Powerpoint Templates and Google slides for Prevention And Mitigation
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Data Breach Prevention And Mitigation Strategies For Businesses Powerpoint Presentation Slides
Data Breach Prevention And Mitigation Strategies For Businesses Powerpoint Presentation SlidesThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Data Breach Prevention And Mitigation Strategies For Businesses Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of seventy five slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Disaster Prevention And Mitigation Powerpoint Presentation Slides
Disaster Prevention And Mitigation Powerpoint Presentation SlidesPresenting this set of slides with name - Disaster Prevention And Mitigation Powerpoint Presentation Slides. This complete deck is oriented to make sure you do not lag in your presentations. Our creatively crafted slides come with apt research and planning. This exclusive deck with thirty three slides is here to help you to strategize, plan, analyse, or segment the topic with clear understanding and apprehension. When you download this presentation by clicking the download button, you can get the presentation in both standard and widescreen format. All slides are fully customizable. Change the colors, font, size, add and remove things as per your needs. The presentation is fully supported with Google Slides. It can be easily converted into JPG or PDF format.
-
 Prevention And Mitigation In Disaster Management Powerpoint Presentation Slides
Prevention And Mitigation In Disaster Management Powerpoint Presentation SlidesPresenting this set of slides with name - Prevention And Mitigation In Disaster Management Powerpoint Presentation Slides. Our topic-specific Prevention And Mitigation In Disaster Management Powerpoint Presentation Slides presentation deck contains thirty-two slides to formulate the topic with a sound understanding. We have created customizable templates keeping your convenience in mind. Edit the color, text, font style at your ease. Add or delete content if needed. Download PowerPoint templates in both widescreen and standard screen. The presentation is fully supported by Google Slides. It can be easily converted into JPG or PDF format
-
 Prevention Protection And Mitigation Planning Powerpoint Presentation Slides
Prevention Protection And Mitigation Planning Powerpoint Presentation SlidesPresenting this set of slides with name - Prevention Protection And Mitigation Planning Powerpoint Presentation Slides. This deck comprises of total of thirty two slides. It has PPT templates with creative visuals and well researched content. Not just this, our PowerPoint professionals have crafted this deck with appropriate diagrams, layouts, icons, graphs, charts and more. This content ready presentation deck is fully editable. Just click the DOWNLOAD button below. Change the colour, text and font size. You can also modify the content as per your need. Get access to this well crafted complete deck presentation and leave your audience stunned.
-
 Data Breach Prevention And Mitigation Data Breach Prevention Status Tracking Dashboard
Data Breach Prevention And Mitigation Data Breach Prevention Status Tracking DashboardThis slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc. Present the topic in a bit more detail with this Data Breach Prevention And Mitigation Data Breach Prevention Status Tracking Dashboard. Use it as a tool for discussion and navigation on Critical Cyber Security, Performance Indicators, Encryption Status, License Consumption, Windows Defender. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
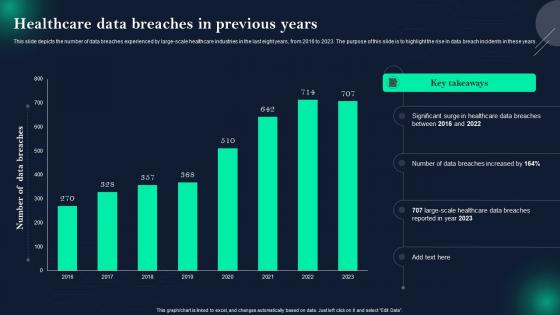 Data Breach Prevention And Mitigation Healthcare Data Breaches In Previous Years
Data Breach Prevention And Mitigation Healthcare Data Breaches In Previous YearsThis slide depicts the number of data breaches experienced by large-scale healthcare industries in the last eight years, from 2016 to 2023. The purpose of this slide is to highlight the rise in data breach incidents in these years. Present the topic in a bit more detail with this Data Breach Prevention And Mitigation Healthcare Data Breaches In Previous Years. Use it as a tool for discussion and navigation on Data Breaches Experienced, Large Scale Healthcare Industries, Significant Surge In Healthcare. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention And Mitigation Number Of Data Breaches In Different Sectors
Data Breach Prevention And Mitigation Number Of Data Breaches In Different SectorsThe purpose of this slide is to outline the number of data breach attacks in different sectors from the year 2011 to 2023. The departments covered in this slide are business, medical, educational, government, and financial. Deliver an outstanding presentation on the topic using this Data Breach Prevention And Mitigation Number Of Data Breaches In Different Sectors. Dispense information and present a thorough explanation of Data Breach Attacks, Business, Medical, Educational, Government, Financial using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agenda For Data Breach Prevention And Mitigation Strategies For Businesses
Agenda For Data Breach Prevention And Mitigation Strategies For BusinessesIntroducing Agenda For Data Breach Prevention And Mitigation Strategies For Businesses to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Data Exploitation Techniques, Data Breach Prevention, Mitigation Strategies For Businesses, using this template. Grab it now to reap its full benefits.
