Powerpoint Templates and Google slides for Protect Data
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Technologies Used To Protect Data In Use Confidential Computing System Technology
Technologies Used To Protect Data In Use Confidential Computing System TechnologyThis slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Deliver an outstanding presentation on the topic using this Technologies Used To Protect Data In Use Confidential Computing System Technology. Dispense information and present a thorough explanation of Technologies, Security Comparison, Scalability Comparison using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
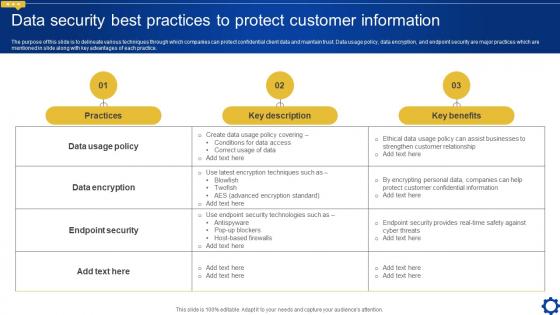 Data Security Best Practices To Protect Customer Creating Personalized Marketing Messages MKT SS V
Data Security Best Practices To Protect Customer Creating Personalized Marketing Messages MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Present the topic in a bit more detail with this Data Security Best Practices To Protect Customer Creating Personalized Marketing Messages MKT SS V. Use it as a tool for discussion and navigation on Practices, Key Description, Key Benefits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Protect Customers Data In Powerpoint And Google Slides Cpb
Protect Customers Data In Powerpoint And Google Slides CpbPresenting Protect Customers Data In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Protect Customers Data. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
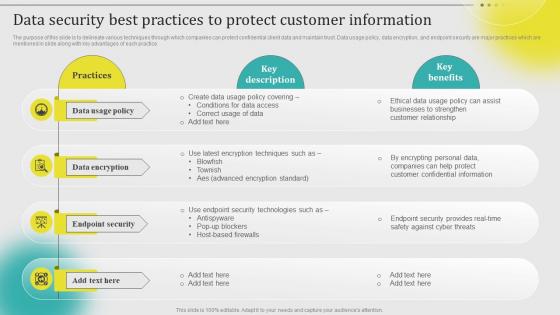 Data Security Best Practices To Protect Customer Information Leveraging Customer Data MKT SS V
Data Security Best Practices To Protect Customer Information Leveraging Customer Data MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Introducing Data Security Best Practices To Protect Customer Information Leveraging Customer Data MKT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Usage Policy, Data Encryption, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Corporate Compliance Strategy Ensure Compliance With Data Protection Laws Strategy SS V
Corporate Compliance Strategy Ensure Compliance With Data Protection Laws Strategy SS VThis slide presents an overview of data protection regulations. It includes aspects such as regulation , purpose, applicability and key points. Present the topic in a bit more detail with this Corporate Compliance Strategy Ensure Compliance With Data Protection Laws Strategy SS V Use it as a tool for discussion and navigation on Implement RiskAccountability, Conduct Timely RiskAssessments This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Corporate Compliance Strategy Guidelines For Implementing Data Protection Regulations Strategy SS V
Corporate Compliance Strategy Guidelines For Implementing Data Protection Regulations Strategy SS VThis slide presents data protection policies and procedures to ensure data compliance in the company. It includes information about data classification, access control, incident response and data privacy policy. Introducing Corporate Compliance Strategy Guidelines For Implementing Data Protection Regulations Strategy SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Workplace Safety Compliance, Recordkeeping Compliance, Employment Law Compliance using this template. Grab it now to reap its full benefits.
