Powerpoint Templates and Google slides for Prevention Techniques
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Multiple Conflict Prevention Techniques Training Ppt
Multiple Conflict Prevention Techniques Training PptPresenting Multiple Conflict Prevention Techniques. Our PowerPoint experts have included all the necessary templates, designs, icons, graphs, and other essential material. This deck is well crafted by extensive research. Slides consist of amazing visuals and appropriate content. These PPT slides can be instantly downloaded with just a click. Compatible with all screen types and monitors. Supports Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Foster Clear Communication Technique For Conflict Prevention Training Ppt
Foster Clear Communication Technique For Conflict Prevention Training PptPresenting Foster Clear Communication Technique for Conflict Prevention. This slide is well crafted and designed by our PowerPoint specialists. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. You can add or delete the content as per your need.
-
 Superordinate Goals Technique For Conflict Prevention Training Ppt
Superordinate Goals Technique For Conflict Prevention Training PptPresenting Superordinate Goals Technique for Conflict Prevention. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Act Decisively Technique For Conflict Prevention Training Ppt
Act Decisively Technique For Conflict Prevention Training PptPresenting Act Decisively Technique for Conflict Prevention. Our PowerPoint experts have included all the necessary templates, designs, icons, graphs, and other essential material. This deck is well crafted by extensive research. Slides consist of amazing visuals and appropriate content. These PPT slides can be instantly downloaded with just a click. Compatible with all screen types and monitors. Supports Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Recognize Representation Gaps Technique For Conflict Prevention Training Ppt
Recognize Representation Gaps Technique For Conflict Prevention Training PptPresenting Recognize Representation Gaps Technique for Conflict Prevention. This slide is well crafted and designed by our PowerPoint specialists. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. You can add or delete the content as per your need.
-
 Manage Passive Aggression Technique For Conflict Prevention At Workplace Training Ppt
Manage Passive Aggression Technique For Conflict Prevention At Workplace Training PptPresenting Recognize and Manage Passive Aggression Technique for Conflict Prevention at Workplace. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Create Psychological Safety Technique For Conflict Prevention Training Ppt
Create Psychological Safety Technique For Conflict Prevention Training PptPresenting Create Psychological Safety Technique for Conflict Prevention. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Download this professionally designed business presentation, add your content, and present it with confidence.
-
 Avoid Using Coercion And Intimidation Technique For Conflict Prevention Training Ppt
Avoid Using Coercion And Intimidation Technique For Conflict Prevention Training PptPresenting Avoid using Coercion and Intimidation Technique for Conflict Prevention. Our PowerPoint experts have included all the necessary templates, designs, icons, graphs, and other essential material. This deck is well crafted by extensive research. Slides consist of amazing visuals and appropriate content. These PPT slides can be instantly downloaded with just a click. Compatible with all screen types and monitors. Supports Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Exchange Of Personnel Technique For Conflict Prevention Training Ppt
Exchange Of Personnel Technique For Conflict Prevention Training PptPresenting Exchange of Personnel Technique for Conflict Prevention. This slide is well crafted and designed by our PowerPoint specialists. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. You can add or delete the content as per your need.
-
 Reducing Interdependence Technique For Conflict Prevention Training Ppt
Reducing Interdependence Technique For Conflict Prevention Training PptPresenting Reducing Interdependence Technique for Conflict Prevention. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Appeal To Higher Authority Technique For Conflict Prevention Training Ppt
Appeal To Higher Authority Technique For Conflict Prevention Training PptPresenting Appeal To Higher Authority Technique for Conflict Prevention. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Download this professionally designed business presentation, add your content, and present it with confidence.
