Powerpoint Templates and Google slides for Process Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Defining security threats effective information security risk management process
Defining security threats effective information security risk management processThis slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures.Introducing Defining Security Threats Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Natural Disaster, Environmental Control Failures, Deliberate Software Attacks, using this template. Grab it now to reap its full benefits.
-
 Defining vulnerability rating effective information security risk management process
Defining vulnerability rating effective information security risk management processFollowing slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description.Present the topic in a bit more detail with this Defining Vulnerability Rating Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Occurrence Of Attack, Organization Is Reasonably, Organization Is Capable Enough. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security management process information security risk assessment
Effective information security management process information security risk assessmentThis slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence.Deliver an outstanding presentation on the topic using this Effective Information Security Management Process Information Security Risk Assessment. Dispense information and present a thorough explanation of Facilities And Equipment, Unauthorized Disclosure, Valuable Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Employee training schedule effective information security risk management process
Employee training schedule effective information security risk management processThis slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration.Present the topic in a bit more detail with this Employee Training Schedule Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Training Duration, Intermediate, Training Mode. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons slide for effective information security risk management process
Icons slide for effective information security risk management processPresenting our well crafted Icons Slide For Effective Information Security Risk Management Process set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Impact assessment matrix effective information security risk management process
Impact assessment matrix effective information security risk management processPresent the topic in a bit more detail with this Impact Assessment Matrix Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Minor To No Infringement, Suspected Malicious Intent, Impact Medium. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact on security performance effective information security risk management process
Impact on security performance effective information security risk management processMentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver an outstanding presentation on the topic using this Impact On Security Performance Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of After Introducing, Risk Assessment Process, Assets Efficiently using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Incident management tool effective information security risk management process
Incident management tool effective information security risk management processMentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform.Present the topic in a bit more detail with this Incident Management Tool Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Notify Employee, Message During Any Breach, Automated Workflow. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
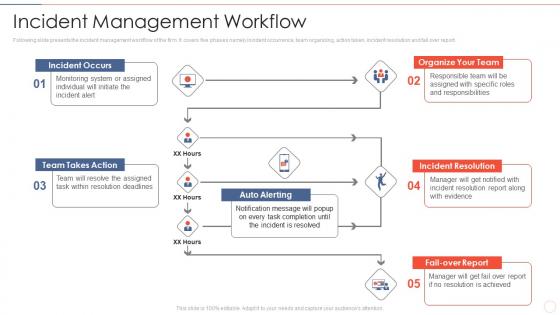 Incident management workflow effective information security risk management process
Incident management workflow effective information security risk management processFollowing slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report.Introducing Incident Management Workflow Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Organize Your Team, Incident Resolution, Team Takes Action, using this template. Grab it now to reap its full benefits.
-
 Incidents effective information security risk management process
Incidents effective information security risk management processThis slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level.Present the topic in a bit more detail with this Incidents Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Preform Primary Work Functions, Inconvenient, Medium Multiple. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
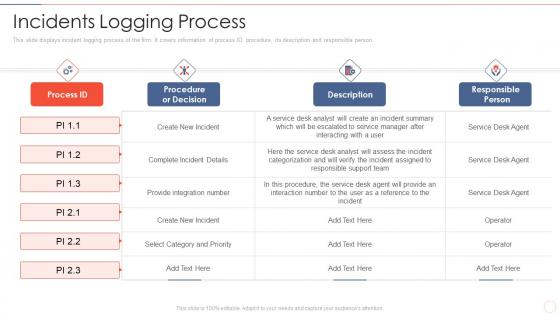 Incidents logging process effective information security risk management process
Incidents logging process effective information security risk management processThis slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person.Deliver an outstanding presentation on the topic using this Incidents Logging Process Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Select Category And Priority, Procedure, The Service, Responsible Person using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information security decision effective information security risk management process
Information security decision effective information security risk management processIncrease audience engagement and knowledge by dispensing information using Information Security Decision Effective Information Security Risk Management Process. This template helps you present information on eight stages. You can also present information on Risk Management, Implementation Responsiveness, Prioritization Weighting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information security effective information security risk management process
Information security effective information security risk management processMentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm.Present the topic in a bit more detail with this Information Security Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Asset And Consequences, Overheating In Server Room, Asset And Consequences. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introducing process workflow effective information security risk management process
Introducing process workflow effective information security risk management processFollowing slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results Deliver an outstanding presentation on the topic using this Introducing Process Workflow Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Threat Categorization, System Characterization, Assigned Remediation Measures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mitigation plan for threat effective information security risk management process
Mitigation plan for threat effective information security risk management processMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver an outstanding presentation on the topic using this Mitigation Plan For Threat Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Resources Required, Expected Resolution Time, Communication Mode using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Multitiered risk effective information security risk management process
Multitiered risk effective information security risk management processIntroducing Multitiered Risk Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Orgnization, Mission Or Business Processes, Information Systems, using this template. Grab it now to reap its full benefits.