-
 Data Security Best Practices To Protect Complete Introduction To Database MKT SS V
Data Security Best Practices To Protect Complete Introduction To Database MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Increase audience engagement and knowledge by dispensing information using Data Security Best Practices To Protect Complete Introduction To Database MKT SS V. This template helps you present information on four stages. You can also present information on Policy, Encryption, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Challenges Of Data In Use Protection And Solutions
Encryption Implementation Strategies Challenges Of Data In Use Protection And SolutionsThis slide outlines the various limitations of data in use protection and their possible solutions. These include limited control after data access, unauthorized copying or sharing of data, limitations of collaboration platforms, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Challenges Of Data In Use Protection And Solutions. Use it as a tool for discussion and navigation on Limitations Of Collaboration Platforms, Unauthorized Copying Or Sharing Of Data, Limited Control After Data Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use
Encryption Implementation Strategies Data Protection Technologies To Secure Information In UseThis slide compares different data in use protection methods, and their working and associated cost. These methods are IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use. Use it as a tool for discussion and navigation on Identity Management Tools, Digital Rights Protection, Data Protection Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Different States Of Data Which Requires Protection
Encryption Implementation Strategies Different States Of Data Which Requires ProtectionThis slide discusses various customer demands to ensure data privacy and authenticity. The purpose of this slide is to highlight the various states of data that require encryption, such as data-at-rest, data-in-transit, and data-in-use. Introducing Encryption Implementation Strategies Different States Of Data Which Requires Protection to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Customer Demands, Data Privacy And Authenticity, Require Encryption, Collaboration Software, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Top Regulatory Compliance Frameworks For Data Protection
Encryption Implementation Strategies Top Regulatory Compliance Frameworks For Data ProtectionThe purpose of this slide is to summarize several relevant regulations. These are GDPR General Data Protection Regulation, CCPA California Consumer Privacy Act, PCI DSS Payment Card Industry Data Security Standard, NIST, and HIPAA, along with their descriptions and scopes. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Top Regulatory Compliance Frameworks For Data Protection. Dispense information and present a thorough explanation of General Data Protection Regulation, California Consumer Privacy Act, Health Insurance Portability And Accountability Act using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Security Best Practices To Protect Customer Database Marketing Strategies MKT SS V
Data Security Best Practices To Protect Customer Database Marketing Strategies MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Introducing Data Security Best Practices To Protect Customer Database Marketing Strategies MKT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Usage Policy, Data Encryption, using this template. Grab it now to reap its full benefits.
-
 File Protection And Data Theft Prevention Icon
File Protection And Data Theft Prevention IconPresenting our well structured File Protection And Data Theft Prevention Icon. The topics discussed in this slide are Protection, Data, Prevention. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Data Protection Impact Assessment Under Gdpr Transforming Healthcare BCT SS
Data Protection Impact Assessment Under Gdpr Transforming Healthcare BCT SSThis slide showcases data protection impact assessment checklist used by healthcare providers or companies to investigate potential vulnerabilities and improve data privacy and compliance status. It include various requirements that are evaluated on the basis of their current stage. Present the topic in a bit more detail with this Data Protection Impact Assessment Under Gdpr Transforming Healthcare BCT SS. Use it as a tool for discussion and navigation on Describe The Processing, Identify And Assess Risks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Employee And Workplace Ensure Compliance With Data Protection Laws And Regulations Strategy SS V
Employee And Workplace Ensure Compliance With Data Protection Laws And Regulations Strategy SS VThis slide presents an overview of data protection regulations. It includes aspects such as regulation , purpose, applicability and key points. Deliver an outstanding presentation on the topic using this Employee And Workplace Ensure Compliance With Data Protection Laws And Regulations Strategy SS V Dispense information and present a thorough explanation of Regulatory Requirement, Training Objectives, Training Method using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Employee And Workplace Guidelines For Implementing Data Protection Regulations Strategy SS V
Employee And Workplace Guidelines For Implementing Data Protection Regulations Strategy SS VThis slide presents data protection policies and procedures to ensure data compliance in the company. It includes information about data classification, access control, incident response and data privacy policy.Increase audience engagement and knowledge by dispensing information using Employee And Workplace Guidelines For Implementing Data Protection Regulations Strategy SS V This template helps you present information on Four stages. You can also present information on Internal Review, External Audit, Compliance Surveys using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ensure Compliance With Data Protection Laws And Regulations Effective Business Risk Strategy SS V
Ensure Compliance With Data Protection Laws And Regulations Effective Business Risk Strategy SS VThis slide represents techniques to effectively engaging employees and stakeholders in the compliance process. It includes strategies such as training programs, communication channels, feedback mechanisms, incentives and recognition and compliance committees. Increase audience engagement and knowledge by dispensing information using Ensure Compliance With Data Protection Laws And Regulations Effective Business Risk Strategy SS V. This template helps you present information on six stages. You can also present information on Training Programs, Communication Channels using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Guidelines For Implementing Data Protection Regulations Effective Business Risk Strategy SS V
Guidelines For Implementing Data Protection Regulations Effective Business Risk Strategy SS VThis slide presents data protection policies and procedures to ensure data compliance in the company. It includes information about data classification, access control, incident response and data privacy policy. Increase audience engagement and knowledge by dispensing information using Guidelines For Implementing Data Protection Regulations Effective Business Risk Strategy SS V. This template helps you present information on four stages. You can also present information on Purpose, Data Classification Policy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V
Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Request Fulfillment using this template. Grab it now to reap its full benefits.
