Powerpoint Templates and Google slides for Procedure Risk
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Introduction To Process Risk And Compliance Management Effective Business Risk Strategy SS V
Introduction To Process Risk And Compliance Management Effective Business Risk Strategy SS VThis slide presents an overview of process risk and why organizations must adhere to process risk compliance. It also includes types of process risks such as poor quality assurance, improper machinery maintenance, reporting and accounting errors. Introducing Introduction To Process Risk And Compliance Management Effective Business Risk Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Poor Quality Assurance, Improper Machinery Maintenance, using this template. Grab it now to reap its full benefits.
-
 Procedure To Report Workplace Health And Safety Incidents Effective Business Risk Strategy SS V
Procedure To Report Workplace Health And Safety Incidents Effective Business Risk Strategy SS VThis slide defines the procedure to report workplace health and safety incidents. It provides information about incident types, report to, reporting requirements and potential consequences. Introducing Procedure To Report Workplace Health And Safety Incidents Effective Business Risk Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Workplace Injuries, Reporting Requirements, using this template. Grab it now to reap its full benefits.
-
 Quality Control Processes To Ensure Compliance Of Quality Of Effective Business Risk Strategy SS V
Quality Control Processes To Ensure Compliance Of Quality Of Effective Business Risk Strategy SS VThis slide outlines quality control processes to ensure compliance of quality of products, services, or processes. It includes information about processes such as inspection, testing, statistical process control and six sigma. Present the topic in a bit more detail with this Quality Control Processes To Ensure Compliance Of Quality Of Effective Business Risk Strategy SS V. Use it as a tool for discussion and navigation on Quality Control Process, Inspection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Standards And Procedures To Guide Regulatory Compliance Effective Business Risk Strategy SS V
Standards And Procedures To Guide Regulatory Compliance Effective Business Risk Strategy SS VThis slide highlights key standards and procedures to maintain regulatory compliance in an organization. It includes information about standards such as NIST, ISO and ISO 19600, ISO or IEC 27002 and COBIT. Present the topic in a bit more detail with this Standards And Procedures To Guide Regulatory Compliance Effective Business Risk Strategy SS V. Use it as a tool for discussion and navigation on Nist Standards, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Traditional Risk Management Process In Powerpoint And Google Slides Cpb
Traditional Risk Management Process In Powerpoint And Google Slides CpbPresenting Traditional Risk Management Process In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Traditional Risk Management Process. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 SAP Implementation Best Practices To Reduce Process Risks
SAP Implementation Best Practices To Reduce Process RisksThis slide showcases various practices that are helpful in the smooth and risk-free implementation of SAP. It further includes various practices such as focus on processes, build team, SAP implementation partner, etc Introducing our premium set of slides with SAP Implementation Best Practices To Reduce Process Risks. Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Focus On Processes, Build Team, SAP Implementation Partner. So download instantly and tailor it with your information.
-
 Cyber Security Risk Audit Process Flowchart Improving Cyber Security Risks Management
Cyber Security Risk Audit Process Flowchart Improving Cyber Security Risks ManagementThe following slide depicts the cyber security review flowchart to manage risk and minimize its impact. It includes elements such as request access, grantor, authorizer, tools, auditor, follow up, alert to end user etc. Present the topic in a bit more detail with this Cyber Security Risk Audit Process Flowchart Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Request Access, Validate User Identity, Dismiss Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Improving Cyber Security Risk Management Process
Table Of Contents For Improving Cyber Security Risk Management ProcessIntroducing Table Of Contents For Improving Cyber Security Risk Management Process to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Risks And Attacks, Management Solutions, Program Courses, using this template. Grab it now to reap its full benefits.
