Powerpoint Templates and Google slides for Networking Mode
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Social Networking Service Business Model Powerpoint Ppt Template Bundles BMC V
Social Networking Service Business Model Powerpoint Ppt Template Bundles BMC VIn the world of cutthroat competition, one can always sustain and excel with the right tools at hand. One such right tool is our insightfully crafted Social Networking Service Business Model Powerpoint Ppt Template Bundles BMC V PowerPoint Document. This document is made to cater to all your concerns, and offer you a deeper understanding of the Business Model, and how to take it forward. Developed lucidly, our Deck caters to all the questions and offers insights with a sector-oriented approach. Showcasing the utmost precision our PPT includes the five-year projections, and covers important details including valuations, break-even analysis, financial statements, and Pay Back Period. It also works well with Google Slides and presents high resolution graphics that can be useful for projection to a wider audience. Having our assistance at bay, this fully editable highly customizable Document will save you time and energy, and get you a sure-shot result.
-
 Job Networking Site Business Model Powerpoint Ppt Template Bundles BMC V
Job Networking Site Business Model Powerpoint Ppt Template Bundles BMC VIf you require a professional template with great design, then this Job Networking Site Business Model Powerpoint Ppt Template Bundles BMC V is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twenty four slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Professional Networking Platform Business Model Powerpoint PPT Template Bundles BMC V
Professional Networking Platform Business Model Powerpoint PPT Template Bundles BMC VIf you require a professional template with great design, then this Professional Networking Platform Business Model Powerpoint PPT Template Bundles BMC V is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twenty four slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
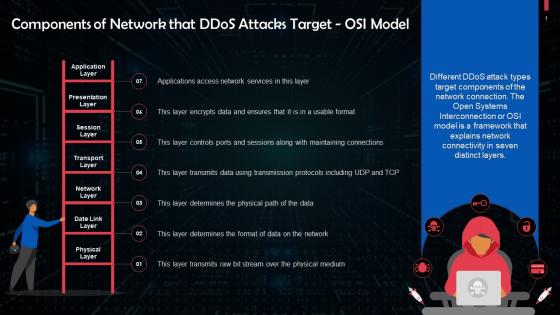 Components Of Network Targeted By DDoS Attacks OSI Model Training Ppt
Components Of Network Targeted By DDoS Attacks OSI Model Training PptPresenting Components of Network Targeted by DDoS Attacks OSI Model. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 7 arrows diverging representing process model charts and networks powerpoint templates
7 arrows diverging representing process model charts and networks powerpoint templatesWe are proud to present our 7 arrows diverging representing process model charts and networks powerpoint templates. This diagram is perfect for illustrating a divergence. The single arrow from which the individual arrows flow is large enough to hold text, making this arrow a place to describe the divergence activity.
-
 Client Server Model Networked Printer Database Working
Client Server Model Networked Printer Database WorkingThis complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Client Server Model Networked Printer Database Working and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of twelve slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.
-
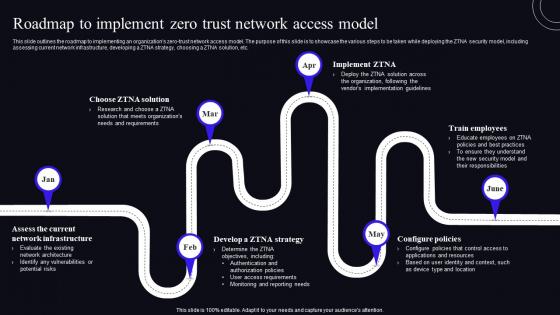 Roadmap To Implement Zero Trust Network Access Model Zero Trust Security Model
Roadmap To Implement Zero Trust Network Access Model Zero Trust Security ModelThis Slide Outlines The Roadmap To Implementing An Organizations Zero-Trust Network Access Model. The Purpose Of This Slide Is To Showcase The Various Steps To Be Taken While Deploying The ZTNA Security Model, Including Assessing Current Network Infrastructure, Developing A ZTNA Strategy, Choosing A ZTNA Solution, Etc. Increase Audience Engagement And Knowledge By Dispensing Information Using Roadmap To Implement Zero Trust Network Access Model Zero Trust Security Model. This Template Helps You Present Information On Six Stages. You Can Also Present Information On Roadmap, Network Infrastructure, Configure Policies Using This PPT Design. This Layout Is Completely Editable So Personaize It Now To Meet Your Audiences Expectations.
