Powerpoint Templates and Google slides for Mitigated
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Man In The Middle MITM Phishing Attack Diagram
Phishing Attacks And Strategies To Mitigate Them V2 Man In The Middle MITM Phishing Attack DiagramThis slide demonstrates the working flow of man-in-the-middle phishing attacks using MITM phishing toolkit cloud server. This slide also elaborates the various real-world examples of MITM attacks such as Equifaxs mobile application, superfish and DigiNotar. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Man In The Middle MITM Phishing Attack Diagram. Dispense information and present a thorough explanation of Phishing Attack Diagram, Equifaxs Mobile Application, Toolkit Cloud Server, Intended Website Server using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
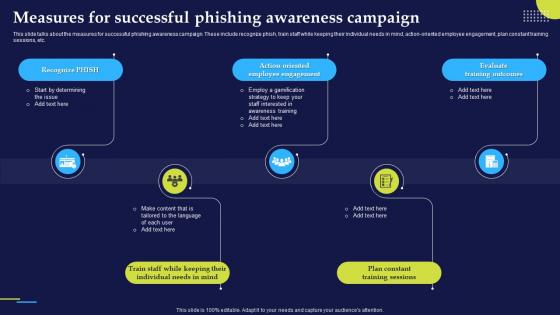 Phishing Attacks And Strategies To Mitigate Them V2 Measures For Successful Phishing Awareness Campaign
Phishing Attacks And Strategies To Mitigate Them V2 Measures For Successful Phishing Awareness CampaignThis slide talks about the measures for successful phishing awareness campaign. These include recognize phish, train staff while keeping their individual needs in mind, action-oriented employee engagement, plan constant training sessions, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Measures For Successful Phishing Awareness Campaign to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Action Oriented Employee Engagement, Evaluate Training Outcomes, Phishing Awareness Campaign, Plan Constant Training Sessions, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Multi Layered Approach To Phishing Defenses
Phishing Attacks And Strategies To Mitigate Them V2 Multi Layered Approach To Phishing DefensesThis slide represents the multi-layered approach to phishing defenses. These include create difficulty for attackers to reach users, guide users in identifying and reporting phishing emails, save your organization from unexpected phishing scams, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Multi Layered Approach To Phishing Defenses. Use it as a tool for discussion and navigation on Multi Layered Approach, Reporting Phishing Emails, Unexpected Phishing Scams. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention Techniques
Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention TechniquesThis slide demonstrates the different types pf pharming phishing scams. The primary types include malware-based pharming and DNS pharming. This slide also outlines the ways which helps to prevent a pharming attack such as verify the URL, install VPN, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Pharming Phishing Types And Prevention Techniques. Dispense information and present a thorough explanation of Pharming Phishing Scams, Malware Based Pharming, Pharming Attack, Prevention Techniques using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Phishing Awareness Training Program For Employees
Phishing Attacks And Strategies To Mitigate Them V2 Phishing Awareness Training Program For EmployeesThis slide represents the training program for employees which will help them to prevent various cyber security scams in business. The purpose of this slide is to outline the mode, venue and schedule for the different training programs. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Phishing Awareness Training Program For Employees. This template helps you present information on one stages. You can also present information on Phishing Awareness Training, Program For Employees, Training Programs, Security Scams In Business using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Popular Man In The Middle Phishing Kits Used
Phishing Attacks And Strategies To Mitigate Them V2 Popular Man In The Middle Phishing Kits UsedThis slide outlines the various phishing kits used by attackers to conduct man-in-the-middle scams. The purpose of thus slide is to describe the reported year and use of different MITM kits such as Evilginx2, Modlishka, Muraena, EvilnoVNC and EvilProxy. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Popular Man In The Middle Phishing Kits Used. Use it as a tool for discussion and navigation on Creates Special Tokens, Uniform Resource Locator, Expose Phishing Content, Stolen Session Cookie. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle Cyber
Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle CyberThis slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle Cyber to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure Connections, Avoid Phishing Emails, Endpoint Security, Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques Employed In Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques Employed In Phishing AttacksThis slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques Employed In Phishing Attacks. This template helps you present information on three stages. You can also present information on Primary Techniques Employed, Phishing Attacks, Phishers To Attack Victims, Attackers To Trick Victims using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples Of Smishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples Of Smishing AttacksThis slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples Of Smishing Attacks to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Real World Examples, Smishing Attacks, Smishing Cyber Attacks, Individuals And Organizations, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Resources And Training That Companies Can Provide
