Powerpoint Templates and Google slides for Operational Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 It security operations powerpoint presentation slides
It security operations powerpoint presentation slidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this IT Security Operations Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the fifty nine slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Security operation centre powerpoint presentation slides
Security operation centre powerpoint presentation slidesPresenting our illustrative security operation center PowerPoint template. This PPT presentation is available for download in both standard and widescreen formats. You can easily edit the content inside the PPT design. It is compatible with all prominent presentation software, including Microsoft Office and Google Slides, among others. This PPT slide can also be edited for print and digital formats such as JPEG, PNG, and PDF.
-
 Enterprise security operations powerpoint presentation slides
Enterprise security operations powerpoint presentation slidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Enterprise Security Operations Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the fifty five slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Facilitating it security and operations powerpoint presentation slides
Facilitating it security and operations powerpoint presentation slidesPresenting our illustrative facilitating IT security and operations PowerPoint template. This PPT presentation is available for download in both standard and widescreen formats. You can easily edit the content inside the PPT design. It is compatible with all prominent presentation software, including Microsoft Office and Google Slides, among others. This PPT slide can also be edited for print and digital formats such as JPEG, PNG, and PDF.
-
 Security and operations integration powerpoint presentation slides
Security and operations integration powerpoint presentation slidesPresenting our security and operations integration PowerPoint presentation slides. This PowerPoint design contains fifty-three slides in it which can be completely customized and edited. It is available for both standard as well as for widescreen formats. This PowerPoint template is compatible with all the presentation software like Microsoft Office, Google Slides, etc. You can download this PPT layout from below.
-
 Enabling Automation In Cyber Security Operations Powerpoint Presentation Slides
Enabling Automation In Cyber Security Operations Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Enabling Automation In Cyber Security Operations Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fourty two slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Operational Security A Cybersecurity Component Training Ppt
Operational Security A Cybersecurity Component Training PptPresenting Operational Security a Cybersecurity Component. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content and present it with confidence.
-
 Security Operations Center Powerpoint Ppt Template Bundles
Security Operations Center Powerpoint Ppt Template BundlesDeliver a credible and compelling presentation by deploying this Security Operations Center Powerpoint Ppt Template Bundles. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twenty three slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Security Operations Center Powerpoint Ppt Template Bundles PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Enterprise Security Operation Powerpoint Ppt Template Bundles
Enterprise Security Operation Powerpoint Ppt Template BundlesDeliver a credible and compelling presentation by deploying this Enterprise Security Operation Powerpoint Ppt Template Bundles. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twenty four slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Enterprise Security Operation Powerpoint Ppt Template Bundles PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Overview Of Importance Of Operational Security Training Ppt
Overview Of Importance Of Operational Security Training PptPresenting Overview of Importance of Operational Security. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Five Steps To Create An Operational Security Plan Training Ppt
Five Steps To Create An Operational Security Plan Training PptPresenting Five Steps to Create an Operational Security Plan. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
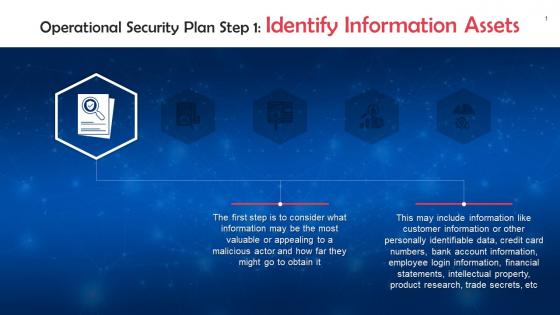 Identifying Information Assets For Operational Security Training Ppt
Identifying Information Assets For Operational Security Training PptPresenting Identifying Information Assets for Operational Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Identifying Threats For Operational Security Training Ppt
Identifying Threats For Operational Security Training PptPresenting Identifying Threats for Operational Security. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Identifying Vulnerabilities For Operational Security Training Ppt
Identifying Vulnerabilities For Operational Security Training PptPresenting Identifying Vulnerabilities for Operational Security. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 General Analysis For Operational Security Training Ppt
General Analysis For Operational Security Training PptPresenting General Analysis for Operational Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Mitigation As A Part Of An Operational Security Plan Training Ppt
Mitigation As A Part Of An Operational Security Plan Training PptPresenting Mitigation as a Part of an Operational Security Plan. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Best Practices For Operational Security OPSEC Training Ppt