-
 Present security effective information security risk management process
Present security effective information security risk management processFollowing slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings.Present the topic in a bit more detail with this Present Security Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Assessing Information, Incident Occurrence Identification, Vulnerability Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk reporting and likelihood effective information security risk management process
Risk reporting and likelihood effective information security risk management processMentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an outstanding presentation on the topic using this Risk Reporting And Likelihood Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Attack Scenario, Risk Encountered, Equipment Failure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Roles and responsibilities effective information security risk management process
Roles and responsibilities effective information security risk management processFollowing slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development.Increase audience engagement and knowledge by dispensing information using Roles And Responsibilities Effective Information Security Risk Management Process. This template helps you present information on one stage. You can also present information on Information Management Manager, Risk Management Officer, Development And Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security risk management process incidents prioritization matrix effective information
Security risk management process incidents prioritization matrix effective informationThis slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level Present the topic in a bit more detail with this Security Risk Management Process Incidents Prioritization Matrix Effective Information. Use it as a tool for discussion and navigation on Enterprise Or Multiple Segments, Single Segment Or Entire Site, Event Underway. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
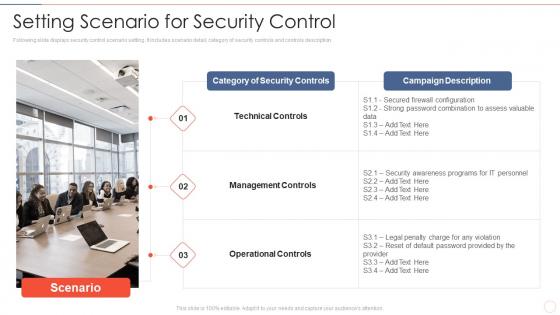 Setting scenario security control effective information security risk management process
Setting scenario security control effective information security risk management processFollowing slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Introducing Setting Scenario Security Control Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Controls, Operational Controls, Technical Controls, using this template. Grab it now to reap its full benefits.
-
 System categorization worksheet effective information security risk management process
System categorization worksheet effective information security risk management processThis slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information.Present the topic in a bit more detail with this System Categorization Worksheet Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on System Accessibility, Accessible Within Organization Boundary, Valuable Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 System disposal checklist effective information security risk management process
System disposal checklist effective information security risk management processMentioned slide shows system disposal checklist. It covers information such as system requirement, its compliance and remarks.Deliver an outstanding presentation on the topic using this System Disposal Checklist Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Stored Information Is Removed, Hardcopy Information, Requirement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 System management checklist effective information security risk management process
System management checklist effective information security risk management processFollowing slide displays system management checklist. It includes system management activities and frequency of performing them.Present the topic in a bit more detail with this System Management Checklist Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on System Monitoring, Security Patches, Virus Scanning . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table of contents for effective information security risk management process
Table of contents for effective information security risk management processDeliver an outstanding presentation on the topic using this Table Of Contents For Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Present Scenario, Training And Budget, Dashboards using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat assessment effective information security risk management process
Threat assessment effective information security risk management processFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Threat Assessment Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Affected Asset, Potential Vulnerability, Vulnerability Ranking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Effective information security incidents logging process
Effective information security incidents logging processThis slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person. Present the topic in a bit more detail with this Effective Information Security Incidents Logging Process. Use it as a tool for discussion and navigation on Complete Incident Details, Select Category And Priority, Provide Integration Number. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
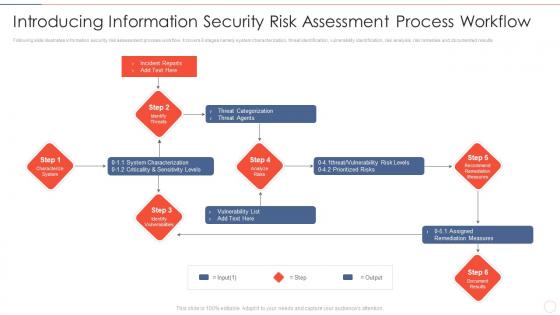 Effective information security introducing information security risk assessment process
Effective information security introducing information security risk assessment processFollowing slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results Increase audience engagement and knowledge by dispensing information using Effective Information Security Introducing Information Security Risk Assessment Process. This template helps you present information on six stages. You can also present information on Incident Reports, Threat Categorization, Vulnerability List, Assigned Remediation Measures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 6 step process to implement data availability security
6 step process to implement data availability securityThis slide represents 6 step process to implement data availability security illustrating simplified recording, on-site maintenance and online security, training, record disposal and plan. Presenting our set of slides with 6 Step Process To Implement Data Availability Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Management, Implement, Organization.