-
 Data Breach Prevention Advanced Measures For Data Breach Prevention And Mitigation
Data Breach Prevention Advanced Measures For Data Breach Prevention And MitigationThis slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach. Deliver an outstanding presentation on the topic using this Data Breach Prevention Advanced Measures For Data Breach Prevention And Mitigation. Dispense information and present a thorough explanation of Incident Response Plans, AI And Automation, Zero Trust Security Approach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention And Mitigation Checklist For Responding To A Data Breach Attack
Data Breach Prevention And Mitigation Checklist For Responding To A Data Breach AttackThis slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc. Present the topic in a bit more detail with this Data Breach Prevention And Mitigation Checklist For Responding To A Data Breach Attack. Use it as a tool for discussion and navigation on Data Breach Response Plan, Fundamental Approaches, Systems Or Networks, Perform A Formal Risk Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention And Mitigation Common Data Breach Attack Vectors
Data Breach Prevention And Mitigation Common Data Breach Attack VectorsThis slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention And Mitigation Common Data Breach Attack Vectors. Dispense information and present a thorough explanation of Brute Force Attacks, Purchasing Stolen Credentials, Phishing Scams, Fraudulent Emails, Deceptive Websites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention And Mitigation Data Breach Attacks Experienced By Major Business
Data Breach Prevention And Mitigation Data Breach Attacks Experienced By Major BusinessThis slide highlights the top data breach victims based on different industrial sectors. These industries include email service providers, social media websites, online auction websites, retail services, government agencies, file-sharing and hosting services, etc. Present the topic in a bit more detail with this Data Breach Prevention And Mitigation Data Breach Attacks Experienced By Major Business. Use it as a tool for discussion and navigation on Heartland Payment Systems, Email Service Provider, Social Media Website, Online Auction Website. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention And Mitigation Data Breach Awareness Training Program
Data Breach Prevention And Mitigation Data Breach Awareness Training ProgramThis slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs. Deliver an outstanding presentation on the topic using this Data Breach Prevention And Mitigation Data Breach Awareness Training Program. Dispense information and present a thorough explanation of Phishing Emails And Social Engineering, Data Breaches And Cybersecurity, Data Privacy Regulations And Compliance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention And Mitigation Data Breach Response Plan Fix Vulnerabilities
Data Breach Prevention And Mitigation Data Breach Response Plan Fix VulnerabilitiesThis slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention And Mitigation Data Breach Response Plan Fix Vulnerabilities. Dispense information and present a thorough explanation of Collaborate With Forensics Experts, Review Network Segmentation, Communicate Transparently using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention And Mitigation Data Exploitation Methods Used By Criminals
Data Breach Prevention And Mitigation Data Exploitation Methods Used By CriminalsThis slide discusses the exploitation of data after stealing it from authorized resources. These methods include opening new credit cards, withdrawing money from accounts, filing fraudulent tax returns, medical treatment using insurance, using credit card rewards, etc. Present the topic in a bit more detail with this Data Breach Prevention And Mitigation Data Exploitation Methods Used By Criminals. Use it as a tool for discussion and navigation on File Fraudulent Tax Returns, Withdraw Money From Accounts, Medical Treatment Using Insurance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention And Mitigation Different Modes Of Data Breach Attack
Data Breach Prevention And Mitigation Different Modes Of Data Breach AttackThis slide discusses the unintentional and intentional methods of data breach attacks. The examples outlined in this slide are accessing unsecured websites, downloading compromised software, losing work devices in a public place, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention And Mitigation Different Modes Of Data Breach Attack. Dispense information and present a thorough explanation of Unintentional And Intentional Methods, Data Breach Attacks, Unsecured Websites, Downloading Compromised Software, Losing Work Devices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention And Mitigation Major Types Of Data Security Breaches
Data Breach Prevention And Mitigation Major Types Of Data Security BreachesThis slide discusses the significant categories of information loss. The purpose of this slide is to describe several types of data security breaches. These include human error, device loss, cyberattacks, internal breaches, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention And Mitigation Major Types Of Data Security Breaches. Dispense information and present a thorough explanation of Social Engineering Attacks, IT Team Misconfiguring Servers, Disgruntled Employees, Gain Unauthorized Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention And Mitigation Malicious Methods Used To Breach Data