Best Practices For Operational Security OPSEC Training PptPresenting Best Practices for Operational Security OPSEC. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Implementing Identity And Access Management For Operational Security OPSEC Training Ppt
Implementing Identity And Access Management For Operational Security OPSEC Training PptPresenting Implementing Identity and Access Management for Operational Security OPSEC. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Operational Security As A Component Of Cybersecurity Training Ppt
Operational Security As A Component Of Cybersecurity Training PptPresenting Operational Security as a Component of Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Global Security Insurance Company Business Operations Illustrating Features
Global Security Insurance Company Business Operations Illustrating FeaturesDeliver a credible and compelling presentation by deploying this Global Security Insurance Company Business Operations Illustrating Features. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twelve slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Global Security Insurance Company Business Operations Illustrating Features PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
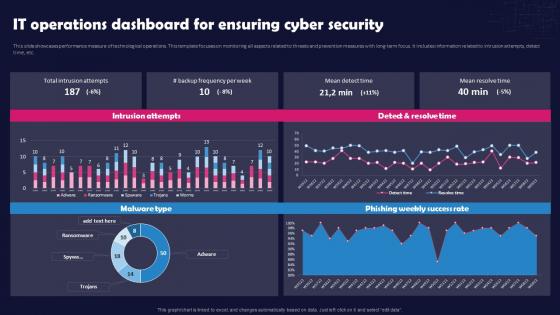 Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber Security
Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber SecurityThis slide showcases performance measure of technological operations. This template focuses on monitoring all aspects related to threats and prevention measures with long-term focus. It includes information related to intrusion attempts, detect time, etc. Present the topic in a bit more detail with this Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber Security. Use it as a tool for discussion and navigation on IT Operations Dashboard, Ensuring Cyber Security, Threats And Prevention, Technological Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Key KPMG Cyber Security KPMG Operational And Marketing Strategy SS V
Overview Of Key KPMG Cyber Security KPMG Operational And Marketing Strategy SS VThis slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights Increase audience engagement and knowledge by dispensing information using Overview Of Key KPMG Cyber Security KPMG Operational And Marketing Strategy SS V. This template helps you present information on five stages. You can also present information on Digital, Security, Automation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mobile Security Dashboard To Monitor Operating Systems
Mobile Security Dashboard To Monitor Operating SystemsThis slide illustrates KPI or Dashboard of mobile security to assess different operating systems and includes iOS, android, other and assigned devices, etc. Introducing our Mobile Security Dashboard To Monitor Operating Systems set of slides. The topics discussed in these slides are Ios Devices, Assigned Devices, Firmware Distribution Ios, Android Devices, Other Devices, Firmware Distribution Android. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Global Security Operation Center Market Size By Region
Global Security Operation Center Market Size By RegionThis slide represents the statistical data for worldwide security operations center market by geographical segmentation that helps to understand the rising potential. It provides insights such as growth factors and market players. Introducing our Global Security Operation Center Market Size By Region set of slides. The topics discussed in these slides are Key Market Players, Growth Factors. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Operation Center Risk Assessment Dashboard
Security Operation Center Risk Assessment DashboardThe following slide illustrates a risk assessment dashboard helps to understand the risk rating breakdown, action plan, top vulnerabilities, etc. of a business. Introducing our Security Operation Center Risk Assessment Dashboard set of slides. The topics discussed in these slides are Risk Assessment Progress, Solved, Action Plan, Risk Rating Breakdown. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ecommerce Fraud Impact On Business Operations Implementing E Commerce Security Measures
Ecommerce Fraud Impact On Business Operations Implementing E Commerce Security MeasuresThis slide represents the impact of fraud attacks on ecommerce companies. It provide information about chargeback fee, high network fee, delayed expansion or investment. Deliver an outstanding presentation on the topic using this Ecommerce Fraud Impact On Business Operations Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Card Payment, Manage Fraud, Businesses Delay Investment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Circle With 4 Quadrants Organization Security Allowance Business Operational Marketing Strategies
Circle With 4 Quadrants Organization Security Allowance Business Operational Marketing StrategiesThis complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of ten slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
-
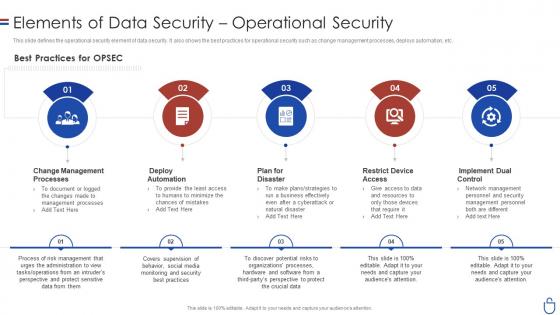 Data security it elements of data security operational security
Data security it elements of data security operational securityThis slide defines the operational security element of data security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Introducing Data Security IT Elements Of Data Security Operational Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Best Practices, OPSEC, Change Management Processes, Deploy Automation, Plan For Disaster, Restrict Device Access, Implement Dual Control, using this template. Grab it now to reap its full benefits.