-
 Data Breach Prevention About Identity Theft Overview And Techniques
Data Breach Prevention About Identity Theft Overview And TechniquesThis slide talks about the major crime committed by phishers, named as identity theft. The purpose of this slide is to outline the ways of stealing information, such as robbery, computer fraud, social networking sites, mail theft, and dumpster diving. Present the topic in a bit more detail with this Data Breach Prevention About Identity Theft Overview And Techniques. Use it as a tool for discussion and navigation on Drivers License, Social Security Card, Debit Or Credit Cards, Social Media Account. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention Techniques
Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention TechniquesThis slide demonstrates the different types pf pharming phishing scams. The primary types include malware-based pharming and DNS pharming. This slide also outlines the ways which helps to prevent a pharming attack such as verify the URL, install VPN, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention Techniques. Dispense information and present a thorough explanation of Pharming Phishing Scams, Malware Based Pharming, Pharming Attack, Prevention Techniques using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 About Techniques Cloud Data Leakage Prevention Cloud Cryptography
About Techniques Cloud Data Leakage Prevention Cloud CryptographyThis slide talks about the cloud data leakage prevention methods. The purpose of this slide is to briefly explain the features of cloud data leakage prevention tools such as data discovery and classification, policy-based controls, data monitoring and alerts, etc. Present the topic in a bit more detail with this About Techniques Cloud Data Leakage Prevention Cloud Cryptography. Use it as a tool for discussion and navigation on Cryptography Techniques, Data Monitoring And Alerts, Encryption And Tokenization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Techniques To Prevent Eclipse Attack And Secure Funds Hands On Blockchain Security Risk BCT SS V
Techniques To Prevent Eclipse Attack And Secure Funds Hands On Blockchain Security Risk BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Introducing Techniques To Prevent Eclipse Attack And Secure Funds Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Random Node Selection, Deterministic Node Selection, New Node Restrictions, using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V
Blockchain And Cybersecurity Techniques To Prevent Eclipse Attack And Secure Funds BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V This template helps you present information on Four stages. You can also present information on Increased Node Connections, Deterministic Node Selection, New Node Restrictions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Corporate World Crime Prevention Techniques
Corporate World Crime Prevention TechniquesThis slide depicts the techniques to prevent crime in corporate world. Its aim is to reduce crimes in organisation. This slide includes hiring crime lawyer, ethics training, monitor system, regulate internet use, cyber protection. Introducing our premium set of slides with Corporate World Crime Prevention Techniques Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Corporate Crime Lawyer, Business Ethics, Monitoring System So download instantly and tailor it with your information.
-
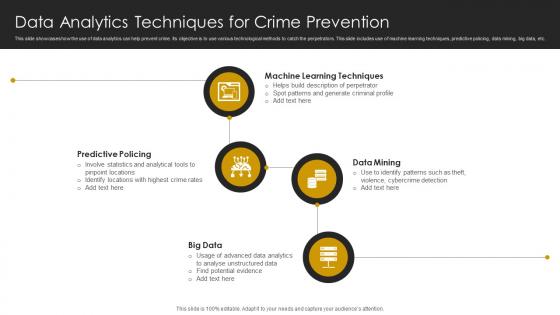 Data Analytics Techniques For Crime Prevention
Data Analytics Techniques For Crime PreventionThis slide showcases how the use of data analytics can help prevent crime. Its objective is to use various technological methods to catch the perpetrators. This slide includes use of machine learning techniques, predictive policing, data mining, big data, etc. Presenting our set of slides with Data Analytics Techniques For Crime Prevention This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Predictive Policing, Data Mining, Machine Learning
-
 Cyber Threats In Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V
Cyber Threats In Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Introducing Cyber Threats In Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Mining Capability, Mining Capabilities, Much Faster Rate using this template. Grab it now to reap its full benefits.