Data Breach Prevention And Mitigation Malicious Methods Used To Breach DataThe purpose of this slide is to outline the different ways to steal user data to accomplish a data breach attack. The main malicious methods used for this purpose are phishing, brute force attacks, social engineering, malware, etc. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention And Mitigation Malicious Methods Used To Breach Data. This template helps you present information on four stages. You can also present information on Criminals Look For Vulnerabilities, Possible Password Combination, Social Engineering, Malware using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Breach Prevention And Mitigation Overview Of Various Targets Of Data Breach
Data Breach Prevention And Mitigation Overview Of Various Targets Of Data BreachThis slide represents information about several data breach targets and types of data compromised. These targets are organizations and businesses, government agencies, healthcare providers, financial institutions, individuals, websites, online platforms, etc. Present the topic in a bit more detail with this Data Breach Prevention And Mitigation Overview Of Various Targets Of Data Breach. Use it as a tool for discussion and navigation on Organizations And Businesses, Healthcare Providers, Educational Institutions, Websites And Online Platforms. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention And Mitigation Steps To Be Taken After Identity Theft
Data Breach Prevention And Mitigation Steps To Be Taken After Identity TheftThis slide outlines the steps to recover from identity theft. These are determining the nature of the data breach, contact the financial institution, strengthen all passwords, review freely available credit reports and monitor accounts for suspicious activity. Deliver an outstanding presentation on the topic using this Data Breach Prevention And Mitigation Steps To Be Taken After Identity Theft. Dispense information and present a thorough explanation of Strengthen All Passwords, Review Free Credit Reports, Contact Your Financial Institution using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention Strategies For Employees Data Breach Prevention And Mitigation
Data Breach Prevention Strategies For Employees Data Breach Prevention And MitigationThis slide highlights the data breach mitigation measures for workers. These strategies include maintain a record of banking receipts, do not believe everything, be mindful of sharing anything on social media, secure all devices, protect individual accounts, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention Strategies For Employees Data Breach Prevention And Mitigation. Dispense information and present a thorough explanation of Data Breach Mitigation Measures, Banking Receipts, Social Media, Secure All Devices, Protect Individual Accounts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention Strategies For Enterprises Data Breach Prevention And Mitigation
Data Breach Prevention Strategies For Enterprises Data Breach Prevention And MitigationThe purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Present the topic in a bit more detail with this Data Breach Prevention Strategies For Enterprises Data Breach Prevention And Mitigation. Use it as a tool for discussion and navigation on Network Security, Data Loss Prevention, Regularly Perform Patching Activities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention Strategies For Users Data Breach Prevention And Mitigation
Data Breach Prevention Strategies For Users Data Breach Prevention And MitigationThis slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention Strategies For Users Data Breach Prevention And Mitigation. Dispense information and present a thorough explanation of Unusual Email Attachments, Maintain Software And Hardware, Several Online Services using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Response Plan Secure Operations Data Breach Prevention And Mitigation
Data Breach Response Plan Secure Operations Data Breach Prevention And MitigationThis slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. Present the topic in a bit more detail with this Data Breach Response Plan Secure Operations Data Breach Prevention And Mitigation. Use it as a tool for discussion and navigation on Assemble Expert Team, Consult With Legal Counsel, Secure Physical Areas. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide For Data Breach Prevention And Mitigation Strategies For Businesses
Icons Slide For Data Breach Prevention And Mitigation Strategies For BusinessesPresenting our well crafted Icons Slide For Data Breach Prevention And Mitigation Strategies For Businesses set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Table Of Contents For Data Breach Prevention And Mitigation Strategies For Businesses
Table Of Contents For Data Breach Prevention And Mitigation Strategies For BusinessesIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Data Breach Prevention And Mitigation Strategies For Businesses. This template helps you present information on ten stages. You can also present information on Data Breach Prevention Tools, Data Breach Response Plan, Prevention And Mitigation, Training And Budget using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 K81 Data Breach Prevention And Mitigation Strategies For Businesses For Table Of Contents
K81 Data Breach Prevention And Mitigation Strategies For Businesses For Table Of ContentsIntroducing K81 Data Breach Prevention And Mitigation Strategies For Businesses For Table Of Contents to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Data Breach Prevention, Mitigation Strategies For Businesses, Data Loss Prevention Tools, using this template. Grab it now to reap its full benefits.