Phishing Attacks And Strategies To Mitigate Them V2 Resources And Training That Companies Can ProvideThis slide demonstrates the resources and training that can be provided by companies to their staff. These include employee training, check to see if you have already been breached, be aware of the various phishing attacks, invest in security education, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Resources And Training That Companies Can Provide. This template helps you present information on five stages. You can also present information on Employee Training, Security Education, Phishing Attacks, Resources And Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Roadmap To Secure Organizations From Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Roadmap To Secure Organizations From PhishingThis slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Roadmap To Secure Organizations From Phishing to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implement Technical Controls, Establish Policies And Procedures, Employee Training, Baseline Security Assessment, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Whaling Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Whaling Phishing AttacksThis slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Whaling Phishing Attacks. This template helps you present information on six stages. You can also present information on Flag Emails Received, Near Similar Email Domains, Spot Grammar, Cross Verify Sensitive Requests using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Spear Phishing Scam
Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Spear Phishing ScamIntroducing Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Spear Phishing Scam to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing Scam, Change Your Passwords, Backup Your Files, Conduct A Hardware Scan, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Identify Smishing Cyber Scams
Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Identify Smishing Cyber ScamsThis slide talks about the various methods of identifying smishing cyber attacks. The purpose of this slide is to help users identify smishing scams. These include suspicious texts from unknown numbers, unrequested links and files, money transfer requests, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Identify Smishing Cyber Scams. Use it as a tool for discussion and navigation on Smishing Cyber Attacks, Smishing Scams, Unrequested Links And Files, Money Transfer Requests. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Techniques Used By Cybercriminals To Conduct
Phishing Attacks And Strategies To Mitigate Them V2 Techniques Used By Cybercriminals To ConductThis slide demonstrates the techniques used by scammers to conduct watering hole attacks. These methods are cross-site scripting, DMS cache poisoning, drive-by downloads, malvertising, etc. This slide also outlines common intelligence gathering methods. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Techniques Used By Cybercriminals To Conduct. Use it as a tool for discussion and navigation on Social Networking Sites, Demographic Information From Websites, Social Engineering, Keyloggers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Timeline To Secure Organizations From Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Timeline To Secure Organizations From PhishingThis slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Timeline To Secure Organizations From Phishing. This template helps you present information on five stages. You can also present information on Implement Technical Controls, Employee Training, Establish Policies And Procedures, Timely Evaluation And Updates using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By Google To Prevent Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By Google To Prevent PhishingThis slide demonstrates the different tools provided by Google to prevent and report cyber phishing scams. These include to spot phishing mails with the help of Gmail, utilize safe browsing in chrome, look for unsafe saved passwords, password alert for chrome, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By Google To Prevent Phishing. Dispense information and present a thorough explanation of Safe Browsing In Chrome, Phishing Mails Detection With Gmail, Two Step Verification, Password Alert For Chrome using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Tricks Employed By Malicious Websites To Scam
Phishing Attacks And Strategies To Mitigate Them V2 Tricks Employed By Malicious Websites To ScamThis slide talks about various tricks utilized by fraudulent websites to scam the visitors. The purpose of this slide is to make users aware of such different tricks such as free or discount offers, low interest rates or free credit cards, employment opportunities, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Tricks Employed By Malicious Websites To Scam to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Employment Opportunities, Emergency Warnings, Malicious Websites, Scam Victims, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Understanding The Process Of E Mail Based Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Understanding The Process Of E Mail Based PhishingThis slide demonstrates the procedure of email-based phishing attacks. The purpose of this slide is to explain how fake websites are used by attackers to get the sensitive data of the users. The key components include database, fake website, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Understanding The Process Of E Mail Based Phishing. Use it as a tool for discussion and navigation on Email Based Phishing Attacks, Fake Website, Phishing Email, Original Website. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And Code
Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And CodeThis slide talks about the techniques which can help in protecting organizations from phishing and vishing attacks. The purpose of this slide is to explain two important methods of preventing cyber scams. These techniques are email signing and code signing. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And Code. Dispense information and present a thorough explanation of Vishing Attacks Prevention, Email Signing And Code Signing, Preventing Cyber Scams using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Warning Signs Of Pop Up Phishing Scams