-
 Top Tenets Of Zero Trust Network Access Model Zero Trust Security Model
Top Tenets Of Zero Trust Network Access Model Zero Trust Security ModelDeliver an outstanding presentation on the topic using this Top Tenets Of Zero Trust Network Access Model Zero Trust Security Model. Dispense information and present a thorough explanation of Continuous Authentication, Data Protection, Facilitate Least Privilege Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Of Zero Trust Network Access Model Zero Trust Security Model
Working Of Zero Trust Network Access Model Zero Trust Security ModelThis slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Deliver an outstanding presentation on the topic using this Working Of Zero Trust Network Access Model Zero Trust Security Model. Dispense information and present a thorough explanation of Demonstrate, Architectures, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Top Tenets Of Zero Trust Network Access Model Identity Defined Networking
Top Tenets Of Zero Trust Network Access Model Identity Defined NetworkingPresent the topic in a bit more detail with this Top Tenets Of Zero Trust Network Access Model Identity Defined Networking Use it as a tool for discussion and navigation on Top Tenets, Trust Network, Access Model This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Projection Job Networking Site Business Model BMC SS V
Financial Projection Job Networking Site Business Model BMC SS VThis slide depicts projected financial performance of LinkedIn company including elements such as Ad revenue, expected growth, global, revenue, etc. Present the topic in a bit more detail with this Financial Projection Job Networking Site Business Model BMC SS V Use it as a tool for discussion and navigation on Market Drivers, Total Revenue Projection This template is free to edit as deemed fit for your organization. Therefore download it now.
-
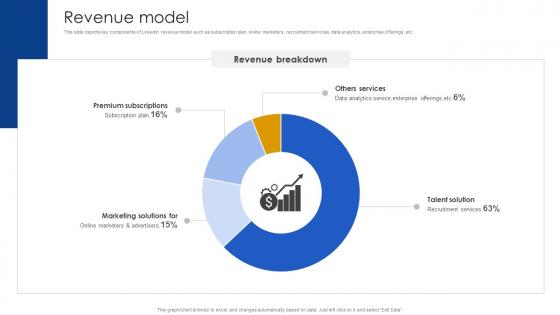 Revenue Model Job Networking Site Business Model BMC SS V
Revenue Model Job Networking Site Business Model BMC SS VThis slide depicts key components of LinkedIn revenue model such as subscription plan, online marketers, recruitment services, data analytics, enterprise offerings, etc. Present the topic in a bit more detail with this Revenue Model Job Networking Site Business Model BMC SS V Use it as a tool for discussion and navigation on Revenue Breakdown, Revenue Model This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Top Tenets Of Zero Trust Network Access Model Ppt File Example
Top Tenets Of Zero Trust Network Access Model Ppt File ExampleDeliver an outstanding presentation on the topic using this Top Tenets Of Zero Trust Network Access Model Ppt File Example. Dispense information and present a thorough explanation of Top Tenets, Zero Trust Network, Access Model using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Financial Projection Professional Networking Platform Business Model BMC SS V
Financial Projection Professional Networking Platform Business Model BMC SS VThis slide depicts projected financial performance of LinkedIn company including elements such as Ad revenue, expected growth, global, revenue, etc. Deliver an outstanding presentation on the topic using this Financial Projection Professional Networking Platform Business Model BMC SS V. Dispense information and present a thorough explanation of Total Revenue Projection, Key Insight, Market Drivers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Revenue Model Professional Networking Platform Business Model BMC SS V
Revenue Model Professional Networking Platform Business Model BMC SS VThis slide depicts key components of LinkedIn revenue model such as subscription plan, online marketers, recruitment services, data analytics, enterprise offerings, etc. Deliver an outstanding presentation on the topic using this Revenue Model Professional Networking Platform Business Model BMC SS V. Dispense information and present a thorough explanation of Revenue Breakdown, Revenue Model using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Different Types Of GAN Models Developed Generative Adversarial Network AI SS
Different Types Of GAN Models Developed Generative Adversarial Network AI SSThis slide provides information regarding different types of GAN models to perform specific tasks along with distinct architectural characteristics in terms of Vanilla GAN, conditional GAN, deep convolutional GAN. Present the topic in a bit more detail with this Different Types Of GAN Models Developed Generative Adversarial Network AI SS. Use it as a tool for discussion and navigation on Vanilla Gan, Conditional GAN, Deep Convolutional GAN. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Networking Service Business Model Financial Projections BMC SS V
Social Networking Service Business Model Financial Projections BMC SS VThis slide presents the financial projections showcasing companys anticipated growth, net income. The projections are based on comprehensive market analysis and historical performance. Present the topic in a bit more detail with this Social Networking Service Business Model Financial Projections BMC SS V. Use it as a tool for discussion and navigation on Revenue, Net Income, Moderate Net Income Growth, Strong Revenue Growth Driven. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Networking Service Business Model Revenue Model BMC SS V
