics RegulatoryThis slide talks about the positive and negative impact of digital therapeutics on information protection. The negative includes the regular patient observation and profiling, the significant impact of personal information breaches, and security issues due to complexity. Introducing Impact Of Digital Therapeutics On Data Protection Digital Therapeutics Regulatory to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Positive, Negative, using this template. Grab it now to reap its full benefits.
-
 Impact analysis of data protection to meet GDPR requirements
Impact analysis of data protection to meet GDPR requirementsThis slide highlights data protection impact assessment to meet GDPR requirements. The purpose of this slide is to support businesses in meeting GDPR compliance requirements. It provides details changes, sources of data risk, probability and degree of harm, etc. Presenting our well structured Impact analysis of data protection to meet GDPR requirements. The topics discussed in this slide are Inadequate Documentation, Comprehensive Inventory, Update Privacy. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Digital Therapeutics Development Impact Of Digital Therapeutics On Data Protection
Digital Therapeutics Development Impact Of Digital Therapeutics On Data ProtectionThis slide talks about the positive and negative impact of digital therapeutics on information protection. The negative includes the regular patient observation and profiling, the significant impact of personal information breaches, and security issues due to complexity. Introducing Digital Therapeutics Development Impact Of Digital Therapeutics On Data Protection to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Positive, Negative, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Challenges Of Data In Use Protection And Solutions
Encryption Implementation Strategies Challenges Of Data In Use Protection And SolutionsThis slide outlines the various limitations of data in use protection and their possible solutions. These include limited control after data access, unauthorized copying or sharing of data, limitations of collaboration platforms, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Challenges Of Data In Use Protection And Solutions. Use it as a tool for discussion and navigation on Limitations Of Collaboration Platforms, Unauthorized Copying Or Sharing Of Data, Limited Control After Data Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Different States Of Data Which Requires Protection
Encryption Implementation Strategies Different States Of Data Which Requires ProtectionThis slide discusses various customer demands to ensure data privacy and authenticity. The purpose of this slide is to highlight the various states of data that require encryption, such as data-at-rest, data-in-transit, and data-in-use. Introducing Encryption Implementation Strategies Different States Of Data Which Requires Protection to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Customer Demands, Data Privacy And Authenticity, Require Encryption, Collaboration Software, using this template. Grab it now to reap its full benefits.
-
 Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V
Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Request Fulfillment using this template. Grab it now to reap its full benefits.
-
 Extensive Business Strategy Other Cyber Strategies Of KPMG For Client Data Protection Strategy SS V
Extensive Business Strategy Other Cyber Strategies Of KPMG For Client Data Protection Strategy SS VThis slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. Increase audience engagement and knowledge by dispensing information using Extensive Business Strategy Other Cyber Strategies Of KPMG For Client Data Protection Strategy SS V. This template helps you present information on five stages. You can also present information on Threat Landscape, Cyber Security, Governance Framework using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Digital Therapeutics Functions Impact Of Digital Therapeutics On Data Protection
Digital Therapeutics Functions Impact Of Digital Therapeutics On Data ProtectionThis slide talks about the positive and negative impact of digital therapeutics on information protection. The negative includes the regular patient observation and profiling, the significant impact of personal information breaches, and security issues due to complexity. Introducing Digital Therapeutics Functions Impact Of Digital Therapeutics On Data Protection to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Positive, Negative, Data Protection using this template. Grab it now to reap its full benefits.
-
 Data Security Strategies To Protect Retail Customer Digital Transformation Of Retail DT SS
Data Security Strategies To Protect Retail Customer Digital Transformation Of Retail DT SSThis slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Increase audience engagement and knowledge by dispensing information using Data Security Strategies To Protect Retail Customer Digital Transformation Of Retail DT SS This template helps you present information on six stages. You can also present information on Customer Data Protection, Online Transactions, Management Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implement General Data Protection Regulation Digital Transformation Of Retail DT SS
Implement General Data Protection Regulation Digital Transformation Of Retail DT SSThis slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance. Introducing Implement General Data Protection Regulation Digital Transformation Of Retail DT SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Ongoing Compliance, Data Security, Consent And Legal Basis using this template. Grab it now to reap its full benefits.