-
 Eliminating manual security processes managing cyber risk in a digital age
Eliminating manual security processes managing cyber risk in a digital ageMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Present the topic in a bit more detail with this Eliminating Manual Security Processes Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Vulnerability, Scanning, Resolution, Team. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber threat security planning process with risk tolerance and threats
Cyber threat security planning process with risk tolerance and threatsThis following slide illustrates the cyber security threat program planning which include steps like identify key personnel, risk tolerance strategy and developing frequency. Presenting our set of slides with Cyber Threat Security Planning Process With Risk Tolerance And Threats. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Built Risk Tolerance, Identify And Document, Establish Governance.
-
 Information and event management logging process real time analysis of security alerts
Information and event management logging process real time analysis of security alertsThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Present the topic in a bit more detail with this Information And Event Management Logging Process Real Time Analysis Of Security Alerts. Use it as a tool for discussion and navigation on Information, Management, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Process Of Disaster Recovery Planning
Information Security Process Of Disaster Recovery PlanningThis slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Increase audience engagement and knowledge by dispensing information using Information Security Process Of Disaster Recovery Planning. This template helps you present information on eight stages. You can also present information on Plan Testing, Approval, Prioritize Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Transaction During E Commerce Financial Process Icon
Secure Transaction During E Commerce Financial Process IconIntroducing our Secure Transaction During E Commerce Financial Process Icon set of slides. The topics discussed in these slides are Secure Transaction During E Commerce Financial Process Icon. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Reverse Proxy It Process Of Secure Reverse Proxying
Reverse Proxy It Process Of Secure Reverse ProxyingThis slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy and secure proxy to a content server. Increase audience engagement and knowledge by dispensing information using Reverse Proxy It Process Of Secure Reverse Proxying. This template helps you present information on five stages. You can also present information on Process Of Secure Reverse Proxying using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Program Cybersecurity Flow Diagram Of Incident Response Process
Information Security Program Cybersecurity Flow Diagram Of Incident Response ProcessMentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Flow Diagram Of Incident Response Process. Dispense information and present a thorough explanation of Flow Diagram Of Incident Response Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Cybersecurity Introducing New Incidents Logging Process
Information Security Program Cybersecurity Introducing New Incidents Logging ProcessThis slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. Present the topic in a bit more detail with this Information Security Program Cybersecurity Introducing New Incidents Logging Process. Use it as a tool for discussion and navigation on Introducing New Incidents Logging Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
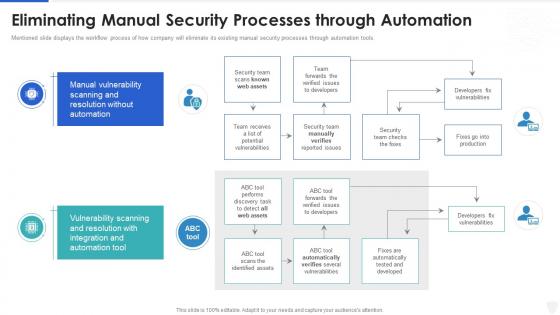
 Information Security Program Eliminating Manual Security Processes Through Automation
Information Security Program Eliminating Manual Security Processes Through AutomationMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver an outstanding presentation on the topic using this Information Security Program Eliminating Manual Security Processes Through Automation. Dispense information and present a thorough explanation of Processes, Automation, Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Embedding Risk Based Approach Product Development Process
Information Security Program Embedding Risk Based Approach Product Development ProcessPurpose of this slide is to highlight the risk based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Present the topic in a bit more detail with this Information Security Program Embedding Risk Based Approach Product Development Process. Use it as a tool for discussion and navigation on Product, Development, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Gap Identification Current Approach Process Flaws And Cost
Information Security Program Gap Identification Current Approach Process Flaws And CostPurpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Present the topic in a bit more detail with this Information Security Program Gap Identification Current Approach Process Flaws And Cost. Use it as a tool for discussion and navigation on Identification, Current Approach, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Eliminating Manual Security Processes Through Automation Risk Based Methodology To Cyber
Eliminating Manual Security Processes Through Automation Risk Based Methodology To CyberMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools.Present the topic in a bit more detail with this Eliminating Manual Security Processes Through Automation Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Manual Vulnerability, Scanning And Resolution, Vulnerability Scanning This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Flow Diagram Of Incident Response Process Introducing A Risk Based Approach To Cyber Security
Flow Diagram Of Incident Response Process Introducing A Risk Based Approach To Cyber SecurityMentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down.Present the topic in a bit more detail with this Flow Diagram Of Incident Response Process Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Remediate Eradicate, Contain Mitigate, Consider The Potential This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introducing New Incidents Logging Process Introducing A Risk Based Approach To Cyber Security
Introducing New Incidents Logging Process Introducing A Risk Based Approach To Cyber SecurityThis slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details.Present the topic in a bit more detail with this Introducing New Incidents Logging Process Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Category Selection, Assigned To Responsible, Provide An Interaction This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network layer security protocols ppt powerpoint presentation pictures layout ideas cpb
Network layer security protocols ppt powerpoint presentation pictures layout ideas cpbPresenting our Network Layer Security Protocols Ppt Powerpoint Presentation Pictures Layout Ideas Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Network Layer Security Protocols This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Building organizational security strategy plan information security process to manage firms sensitive
Building organizational security strategy plan information security process to manage firms sensitiveThis slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Information Security Process To Manage Firms Sensitive. Use it as a tool for discussion and navigation on Information, Process, Sensitive. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan security process to manage firms
Building organizational security strategy plan security process to manage firmsThis slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an outstanding presentation on the topic using this Building Organizational Security Strategy Plan Security Process To Manage Firms. Dispense information and present a thorough explanation of Information, Process, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Improve it security with vulnerability information and event management logging process
Improve it security with vulnerability information and event management logging processThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Introducing Improve It Security With Vulnerability Information And Event Management Logging Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Management, Process, using this template. Grab it now to reap its full benefits.