-
 Confidential Computing V2 Technologies Used To Protect Data In Use
Confidential Computing V2 Technologies Used To Protect Data In UseThis slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present the topic in a bit more detail with this Confidential Computing V2 Technologies Used To Protect Data In Use. Use it as a tool for discussion and navigation on Homomorphic Encryption, Trusted Execution Environments, Privacy Preserving Computation, Protecting Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ways Protect Data In Powerpoint And Google Slides Cpb
Ways Protect Data In Powerpoint And Google Slides CpbPresenting our Ways Protect Data In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Ways Protect Data. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cloud Storage Data Protection Strategy
Cloud Storage Data Protection StrategyThis slide outlines the cloud for backup covers trends, techniques and best practices in optimizing cloud object storage for backup. It includes various data protection strategy such as identify data and applications, prioritize backups based on recovery plan, optimize and secure data backups. Presenting our set of slides with Cloud Storage Data Protection Strategy. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify Data And Applications, Optimize Secure Backups.
-
 Data Protection Jobs In Powerpoint And Google Slides Cpb
Data Protection Jobs In Powerpoint And Google Slides CpbPresenting our Data Protection Jobs In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Data Protection Jobs This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Data Protection Market In Powerpoint And Google Slides Cpb
Data Protection Market In Powerpoint And Google Slides CpbPresenting our Data Protection Market In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases two stages. It is useful to share insightful information on Data Protection Market. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Data Lineage Protection Solutions
Data Lineage Protection SolutionsThis slide shows solutions for data lineage protection to validate data accuracy and consistency. It includes methods such as firewall, rights management, loss prevention, behavior analytics, and prioritization. Introducing our premium set of slides with Data Lineage Protection Solutions. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Firewall, Loss Prevention, Behavior Analytics. So download instantly and tailor it with your information.
-
 Information Security Management Framework For Organization Data Protection
Information Security Management Framework For Organization Data ProtectionThis slide represents framework that assists organizations in developing information security management to enhance data protection. This model sets information security at tactical level, strategic level, and operational level. Introducing our Information Security Management Framework For Organization Data Protection set of slides. The topics discussed in these slides are Information Security Plan, Consciousness Management, Risk Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information Security Management Icon For Data Protection
Information Security Management Icon For Data ProtectionPresenting our set of slides with Information Security Management Icon For Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Information Security Management Icon, Data Protection.
-
 Managing Information Security Threats To Enhance Data Protection
Managing Information Security Threats To Enhance Data ProtectionThis slide represents strategies that help businesses mitigate threats of information security management and reduce data loss incidents. It includes various threats such as social media attacks, social engineering, lack of encryption, etc. Presenting our well structured Managing Information Security Threats To Enhance Data Protection. The topics discussed in this slide are Social Media Attacks, Social Engineering, Malware On Endpoints. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Extensive Business Strategy Cyber Strategies For KPMG For Client Data Protection Strategy SS V
Extensive Business Strategy Cyber Strategies For KPMG For Client Data Protection Strategy SS VThis slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Introducing Extensive Business Strategy Cyber Strategies For KPMG For Client Data Protection Strategy SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on People, Process, Regulatory, using this template. Grab it now to reap its full benefits.