-
 Digital Therapeutics Adoption Challenges Impact Of Digital Therapeutics On Data Protection
Digital Therapeutics Adoption Challenges Impact Of Digital Therapeutics On Data ProtectionThis slide talks about the positive and negative impact of digital therapeutics on information protection. The negative includes the regular patient observation and profiling, the significant impact of personal information breaches, and security issues due to complexity. Present the topic in a bit more detail with this Digital Therapeutics Adoption Challenges Impact Of Digital Therapeutics On Data Protection. Use it as a tool for discussion and navigation on Digital Therapeutics, Patient Observation And Profiling, Personal Information Breaches, Data Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Digital Therapeutics Types Impact Of Digital Therapeutics On Data Protection Ppt Professional
Digital Therapeutics Types Impact Of Digital Therapeutics On Data Protection Ppt ProfessionalThis slide talks about the positive and negative impact of digital therapeutics on information protection. The negative includes the regular patient observation and profiling, the significant impact of personal information breaches, and security issues due to complexity. Introducing Digital Therapeutics Types Impact Of Digital Therapeutics On Data Protection Ppt Professional to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Positive, Negative, Regular Patient Observation, using this template. Grab it now to reap its full benefits.
-
 Implementation Stats Of Big Data Analytics For Cyber Protection
Implementation Stats Of Big Data Analytics For Cyber ProtectionThe following slide highlights key points like prioritizing, training, improving, and security infrastructure to show implementation stats of big data analytics for cybersecurity. It helps organizations to enhance cyber threat detection and response capabilities. Presenting our set of slides with Implementation Stats Of Big Data Analytics For Cyber Protection. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implementation, Data Analytics, Cybersecurity.
-
 Configurations Of Storage Virtualization To Protect Data
Configurations Of Storage Virtualization To Protect DataThis slide showcases the con figurations of storage virtualization securing important and sensitive data which helps an organization to reduce hardware costs and distributors lock-ins. It include details such as in-band symmetric and out band asymmetric approach. Presenting our set of slides with name Configurations Of Storage Virtualization To Protect Data. This exhibits information on Two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on In Band Approach Symmetric, Out Band Approach Asymmetric.
-
 Types Of Wireless Internet Security For Data Protection
Types Of Wireless Internet Security For Data ProtectionThe following slide highlights key points such as WEP, WPA, WPA2, and WPA3 protocols to show types of wireless internet security for privacy protection. It helps in understanding and comparing different safety procedures for effective data protection. Introducing our premium set of slides with Types Of Wireless Internet Security For Data Protection. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Protection, Wireless Internet. So download instantly and tailor it with your information.
-
 Steps Of Cybersecurity Firewall To Protect Business Data
Steps Of Cybersecurity Firewall To Protect Business DataThis slide showcases the effective guidelines of cybersecurity firewall for securing organizational data which helps an organization to employ new updated policies easily and quickly. It include details such as introduce incoming connections, track audit logs, etc. Presenting our well structured Steps Of Cybersecurity Firewall To Protect Business Data. The topics discussed in this slide are Effective Steps, Techniques, Business Data. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Impact Of Encryption On Various Industries For Data Protection
Impact Of Encryption On Various Industries For Data ProtectionThis slide represents impact of encryption in various industries which assists organization to protect their financial data and customers information. It includes impact of encryption in various industries such as financial services, government, manufacturing, etc. Presenting our well structured Impact Of Encryption On Various Industries For Data Protection. The topics discussed in this slide are Financial Services, Government, Manufacturing. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Applications Of SCADA Cybersecurity Tools For Data Protection
Applications Of SCADA Cybersecurity Tools For Data ProtectionThis slide represents various applications of SCADA cybersecurity tools that assist IT companies to enhance their data protection effectively. It includes various applications such as data encryption, vulnerability assessment, etc. Introducing our premium set of slides with Applications Of SCADA Cybersecurity Tools For Data Protection Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Intrusion Detection Systems, Firewalls And Network Segmentation, Encryption And Secure Protocols. So download instantly and tailor it with your information.