Phishing Attacks And Strategies To Mitigate Them V2 Warning Signs Of Pop Up Phishing ScamsThis slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Warning Signs Of Pop Up Phishing Scams to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Terrible Pop Up Advertisement, Pop Up Phishing Cyber Attacks, Install Their Malware, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Why Businesses Fall Victim To Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Why Businesses Fall Victim To Phishing AttacksThis slide outlines the various reasons responsible for businesses to fall victim to different phishing attacks. These include inadequate employee training, never evaluate the success of the training, careless browsing habits of the employees, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Why Businesses Fall Victim To Phishing Attacks. This template helps you present information on five stages. You can also present information on Inadequate Employee Training, Training Or Policy Improvement, Organizations Are Unaware, Changing Phishing Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Working Of Phishing Training Programs
Phishing Attacks And Strategies To Mitigate Them V2 Working Of Phishing Training ProgramsIntroducing Phishing Attacks And Strategies To Mitigate Them V2 Working Of Phishing Training Programs to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Start With Employee Training, Make Fictitious Phishing Campaigns, Track Progress And Upgrade, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Working Of Watering Hole Phishing Attack
Phishing Attacks And Strategies To Mitigate Them V2 Working Of Watering Hole Phishing AttackThis slide represents the working process of watering hole phishing attacks. The purpose of this slide is to illustrate the flow diagram of watering hole phishing scams. The key points include research and identification, analysis, preparation and execution. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Working Of Watering Hole Phishing Attack. This template helps you present information on four stages. You can also present information on Analysis, Research And Identification, Preparation, Execution, Phishing Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Working Procedure Of Spear Phishing Attack
Phishing Attacks And Strategies To Mitigate Them V2 Working Procedure Of Spear Phishing AttackThis slide illustrates the structure of spear phishing attack. The purpose of this slide is to explain the working flow of spear phishing attack. The key components include attacker, phishing email, targeted users, exploited system, internal network, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Working Procedure Of Spear Phishing Attack to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Email, Targeted Users, Exploited System, Internal Network, Attacker, using this template. Grab it now to reap its full benefits.
-
 Real World Examples Of Watering Hole Phishing Attacks And Strategies To Mitigate Them V2
Real World Examples Of Watering Hole Phishing Attacks And Strategies To Mitigate Them V2This slide describes the real-world examples of watering hole phishing scams. These include Facebook, Twitter, Microsoft, and Apple scam, LuckyMouse scam, International Civil Aviation Organization ICAO scam, Ccleaner scam and Holy Water scam. Increase audience engagement and knowledge by dispensing information using Real World Examples Of Watering Hole Phishing Attacks And Strategies To Mitigate Them V2. This template helps you present information on four stages. You can also present information on International Civil Aviation, Organization Scam, Watering Hole Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Content For Phishing Attacks And Strategies To Mitigate Them V2
Table Of Content For Phishing Attacks And Strategies To Mitigate Them V2Introducing Table Of Content For Phishing Attacks And Strategies To Mitigate Them V2 to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Attacks Prevention, Phishing Attacks Awareness Training, Phishing Attacks Introduction, using this template. Grab it now to reap its full benefits.
-
 Effective And Mitigation Process Achieving Business Goals Procurement Strategies Strategy SS V
Effective And Mitigation Process Achieving Business Goals Procurement Strategies Strategy SS VThis slide provides an overview of the steps covered in managing potential threats and risks that can negatively impact the firm. Major steps covered in the process are risk identification, analysis, prioritization, mitigation and monitoring. Increase audience engagement and knowledge by dispensing information using Effective And Mitigation Process Achieving Business Goals Procurement Strategies Strategy SS V. This template helps you present information on five stages. You can also present information on Risk Identification, Risk Monitoring, Risk Analysis using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Risk Mitigation Plan To Reduce Achieving Business Goals Procurement Strategies Strategy SS V
Risk Mitigation Plan To Reduce Achieving Business Goals Procurement Strategies Strategy SS VThis slide provides an overview of the strategies adopted to reduce risk impacts. The plans covered are adopting hedge funding, having flexible budget, using supply chain software, diversifying suppliers, creating a contingency plan, etc. Deliver an outstanding presentation on the topic using this Risk Mitigation Plan To Reduce Achieving Business Goals Procurement Strategies Strategy SS V. Dispense information and present a thorough explanation of Procurement, Risk Mitigation, Overview using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Risk Assessment And Mitigation Achieving Business Goals Procurement Strategies Strategy SS V