Social Networking Service Business Model Revenue Model BMC SS VThis slide showcases that the social media revenue generated from reality labs and family of apps. Present the topic in a bit more detail with this Social Networking Service Business Model Revenue Model BMC SS V. Use it as a tool for discussion and navigation on Revenue Model. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business network diagram networking models concept powerpoint templates ppt backgrounds for slides
Business network diagram networking models concept powerpoint templates ppt backgrounds for slidesWe are proud to present our business network diagram networking models concept powerpoint templates ppt backgrounds for slides. The above PowerPoint Diagram contains an image of four networking models. This Business Oriented Chart will definitely help you to be more successful. Use this graphics as key element in streamlining your plans. It consists of four connected series of stages to one another.
-
 Activities successful networking ppt powerpoint presentation model display cpb
Activities successful networking ppt powerpoint presentation model display cpbPresenting our Activities Successful Networking Ppt Powerpoint Presentation Model Display Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Activities Successful Networking This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Firewall As A Service Fwaas Potential Threats Of Traditional Firewall Systems In Modern Network
Firewall As A Service Fwaas Potential Threats Of Traditional Firewall Systems In Modern NetworkThis slide highlights the various limitations of traditional firewall systems. The purpose of this slide is to outline the different issues of traditional firewalls. These include unable to prevent transfer of infected files, do not protect already compromised systems, etc. Deliver an outstanding presentation on the topic using this Firewall As A Service Fwaas Potential Threats Of Traditional Firewall Systems In Modern Network. Dispense information and present a thorough explanation of Traditional Firewall Systems, Compromised Systems, Potential Threats, Network Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Before Vs After Zero Trust Network Access Implementation Zero Trust Security Model
Before Vs After Zero Trust Network Access Implementation Zero Trust Security ModelThis slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Deliver an outstanding presentation on the topic using this Before Vs After Zero Trust Network Access Implementation Zero Trust Security Model. Dispense information and present a thorough explanation of Implementation, Distributed, Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Benefits Of Zero Trust Network Access ZTNA Zero Trust Security Model
Benefits Of Zero Trust Network Access ZTNA Zero Trust Security ModelThis Slide Represents The Benefits Of Zero Trust Network Access, A Component Of SASE Technology. The Purpose Of This Slide Is To Demonstrate The Multiple Benefits Of ZTNA To Businesses And Users. It Also Caters To The Security Benefits Such As Increased Control And Visibility, Invisible Infrastructure, And Simple App Segmentation. Present The Topic In A Bit More Detail With This Benefits Of Zero Trust Network Access ZTNA Zero Trust Security Model. Use It As A Tool For Discussion And Navigation On Deployment, Experiences, Appliances. This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Checklist To Build Zero Trust Network Access Architecture Zero Trust Security Model
Checklist To Build Zero Trust Network Access Architecture Zero Trust Security ModelThis slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Deliver an outstanding presentation on the topic using this Checklist To Build Zero Trust Network Access Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Measures, Organizations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Critical Principles Of Zero Trust Network Access Model Zero Trust Security Model
Critical Principles Of Zero Trust Network Access Model Zero Trust Security ModelThis slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Present the topic in a bit more detail with this Critical Principles Of Zero Trust Network Access Model Zero Trust Security Model. Use it as a tool for discussion and navigation on Description, Segmentation, Validation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Endpoint Initiated Zero Trust Network Topology Model Zero Trust Security Model
Endpoint Initiated Zero Trust Network Topology Model Zero Trust Security ModelThis slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. Deliver an outstanding presentation on the topic using this Endpoint Initiated Zero Trust Network Topology Model Zero Trust Security Model. Dispense information and present a thorough explanation of Management, Infrastructure, Installation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 External Components Of Zero Trust Network Architecture Zero Trust Security Model
External Components Of Zero Trust Network Architecture Zero Trust Security ModelThis slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Deliver an outstanding presentation on the topic using this External Components Of Zero Trust Network Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Documentation, Potential using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F1585 Zero Trust Network Access Architectural Models Zero Trust Security Model
F1585 Zero Trust Network Access Architectural Models Zero Trust Security ModelThis slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Introducing F1585 Zero Trust Network Access Architectural Models Zero Trust Security Model to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Architectural, Resources, Verification, using this template. Grab it now to reap its full benefits.