-
 Ransomware In Digital Age About Cryptolocker Overview And Prevention Techniques
Ransomware In Digital Age About Cryptolocker Overview And Prevention TechniquesThis slide highlights the overview of CryptoLocker ransomware attack. The purpose of this slide is to showcase the strategies used in prevention of this attack and also describes the steps to defend against CryptoLocker such as immediately disconnect from the network, report to law enforcement authorities, etc. Deliver an outstanding presentation on the topic using this Ransomware In Digital Age About Cryptolocker Overview And Prevention Techniques. Dispense information and present a thorough explanation of Cryptolocker Ransomware Attack, Prevention Of This Attack, Law Enforcement Authorities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ransomware In Digital Age About Locky Overview And Prevention Techniques
Ransomware In Digital Age About Locky Overview And Prevention TechniquesThis slide highlights the overview of Locky ransomware attack, describing its specific characteristics and highlighting effective prevention techniques to protect against these type of attacks such as keep software updated, implement robust backup solutions, etc. Deliver an outstanding presentation on the topic using this Ransomware In Digital Age About Locky Overview And Prevention Techniques. Dispense information and present a thorough explanation of Email Attachments, Fake Websites, Unethical Advertisement, Potential Damage Caused using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ransomware In Digital Age Ransomware Prevention Techniques Implementation Budget
Ransomware In Digital Age Ransomware Prevention Techniques Implementation BudgetThis slide represents the budget allocation to tackle ransomware attacks. This budget aims to implement protection measure techniques such as firewall installation, data backup solutions, security monitoring, and a proper incident response plan. Deliver an outstanding presentation on the topic using this Ransomware In Digital Age Ransomware Prevention Techniques Implementation Budget. Dispense information and present a thorough explanation of Antivirus Software, Data Backup Solution, Vulnerability Management, Network Segmentation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ransomware In Digital Age Teslacrypt Ransomware Overview And Preventing Techniques
Ransomware In Digital Age Teslacrypt Ransomware Overview And Preventing TechniquesThis slide provides an overview of TeslaCrypt, its targets, and distribution methods. It emphasizes on defense measures to be taken after a ransomware attack and prevention strategies such as backup, software update, and utilizing security products. Deliver an outstanding presentation on the topic using this Ransomware In Digital Age Teslacrypt Ransomware Overview And Preventing Techniques. Dispense information and present a thorough explanation of After Attack Prevention Measures, Preventing Techniques, Plugins And Operating Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Techniques To Prevent Eclipse Attack And Secure Funds Guide For Blockchain BCT SS V
Techniques To Prevent Eclipse Attack And Secure Funds Guide For Blockchain BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Introducing Techniques To Prevent Eclipse Attack And Secure Funds Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Random Node Selection, Deterministic Node Selection using this template. Grab it now to reap its full benefits.
-
 Techniques To Prevent Eclipse Securing Blockchain Transactions A Beginners Guide BCT SS V
Techniques To Prevent Eclipse Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Increase audience engagement and knowledge by dispensing information using Techniques To Prevent Eclipse Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on four stages. You can also present information on Random Node Selection, New Node Restrictions, Increased Node Connections using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Stimulation And Prevention Conflict For Managing Resolution Techniques
Stimulation And Prevention Conflict For Managing Resolution TechniquesThis slide showcases stimulation and prevention conflict resolution techniques for maintaining balanced approach between productive and harmonious work environment. It includes strategies such as reorganizing, communication, competition, etc. Presenting our well structured Stimulation And Prevention Conflict For Managing Resolution Techniques. The topics discussed in this slide are Basis, Conflict Promotion Techniques. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Key Techniques To Prevent Negative Feedback
Key Techniques To Prevent Negative FeedbackThis slide presents strategies to prevent negative feedback before it occurs. It covers techniques such as periodic feedback, customer prioritization, real-time customer support, etc. Presenting our set of slides with Key Techniques To Prevent Negative Feedback. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Periodic Feedback, Customer Prioritization, Real Time Customer Support.
-
 Prevention Techniques For Cyber Security Data Attacks
Prevention Techniques For Cyber Security Data AttacksThe highlighted slide identifies critical types of cybersecurity attacks on data, including malware, phishing, password attacks, man in the middle attacks, and SQL injection. This information is essential for understanding and preparing against various threats, contributing to a more robust defense strategy for safeguarding data. Introducing our Prevention Techniques For Cyber Security Data Attacks set of slides. The topics discussed in these slides are Malware Attack, Phishing Attack, Password Attack. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Employee Theft Prevention Techniques To Reduce Inventory Shrinkage
Employee Theft Prevention Techniques To Reduce Inventory ShrinkageThis slide mentions the preventive measures to reduce employee thefts for minimizing inventory shrinkage. Various measures included are conducting regular audits, testing the employees, and securing the staff-only areas. Introducing our premium set of slides with Employee Theft Prevention Techniques To Reduce Inventory Shrinkage Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Conduct Regular Audits, Test The Employees, Secure Inventory Area So download instantly and tailor it with your information.
