Powerpoint Templates and Google slides for OT Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 OT Cyber Security Powerpoint Ppt Template Bundles
OT Cyber Security Powerpoint Ppt Template BundlesDeliver a lucid presentation by utilizing this OT Cyber Security Powerpoint Ppt Template Bundles. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Industrial Control System ICS Security, Operational Technology Security, SCADA Supervisory Control And Data Acquisition Security, Critical Infrastructure Protection, Industrial Cybersecurity. All the Twenty Two slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 Dashboard To Monitor OT Cyber Security Parameters
Dashboard To Monitor OT Cyber Security ParametersThis slide represents dashboard that assist companies to trach and monitor their OT cyber security for enhancing data protection. It includes various OT cyber security indicators such as intrusion detection system alert, prohibited traffic allowed, etc. Introducing our Dashboard To Monitor OT Cyber Security Parameters set of slides. The topics discussed in these slides are Restricted Traffic, Over Time By DestinationThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Global Market Size Of OT Cyber Security Solutions
Global Market Size Of OT Cyber Security SolutionsThis slide graphically represents global market size of operating technology OT security solutions to protect them from multiple cyber-risks. It includes various key drivers such as increasing cyber threats, enhancing remote work culture, etc. Presenting our well structured Global Market Size Of OT Cyber Security Solutions The topics discussed in this slide are Cloud Adoption, Global OT Security, Solution Market ValueThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Ai Technology Implementation Icon For Robust OT Cyber Security
Ai Technology Implementation Icon For Robust OT Cyber SecurityPresenting our set of slides with Ai Technology Implementation Icon For Robust OT Cyber Security This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on AI Technology Implementation Icon, Robust OT Cyber Security
-
 Approaches For IT And OT Cyber Security Convergence
Approaches For IT And OT Cyber Security ConvergenceIntroducing our premium set of slides with Approaches For IT And OT Cyber Security Convergence Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Understand Unique Needs, Select Right Technology Blend, Team Collaboration So download instantly and tailor it with your information.
-
 Best Practices To Enhance OT Cyber Security
Best Practices To Enhance OT Cyber SecurityThis slide represents various best practices that assist companies to enhance their cybersecurity of operational technology OT assets from cyber-risks. It includes best practices such as identifying OT assets, updating software, etc. Presenting our set of slides with Best Practices To Enhance OT Cyber Security This exhibits information on Two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify And Prioritize OT Assets, Update And Patch Software
-
 Checklist To Enhance OT Security From Cyber Risks
Checklist To Enhance OT Security From Cyber RisksThis slide represents checklist that assist companies to optimize their OT security against multiple cyber threats efficiently. It includes various steps such as separate IT and OT assets, Restrict industrial security, document all communication, etc. Introducing our Checklist To Enhance OT Security From Cyber Risks set of slides. The topics discussed in these slides are Checklist, Status, PhaseThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis Of OT Cyber Security Solutions
Comparative Analysis Of OT Cyber Security SolutionsThis slide represents comparative analysis of various OT security tools assisting companies to enhance their data protection against multiple cyber risks. It includes various tools such as Nozomi networks, Claroty, mission secure, etc. Presenting our well structured Comparative Analysis Of OT Cyber Security Solutions The topics discussed in this slide are Network Visualization, Vulnerability Assessment, Risk MonitoringThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Four Step Approach To Select OT Cyber Security Vendor
Four Step Approach To Select OT Cyber Security VendorThis slide focuses on four-step approach that assists IT companies in selecting right vendor to enhance their OT cyber security according to NIST and ICS framework. It includes various steps such as access engineering involvement, framework pillar prioritization, etc. Introducing our premium set of slides with Four Step Approach To Select OT Cyber Security Vendor Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Engineering Involvement, Framework Pillar Prioritization So download instantly and tailor it with your information.
-
 Integrating Artificial Intelligence For Optimizing OT Cyber Security
Integrating Artificial Intelligence For Optimizing OT Cyber SecurityThis slide represents various applications of artificial intelligence that assist companies to enhance their OT cyber security and protect from potential cyber threats. It includes various applications such as rapid analysis, task prioritization, etc. Introducing our premium set of slides with Integrating Artificial Intelligence For Optimizing OT Cyber Security Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Threat Detection Capabilities, Routine Task Automation So download instantly and tailor it with your information.