-
 Data security it main steps of operational security
Data security it main steps of operational securityThis slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Increase audience engagement and knowledge by dispensing information using Data Security IT Main Steps Of Operational Security. This template helps you present information on one stages. You can also present information on Financial Details, Product Research, Exploit Data, Plan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network security audit remote operations ppt powerpoint presentation outline information cpb
Network security audit remote operations ppt powerpoint presentation outline information cpbPresenting Network Security Audit Remote Operations Ppt Powerpoint Presentation Outline Information Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Network Security Audit Remote Operations. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Elements of computer security operational security computer system security
Elements of computer security operational security computer system securityThis slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Increase audience engagement and knowledge by dispensing information using Elements Of Computer Security Operational Security Computer System Security. This template helps you present information on five stages. You can also present information on Change Management Processes, Deploy Automation, Plan For Disaster, Restrict Device Access, Implement Dual Control using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security main steps of operational security
Computer system security main steps of operational securityThis slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Introducing Computer System Security Main Steps Of Operational Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Assessment Of Risks, Analyze Security Holes And Vulnerabilities, Potential Threats, Sensitive Information, Implementation Of Appropriate Countermeasures, using this template. Grab it now to reap its full benefits.
-
 Icon For Enterprise Security Automation Operation
Icon For Enterprise Security Automation OperationPresenting our set of slides with Icon For Enterprise Security Automation Operation. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Enterprise Security Automation Operation.
-
 Security Automation Metrics For Operational Efficiency
Security Automation Metrics For Operational EfficiencyThis slide displays the security automation metrics for operation efficiency. It includes detailed information on metrics such as the time to remediation, operation performance enhancements, sensor value, workflow effectiveness indicators etc. Presenting our set of slides with Security Automation Metrics For Operational Efficiency. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Sensor Value System Utilization, Workflow Effectiveness.
-
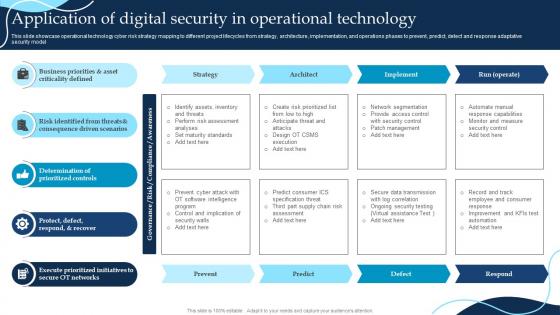 Application Of Digital Security In Operational Technology
Application Of Digital Security In Operational TechnologyThis slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model Presenting our well structured Application Of Digital Security In Operational Technology. The topics discussed in this slide are Digital, Priorities, Scenarios. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Role Of ZTNA To Improve Business Operations And Security Zero Trust Security Model
Role Of ZTNA To Improve Business Operations And Security Zero Trust Security ModelThis slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Deliver an outstanding presentation on the topic using this Role Of ZTNA To Improve Business Operations And Security Zero Trust Security Model. Dispense information and present a thorough explanation of Enhanced User Experience, Remote Workforce Protection, Improve Data Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Zero Trust Security Model
Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Zero Trust Security ModelThis slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Deliver an outstanding presentation on the topic using this Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Zero Trust Security Model. Dispense information and present a thorough explanation of Operational, Implement, Performance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Response Plan Secure Operations Data Breach Prevention And Mitigation
Data Breach Response Plan Secure Operations Data Breach Prevention And MitigationThis slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. Present the topic in a bit more detail with this Data Breach Response Plan Secure Operations Data Breach Prevention And Mitigation. Use it as a tool for discussion and navigation on Assemble Expert Team, Consult With Legal Counsel, Secure Physical Areas. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Operating Maturity Model Levels
Security Operating Maturity Model LevelsThe slide contains security operating maturity levels that assist in providing overall consistency, reliability, and resilience to IT systems at the hands of management, design, etc. The slide has improved visibility, quick identification of threats,and decreased response time. Presenting our set of slides with Security Operating Maturity Model Levels. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Decreased Response, Improvement In Visibility, Quick Identification.