-
 Access Management Techniques To Prevent Cyberattacks Strategic Guide To Implement Strategy SS
Access Management Techniques To Prevent Cyberattacks Strategic Guide To Implement Strategy SSThis slide showcases Access management techniques to prevent cyber attacks. It includes strategies such as Single sign-On, password management, biometric authentication and access control lists ACLs.Introducing Access Management Techniques To Prevent Cyberattacks Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Password Management, Biometric Authentication, Access Control Lists, using this template. Grab it now to reap its full benefits.
-
 Techniques To Prevent Employee Personal Accounts Strategic Guide To Implement Strategy SS
Techniques To Prevent Employee Personal Accounts Strategic Guide To Implement Strategy SSThis slide showcases the Techniques to prevent employee personal accounts. It includes strategies such as education and training, device security, two-factor authentication 2FA and secure Wi-Fi and networks.Increase audience engagement and knowledge by dispensing information using Techniques To Prevent Employee Personal Accounts Strategic Guide To Implement Strategy SS. This template helps you present information on four stages. You can also present information on Device Security, Education And Training, Two Factor Authentication, Networks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attack Prevention Techniques Building A Security Awareness Program
Social Engineering Attack Prevention Techniques Building A Security Awareness ProgramThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. Deliver an outstanding presentation on the topic using this Social Engineering Attack Prevention Techniques Building A Security Awareness Program. Dispense information and present a thorough explanation of Public Information, Prevention Techniques, Social Engineering Attack using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Attack Prevention Techniques Conducting Security Awareness
Social Engineering Attack Prevention Techniques Conducting Security AwarenessThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Conducting Security Awareness. Use it as a tool for discussion and navigation on Techniques, Limit Public Information, Verify Source. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attack Prevention Techniques Developing Cyber Security Awareness Training
Social Engineering Attack Prevention Techniques Developing Cyber Security Awareness TrainingThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. Deliver an outstanding presentation on the topic using this Social Engineering Attack Prevention Techniques Developing Cyber Security Awareness Training. Dispense information and present a thorough explanation of Limit Public Information, Verify The Source, No Sharing Of Password using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security
Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Limit Public Information, Verify The Source, No Sharing Of Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attack Prevention Techniques Implementing Security Awareness Training
Social Engineering Attack Prevention Techniques Implementing Security Awareness TrainingThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Limit Public Information, Verify The Source, No Sharing Of Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attack Prevention Techniques Raising Cyber Security Awareness In Organizations
Social Engineering Attack Prevention Techniques Raising Cyber Security Awareness In OrganizationsThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Raising Cyber Security Awareness In Organizations. Use it as a tool for discussion and navigation on Verify The Source, Sharing Of Password, Public Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Customer Churn Prevention Strategies On Business Churn Management Techniques
Impact Of Customer Churn Prevention Strategies On Business Churn Management TechniquesMentioned slide outlines the impact of implementing attrition rate prevention techniques on organizational performance. The graph is covering information about monthly recurring revenue MRR, customer lifetime value CLV, and customer acquisition cost CAC along with key intakes. Present the topic in a bit more detail with this Impact Of Customer Churn Prevention Strategies On Business Churn Management Techniques. Use it as a tool for discussion and navigation on Customer Churn, Prevention Strategies, Business Performance, Streamlining Customer Onboarding. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk analysis techniques cost tracker for preventing funds misappropriation
Risk analysis techniques cost tracker for preventing funds misappropriationThis slide covers a worksheet to categorize all the costs associated with a detailed project and specifies labour rates and material required for each task. Present the topic in a bit more detail with this Risk Analysis Techniques Cost Tracker For Preventing Funds Misappropriation. Use it as a tool for discussion and navigation on Project Lead, Project Info, Budget Summary, Excavation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Inventory Shrinkages Types With Loss Prevention Mitigation Techniques
Inventory Shrinkages Types With Loss Prevention Mitigation TechniquesFollowing slide illustrates various types of inventory shrinkage in retail businesses such as shoplifting, return fraud etc. The template covers information about loss prevention mitigation techniques which will assist store manager to increase business profits. Presenting our well structured Inventory Shrinkages Types With Loss Prevention Mitigation Techniques. The topics discussed in this slide are Return Fraud, Employee Theft, Vendor Fraud. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Various Techniques To Successfully Prevent Business Compromise Conducting Security Awareness