-
 Working Model Of SCADA Cybersecurity For Data Protection
Working Model Of SCADA Cybersecurity For Data ProtectionThis slide represents working model of SCADA cybersecurity that assists IT companies to secure their data from vulnerable attacks. It includes various components such as impact analysis, mitigation strategies, etc. Presenting our well structured Working Model Of SCADA Cybersecurity For Data Protection The topics discussed in this slide are Remedial, Prevention, Decision Making. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 DTx Enablers Impact Of Digital Therapeutics On Data Protection
DTx Enablers Impact Of Digital Therapeutics On Data ProtectionThis slide talks about the positive and negative impact of digital therapeutics on information protection. The negative includes the regular patient observation and profiling, the significant impact of personal information breaches, and security issues due to complexity. Present the topic in a bit more detail with this DTx Enablers Impact Of Digital Therapeutics On Data Protection. Use it as a tool for discussion and navigation on Market Structure, Technology, Data Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Significance Of Cloud Storage Management For Data Protection
Significance Of Cloud Storage Management For Data ProtectionThis slide highlights importance of online storage management techniques. The purpose of this slide is to enable organizations in understanding the derived benefits from using cloud storage for ensuring efficient operations. It includes elements such as security, compliance, etc. Introducing our premium set of slides with Significance Of Cloud Storage Management For Data Protection. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security, Compliance, Data Governance. So download instantly and tailor it with your information.
-
 Different Types Of Visualization Security For Protecting Data
Different Types Of Visualization Security For Protecting DataThis slides showcases various types of visualization data. The main purpose of this template is to showcase data encryption for shared data. This includes role based access control, encrypted file sharing, regular security audits, etc. Introducing our premium set of slides with Different Types Of Visualization Security For Protecting Data. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Methods, Regular Security Audits, Encrypted File Sharing. So download instantly and tailor it with your information.
-
 Major Components Of IP Security To Protect Sensitive Data
Major Components Of IP Security To Protect Sensitive DataThis slide showcases key elements of IP security for protecting data. The main purpose of this template is to showcase protection and trustworthiness of data. This includes encapsulating security payload, authentication header, and internet key exchange. Presenting our set of slides with name Major Components Of IP Security To Protect Sensitive Data. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Internet Key Exchange, Authentication Header, Encapsulating Security Payload.
-
 Major Types Of Cybersecurity Policy To Protect Data
Major Types Of Cybersecurity Policy To Protect DataThis slide showcases the important types of cybersecurity policy securing sensitive information which helps an organization to regulate compliance and ensure providing better data management. It include details such as account management, anti-virus, email policy, etc. Presenting our set of slides with Major Types Of Cybersecurity Policy To Protect Data This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Systems Acceptable Use Policy, Account Management Policy
-
 Types Of Cybersecurity Ethical Issues Affecting Data Protection
Types Of Cybersecurity Ethical Issues Affecting Data ProtectionThis slide represents various actions to mitigate multiple cybersecurity ethical issues assisting companies to enhance corporate and customer data protection. It includes issues such as harm to privacy, harm to property, transparency, etc. Presenting our well structured Types Of Cybersecurity Ethical Issues Affecting Data Protection. The topics discussed in this slide are Details, Actions By Professional, Priority. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Applications Of Cyber Security In Banking For Data Protection
Applications Of Cyber Security In Banking For Data ProtectionThis slide represents cyber security applications in banking for data protection. This template aims to safeguard data and systems, ensure variety of cyber security tools and methodologies at access. It includes different approaches such as network security surveillance, software security, etc. Introducing our Applications Of Cyber Security In Banking For Data Protection set of slides. The topics discussed in these slides are Network Security Surveillance, Software Security, Risk Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices Of Saas Governance For Enhancing Data Protection
