Powerpoint Templates and Google slides for Optimizing Cybersecurity
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Blockchain And Cybersecurity Ways To Minimize 51 Percent Attacks And Optimize Hash Rate BCT SS V
Blockchain And Cybersecurity Ways To Minimize 51 Percent Attacks And Optimize Hash Rate BCT SS VThe following slide illustrates various methods to reduce the impact of 51percent attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc. Introducing Blockchain And Cybersecurity Ways To Minimize 51 Percent Attacks And Optimize Hash Rate BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Single User, Constant Updates, Network System using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Incident Response Plan Architecture For Optimizing BCP
Cybersecurity Incident Response Plan Architecture For Optimizing BCPThis slide represents architecture that assists businesses in implementing cybersecurity incident response plans to optimize business continuity planning BCP. It includes various elements such as incident detection, incident response, cyber resiliency, etc. Introducing our Cybersecurity Incident Response Plan Architecture For Optimizing BCP set of slides. The topics discussed in these slides are Cyber Resiliency, Incident Detection, System Restored This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
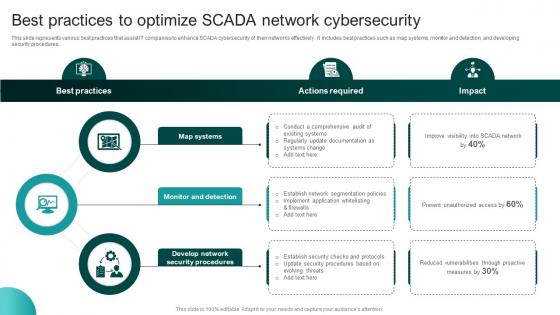 Best Practices To Optimize SCADA Network Cybersecurity
Best Practices To Optimize SCADA Network CybersecurityThis slide represents various best practices that assist IT companies to enhance SCADA cybersecurity of their networks effectively. It includes best practices such as map systems, monitor and detection, and developing security procedures. Presenting our set of slides with Best Practices To Optimize SCADA Network Cybersecurity This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Procedures, Monitor And Detection, Map Systems
-
 Focus Areas To Optimize Cybersecurity Of SCADA Networks
Focus Areas To Optimize Cybersecurity Of SCADA NetworksThis slide represents various focus areas that assist IT companies to enhance their SCADA network cybersecurity and improve information protection. It includes various areas such as network connection, software security, etc. Presenting our well structured Focus Areas To Optimize Cybersecurity Of SCADA Networks The topics discussed in this slide are Network Connections, Security Measure, Area Of Focus. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Icon For Ethical Standards To Optimize Business Cybersecurity
Icon For Ethical Standards To Optimize Business CybersecurityIntroducing our premium set of slides with Icon For Ethical Standards To Optimize Business Cybersecurity. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon, Ethical Standards, Optimize Business Cybersecurity. So download instantly and tailor it with your information.
-
 Case Study For Implementing Optimized OT Cybersecurity Strategy
Case Study For Implementing Optimized OT Cybersecurity StrategyThis slide represents case study for implementing effective OT cybersecurity approach to mitigate cyber threats and enhance infrastructure protection. It includes various elements such as overview, challenges, solutions, and benefits. Presenting our set of slides with Case Study For Implementing Optimized OT Cybersecurity Strategy This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Overview, Challenges, Solution, Benefits
-
 Addressing Challenges For Implementing Pam To Optimize Cybersecurity
Addressing Challenges For Implementing Pam To Optimize CybersecurityThis slide represents various strategies that assist companies in mitigating challenges in implementing and monitoring PAM for enhancing cybersecurity. It includes challenges such as managing account credentials, tracking privileged activity, etc. Introducing our Addressing Challenges For Implementing Pam To Optimize Cybersecurity set of slides. The topics discussed in these slides are Managing Account Credentials, Tracking Privileged Activity, Controlling Privileged User Access. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ai Driven Pam Architecture To Optimizing Cybersecurity
Ai Driven Pam Architecture To Optimizing CybersecurityThis slide represents AI-driven PAM architecture that assists companies in enhancing their cybersecurity from data threats. It includes various components such as cloud computing, PAM-SOAR, IAM governance, AI, ML, etc. Presenting our well structured Ai Driven Pam Architecture To Optimizing Cybersecurity. The topics discussed in this slide are Optimizing, Cybersecurity, Architecture. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparison Analysis Of Pam Software For Optimizing Cybersecurity
Comparison Analysis Of Pam Software For Optimizing CybersecurityThis slide represents comparative analysis of PAM software that assists companies in selecting best solution for their cybersecurity and data protection. It includes various software such as Microsoft Entra ID, JumpCloud, Ermetic, etc. Introducing our Comparison Analysis Of Pam Software For Optimizing Cybersecurity set of slides. The topics discussed in these slides are Comparison, Analysis, Cybersecurity. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Pam Implementation Icon To Optimize Data Cybersecurity
Pam Implementation Icon To Optimize Data CybersecurityIntroducing our premium set of slides with Pam Implementation Icon To Optimize Data Cybersecurity. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like PAM Implementation, Optimize, Data Cybersecurity. So download instantly and tailor it with your information.