-
 F1586 Zero Trust Network Access Architecture Overview Zero Trust Security Model
F1586 Zero Trust Network Access Architecture Overview Zero Trust Security ModelThis slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Present the topic in a bit more detail with this F1586 Zero Trust Network Access Architecture Overview Zero Trust Security Model. Use it as a tool for discussion and navigation on Resources, Architecture, Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security Model
F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security ModelThis slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Increase audience engagement and knowledge by dispensing information using F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security Model. This template helps you present information on six stages. You can also present information on Architecture, Workflow, Resources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 F1588 Zero Trust Network Access Implementation Challenges Zero Trust Security Model
F1588 Zero Trust Network Access Implementation Challenges Zero Trust Security ModelThis slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on Present the topic in a bit more detail with this F1588 Zero Trust Network Access Implementation Challenges Zero Trust Security Model. Use it as a tool for discussion and navigation on Implementation, Organizations, Productivity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1589 Zero Trust Network Access Performance Tracking Dashboard Zero Trust Security Model
F1589 Zero Trust Network Access Performance Tracking Dashboard Zero Trust Security ModelThis slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. Deliver an outstanding presentation on the topic using this F1589 Zero Trust Network Access Performance Tracking Dashboard Zero Trust Security Model. Dispense information and present a thorough explanation of Performance, Dashboard, Represents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F1590 Zero Trust Network Access System Use Cases Zero Trust Security Model
F1590 Zero Trust Network Access System Use Cases Zero Trust Security ModelThis slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Present the topic in a bit more detail with this F1590 Zero Trust Network Access System Use Cases Zero Trust Security Model. Use it as a tool for discussion and navigation on Internal Firewall Replacement, Limiting User Access, Network Access Control Replacement. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1591 Zero Trust Network Access User Flow Overview Zero Trust Security Model
F1591 Zero Trust Network Access User Flow Overview Zero Trust Security ModelThis slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Deliver an outstanding presentation on the topic using this F1591 Zero Trust Network Access User Flow Overview Zero Trust Security Model. Dispense information and present a thorough explanation of Authentication, Process, Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F1592 Zero Trust Network Access ZTNA Introduction Zero Trust Security Model
F1592 Zero Trust Network Access ZTNA Introduction Zero Trust Security ModelThis slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Present the topic in a bit more detail with this F1592 Zero Trust Network Access ZTNA Introduction Zero Trust Security Model. Use it as a tool for discussion and navigation on Introduction, Appliances, Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1593 Zero Trust Network Access Vs Virtual Private Network Zero Trust Security Model
F1593 Zero Trust Network Access Vs Virtual Private Network Zero Trust Security ModelThis slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Deliver an outstanding presentation on the topic using this F1593 Zero Trust Network Access Vs Virtual Private Network Zero Trust Security Model. Dispense information and present a thorough explanation of Infrastructure, Configuration, Equipment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Features Of Zero Trust Network Access Security Model Zero Trust Security Model
Features Of Zero Trust Network Access Security Model Zero Trust Security ModelThis slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Present the topic in a bit more detail with this Features Of Zero Trust Network Access Security Model Zero Trust Security Model. Use it as a tool for discussion and navigation on Organizations, Applications, Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Main Pillars Of Zero Network Trust Access Zero Trust Security Model
Main Pillars Of Zero Network Trust Access Zero Trust Security ModelThis slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation. Present the topic in a bit more detail with this Main Pillars Of Zero Network Trust Access Zero Trust Security Model. Use it as a tool for discussion and navigation on Application, Infrastructure, Orchestration Automation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 On Ramp Option 3 The Network Zero Trust Security Model
On Ramp Option 3 The Network Zero Trust Security ModelThis slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Present the topic in a bit more detail with this On Ramp Option 3 The Network Zero Trust Security Model. Use it as a tool for discussion and navigation on Organizations, Microsegmentation, Stateful Session Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Reasons To Adopt Zero Trust Network Access Model Zero Trust Security Model
Reasons To Adopt Zero Trust Network Access Model Zero Trust Security ModelThis slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Introducing Reasons To Adopt Zero Trust Network Access Model Zero Trust Security Model to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Businesses, Resources, Organizations, using this template. Grab it now to reap its full benefits.