-
 Agenda For Procurement Risk Analysis And Mitigation Process For Managing Supply Chain Channels
Agenda For Procurement Risk Analysis And Mitigation Process For Managing Supply Chain ChannelsIntroducing Agenda For Procurement Risk Analysis And Mitigation Process For Managing Supply Chain Channels to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Agenda using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Procurement Risk Analysis And Mitigation Process For Managing Supply Chain Channels
Icons Slide For Procurement Risk Analysis And Mitigation Process For Managing Supply Chain ChannelsIntroducing our well researched set of slides titled Icons Slide For Procurement Risk Analysis And Mitigation Process For Managing Supply Chain Channels. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Kpis To Measure Procurement Process Performance Post Procurement Risk Analysis And Mitigation
Kpis To Measure Procurement Process Performance Post Procurement Risk Analysis And MitigationThis slide showcases various metrics to measure and analyze performance of procurement process . It includes key KPIs such as compliance rate, purchase order accuracy, supplier defect rate, inventory aging, inventory turnover ratio, inventory carrying cost, supplier lead time, emergency purchase rate, etc. Deliver an outstanding presentation on the topic using this Kpis To Measure Procurement Process Performance Post Procurement Risk Analysis And Mitigation Dispense information and present a thorough explanation of Quality, Inventory, Delivery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Procurement Risk Analysis And Mitigation Commercial And Process Levers To Reduce Procurement
Procurement Risk Analysis And Mitigation Commercial And Process Levers To Reduce ProcurementThe slide presents various levers to minimize procurement costs with measures of each step. It includes measures such as negotiation, tender process, bundling, optimize specifications, reduce consumption, redefine supply chain, insourcing outsourcing and strategic partnerships. Present the topic in a bit more detail with this Procurement Risk Analysis And Mitigation Commercial And Process Levers To Reduce Procurement Use it as a tool for discussion and navigation on Negotiation, Tender Process, Bundling This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Procurement Risk Analysis And Mitigation Impact Of Automation On Procurement Process
Procurement Risk Analysis And Mitigation Impact Of Automation On Procurement ProcessThis slide illustrates effect on business after automating vital activities of procurement process. It includes components such as purchase requisition, purchase order, invoice management, vendor management and contract management. Introducing Procurement Risk Analysis And Mitigation Impact Of Automation On Procurement Process to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Purchase Requisition, Purchase Order, Invoice Management using this template. Grab it now to reap its full benefits.
-
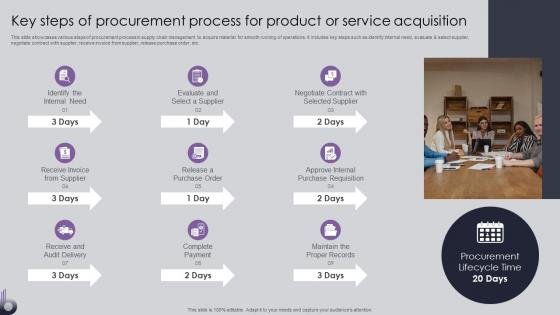 Procurement Risk Analysis And Mitigation Key Steps Of Procurement Process For Product Or Service
Procurement Risk Analysis And Mitigation Key Steps Of Procurement Process For Product Or ServiceThis slide showcases various steps of procurement process in supply chain management to acquire material for smooth running of operations. It includes key steps such as identify internal need, evaluate and select supplier,negotiate contract with supplier, receive invoice from supplier, release purchase order, etc. Increase audience engagement and knowledge by dispensing information using Procurement Risk Analysis And Mitigation Key Steps Of Procurement Process For Product Or Service This template helps you present information on Nine stages. You can also present information on Procurement Process, Procurement Cycle Time, Supply Chain Risks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Procurement Risk Analysis And Mitigation Kpis To Measure Procurement Process Performance
Procurement Risk Analysis And Mitigation Kpis To Measure Procurement Process PerformanceThis slide showcases various metrics to measure and analyze performance of procurement process . It includes key KPIs such as compliance rate, purchase order accuracy, supplier defect rate, inventory aging, inventory turnover ratio, inventory carrying cost, supplier lead time, emergency purchase rate, etc. Deliver an outstanding presentation on the topic using this Procurement Risk Analysis And Mitigation Kpis To Measure Procurement Process Performance Dispense information and present a thorough explanation of Proper Records, Purchase Requisition, Contract With Selected Supplier using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Procurement Risk Analysis And Mitigation Optimizing Cost Drivers In Procurement Process
Procurement Risk Analysis And Mitigation Optimizing Cost Drivers In Procurement ProcessThe slide illustrates identification of multiple cost drivers of procurement process to reduce cost. It includes indicators and measures of key elements such as activity, productivity and unit cost. Introducing Procurement Risk Analysis And Mitigation Optimizing Cost Drivers In Procurement Process to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Inventory, Delivery, Quality using this template. Grab it now to reap its full benefits.