-
 Cybersecurity Optimization Meeting Summary Icon
Cybersecurity Optimization Meeting Summary IconIntroducing our premium set of slides with Cybersecurity Optimization Meeting Summary Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cybersecurity Optimization, Meeting Summary, Icon. So download instantly and tailor it with your information.
-
 Mdr Framework To Optimize Business Cybersecurity
Mdr Framework To Optimize Business CybersecurityThis slide represents framework that assists IT companies in understanding workflow of MDR solutions to enhance their data cybersecurity and risk management. It includes various components such as data lake, SIEM, SOAR, playbooks, ITSM, etc. Presenting our well structured Mdr Framework To Optimize Business Cybersecurity. The topics discussed in this slide are Business, Cybersecurity, Framework. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Trends In Mdr Cybersecurity For Optimizing Threat Intelligence
Trends In Mdr Cybersecurity For Optimizing Threat IntelligenceThis slide represents various trends in MDR cybersecurity that assist companies to enhance their data protection against online threats. It includes trends such as Multi-cloud MDR, Digital risk protection services, and API security monitoring. Introducing our Trends In Mdr Cybersecurity For Optimizing Threat Intelligence set of slides. The topics discussed in these slides are Intelligence, Cybersecurity, Digital Risk Protection Services. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Approaches To Overcome Cybersecurity Risk Faced By Real Estate Optimizing Process Improvement
Approaches To Overcome Cybersecurity Risk Faced By Real Estate Optimizing Process ImprovementThe following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add ons, using a customized web application firewall etc. Present the topic in a bit more detail with this Approaches To Overcome Cybersecurity Risk Faced By Real Estate Optimizing Process Improvement. Use it as a tool for discussion and navigation on Ransomware, Phishing, Business Email Compromise. This template is free to edit as deemed fit for your organization. Therefore download it now
-
 Process optimization cybersecurity strategy insider threat statistics fundraising cpb
Process optimization cybersecurity strategy insider threat statistics fundraising cpbPresenting this set of slides with name - Process Optimization Cybersecurity Strategy Insider Threat Statistics Fundraising Cpb. This is an editable seven stages graphic that deals with topics like Process Optimization, Cybersecurity Strategy, Insider Threat Statistics, Fundraising to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Optimizing cybersecurity framework roadmap security program ppt design ideas
Optimizing cybersecurity framework roadmap security program ppt design ideasThis slide portrays information regarding optimization of current cybersecurity framework. The IT department will require to fulfill crucial activities in specific timeframe. Presenting this set of slides with name Optimizing Cybersecurity Framework Roadmap Security Program Ppt Design Ideas. The topics discussed in these slides are Optimizing Cybersecurity, Framework Roadmap, Security Program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Optimizing cybersecurity framework roadmap program ppt gallery visual aids
Optimizing cybersecurity framework roadmap program ppt gallery visual aidsThis slide portrays information regarding optimization of current cybersecurity framework. The IT department will require to fulfill crucial activities in specific timeframe. Presenting this set of slides with name Optimizing Cybersecurity Framework Roadmap Program Ppt Gallery Visual Aids. This is a three stage process. The stages in this process are Implement Enterprise Security Program, Implement Control Environment, Implement Security Processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Optimizing cybersecurity framework roadmap logging monitoring ppt gallery
Optimizing cybersecurity framework roadmap logging monitoring ppt galleryThis slide portrays information regarding optimization of current cybersecurity framework. The IT department will require to fulfill crucial activities in specific timeframe. Presenting this set of slides with name Optimizing Cybersecurity Framework Roadmap Logging Monitoring Ppt Gallery. The topics discussed in these slides are Optimizing Cybersecurity, Framework Roadmap, Logging Monitoring. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.