-
 Extensive Business Strategy Other Cyber Strategies Of KPMG For Client Data Protection Strategy SS V
Extensive Business Strategy Other Cyber Strategies Of KPMG For Client Data Protection Strategy SS VThis slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. Increase audience engagement and knowledge by dispensing information using Extensive Business Strategy Other Cyber Strategies Of KPMG For Client Data Protection Strategy SS V. This template helps you present information on five stages. You can also present information on Threat Landscape, Cyber Security, Governance Framework using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Protection Processes Rules In Powerpoint And Google Slides Cpb
Data Protection Processes Rules In Powerpoint And Google Slides CpbPresenting our Data Protection Processes Rules In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Data Protection Processes Rules. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Digital Therapeutics Functions Impact Of Digital Therapeutics On Data Protection
Digital Therapeutics Functions Impact Of Digital Therapeutics On Data ProtectionThis slide talks about the positive and negative impact of digital therapeutics on information protection. The negative includes the regular patient observation and profiling, the significant impact of personal information breaches, and security issues due to complexity. Introducing Digital Therapeutics Functions Impact Of Digital Therapeutics On Data Protection to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Positive, Negative, Data Protection using this template. Grab it now to reap its full benefits.
-
 Data Security Strategies To Protect Retail Customer Digital Transformation Of Retail DT SS
Data Security Strategies To Protect Retail Customer Digital Transformation Of Retail DT SSThis slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Increase audience engagement and knowledge by dispensing information using Data Security Strategies To Protect Retail Customer Digital Transformation Of Retail DT SS This template helps you present information on six stages. You can also present information on Customer Data Protection, Online Transactions, Management Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implement General Data Protection Regulation Digital Transformation Of Retail DT SS
Implement General Data Protection Regulation Digital Transformation Of Retail DT SSThis slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance. Introducing Implement General Data Protection Regulation Digital Transformation Of Retail DT SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Ongoing Compliance, Data Security, Consent And Legal Basis using this template. Grab it now to reap its full benefits.
-
 Implementing Byod Policy To Enhance Develop Security Policies For Data Protection
Implementing Byod Policy To Enhance Develop Security Policies For Data ProtectionThis slide shows major data protection policies for handling sensitive data of corporate. It include policies such as device security, network and data handling, etc. Introducing Implementing Byod Policy To Enhance Develop Security Policies For Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Data Handling, Device Security, Data Protection, using this template. Grab it now to reap its full benefits.
-
 Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy
Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod PolicyThis slide shows essential considerations for protecting crucial data of company in organization. It include security areas such as device security, network security and software updates, etc. Increase audience engagement and knowledge by dispensing information using Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy. This template helps you present information on five stages. You can also present information on Device Security, Mobile Device Management, Network Security, Malware Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Protection Under SAP Cybersecurity
Data Protection Under SAP CybersecurityThis slide highlights the data protection under systems applications and product cybersecurity. The purpose of this template is to help the business ensure its data is being protected against malware through the use of elements such as SAP concentrated run, SAP business threat detection cloud edition, etc. Presenting our well structured Data Protection Under SAP Cybersecurity. The topics discussed in this slide are Identity Access Governance, Identify And Correct Security, Evaluate And Report. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Digital Therapeutics Adoption Challenges Impact Of Digital Therapeutics On Data Protection
Digital Therapeutics Adoption Challenges Impact Of Digital Therapeutics On Data ProtectionThis slide talks about the positive and negative impact of digital therapeutics on information protection. The negative includes the regular patient observation and profiling, the significant impact of personal information breaches, and security issues due to complexity. Present the topic in a bit more detail with this Digital Therapeutics Adoption Challenges Impact Of Digital Therapeutics On Data Protection. Use it as a tool for discussion and navigation on Digital Therapeutics, Patient Observation And Profiling, Personal Information Breaches, Data Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Security Strategies To Protect Retail Customer Comprehensive Retail Transformation DT SS
Data Security Strategies To Protect Retail Customer Comprehensive Retail Transformation DT SSThis slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Present the topic in a bit more detail with this Data Security Strategies To Protect Retail Customer Comprehensive Retail Transformation DT SS. Use it as a tool for discussion and navigation on Online Transactions, Customer Data Protection, POS Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Data Protection Devices Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Data Protection Devices Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a great visual aid for representing folder password protection. It is a modern and vibrant design that will add a professional touch to any presentation. The icon is easy to use and can be used to quickly and effectively communicate the importance of password security.