-
 Procurement Risk Analysis And Mitigation Software Assessment To Automate Procurement Process
Procurement Risk Analysis And Mitigation Software Assessment To Automate Procurement ProcessThe slide showcases assessment of multiple software to automate procurement process. It includes features such as communication and collaboration tools, self service portals, AI and data analytics, cloud based procurement software, vendor experience management, etc. Deliver an outstanding presentation on the topic using this Procurement Risk Analysis And Mitigation Software Assessment To Automate Procurement Process Dispense information and present a thorough explanation of Self Service Portals, Based Procurement Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tables Of Contents For Procurement Risk Analysis And Mitigation Process For Managing Supply Chain
Tables Of Contents For Procurement Risk Analysis And Mitigation Process For Managing Supply ChainIntroducing Tables Of Contents For Procurement Risk Analysis And Mitigation Process For Managing Supply Chain to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Scenario Analysis, Impact Analysis, Procurement Process using this template. Grab it now to reap its full benefits.
-
 C110 Procurement Risk Analysis And Mitigation Process For Managing Supply Chain Tables Of Contents
C110 Procurement Risk Analysis And Mitigation Process For Managing Supply Chain Tables Of ContentsIntroducing C110 Procurement Risk Analysis And Mitigation Process For Managing Supply Chain Tables Of Contents to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Backup Plan, Evaluation Tools, Back Up Stock using this template. Grab it now to reap its full benefits.
-
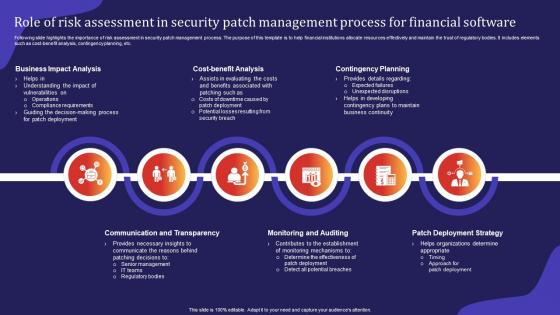 Role Of Risk Assessment In Security Patch Management Process For Financial Software
Role Of Risk Assessment In Security Patch Management Process For Financial SoftwareFollowing slide highlights the importance of risk assessment in security patch management process. The purpose of this template is to help financial institutions allocate resources effectively and maintain the trust of regulatory bodies. It includes elements such as cost benefit analysis, contingency planning, etc.Introducing our premium set of slides with Role Of Risk Assessment In Security Patch Management Process For Financial Software. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Contingency Planning, Communication Transparency, Monitoring Auditing. So download instantly and tailor it with your information.
-
 Credit Risk Management Process For Financial Stability
Credit Risk Management Process For Financial StabilityThis slide exhibits phases of credit risk management to ensure optimum usage of money with appropriate risk . It includes steps such as know your customer, analyze risks, evaluate risks, risk measurement and post- facto analysis. Introducing our premium set of slides with Credit Risk Management Process For Financial Stability. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Know Your Customer, Analyze Risks, Evaluate Risks. So download instantly and tailor it with your information.
-
 Adopt Security Auditing Checklist To Verify Processes Hands On Blockchain Security Risk BCT SS V
Adopt Security Auditing Checklist To Verify Processes Hands On Blockchain Security Risk BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Adopt Security Auditing Checklist To Verify Processes Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Parameters, Description, Comments. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS V
Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS VThe following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer-to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. Introducing Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Enabled Attack, Achieve Control, Incoming And Outgoing, using this template. Grab it now to reap its full benefits.