Best Practices Of Saas Governance For Enhancing Data ProtectionThis slide represents various best practices that assist companies in implementing Software as a Service SaaS governance to enhance sensitive data security. It includes various practices such as information security policies, asset management, access control, etc. Introducing our Best Practices Of Saas Governance For Enhancing Data Protection set of slides. The topics discussed in these slides are Information Security Policies, Organization Of Information Security, Asset Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Mobile Device Security For Data Protection Table Of Contents Cybersecurity SS
Mobile Device Security For Data Protection Table Of Contents Cybersecurity SSIntroducing Mobile Device Security For Data Protection Table Of Contents Cybersecurity SS to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Target Devices, Target Employees, Encryption Technique Used using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Mobile Device Security For Data Protection Cybersecurity SS
Table Of Contents For Mobile Device Security For Data Protection Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Mobile Device Security For Data Protection Cybersecurity SS This template helps you present information on Five stages. You can also present information on Financial Companies, Million Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Major Categories Of Cyberterrorism For Data Protection Strategic Guide To Implement Strategy SS
Major Categories Of Cyberterrorism For Data Protection Strategic Guide To Implement Strategy SSThis slide showcases the major categories of cyber terrorism for data protection. It includes categories such as simple and unstructured, advanced-structure and complex-coordinated.Present the topic in a bit more detail with this Major Categories Of Cyberterrorism For Data Protection Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Advanced Structure, Complex Coordinated, Categories, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Architecture Of Cloud Security Cloud Data Protection
Architecture Of Cloud Security Cloud Data ProtectionThis slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an outstanding presentation on the topic using this Architecture Of Cloud Security Cloud Data Protection. Dispense information and present a thorough explanation of Infrastructure Security, Monitoring, Processing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Data Protection Architecture Of Cloud Security
Cloud Data Protection Architecture Of Cloud SecurityThis slide defines the architecture of the cloud security system and how data is kept, managed, and secured based on customer and service providers responsibilities. Increase audience engagement and knowledge by dispensing information using Cloud Data Protection Architecture Of Cloud Security. This template helps you present information on two stages. You can also present information on Customer Data, Customer Responsibility, Cloud Service using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Data Protection Essential Pillars Of Cloud Security
Cloud Data Protection Essential Pillars Of Cloud SecurityThis slide shows the four essential pillars of cloud security, namely visibility and consistency, process based security, network security, and identity security. Introducing Cloud Data Protection Essential Pillars Of Cloud Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Process Based Security, Network Security, Identity Security, using this template. Grab it now to reap its full benefits.
-
 Cloud Data Protection What Are The Downsides Of A Cloud Security
Cloud Data Protection What Are The Downsides Of A Cloud SecurityThis slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Introducing Cloud Data Protection What Are The Downsides Of A Cloud Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Data Security, Organizations, Data Breaches, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Loss Of Data Cloud Data Protection
Cloud Security Threats Loss Of Data Cloud Data ProtectionThis slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Loss Of Data Cloud Data Protection. This template helps you present information on four stages. You can also present information on Storage Locations, Organization, Strategies using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Pillars Of Cloud Security Identity Security Cloud Data Protection
Pillars Of Cloud Security Identity Security Cloud Data ProtectionThis slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss. Increase audience engagement and knowledge by dispensing information using Pillars Of Cloud Security Identity Security Cloud Data Protection. This template helps you present information on four stages. You can also present information on Pillars Of Cloud Security Identity Security using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Pillars Of Cloud Security Network Security Cloud Data Protection
Pillars Of Cloud Security Network Security Cloud Data ProtectionThis slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks. Introducing Pillars Of Cloud Security Network Security Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Micro Segmentation, Operations, Security, using this template. Grab it now to reap its full benefits.