-
 Encryption Data Protection Devices Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Data Protection Devices Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Folder Password is a simple yet effective way to protect your confidential data. It is easy to use and provides a secure encryption for your files. It is an ideal solution for those who want to keep their documents safe and secure.
-
 Essential Guide To Database Marketing Data Security Best Practices To Protect Customer Information MKT SS V
Essential Guide To Database Marketing Data Security Best Practices To Protect Customer Information MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Essential Guide To Database Marketing Data Security Best Practices To Protect Customer Information MKT SS V Dispense information and present a thorough explanation of Data Usage Policy, Data Encryption, Endpoint Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Blackberry Cybersecurity Approach For Protecting Data
Blackberry Cybersecurity Approach For Protecting DataThis slide showcases blackberry cybersecurity strategy for data protection. The purpose of this slide is to aid IT teams aids in effective protection and maintenance of sensitive information. It includes elements such as continuous monitoring, data loss prevention, etc. Presenting our set of slides with Blackberry Cybersecurity Approach For Protecting Data. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitoring, Access, Prevention.
-
 Digital Therapeutics Types Impact Of Digital Therapeutics On Data Protection Ppt Professional
Digital Therapeutics Types Impact Of Digital Therapeutics On Data Protection Ppt ProfessionalThis slide talks about the positive and negative impact of digital therapeutics on information protection. The negative includes the regular patient observation and profiling, the significant impact of personal information breaches, and security issues due to complexity. Introducing Digital Therapeutics Types Impact Of Digital Therapeutics On Data Protection Ppt Professional to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Positive, Negative, Regular Patient Observation, using this template. Grab it now to reap its full benefits.
-
 Data Security Best Practices To Protect Database Marketing Practices To Increase MKT SS V
Data Security Best Practices To Protect Database Marketing Practices To Increase MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Increase audience engagement and knowledge by dispensing information using Data Security Best Practices To Protect Database Marketing Practices To Increase MKT SS V. This template helps you present information on four stages. You can also present information on Policy, Encryption, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloning In Cyber Security For Data Protection
Cloning In Cyber Security For Data ProtectionThis slide shows benefits of cloning for cyber protection. It aims to prevent cloning security risks to mitigate unauthorized access to technical assets. It covers four cyber security measures such as data protection, integrity, loss prevention and transfers. Presenting our set of slides with name Cloning In Cyber Security For Data Protection. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Data Integrity, Data Transfers.
-
 Data Security Best Practices To Protect Using Customer Data To Improve MKT SS V
Data Security Best Practices To Protect Using Customer Data To Improve MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Data Security Best Practices To Protect Using Customer Data To Improve MKT SS V. Dispense information and present a thorough explanation of Policy, Data, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Big Data Analytics Cyber Protection Tools
Big Data Analytics Cyber Protection ToolsThe following slide highlights resources like EPP, SIEM, threat intelligence software, fraud detection, predictive modeling, and anti-malware sandboxes to show big data analytics cybersecurity tools. It helps organizations to bolster their cyber defense capabilities and safeguard against a wide range of threats. Presenting our set of slides with Big Data Analytics Cyber Protection Tools. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Fraud Detection, Predictive Modeling, Anti-Malware Sandboxes.