-
 Service Initiated Zero Trust Network Topology Model Zero Trust Security Model
Service Initiated Zero Trust Network Topology Model Zero Trust Security ModelThis slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Deliver an outstanding presentation on the topic using this Service Initiated Zero Trust Network Topology Model Zero Trust Security Model. Dispense information and present a thorough explanation of Environment, Enterprise, Access Connection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps To Implement Zero Trust Network Access Model Zero Trust Security Model
Steps To Implement Zero Trust Network Access Model Zero Trust Security ModelThis slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Present the topic in a bit more detail with this Steps To Implement Zero Trust Network Access Model Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Protection, Monitor The Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technologies Used In Zero Trust Network Access Zero Trust Security Model
Technologies Used In Zero Trust Network Access Zero Trust Security ModelThis slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Deliver an outstanding presentation on the topic using this Technologies Used In Zero Trust Network Access Zero Trust Security Model. Dispense information and present a thorough explanation of Technologies, Techniques, Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Timeline To Implement Zero Trust Network Access Model Zero Trust Security Model
Timeline To Implement Zero Trust Network Access Model Zero Trust Security ModelThis slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Introducing Timeline To Implement Zero Trust Network Access Model Zero Trust Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Implementation, Applications, using this template. Grab it now to reap its full benefits.
-
 Top Zero Trust Network Access Software Solutions Zero Trust Security Model
Top Zero Trust Network Access Software Solutions Zero Trust Security ModelThis slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Present the topic in a bit more detail with this Top Zero Trust Network Access Software Solutions Zero Trust Security Model. Use it as a tool for discussion and navigation on Software, Solutions, Implementation . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Traditional Perimeter Based Network Security Overview And Limitations Zero Trust Security Model
Traditional Perimeter Based Network Security Overview And Limitations Zero Trust Security ModelThis slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. Deliver an outstanding presentation on the topic using this Traditional Perimeter Based Network Security Overview And Limitations Zero Trust Security Model. Dispense information and present a thorough explanation of Traditional, Overview, Limitations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Traditional Security Models Vs Zero Trust Network Access Zero Trust Security Model
Traditional Security Models Vs Zero Trust Network Access Zero Trust Security ModelThis slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Present the topic in a bit more detail with this Traditional Security Models Vs Zero Trust Network Access Zero Trust Security Model. Use it as a tool for discussion and navigation on Dependence, Foundation, Attack Surface. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Training Program For Zero Trust Network Access Model Zero Trust Security Model
Training Program For Zero Trust Network Access Model Zero Trust Security ModelThis slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Deliver an outstanding presentation on the topic using this Training Program For Zero Trust Network Access Model Zero Trust Security Model. Dispense information and present a thorough explanation of Micro Segmentation, Solutions, Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Of Zero Trust Network Access ZTNA Models Zero Trust Security Model
Types Of Zero Trust Network Access ZTNA Models Zero Trust Security ModelThis Slide Describes The Various Types Of Zero-Trust Network Access Models. The Purpose Of This Slide Is To Demonstrate The Various ZTNA Models And Core Elements Of ZTNA Implementation. The Model Types Include User Protection, Workload Protection, And Device Protection. Present The Topic In A Bit More Detail With This Types Of Zero Trust Network Access ZTNA Models Zero Trust Security Model. Use It As A Tool For Discussion And Navigation On Knowledge Conviction, Disruptive Technologies, Cultural Mindset Change. This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Working Functions Of Zero Trust Network Access Architecture Zero Trust Security Model
Working Functions Of Zero Trust Network Access Architecture Zero Trust Security ModelThis slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Introducing Working Functions Of Zero Trust Network Access Architecture Zero Trust Security Model to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Architecture, Abnormalities, Processing, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Network Access Vs Zero Trust Architecture Zero Trust Security Model
Zero Trust Network Access Vs Zero Trust Architecture Zero Trust Security ModelThis slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Deliver an outstanding presentation on the topic using this Zero Trust Network Access Vs Zero Trust Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Implementation, Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Stewardship Model Creating A Data Steward Network Ppt Ideas Graphics