-
 Key Pillars Of Robust OT Cyber Security
Key Pillars Of Robust OT Cyber SecurityThis slide represents key pillars that assist companies to implement robust OT cyber security strategies to enhance infrastructure protection. It includes various pillars such as business continuity, strategy, resiliency, finance, and culture. Presenting our set of slides with Key Pillars Of Robust OT Cyber Security This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Business Continuity, Strategy, Resiliency
-
 Maturity Model To Monitor OT Cyber Security Adoption
Maturity Model To Monitor OT Cyber Security AdoptionThis slide represents maturity model that assist companies to monitor and track cyber security adoption for enhancing OT protection. It includes various phases such as secure, defend, contain, monitor and manage phase. Presenting our well structured Maturity Model To Monitor OT Cyber Security Adoption The topics discussed in this slide are Secure, Defend, Contain, MonitorThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Mitigating Challenges Of Cyber Security On OT Network
Mitigating Challenges Of Cyber Security On OT NetworkThis slide represents various strategies that assist companies to mitigate various cyber security challenges on operational technology network effectively. It includes various challenges such as cloud and internet, IoT bots, DDoS attacks, etc. Introducing our premium set of slides with Mitigating Challenges Of Cyber Security On OT Network Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud And Internet, Ddos Attacks, Human Error And BYOD So download instantly and tailor it with your information.
-
 OT Cyber Security Icon To Prevent Unauthorized Access
OT Cyber Security Icon To Prevent Unauthorized AccessIntroducing our premium set of slides with OT Cyber Security Icon To Prevent Unauthorized Access Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like OT Cyber Security Icon To Prevent, Unauthorized Access So download instantly and tailor it with your information.
-
 OT Cyber Security Training Schedule For It Employees
OT Cyber Security Training Schedule For It EmployeesThis slide represents training plan that assist companies to educate their IT employee for enhancing operational technology cyber security effectively. It includes various elements such as course, details, timings, modules, mode, etc. Introducing our OT Cyber Security Training Schedule For It Employees set of slides. The topics discussed in these slides are Details, Timings, ModulesThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 OT Security Icon For Cyber Threat Protection
OT Security Icon For Cyber Threat ProtectionIntroducing our premium set of slides with OT Security Icon For Cyber Threat Protection Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like OT Security Icon, Cyber Threat Protection So download instantly and tailor it with your information.
-
 Roadmap To Implement Robust OT Cyber Security
Roadmap To Implement Robust OT Cyber SecurityThis slide represents roadmap that guides companies to implement strong operational technology cybersecurity model for enhancing information protection. It includes various steps such as conducting OT threat assessment, know network and assets, etc. Presenting our set of slides with Roadmap To Implement Robust OT Cyber Security This exhibits information on Seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Conduct OT Threat Assessment, Know Network And Assets, Publish OT Security Policy
-
 Strategies To Optimize OT Cyber Security
Strategies To Optimize OT Cyber SecurityThis slide represents various strategies that assist companies to enhance their OT cyber security with ICS products effectively. It includes various strategies such as host security, security monitoring, physical security, etc. Introducing our premium set of slides with Strategies To Optimize OT Cyber Security Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Host Security, Physical Security, Security Monitoring So download instantly and tailor it with your information.