-
 Implementation Stats Of Big Data Analytics For Cyber Protection
Implementation Stats Of Big Data Analytics For Cyber ProtectionThe following slide highlights key points like prioritizing, training, improving, and security infrastructure to show implementation stats of big data analytics for cybersecurity. It helps organizations to enhance cyber threat detection and response capabilities. Presenting our set of slides with Implementation Stats Of Big Data Analytics For Cyber Protection. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implementation, Data Analytics, Cybersecurity.
-
 Strategies For Big Data Cyber Protection Analytics
Strategies For Big Data Cyber Protection AnalyticsThe following slide highlights key points like data collection, data normalization, expansion, enrichment, automation, standardization, and advanced detection to show strategies for big data analytics cybersecurity. It helps organizations to proactively defend against cyber threats and enhance overall security posture. Introducing our premium set of slides with Strategies For Big Data Cyber Protection Analytics. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Collection, Data Normalization, Expansion. So download instantly and tailor it with your information.
-
 Configurations Of Storage Virtualization To Protect Data
Configurations Of Storage Virtualization To Protect DataThis slide showcases the con figurations of storage virtualization securing important and sensitive data which helps an organization to reduce hardware costs and distributors lock-ins. It include details such as in-band symmetric and out band asymmetric approach. Presenting our set of slides with name Configurations Of Storage Virtualization To Protect Data. This exhibits information on Two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on In Band Approach Symmetric, Out Band Approach Asymmetric.
-
 Types Of Wireless Internet Security For Data Protection
Types Of Wireless Internet Security For Data ProtectionThe following slide highlights key points such as WEP, WPA, WPA2, and WPA3 protocols to show types of wireless internet security for privacy protection. It helps in understanding and comparing different safety procedures for effective data protection. Introducing our premium set of slides with Types Of Wireless Internet Security For Data Protection. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Protection, Wireless Internet. So download instantly and tailor it with your information.
-
 Csirt Cyber Security Icon For Protecting Data
Csirt Cyber Security Icon For Protecting DataIntroducing our premium set of slides with Csirt Cyber Security Icon For Protecting Data. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Csirt Cyber Security, Protecting Data. So download instantly and tailor it with your information.
-
 Data Protection Server Security Technology Icon
Data Protection Server Security Technology IconPresenting our set of slides with Data Protection Server Security Technology Icon. This exhibits information on threestages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Server Security Technology.
-
 Enhance Server Security Through Data Protection Storage Icon
Enhance Server Security Through Data Protection Storage IconPresenting our set of slides with Enhance Server Security Through Data Protection Storage Icon. This exhibits information on fourstages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Server Security, Data Protection Storage.
-
 Cybersecurity Incident Response Icon For Data Protection
Cybersecurity Incident Response Icon For Data ProtectionIntroducing our premium set of slides with name Cybersecurity Incident Response Icon For Data Protection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cybersecurity Incident, Response Icon, Data Protection. So download instantly and tailor it with your information.
-
 Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS V
Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS V. Dispense information and present a thorough explanation of Data Usage Policy, Data Encryption, Endpoint Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Hypervisor database protection icon for server
Hypervisor database protection icon for serverIntroducing our Hypervisor database protection icon for server set of slides. The topics discussed in these slides are Hypervisor Database, Protection Icon Server. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Incident Investigation Icon To Enhance Data Protection
Cybersecurity Incident Investigation Icon To Enhance Data ProtectionIncrease audience engagement and knowledge by dispensing information using Cybersecurity Incident Investigation Icon To Enhance Data Protection. This template helps you present information on four stages. You can also present information on Cybersecurity Incident Investigation Icon, Enhance Data Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps Of Cybersecurity Firewall To Protect Business Data
Steps Of Cybersecurity Firewall To Protect Business DataThis slide showcases the effective guidelines of cybersecurity firewall for securing organizational data which helps an organization to employ new updated policies easily and quickly. It include details such as introduce incoming connections, track audit logs, etc. Presenting our well structured Steps Of Cybersecurity Firewall To Protect Business Data. The topics discussed in this slide are Effective Steps, Techniques, Business Data. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.