-
 K103 Identification And Prevention Of Spear Phishing Attacks And Strategies To Mitigate Them V2
K103 Identification And Prevention Of Spear Phishing Attacks And Strategies To Mitigate Them V2This slide talks about the various methods of identifying spear phishing cyber attacks. The purpose of this slide is to help users prevent spear phishing scams. The key signs include unusual request, shared drive links and documents with password protection. Introducing K103 Identification And Prevention Of Spear Phishing Attacks And Strategies To Mitigate Them V2 to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing Cyber Attacks, Prevent Spear Phishing Scams, Password Protection, Identification And Prevention, using this template. Grab it now to reap its full benefits.
-
 K104 Preventive Measures To Avoid Evil Twin Scams Phishing Attacks And Strategies To Mitigate Them V2
K104 Preventive Measures To Avoid Evil Twin Scams Phishing Attacks And Strategies To Mitigate Them V2This slide outlines the various preventive measures to avoid evil twin attacks. The key steps include use your own hotspot, avoid unsecured wi-fis, disable auto-connect, avoid logging into private accounts on public Wi-Fi, use VPN, visit HTTPS websites, etc. Increase audience engagement and knowledge by dispensing information using K104 Preventive Measures To Avoid Evil Twin Scams Phishing Attacks And Strategies To Mitigate Them V2. This template helps you present information on six stages. You can also present information on Avoid Evil Twin Scams, Personal Information, Preventive Measures, Hackers Accessing Your Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 K105 Preventive Measures To Avoid Watering Hole Phishing Attacks And Strategies To Mitigate Them V2
K105 Preventive Measures To Avoid Watering Hole Phishing Attacks And Strategies To Mitigate Them V2This slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc. Introducing K105 Preventive Measures To Avoid Watering Hole Phishing Attacks And Strategies To Mitigate Them V2 to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability Scanning, Security Patches, Bug Bounty Programs, Input Validation, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Clone Phishing Attacks Preventive Measures
Phishing Attacks And Strategies To Mitigate Them V2 Clone Phishing Attacks Preventive MeasuresThis slide talks about the various steps that can be taken to prevent clone phishing attacks. These include review senders address, preview links before opening them, use a password manager, investigate spoofed replies, double check URL addresses, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Clone Phishing Attacks Preventive Measures. This template helps you present information on eight stages. You can also present information on Investigate Spoofed Replies, Clone Phishing Attacks Preventive, Resemble Authentic Email Addresses using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Identification And Prevention Of Angler Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Identification And Prevention Of Angler PhishingThis slide talks about the various methods of identifying angler phishing cyber attacks. The purpose of this slide is to help users identify angler phishing scams. These include notifications, abnormal direct messages, links to the different websites, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Identification And Prevention Of Angler Phishing. Use it as a tool for discussion and navigation on Identification And Prevention, Angler Phishing Scams, Abnormal Direct Messages, Credentials In Direct Messages. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention Techniques
Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention TechniquesThis slide demonstrates the different types pf pharming phishing scams. The primary types include malware-based pharming and DNS pharming. This slide also outlines the ways which helps to prevent a pharming attack such as verify the URL, install VPN, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention Techniques. Dispense information and present a thorough explanation of Pharming Phishing Scams, Malware Based Pharming, Pharming Attack, Prevention Techniques using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle Cyber
Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle CyberThis slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle Cyber to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure Connections, Avoid Phishing Emails, Endpoint Security, Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And Code
Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And CodeThis slide talks about the techniques which can help in protecting organizations from phishing and vishing attacks. The purpose of this slide is to explain two important methods of preventing cyber scams. These techniques are email signing and code signing. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And Code. Dispense information and present a thorough explanation of Vishing Attacks Prevention, Email Signing And Code Signing, Preventing Cyber Scams using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Methods To Prevent And Mitigate Security Incidents
Methods To Prevent And Mitigate Security IncidentsThis slide depicts the multiple methods to prevent and mitigate security incidents. The purpose of this slide is to help the business identify a suitable approach to eliminate current and future security incidents. It includes security incident detection, tracking suspicious activity, etc. Presenting our set of slides with Methods To Prevent And Mitigate Security Incidents. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Incident, Account Behavior, Monitor Network Traffic.