Data Stewardship Model Creating A Data Steward Network Ppt Ideas GraphicsThis slide represents creating a data steward network in which existing and aspiring data stewards collaborate to create strategies, tools and structures that helps in effective, collective, practical and safe data collaboratives. Increase audience engagement and knowledge by dispensing information using Data Stewardship Model Creating A Data Steward Network Ppt Ideas Graphics. This template helps you present information on two stages. You can also present information on Data Steward Network, Safe Data Collaboratives, Public-Private Collaborations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Business Model Supply Network Business Investor Funding Elevator Pitch Deck
Business Model Supply Network Business Investor Funding Elevator Pitch DeckFollowing slide provided detailed insights into companies business model which comprises of key partners, key activities, resources, value proposition, customer relations, channels, customer segment, cost structure and revenue sources. Deliver an outstanding presentation on the topic using this Business Model Supply Network Business Investor Funding Elevator Pitch Deck. Dispense information and present a thorough explanation of Key Partners, Value Proposition, Channels using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Model To Effective Delivering ICT Services For Enhanced Business Strategy SS V
Network Security Model To Effective Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Introducing Network Security Model To Effective Delivering ICT Services For Enhanced Business Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threats, Security Breaches, Virtual Private, using this template. Grab it now to reap its full benefits.
-
 Business Model Social Audio Networking Application Investor Funding Elevator Pitch Deck
Business Model Social Audio Networking Application Investor Funding Elevator Pitch DeckThe purpose of this slide is to highlight the business model used to understand the operational details of the company. It includes information related to partners, activities, resources, value propositions, channels, revenue streams, etc. Deliver an outstanding presentation on the topic using this Business Model Social Audio Networking Application Investor Funding Elevator Pitch Deck. Dispense information and present a thorough explanation of Key Partners, Value Proposition, Channels using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementation Of Information Network Security Model To Effective Communication Strategy SS V
Implementation Of Information Network Security Model To Effective Communication Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Present the topic in a bit more detail with this Implementation Of Information Network Security Model To Effective Communication Strategy SS V. Use it as a tool for discussion and navigation on Message Transformation, Information Channel. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How Deep Learning Model Functions With Neural Networks Generative Ai Artificial Intelligence AI SS
How Deep Learning Model Functions With Neural Networks Generative Ai Artificial Intelligence AI SSThis slide provides information regarding the operation of deep learning models with various layers of neural networks. It also highlights the role of a neural network as they help in impersonating the human brain by collaborating data inputs, bias, etc. Deliver an outstanding presentation on the topic using this How Deep Learning Model Functions With Neural Networks Generative Ai Artificial Intelligence AI SS. Dispense information and present a thorough explanation of Architectures, Extraction, Classification using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Building Model Neural Network Layers Chatgpt Ai Powered Architecture Explained ChatGPT SS
Building Model Neural Network Layers Chatgpt Ai Powered Architecture Explained ChatGPT SSThis slide caters to details related to the building blocks that work together in the Chat-GPT transformer model to process input sequences, capture contextual information, and generate meaningful output sequences. Deliver an outstanding presentation on the topic using this Building Model Neural Network Layers Chatgpt Ai Powered Architecture Explained ChatGPT SS. Dispense information and present a thorough explanation of Transformer, Neighborhood, Convolutional using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Computer Networking Devices Modem For Decoding Digital Data
Computer Networking Devices Modem For Decoding Digital DataThis slide showcases the essential types of modem an important part of computer networking devices which helps an organization to update any global standard by using software patch. It include details such as optical, acoustic and smart modem. Introducing our Computer Networking Devices Modem For Decoding Digital Data set of slides. The topics discussed in these slides are Optical Modem, Acoustic Modem, Smart Modem. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Omnichannel Model Icon For Customer Network Marketing
Omnichannel Model Icon For Customer Network MarketingPresenting our set of slides with Omnichannel Model Icon For Customer Network Marketing. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Omnichannel, Marketing, Customer Network.