-
 Pillars Of Cloud Security Process Based Security Cloud Data Protection
Pillars Of Cloud Security Process Based Security Cloud Data ProtectionThis slide represents the process-based security pillar of cloud security. It also shows how it works and what precautions does it take. Increase audience engagement and knowledge by dispensing information using Pillars Of Cloud Security Process Based Security Cloud Data Protection. This template helps you present information on four stages. You can also present information on Operational Security, Management, Operations using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Pillars Of Cloud Security Visibility And Consistency Cloud Data Protection
Pillars Of Cloud Security Visibility And Consistency Cloud Data ProtectionThis slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security. Introducing Pillars Of Cloud Security Visibility And Consistency Cloud Data Protection to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispense information on Cloud Framework, Data Security, Asset Inventory, using this template. Grab it now to reap its full benefits.
-
 Roadmap Of Cloud Security Implementation Cloud Data Protection
Roadmap Of Cloud Security Implementation Cloud Data ProtectionThis slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Introducing Roadmap Of Cloud Security Implementation Cloud Data Protection to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispense information on Cloud Services Monitoring, Services Management, Database Security Measures, Network Security, using this template. Grab it now to reap its full benefits.
-
 Segmentation Of Cloud Security Responsibilities Cloud Data Protection
Segmentation Of Cloud Security Responsibilities Cloud Data ProtectionThis slide shows cloud security responsibilities based on service type, namely Software as a Service SaaS, Platform as a service PaaS, Infrastructure as a Service IaaS. Increase audience engagement and knowledge by dispensing information using Segmentation Of Cloud Security Responsibilities Cloud Data Protection. This template helps you present information on three stages. You can also present information on Segmentation Of Cloud Security Responsibilities using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Table Of Contents For Cloud Data Protection Ppt Demonstration
Table Of Contents For Cloud Data Protection Ppt DemonstrationIntroducing Table Of Contents For Cloud Data Protection Ppt Demonstration to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispense information on Benefits Of Cloud Security, Architecture Of Cloud Security, Cloud Security Important, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Cloud Data Protection Ppt Powerpoint Icons
Table Of Contents For Cloud Data Protection Ppt Powerpoint IconsIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Cloud Data Protection Ppt Powerpoint Icons. This template helps you present information on eleven stages. You can also present information on Cloud Security Responsibilities, Cloud Security Management, Working Of Cloud Security using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Theft Or Loss Of Intellectual Property Cloud Data Protection
Theft Or Loss Of Intellectual Property Cloud Data ProtectionThis slide represents the loss of intellectual property threat and how organizations get affected by these types of risks. Introducing Theft Or Loss Of Intellectual Property Cloud Data Protection to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispense information on Businesses Experience, Organizations, Cloud Storage, using this template. Grab it now to reap its full benefits.
-
 Types Of Cloud Security Solutions Cloud Data Protection
Types Of Cloud Security Solutions Cloud Data ProtectionThis slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions. Increase audience engagement and knowledge by dispensing information using Types Of Cloud Security Solutions Cloud Data Protection. This template helps you present information on three stages. You can also present information on Enterprise Cloud Security, Hybrid Cloud Security, Cloud Security using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 What Are The Benefits Of A Cloud Security System Cloud Data Protection
What Are The Benefits Of A Cloud Security System Cloud Data ProtectionThis slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security. Introducing What Are The Benefits Of A Cloud Security System Cloud Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Efficient Recovery, Efficient Data Security, Business Capacity, using this template. Grab it now to reap its full benefits.
-
 Icon Of Security Incident Management For Data Protection
Icon Of Security Incident Management For Data ProtectionIntroducing our premium set of slides with Icon Of Security Incident Management For Data Protection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Of Security Incident, Management For Data ProtectionIcon Of Security Incident, Management For Data Protection. So download instantly and tailor it with your information.
-
 Elements Of Successful Enterprise Data Protection Policy
Elements Of Successful Enterprise Data Protection PolicyThis slide showcases elements of data protection policy. It includes data risk management, backup, breach prevention, cybersecurity management, monitoring and reviewing. Introducing our premium set of slides with Elements Of Successful Enterprise Data Protection Policy. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Risk Management, Data Breach Prevention, Monitoring And Reviewing. So download instantly and tailor it with your information.