Various Techniques To Successfully Prevent Business Compromise Conducting Security AwarenessThe purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Present the topic in a bit more detail with this Various Techniques To Successfully Prevent Business Compromise Conducting Security Awareness. Use it as a tool for discussion and navigation on Techniques, Key Description, Priority. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various Techniques To Successfully Prevent Business Email Compromise Attack Developing Cyber Security Awareness
Various Techniques To Successfully Prevent Business Email Compromise Attack Developing Cyber Security AwarenessThe purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Present the topic in a bit more detail with this Various Techniques To Successfully Prevent Business Email Compromise Attack Developing Cyber Security Awareness. Use it as a tool for discussion and navigation on Various Techniques, Successfully Prevent, Business Email, Compromise Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various Techniques To Successfully Prevent Business Implementing Security Awareness Training
Various Techniques To Successfully Prevent Business Implementing Security Awareness TrainingThe purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Increase audience engagement and knowledge by dispensing information using Various Techniques To Successfully Prevent Business Implementing Security Awareness Training. This template helps you present information on one stage. You can also present information on Sender Policy Framework, Strong Process For Wire Transfers, Strong Password Policy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Techniques To Recover Revenue And Prevent Leak In Healthcare Industry
Techniques To Recover Revenue And Prevent Leak In Healthcare IndustryThe given below slide depicts some ways to prevent revenue loss in healthcare sector. It includes activities such as promoting customers, engaging patients, building up offerings, maximizing referrals and reducing denials etc. Presenting our set of slides with Techniques To Recover Revenue And Prevent Leak In Healthcare Industry. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Promote Consumers, Engage Patients, Reduce Turndown.
-
 Various Techniques To Successfully Prevent Business Email Preventing Data Breaches Through Cyber Security
Various Techniques To Successfully Prevent Business Email Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Increase audience engagement and knowledge by dispensing information using Various Techniques To Successfully Prevent Business Email Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Sender Policy Framework, Strong Password Policy, Strong Process For Wire Transfers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ultimate Guide For Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS
Ultimate Guide For Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SSThe following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51 Percent attack, etc. Increase audience engagement and knowledge by dispensing information using Ultimate Guide For Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS This template helps you present information on Three stages. You can also present information on Random Node Selection, Deterministic Node Selection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Retail Loss Prevention Techniques In Powerpoint And Google Slides Cpb
Retail Loss Prevention Techniques In Powerpoint And Google Slides CpbPresenting Retail Loss Prevention Techniques In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Retail Loss Prevention Techniques. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Various Techniques To Successfully Prevent Raising Cyber Security Awareness In Organizations
Various Techniques To Successfully Prevent Raising Cyber Security Awareness In OrganizationsThe purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Deliver an outstanding presentation on the topic using this Various Techniques To Successfully Prevent Raising Cyber Security Awareness In Organizations. Dispense information and present a thorough explanation of Strong Password Policy, Strong Process, Wire Transfers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Benefits Of Preventing Customer Churn Churn Management Techniques Ppt Icon Information
Key Benefits Of Preventing Customer Churn Churn Management Techniques Ppt Icon InformationMentioned slide outlines the different benefits associated with preventing attrition rate and retaining customers. The major advantages are reduced customer acquisition cost CAC, strengthened customer loyalty, word of mouth WOM referrals, and increased customer lifetime value CLV. Increase audience engagement and knowledge by dispensing information using Key Benefits Of Preventing Customer Churn Churn Management Techniques Ppt Icon Information. This template helps you present information on four stages. You can also present information on Reduced Customer Acquisition Cost, Strengthen Customer Loyalty, Increased Customer Lifetime Value using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Asset Tagging And Labeling For Theft Prevention Optimization Of Fixed Asset Techniques To Enhance