-
 Credit Card Processing Security Ppt Powerpoint Presentation Portfolio Brochure Cpb
Credit Card Processing Security Ppt Powerpoint Presentation Portfolio Brochure CpbPresenting our Credit Card Processing Security Ppt Powerpoint Presentation Portfolio Brochure Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Credit Card Processing Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Secure Loan Processing Ppt Powerpoint Presentation Show Skills Cpb
Secure Loan Processing Ppt Powerpoint Presentation Show Skills CpbPresenting Secure Loan Processing Ppt Powerpoint Presentation Show Skills Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Loan Processing. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Network Security Process Of Disaster Recovery Planning
Network Security Process Of Disaster Recovery PlanningThis slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Introducing Network Security Process Of Disaster Recovery Planning to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Operations, Processes, Assessment, Perform, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Process Of Disaster Recovery Planning
Information Technology Security Process Of Disaster Recovery PlanningThis slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Introducing Information Technology Security Process Of Disaster Recovery Planning to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Process Of Disaster Recovery Planning, using this template. Grab it now to reap its full benefits.
-
 Siem For Security Analysis Information And Event Management Logging Process
Siem For Security Analysis Information And Event Management Logging ProcessThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Introducing Siem For Security Analysis Information And Event Management Logging Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Management, Process, using this template. Grab it now to reap its full benefits.
-
 Computer Security Technical Assessment Process
Computer Security Technical Assessment ProcessThis slide signifies the technical assessment process on company security. It steps include identify, analyse, prioritize and monitoring. Introducing our premium set of slides with Computer Security Technical Assessment Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify, Analyse, Prioritize, Monitoring. So download instantly and tailor it with your information.
-
 Cyber Security Technical Assessment Process
Cyber Security Technical Assessment ProcessThis slide signifies the technical assessment process of cyber security. It include stages like identify, planning, execution, monitor and closure. Presenting our set of slides with Cyber Security Technical Assessment Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Execution, Closure, Planning, Monitor.
-
 Secure Online Credit Card Processing Ppt Powerpoint Presentation File Backgrounds Cpb
Secure Online Credit Card Processing Ppt Powerpoint Presentation File Backgrounds CpbPresenting Secure Online Credit Card Processing Ppt Powerpoint Presentation File Backgrounds Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Online Credit Card Processing. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Building organizational security strategy plan streamlining employee verification process to ensure
Building organizational security strategy plan streamlining employee verification process to ensureThis slide provides information about streamlining employee verification process at workplace to ensure people security by performing pre and post employee verification. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Streamlining Employee Verification Process To Ensure. Use it as a tool for discussion and navigation on Streamlining, Verification, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 4 steps of rpa security for process automation improvement
4 steps of rpa security for process automation improvementPresenting our set of slides with 4 Steps Of RPA Security For Process Automation Improvement. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Ensure Accountability, Protect Log Integrity, Enable Secure RPA Development.
-
 Cybersecurity and digital business risk management eliminating manual security processes
Cybersecurity and digital business risk management eliminating manual security processesMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Present the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Eliminating Manual Security Processes. Use it as a tool for discussion and navigation on Processes, Resolution, Automation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social security retirement age ppt powerpoint presentation styles rules cpb
Social security retirement age ppt powerpoint presentation styles rules cpbPresenting our Social Security Retirement Age Ppt Powerpoint Presentation Styles Rules Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Three Major Steps Requirements Specification This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Secure Online Payment Processing Ppt Powerpoint Presentation Ideas Background Cpb
Secure Online Payment Processing Ppt Powerpoint Presentation Ideas Background CpbPresenting our Secure Online Payment Processing Ppt Powerpoint Presentation Ideas Background Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Secure Online Payment Processing. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.