-
 Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS V
Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS VThe following slide illustrates brief introduction of distributed denial of service DDOS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. Increase audience engagement and knowledge by dispensing information using Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Website Hostage, Close The Attack, Inability To Resolve using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 HR Offboarding Process Mapping To Mitigate Security Risks
HR Offboarding Process Mapping To Mitigate Security RisksThis slide represents HR offboarding process mapping to mitigate security risks. It further includes manager request, replacement, job vacancy, preparation of resignation letter and health check, etc. Presenting our well structured HR Offboarding Process Mapping To Mitigate Security Risks. The topics discussed in this slide are Resignation, Documentation, Termination. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Agenda For Implementing Cyber Risk Management Process
Agenda For Implementing Cyber Risk Management ProcessIntroducing Agenda For Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Awareness Trends, Management Process, Key Metrics, using this template. Grab it now to reap its full benefits.
-
 Allocate Team Roles And Responsibilities Implementing Cyber Risk Management Process
Allocate Team Roles And Responsibilities Implementing Cyber Risk Management ProcessThe following slide showcases the key roles and responsibilities of cyber security team to enhance decision making and goal accomplishment. It includes activities such as developing information security strategies, managing security architecture, planning disaster recovery etc. Increase audience engagement and knowledge by dispensing information using Allocate Team Roles And Responsibilities Implementing Cyber Risk Management Process. This template helps you present information on six stages. You can also present information on Technical Directors, Team Leads, Engineers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Analyse And Rank Impact Of Cyber Threat Implementing Cyber Risk Management Process
Analyse And Rank Impact Of Cyber Threat Implementing Cyber Risk Management ProcessThe following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Deliver an outstanding presentation on the topic using this Analyse And Rank Impact Of Cyber Threat Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Threat, Threat Source, Likelihood using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Analyse Impact Of Cyber Attack On Valuable Assets Implementing Cyber Risk Management Process
Analyse Impact Of Cyber Attack On Valuable Assets Implementing Cyber Risk Management ProcessThe following slide depicts the consequences of data breach threats to prevent information leakage. It mainly includes elements such as impact on revenue, protection cost, liability if lost, weightage criteria, asset importance etc. Present the topic in a bit more detail with this Analyse Impact Of Cyber Attack On Valuable Assets Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Criteria, Impact On Revenue, Protection Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices To Prevent Cyber Attacks Implementing Cyber Risk Management Process
Best Practices To Prevent Cyber Attacks Implementing Cyber Risk Management ProcessThe following slide illustrates some activities to minimize the probability of cybercrimes within the organization. It includes elements such as utilizing anti-virus, preventing to open suspicious emails, keeping systems up-to date etc. Introducing Best Practices To Prevent Cyber Attacks Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Utilize Anti Virus, Prevent Opening Suspicious, Leverage Firewalls, using this template. Grab it now to reap its full benefits.
-
 Build Cyber Security Team Structure Implementing Cyber Risk Management Process
Build Cyber Security Team Structure Implementing Cyber Risk Management ProcessThe following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc. Deliver an outstanding presentation on the topic using this Build Cyber Security Team Structure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Security Analyst, Security Manager, Chief Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Classify Assets Vulnerable To Cyber Attack Implementing Cyber Risk Management Process
Classify Assets Vulnerable To Cyber Attack Implementing Cyber Risk Management ProcessThe following slide depicts some major assets that are more prone to cyber-attack. It mainly includes elements such as sales record, sales lead record, company internal database, customer and product information etc. Present the topic in a bit more detail with this Classify Assets Vulnerable To Cyber Attack Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Assets, Details, Comments. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Conduct Third Party Risk Assessment Implementing Cyber Risk Management Process
Conduct Third Party Risk Assessment Implementing Cyber Risk Management ProcessThe following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Deliver an outstanding presentation on the topic using this Conduct Third Party Risk Assessment Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Response, Status, Notes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Incident Escalation Response Flowchart Implementing Cyber Risk Management Process
Cyber Incident Escalation Response Flowchart Implementing Cyber Risk Management ProcessThe following slide depicts the incident response chart to determine actions to be taken to escalate issue and manage security. It includes elements such as incident identification, informing security team, performing initial analysis, communicating to key members etc. Present the topic in a bit more detail with this Cyber Incident Escalation Response Flowchart Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Notify, Security Team, Classify Incident. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management Process
Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management ProcessThe following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Introducing Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering, Data Breaches, Mobile Malware Attacks, using this template. Grab it now to reap its full benefits.