Asset Tagging And Labeling For Theft Prevention Optimization Of Fixed Asset Techniques To EnhanceThis slide represents asset tagging and labeling for theft prevention. It covers RFID, BLE, Wi Fi, cellular, GPS and satellite for asset tracking and monitoring. Present the topic in a bit more detail with this Asset Tagging And Labeling For Theft Prevention Optimization Of Fixed Asset Techniques To Enhance. Use it as a tool for discussion and navigation on Prevention, Tagging, Labeling. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Techniques To Prevent Identity Fraud Incidents
Techniques To Prevent Identity Fraud IncidentsThis slide showcases strategies undertaken to reduce chances of identity fraud. This template focuses on reducing risk of becoming victim by taking simple steps to protect personal information. It covers aspects such as freezing credit, creating strong passwords, etc.Introducing our Techniques To Prevent Identity Fraud Incidents set of slides. The topics discussed in these slides are Antivirus Software, Individual Itself, Accessing Information. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ecommerce Fraud Prevention Techniques In Powerpoint And Google Slides Cpb
Ecommerce Fraud Prevention Techniques In Powerpoint And Google Slides CpbPresenting our Ecommerce Fraud Prevention Techniques In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Down Round Funding This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Preventive Measures To Reduce Warehouse Theft Techniques To Optimize Warehouse
Preventive Measures To Reduce Warehouse Theft Techniques To Optimize WarehouseThis slide showcases preventive measure that can be taken by organization to prevent theft in warehouse. It includes improving layout of warehouse and managing plus monitoring human activity in warehouse. Introducing Preventive Measures To Reduce Warehouse Theft Techniques To Optimize Warehouse to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Managing Human Activity, Improving Warehouse Layout, Less Doors, using this template. Grab it now to reap its full benefits.
-
 Q925 Implementing Warehouse Management System For Theft Prevention Techniques To Optimize
Q925 Implementing Warehouse Management System For Theft Prevention Techniques To OptimizeThis slide showcases implementation of warehouse management system that can help organization in theft prevention. It showacses features and impact of implementing WMS in organization. Present the topic in a bit more detail with this Q925 Implementing Warehouse Management System For Theft Prevention Techniques To Optimize. Use it as a tool for discussion and navigation on Parameters, System Security, Warehouse Theft. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Preventive Measures To Reduce Warehouse Theft Techniques For Inventory Management
Preventive Measures To Reduce Warehouse Theft Techniques For Inventory ManagementThis slide showcases preventive measure that can be taken by organization to prevent theft in warehouse. It includes improving layout of warehouse and managing plus monitoring human activity in warehouse. Present the topic in a bit more detail with this Preventive Measures To Reduce Warehouse Theft Techniques For Invent Management. Use it as a tool for discussion and navigation on Managing Human Activity, Improving Warehouse Layout, Review Employee Performances. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Preventive Measures To Reduce Warehouse Theft Inventory Management Techniques To Reduce
Preventive Measures To Reduce Warehouse Theft Inventory Management Techniques To ReduceThis slide showcases preventive measure that can be taken by organization to prevent theft in warehouse. It includes improving layout of warehouse and managing plus monitoring human activity in warehouse. Deliver an outstanding presentation on the topic using this Preventive Measures To Reduce Warehouse Theft Inventory Management Techniques To Reduce. Dispense information and present a thorough explanation of Measures, Reduce, Theft using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Marketing plan preventive maintenance branding technique business automation
Marketing plan preventive maintenance branding technique business automationPresenting this set of slides with name - Marketing Plan Preventive Maintenance Branding Technique Business Automation. This is an editable six graphic that deals with topics like Marketing Plan, Preventive Maintenance, Branding Technique, Business Automation to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Ddos prevention techniques ppt powerpoint presentation file slideshow cpb
Ddos prevention techniques ppt powerpoint presentation file slideshow cpbPresenting this set of slides with name DDOS Prevention Techniques Ppt Powerpoint Presentation File Slideshow Cpb. This is an editable Powerpoint four stages graphic that deals with topics like DDOS Prevention Techniques to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Data breach prevention techniques ppt powerpoint presentation infographics skills cpb
Data breach prevention techniques ppt powerpoint presentation infographics skills cpbPresenting this set of slides with name Data Breach Prevention Techniques Ppt Powerpoint Presentation Infographics Skills Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Data Breach Prevention Techniques to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Data breach prevention techniques ppt powerpoint presentation tips cpb
Data breach prevention techniques ppt powerpoint presentation tips cpbPresenting this set of slides with name Data Breach Prevention Techniques Ppt Powerpoint Presentation Tips Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Data Breach Prevention Techniques to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.