-
 Security Operating Model In Powerpoint And Google Slides Cpb
Security Operating Model In Powerpoint And Google Slides CpbPresenting our Security Operating Model In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Operating Model This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 How Does Secure Blockchain Network Operates Ultimate Guide To Blockchain BCT SS
How Does Secure Blockchain Network Operates Ultimate Guide To Blockchain BCT SSThis slide covers steps to increase operational security of blockchain networks. It includes steps such as requesting transaction by users, creation of block representing the transaction, broadcasting of blocks to network nodes, etc. Introducing How Does Secure Blockchain Network Operates Ultimate Guide To Blockchain BCT SS to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Transaction Requested, Verified Transaction, Network Operates, using this template. Grab it now to reap its full benefits.
-
 Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS V
Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS VThis slide covers checklist for assessing vendor before integrating technology strategy in operations to enhance security. It involves key points such as IT risk assessment, threat and security experts and expertise in developing new technologies. Deliver an outstanding presentation on the topic using this Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS V. Dispense information and present a thorough explanation of Cloud Environments, Risk Arising, Digital Transformation Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Operational Technology Security Controls To Enhance Safety Guide For Integrating Technology Strategy SS V
Operational Technology Security Controls To Enhance Safety Guide For Integrating Technology Strategy SS VThis slide covers operational technology security controls to improve IT safety. It involves five kinds of security controls such as update asset inventory, training, ,manage portable media and secure configuration. Introducing Operational Technology Security Controls To Enhance Safety Guide For Integrating Technology Strategy SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Update Asset Inventory, Portable Media, Backup And Restore, using this template. Grab it now to reap its full benefits.
-
 Case Study 2 Setting Up Cyber Security Infrastructure Strategic Improvement In Banking Operations
Case Study 2 Setting Up Cyber Security Infrastructure Strategic Improvement In Banking OperationsThe purpose of the mentioned slide is to showcase various measures initiated for cyber security protection in banking operations. This slide depicts various challenges faced by the bank along with desired solutions and impact Introducing Case Study 2 Setting Up Cyber Security Infrastructure Strategic Improvement In Banking Operations to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Infrastructure, Desired Solutions, Environment, using this template. Grab it now to reap its full benefits.