-
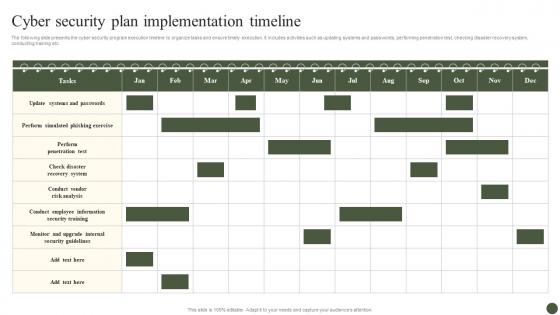 Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process
Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management ProcessThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Present the topic in a bit more detail with this Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Security Plan, Implementation Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management Process
Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management ProcessThe following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Increase audience engagement and knowledge by dispensing information using Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management Process. This template helps you present information on five stages. You can also present information on Malware Infection, Systems With Passwords, Employees Feels, Allow Official Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process
Determine Cyber Security Risks And Threats Implementing Cyber Risk Management ProcessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Objectives, Issue Identifier. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Develop RACI Chart For Team Collaboration Implementing Cyber Risk Management Process
Develop RACI Chart For Team Collaboration Implementing Cyber Risk Management ProcessThe following slide depicts the RACI accountable, consulted, responsible, informed plan to facilitate and ensure speedy communication during cyber issue management. It includes activities such as overall coordination, media messaging, internal communication, technical assistance etc. Deliver an outstanding presentation on the topic using this Develop RACI Chart For Team Collaboration Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Accountable, Consulted, Responsible, Informed using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encrypt And Create Backup Of Useful Data Implementing Cyber Risk Management Process
Encrypt And Create Backup Of Useful Data Implementing Cyber Risk Management ProcessThe following slide illustrates various methods to encrypt and back-up key data to avoid information loss and improved accessibility. It includes elements such as network attached storage, cloud storage services, flat backup system, details, advantages, disadvantages, cost. Present the topic in a bit more detail with this Encrypt And Create Backup Of Useful Data Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Advantages, Disadvantages. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Evaluate Impact And Probability Of Risk Occurrence Implementing Cyber Risk Management Process
Evaluate Impact And Probability Of Risk Occurrence Implementing Cyber Risk Management ProcessThe following slide depicts the potential risk score of identified cyber risks to communicate and level threats. It includes key elements such as human and general errors, outdated security policy, selling companys confidential information, system failure etc. Deliver an outstanding presentation on the topic using this Evaluate Impact And Probability Of Risk Occurrence Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Parameters, Impact, Probability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process
Global Cyber Security Trend Analysis Implementing Cyber Risk Management ProcessThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber-attacks etc. Introducing Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Businesses Targeted, Ransomware Attack, Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Implementing Cyber Risk Management Process
Icons Slide For Implementing Cyber Risk Management ProcessIntroducing our well researched set of slides titled Icons Slide For Implementing Cyber Risk Management Process. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Identify Threat And Vulnerabilities Within Information Implementing Cyber Risk Management Process
Identify Threat And Vulnerabilities Within Information Implementing Cyber Risk Management ProcessThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Present the topic in a bit more detail with this Identify Threat And Vulnerabilities Within Information Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Vulnerability, Threat, Threat Source. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identifying Impact Of Cyber Attack On Business Implementing Cyber Risk Management Process
Identifying Impact Of Cyber Attack On Business Implementing Cyber Risk Management ProcessThe following slide depicts the negative impact of cyber-crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Increase audience engagement and knowledge by dispensing information using Identifying Impact Of Cyber Attack On Business Implementing Cyber Risk Management Process. This template helps you present information on four stages. You can also present information on Reputational Damage, Rising Cost, Operational Disruption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management Process
Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management ProcessThe following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Present the topic in a bit more detail with this Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Attack Type, Remarks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process
Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management ProcessThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions. Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Background Check using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implement Automated Patch Management Solution Implementing Cyber Risk Management Process