-
 Social Engineering Methods And Mitigation Identification And Prevention Of Angler Phishing Scams
Social Engineering Methods And Mitigation Identification And Prevention Of Angler Phishing ScamsThis slide talks about the various methods of identifying angler phishing cyber attacks. The purpose of this slide is to help users identify angler phishing scams. These include notifications, abnormal direct messages, links to the different websites, etc. Introducing Social Engineering Methods And Mitigation Identification And Prevention Of Angler Phishing Scams to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Angler Phishing Cyber Attacks, Angler Phishing Scams, Notifications, Abnormal Direct Message, using this template. Grab it now to reap its full benefits.
-
 Identification And Prevention Of Spear Phishing Attacks Social Engineering Methods And Mitigation
Identification And Prevention Of Spear Phishing Attacks Social Engineering Methods And MitigationThis slide talks about the various methods of identifying spear phishing cyber attacks. The purpose of this slide is to help users prevent spear phishing scams. The key signs include unusual request, shared drive links and documents with password protection. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Identification And Prevention Of Spear Phishing Attacks. This template helps you present information on three stages. You can also present information on Unusual Request, Shared Drive Links, Documents With Password Protection, Spear Phishing Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cost Tracker For Preventing Funds Risk Assessment And Mitigation Plan
Cost Tracker For Preventing Funds Risk Assessment And Mitigation PlanThis slide covers a worksheet to categorize all the costs associated with a detailed project and specifies labour rates and material required for each task. Present the topic in a bit more detail with this Cost Tracker For Preventing Funds Risk Assessment And Mitigation Plan. Use it as a tool for discussion and navigation on Cost Tracker For Preventing Funds Misappropriation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cost Tracker For Preventing Funds Misappropriation Risk Evaluation And Mitigation Plan
Cost Tracker For Preventing Funds Misappropriation Risk Evaluation And Mitigation PlanThis slide covers a worksheet to categorize all the costs associated with a detailed project and specifies labour rates and material required for each task. Deliver an outstanding presentation on the topic using this Cost Tracker For Preventing Funds Misappropriation Risk Evaluation And Mitigation Plan. Dispense information and present a thorough explanation of Cost Tracker For Preventing Funds Misappropriation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Prevention And Mitigation Strategies Table
Risk Prevention And Mitigation Strategies TableThis slide covers the mitigation strategies to prevent from potential risks involved in different scenarios ramming, triggered explosion, hijacking or terrorist. Presenting our well-structured Risk Prevention And Mitigation Strategies Table. The topics discussed in this slide are Target, Scenario, Mechanism, Mitigation. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Mitigating Transaction Risks Through Policies And Preventing Money Laundering Through Transaction
Mitigating Transaction Risks Through Policies And Preventing Money Laundering Through TransactionThis slide illustrates mitigating transaction risks through policies and procedures. It provides information about due diligence, transaction monitoring, screening, customer identification, data analysis, investigation, review, etc.Introducing Mitigating Transaction Risks Through Policies And Preventing Money Laundering Through Transaction to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Transaction Monitoring, Ongoing Due Diligence, Customer Identification, using this template. Grab it now to reap its full benefits.