-
 Methods To Improve Online Banking Security For Customers Strategic Improvement In Banking Operations
Methods To Improve Online Banking Security For Customers Strategic Improvement In Banking OperationsThe purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc. Increase audience engagement and knowledge by dispensing information using Methods To Improve Online Banking Security For Customers Strategic Improvement In Banking Operations. This template helps you present information on four stages. You can also present information on Strong Authentication, Encryption And Secure Connections, Robust Backend Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Buying Securities Open Market Operations In Powerpoint And Google Slides Cpb
Buying Securities Open Market Operations In Powerpoint And Google Slides CpbPresenting Buying Securities Open Market Operations In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Buying Securities, Open Market, Operations. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Best Tools For Security Operations Secops V2 Ppt Infographic Template Files
Best Tools For Security Operations Secops V2 Ppt Infographic Template FilesThis slide represents the best security operations tools for the year 2023. The purpose of this slide is to showcase the various prominent tools for SecOps, including Grafana, StackStorm, GRR Rapid Response, Chef Inspec, and Alerta. Deliver an outstanding presentation on the topic using this Best Tools For Security Operations Secops V2 Ppt Infographic Template Files. Dispense information and present a thorough explanation of Needs Comprehensive Knowledge, Complex Version Management, Incident Response Framework using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Introduction To Secops V2 Security Operations Solution Ppt Infographics Guide
Introduction To Secops V2 Security Operations Solution Ppt Infographics GuideThis slide outlines the introduction to security operations. The purpose of this slide is to give an overview of SecOps, including its goals, benefits, and critical functions. The functions include security monitoring, threat intelligence, triage and investigation, incident response, and forensics and root cause analysis. Increase audience engagement and knowledge by dispensing information using Introduction To Secops V2 Security Operations Solution Ppt Infographics Guide. This template helps you present information on four stages. You can also present information on Security Operations, Security Monitoring, Threat Intelligence, Triage And Investigation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Methods To Integrate Secops V2 Into Security Operations Soc
Methods To Integrate Secops V2 Into Security Operations SocThis slide represents the ways to implement SecOps into security operations. The purpose of this slide is to highlight the main methods to combine SecOps and SOC and the strategies that cater to distributing security operations, building a security center of excellence, and establishing a culture of collaboration. Introducing Methods To Integrate Secops V2 Into Security Operations Soc to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Build Security Center Of Excellence, Establish Culture Of Collaboration, Security Operations, using this template. Grab it now to reap its full benefits.
-
 Secops V2 Challenges And Solutions Of Security Operations Centres
Secops V2 Challenges And Solutions Of Security Operations CentresThis slide outlines the key challenges and solutions of security operations centers. The purpose of this slide is to highlight the problems faced by SOC teams and methods to overcome those problems. The main challenges include talent gaps, sophisticated attackers, increased data and network traffic, etc. Present the topic in a bit more detail with this Secops V2 Challenges And Solutions Of Security Operations Centres. Use it as a tool for discussion and navigation on Challenges And Solutions, Security Operations Centres, Sophisticated Attackers, Data And Network Traffic. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secops V2 Conceptual Architecture Of Security Operations Center
Secops V2 Conceptual Architecture Of Security Operations CenterThis slide describes the conceptual architecture of the security operations center. The purpose of this slide is to highlight the architecture of SecOps and the elements that formalize the architecture. The main components include network taps, operating systems, apps, security elements, etc. Deliver an outstanding presentation on the topic using this Secops V2 Conceptual Architecture Of Security Operations Center. Dispense information and present a thorough explanation of Conceptual Architecture, Security Operations Center, Network Taps, Operating Systems, Security Elements using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secops V2 Key Outcomes Manage By Security Operations Team
Secops V2 Key Outcomes Manage By Security Operations TeamThis slide outlines the critical outcomes that are handled by the security operations team. The purpose of this slide is to demonstrate the various key outcomes, their activities, responsible person and remarks. The main outcomes include incident management, incident preparation and threat intelligence. Deliver an outstanding presentation on the topic using this Secops V2 Key Outcomes Manage By Security Operations Team. Dispense information and present a thorough explanation of Incident Management, Incident Preparation, Threat Intelligence, Security Leadership using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secops V2 Key Responsibilities Of Command Security Operations Center
Secops V2 Key Responsibilities Of Command Security Operations CenterThis slide depicts the main tasks of the command security operations center. The purpose of this slide is to highlight the main responsibilities, responsible team members, and task status. The main tasks include monitoring and analyzing security events, coordinating incident response, managing security operations, etc. Present the topic in a bit more detail with this Secops V2 Key Responsibilities Of Command Security Operations Center. Use it as a tool for discussion and navigation on Monitoring And Analysing Security Events, Coordinating Incident Response, Regulatory Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secops V2 Main Responsibilities Of Security Operations Center Soc
Secops V2 Main Responsibilities Of Security Operations Center SocThis slide describes the different responsibilities of a secure operations center. The purpose of this slide is to showcase the multiple functions SOC teams perform, including communication with DevOps teams, coordinating incident response process, incident investigation, and prioritization of threats. Introducing Secops V2 Main Responsibilities Of Security Operations Center Soc to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Coordinating Incident Response Process, Incident Investigation, Prioritization, using this template. Grab it now to reap its full benefits.