-
 F516 It Ot Convergence Security Objectives Challenges Managing The Successful Convergence Of It And Ot
F516 It Ot Convergence Security Objectives Challenges Managing The Successful Convergence Of It And OtThis slide covers objectives challenges catalysts and benefits of the Security in IT or OT convergence and Reduce systems cyberattack surface Increase audience engagement and knowledge by dispensing information using F516 It Ot Convergence Security Objectives Challenges Managing The Successful Convergence Of It And Ot. This template helps you present information on four stages. You can also present information on Objectives, Resources, Convergence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 It Ot Convergence Strategy Security Objectives Challenges Catalysts And Benefits
It Ot Convergence Strategy Security Objectives Challenges Catalysts And BenefitsThis slide covers objectives challenges catalysts and benefits of the Security in IT or OT convergence and Reduce systems cyberattack surface Present the topic in a bit more detail with this It Ot Convergence Strategy Security Objectives Challenges Catalysts And Benefits. Use it as a tool for discussion and navigation on Objectives, Catalysts Resources, Challenges. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It Ot Convergence Strategy Two Way Interactions Between Safety Security And Cybersecurity
It Ot Convergence Strategy Two Way Interactions Between Safety Security And CybersecurityThis slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. IT or OT industrial cyber security deployment Present the topic in a bit more detail with this It Ot Convergence Strategy Two Way Interactions Between Safety Security And Cybersecurity. Use it as a tool for discussion and navigation on Interactions, Security, Cybersecurity This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Smart Enterprise Digitalization IT OT Convergence Security Objectives Challenges Catalysts
Smart Enterprise Digitalization IT OT Convergence Security Objectives Challenges CatalystsThis slide covers objectives challenges catalysts and benefits of the Security in IT or OT convergence and Reduce systems cyberattack surface. Increase audience engagement and knowledge by dispensing information using Smart Enterprise Digitalization IT OT Convergence Security Objectives Challenges Catalysts. This template helps you present information on four stages. You can also present information on Objectives, Catalysts, Resources, Challenges, Benefits using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
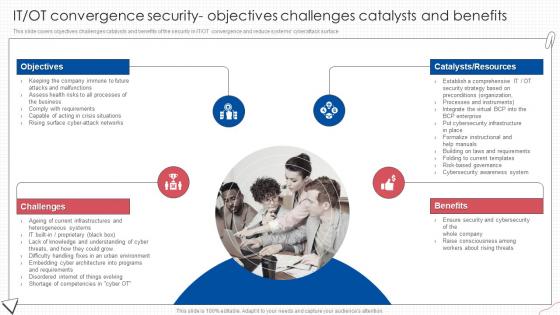 IT OT Convergence Security Objectives Digital Transformation Of Operational Industries
IT OT Convergence Security Objectives Digital Transformation Of Operational IndustriesThis slide covers objectives challenges catalysts and benefits of the security in IT OT convergence and reduce systems cyberattack surface.Introducing IT OT Convergence Security Objectives Digital Transformation Of Operational Industries to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Benefits, Consciousness Among, using this template. Grab it now to reap its full benefits.
-
 F542 It Ot Convergence Security Objectives Challenges Catalysts And Strategies Ot And It Modern Pi System
F542 It Ot Convergence Security Objectives Challenges Catalysts And Strategies Ot And It Modern Pi SystemThis slide covers objectives challenges catalysts and benefits of the Security in IT or OT convergence and Reduce systems cyberattack surface Increase audience engagement and knowledge by dispensing information using F542 It Ot Convergence Security Objectives Challenges Catalysts And Strategies Ot And It Modern Pi System. This template helps you present information on four stages. You can also present information on Resources, Requirements, Heterogeneous using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
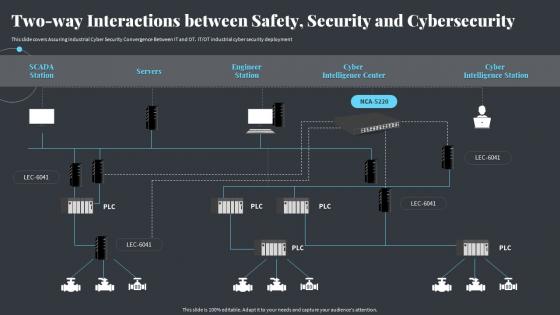 Two Way Interactions Between Safety Security And Cybersecurity Strategies Ot And It Modern Pi System
Two Way Interactions Between Safety Security And Cybersecurity Strategies Ot And It Modern Pi SystemThis slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. IT or OT industrial cyber security deployment Deliver an outstanding presentation on the topic using this Two Way Interactions Between Safety Security And Cybersecurity Strategies Ot And It Modern Pi System. Dispense information and present a thorough explanation of Cybersecurity, Interactions, Intelligence Station using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 OT Cyber Security Strategy Maturity Model
OT Cyber Security Strategy Maturity ModelThis slide represents OT cyber security strategy maturity model illustrating networking, human resource, processes, security management technology, security technology etc. Introducing our OT Cyber Security Strategy Maturity Model set of slides. The topics discussed in these slides are Security, Defense, Contain, Monitor. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 OT Cyber Security Icon To Mitigate Data Breach Threats
OT Cyber Security Icon To Mitigate Data Breach ThreatsPresenting our set of slides with OT Cyber Security Icon To Mitigate Data Breach Threats This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on OT Cyber Security Icon To Mitigate, Data Breach Threats