-
 Prevention Mitigation Measures In Powerpoint And Google Slides Cpb
Prevention Mitigation Measures In Powerpoint And Google Slides CpbPresenting Prevention Mitigation Measures In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Prevention Mitigation Measures. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Prevention and mitigation risk assessments financial impact analysis ppt powerpoint presentation
Prevention and mitigation risk assessments financial impact analysis ppt powerpoint presentationPresenting this set of slides with name Prevention And Mitigation Risk Assessments Financial Impact Analysis Ppt Powerpoint Presentation. This is a five stage process. The stages in this process are Hazard Identification, Risk Assessments, Operational Impact Analysis, Financial Impact Analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Prevention and mitigation operational impact analysis ppt powerpoint presentation icon example
Prevention and mitigation operational impact analysis ppt powerpoint presentation icon examplePresenting this set of slides with name Prevention And Mitigation Operational Impact Analysis Ppt Powerpoint Presentation Icon Example. This is a five stage process. The stages in this process are Risk Assessments, Financial, Impact, Analysis, Operational. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Prevention and mitigation financial impact analysis ppt powerpoint presentation infographics vector
Prevention and mitigation financial impact analysis ppt powerpoint presentation infographics vectorPresenting this set of slides with name Prevention And Mitigation Financial Impact Analysis Ppt Powerpoint Presentation Infographics Vector. This is a five stage process. The stages in this process are Risk, Assessments, Financial, Impact, Analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Prevention and mitigation risk assessments ppt powerpoint presentation file objects
Prevention and mitigation risk assessments ppt powerpoint presentation file objectsPresenting this set of slides with name Prevention And Mitigation Risk Assessments Ppt Powerpoint Presentation File Objects. This is a five process. The stages in this process are stages Our Team, Communication, Management, Planning, Business. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Social Engineering Methods And Mitigation Methods To Prevent Reverse Social Engineering Attacks
Social Engineering Methods And Mitigation Methods To Prevent Reverse Social Engineering AttacksThis slide outlines the strategies to avoid reverse social engineering scams. The methods discussed in this slide are identify technical support specialists, use separate internal identifiers, provide regular security awareness training to employees, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Methods To Prevent Reverse Social Engineering Attacks. This template helps you present information on three stages. You can also present information on Identify Technical Support Specialists, Use Separate Internal Identifiers, Provide Regular Security Awareness Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Methods And Mitigation Prevention Strategies To Safeguard Against Impersonation
Social Engineering Methods And Mitigation Prevention Strategies To Safeguard Against ImpersonationThis slide represents the effective strategies to stay safe from impersonation attacks. These are custom email domains, email security and solutions software, AI-driven and automated software, implementing dual-control transactions and taking false domains. Introducing Social Engineering Methods And Mitigation Prevention Strategies To Safeguard Against Impersonation to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Custom Email Domains, Taking Down False Domains, Dual Control Transactions, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Methods And Mitigation Preventive Measures For Man In The Middle Cyber Attacks
Social Engineering Methods And Mitigation Preventive Measures For Man In The Middle Cyber AttacksThis slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Preventive Measures For Man In The Middle Cyber Attacks. This template helps you present information on four stages. You can also present information on Secure Connections, Avoid Phishing Emails, Endpoint Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Methods And Mitigation Preventive Measures To Avoid Watering Hole Phishing
Social Engineering Methods And Mitigation Preventive Measures To Avoid Watering Hole PhishingThis slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc. Introducing Social Engineering Methods And Mitigation Preventive Measures To Avoid Watering Hole Phishing to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability Scanning, Security Patches, Input Vulnerability, Bug Bounty Programs, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Methods And Mitigation Preventive Strategies For Baiting Cyber Attacks
Social Engineering Methods And Mitigation Preventive Strategies For Baiting Cyber AttacksThis slide outlines the methods to prevent baiting attacks. These are employee training, dont follow links blindly, use anti-virus and anti-malware software, avoid use of external devices without scanning and hold organized simulated attacks. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Preventive Strategies For Baiting Cyber Attacks. Dispense information and present a thorough explanation of Vulnerability Scanning, Security Patches, Input Vulnerability, Bug Bounty Programs using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation Roadmap To Implement Social Engineering Prevention Strategies
Social Engineering Methods And Mitigation Roadmap To Implement Social Engineering Prevention StrategiesThis slide represents the roadmap to prevent social engineering attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Introducing Social Engineering Methods And Mitigation Roadmap To Implement Social Engineering Prevention Strategies to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Employee Training, Implement Technical Controls, Social Engineering Prevention Strategies, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Methods And Mitigation Timeline To Implement Social Engineering Prevention Strategies
Social Engineering Methods And Mitigation Timeline To Implement Social Engineering Prevention StrategiesThis slide shows the timeline to protect organizations from social engineering attacks. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Introducing Social Engineering Methods And Mitigation Timeline To Implement Social Engineering Prevention Strategies to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Employee Training, Implement Technical Controls, Establish Policies And Procedures, Timely Evaluation And Updates, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Methods And Mitigation Tools And Best Practices For Scareware Prevention
Social Engineering Methods And Mitigation Tools And Best Practices For Scareware PreventionThe purpose of this slide is to outline the tools and best practice to avoid scareware attacks. The major components discussed in this slide are anti-malware tools, network security tools, cybersecurity awareness training, software updates and patches, etc. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation Tools And Best Practices For Scareware Prevention. Use it as a tool for discussion and navigation on Anti Malware Tools, Network Security Tools, Software Updates And Patches, Cybersecurity Awareness Training. This template is free to edit as deemed fit for your organization. Therefore download it now.