Implement Automated Patch Management Solution Implementing Cyber Risk Management ProcessThe following slide showcases the automated patch management process to fix software vulnerabilities and ensure smooth functioning of systems. It includes activities such as scanning of systems, requesting to take back-up etc. Present the topic in a bit more detail with this Implement Automated Patch Management Solution Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Vulnerability Assessment, List Of Servers, Determine Missing Patches. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Cyber Risk Management Process Table Of Contents
Implementing Cyber Risk Management Process Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Implementing Cyber Risk Management Process Table Of Contents. This template helps you present information on one stages. You can also present information on Understanding Cyber Security, Risk Management Process using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process
KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management ProcessThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Before, After. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Leverage Strong And Complex Password Management Implementing Cyber Risk Management Process
Leverage Strong And Complex Password Management Implementing Cyber Risk Management ProcessThe following slide illustrates some practices to ensure strong password management and restrict access to data. It includes activities such as avoiding weak passwords, encryption, multi-factor authentication, conducting test etc. Introducing Leverage Strong And Complex Password Management Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Select Strong Password, Conduct Password Test, Password Encryption, using this template. Grab it now to reap its full benefits.
-
 Monitor And Assess Vendor Risk Management Implementing Cyber Risk Management Process
Monitor And Assess Vendor Risk Management Implementing Cyber Risk Management ProcessThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Introducing Monitor And Assess Vendor Risk Management Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Details, Reviews, using this template. Grab it now to reap its full benefits.
-
 Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process
Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management ProcessThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Present the topic in a bit more detail with this Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Target Audience, Trainer Name, Mode. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Plan Useful Data Backup Schedule Implementing Cyber Risk Management Process
Plan Useful Data Backup Schedule Implementing Cyber Risk Management ProcessThe following slide showcases the monthly calendar for data backup to advance cybersecurity protection and loss of information. It mainly includes techniques such as fully and incremental data backup etc. Deliver an outstanding presentation on the topic using this Plan Useful Data Backup Schedule Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Monday, Tuesday, Wednesday, Thursday using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process
Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management ProcessThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Present the topic in a bit more detail with this Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Rare, Unlikely, Possible. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Reduce Attack Surface With Privilege Access Management Implementing Cyber Risk Management Process
Reduce Attack Surface With Privilege Access Management Implementing Cyber Risk Management ProcessThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Deliver an outstanding presentation on the topic using this Reduce Attack Surface With Privilege Access Management Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Users Access Request, Approval Rules, Session Proxy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process
Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management ProcessThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Parameters, Tasks, Status, Reviews. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Run Penetration Testing To Review Risk Implementing Cyber Risk Management Process
Run Penetration Testing To Review Risk Implementing Cyber Risk Management ProcessThe following slide showcases various methods to review cyber risks to determine probability and impact of risks. It includes elements such as penetration, red team and risk based testing along with objectives, features, cost, outcomes, duration etc. Deliver an outstanding presentation on the topic using this Run Penetration Testing To Review Risk Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Elements, Penetration Testing, Red Team Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Select Cybersecurity Training Program Courses Implementing Cyber Risk Management Process
Select Cybersecurity Training Program Courses Implementing Cyber Risk Management ProcessThe following slide showcases the best cybersecurity training courses to educate employees and minimize the possibility of cyber-attacks. It includes cloud, disaster recovery, hardware, information security programs, duration, mode and cost. Present the topic in a bit more detail with this Select Cybersecurity Training Program Courses Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Course Name, Duration, Mode, Start Date. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process
Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management ProcessThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Deliver an outstanding presentation on the topic using this Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Features, Free Trial, Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