-
 Secops V2 Roles And Responsibilities Of Security Operations Center Team
Secops V2 Roles And Responsibilities Of Security Operations Center TeamThis slide outlines the roles and responsibilities of the security operations center team. The purpose of this slide is to showcase the roles as well as duties of the SOC team. The prominent roles include incident responder, security investigator, advanced security analyst, SOC manager, and security engineer. Introducing Secops V2 Roles And Responsibilities Of Security Operations Center Team to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Incident Responder, Security Investigator, Advanced Security Analyst, Security Engineer Or Architect, using this template. Grab it now to reap its full benefits.
-
 Secops V2 Security Operations Center Teams Structure Ppt Infographics Themes
Secops V2 Security Operations Center Teams Structure Ppt Infographics ThemesThis slide describes the team structure of the security operations center. The purpose of this slide is to showcase the team hierarchy of SOC and it includes teams, their tasks and the name of the team members. The primary units include triage, investigation, and hunters. Deliver an outstanding presentation on the topic using this Secops V2 Security Operations Center Teams Structure Ppt Infographics Themes. Dispense information and present a thorough explanation of Security Operations Center, Teams Structure, Investigation And Hunters, Forensics Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
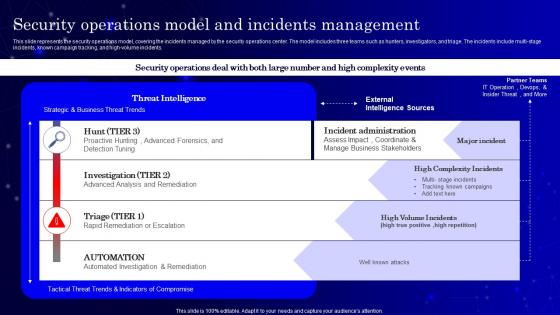 Secops V2 Security Operations Model And Incidents Management
Secops V2 Security Operations Model And Incidents ManagementThis slide represents the security operations model, covering the incidents managed by the security operations center. The model includes three teams such as hunters, investigators, and triage. The incidents include multi-stage incidents, known campaign tracking, and high-volume incidents. Present the topic in a bit more detail with this Secops V2 Security Operations Model And Incidents Management. Use it as a tool for discussion and navigation on Security Operations Model, Incidents Management, Known Campaign Tracking, Rapid Remediation Or Escalation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secops V2 Security Operations Modernization Driving Trends
Secops V2 Security Operations Modernization Driving TrendsThis slide outlines the driving trends for security operations modernization. The purpose of this slide is to highlight the leading trends that drive the modernization of security operations centers. The main drivers include cloud platform coverage, a shift to identify-centric security, IoT and OT coverage, etc. Introducing Secops V2 Security Operations Modernization Driving Trends to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Platform Coverage, Cloud Processing Of Telemetry, Operational Technology Coverage, using this template. Grab it now to reap its full benefits.
-
 Secops V2 Security Operations Threat Management Process
Secops V2 Security Operations Threat Management ProcessThis slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. Deliver an outstanding presentation on the topic using this Secops V2 Security Operations Threat Management Process. Dispense information and present a thorough explanation of Extended Investigation, Preliminary Investigation, Security Operations Threat
-
 Secops V2 Skills Required For Security Operations Teams Ppt Infographics Tips
Secops V2 Skills Required For Security Operations Teams Ppt Infographics TipsThis slide talks about the skills required for security operation teams. The purpose of this slide is to showcase the various skills that can help SecOps to secure an organization completely. The primary skills include no-code automation, communicating modern threats from first principles, peer influence, and so on. Present the topic in a bit more detail with this Secops V2 Skills Required For Security Operations Teams Ppt Infographics Tips. Use it as a tool for discussion and navigation on Security Operations Teams, Peer Influence, Communicating Business Value, Organizational Security. This template is free to edit as deemed fit for your organization. Therefore download it now.