-
 Key Drivers Of Data Protection And Policy
Key Drivers Of Data Protection And PolicyThe following slide showcases data protection drivers to assist businesses with their legitimate use of personal data. The drivers covered are data location, sensitivity, protection, access and flow. Presenting our set of slides with Key Drivers Of Data Protection And Policy. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Location, Data Sensitivity, Data Protection, Data Access.
-
 Model For Protection And Security Of Healthcare Data
Model For Protection And Security Of Healthcare DataThis slide depicts the flowchart used for explaining the process of protecting the healthcare data. The purpose of this template is to define a model used for maintaining privacy and confidentiality of health data. It includes information related to security, trust, confidentiality and privacy. Introducing our Model For Protection And Security Of Healthcare Data set of slides. The topics discussed in these slides are Security, Trust, Confidentiality, Privacy. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Digital Therapeutics It Impact Of Digital Therapeutics On Data Protection Ppt Show Microsoft
Digital Therapeutics It Impact Of Digital Therapeutics On Data Protection Ppt Show MicrosoftThis slide talks about the positive and negative impact of digital therapeutics on information protection. The negative includes the regular patient observation and profiling, the significant impact of personal information breaches, and security issues due to complexity. Increase audience engagement and knowledge by dispensing information using Digital Therapeutics It Impact Of Digital Therapeutics On Data Protection Ppt Show Microsoft This template helps you present information on two stages. You can also present information on Security Issues, Result, Significant Impact, Observation And Profiling using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of Business ICT Security Data Protection Implementation ICT Strategic Plan Strategy SS
Overview Of Business ICT Security Data Protection Implementation ICT Strategic Plan Strategy SSThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc.Present the topic in a bit more detail with this Overview Of Business ICT Security Data Protection Implementation ICT Strategic Plan Strategy SS. Use it as a tool for discussion and navigation on Factor Authentication, Organizations Information, Ensure Confidentiality. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Business ICT Security For Data Protection ICT Strategic Framework Strategy SS V
Overview Of Business ICT Security For Data Protection ICT Strategic Framework Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Present the topic in a bit more detail with this Overview Of Business ICT Security For Data Protection ICT Strategic Framework Strategy SS V. Use it as a tool for discussion and navigation on Network Security, Access Security, Data Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Protect the carton data management settings of document search ppt icons graphics
Protect the carton data management settings of document search ppt icons graphicsPresenting protect the carton data management settings of document search ppt icons graphics. This Power Point icons template slide has been crafted with graphic of four data icons. This PPT diagram contains the concept of protection and data management . Use this PPT diagram for business and marketing related presentations.
-
 Shopping basket size protected data afraid of water ppt icons graphics
Shopping basket size protected data afraid of water ppt icons graphicsPresenting shopping basket size protected data afraid of water ppt icons graphics. This Power Point icon template has been crafted with graphic of shopping basket and data icons. This PPT icon slide contains the concept of data protection and shopping skills representation. This icon template diagram can be used for sales and safety related presentations.
-
 Icon of data governance protection with contract file
Icon of data governance protection with contract fileIntroducing our premium set of slides with Icon Of Data Governance Protection With Contract File. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Of Data Governance Protection With Contract File. So download instantly and tailor it with your information.
-
 Icon depicting protection of datacenter from external threats
Icon depicting protection of datacenter from external threatsIntroducing our premium set of slides with Icon Depicting Protection Of Datacenter From External Threats. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Depicting Protection Of Datacenter From External Threats. So download instantly and tailor it with your information.
-
 Four steps arrow process of video call data protection infographic template
Four steps arrow process of video call data protection infographic templateThis is a single slide titled Four Steps Arrow Process Of Video Call Data Protection Infographic Template. It is crafted using high quality vector based visuals that are 100 percent editable and available for immediate download in standard and widescreen aspect ratios.