Risk Risk Assessment And Mitigation Achieving Business Goals Procurement Strategies Strategy SS VThis slide provides an overview of the various types of risks associated with vendors that affect a companys operations. Major risks covered are strategic, operational, financial, reputational, compliance and regulatory. Present the topic in a bit more detail with this Risk Risk Assessment And Mitigation Achieving Business Goals Procurement Strategies Strategy SS V. Use it as a tool for discussion and navigation on Risk Mitigation, Risk Assessment, Mitigation Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Multiple Ways To Mitigate Foreign Expansion Risks Global Market Expansion For Product
Multiple Ways To Mitigate Foreign Expansion Risks Global Market Expansion For ProductThe slide carries different risk mitigation strategies to overcome the challenges of global expansion faced by companies. Various risks involved are foreign exchange risk, credit risk and intellectual property risk.Introducing Multiple Ways To Mitigate Foreign Expansion Risks Global Market Expansion For Product to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Foreign Exchange, Complete Payment, Fluctuations Business, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Risks Mitigation With Serverless Computing V2
Cybersecurity Risks Mitigation With Serverless Computing V2This slide talks about some ways that a serverless system can help reduce the attack surface by minimizing the number of attack vectors. These include reduced infrastructure, access control restrictions, stateless computing, and auto-scaling. Increase audience engagement and knowledge by dispensing information using Cybersecurity Risks Mitigation With Serverless Computing V2. This template helps you present information on four stages. You can also present information on Reduced Infrastructure, Access Control Restrictions, Stateless Computing, Serverless Computing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Supply Chain Risk Trends Matrix For Developing Mitigation Plan
Supply Chain Risk Trends Matrix For Developing Mitigation PlanThis slide represents matrix for proactively managing risks and trends by enhancing supply chain efficiency. It includes aspects such as global trade and offshoring, monopoly sourcing, etc. and risks such as natural disasters, economic risks, etc. Introducing our Supply Chain Risk Trends Matrix For Developing Mitigation Plan set of slides. The topics discussed in these slides are Global Trade Offshoring, Lean Manufacturing, Resource Dependence. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Product Expansion Guide To Increase Brand Multiple Ways To Mitigate Foreign Expansion Risks
Product Expansion Guide To Increase Brand Multiple Ways To Mitigate Foreign Expansion RisksThe slide carries different risk mitigation strategies to overcome the challenges of global expansion faced by companies. Various risks involved are foreign exchange risk, credit risk and intellectual property risk. Increase audience engagement and knowledge by dispensing information using Product Expansion Guide To Increase Brand Multiple Ways To Mitigate Foreign Expansion Risks. This template helps you present information on three stages. You can also present information on Foreign Exchange Risk, Credit Risk, Intellectual Property Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Mitigate Liquidity Risks Ultimate Guide To Commercial Fin SS
Best Practices To Mitigate Liquidity Risks Ultimate Guide To Commercial Fin SSThis slide shows information which can be used to understand how to manage liquidity risk associated with commercial banks. It includes practices such as risk assessment, contingency planning and cash flow management, etc. Deliver an outstanding presentation on the topic using this Best Practices To Mitigate Liquidity Risks Ultimate Guide To Commercial Fin SS. Dispense information and present a thorough explanation of Risk Assessment, Contingency Planning using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Market Risk Mitigation Practices For Banks Ultimate Guide To Commercial Fin SS
Key Market Risk Mitigation Practices For Banks Ultimate Guide To Commercial Fin SSThis slide shows details regarding various practices which can be used by commercial banks to manage market risk. It includes strategies such as risk measurement and monitoring, diversification, stress testing, etc. Deliver an outstanding presentation on the topic using this Key Market Risk Mitigation Practices For Banks Ultimate Guide To Commercial Fin SS. Dispense information and present a thorough explanation of Diversification, Market Research using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cost Reduction Strategies Effective Risk Management And Mitigation Process Strategy SS V
Cost Reduction Strategies Effective Risk Management And Mitigation Process Strategy SS VThis slide provides an overview of the steps covered in managing potential threats and risks that can negatively impact the firm. Major steps covered in the process are risk identification, analysis, prioritization, mitigation and monitoring. Introducing Cost Reduction Strategies Effective Risk Management And Mitigation Process Strategy SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Risk Identification, Risk Monitoring, Risk Analysis, Risk Mitigation, using this template. Grab it now to reap its full benefits.
-
 Cost Reduction Strategies Risk Mitigation Mitigation Plan To Reduce Procurement Risks Strategy SS V
Cost Reduction Strategies Risk Mitigation Mitigation Plan To Reduce Procurement Risks Strategy SS VThis slide provides an overview of the strategies adopted to reduce risk impacts. The plans covered are adopting hedge funding, having flexible budget, using supply chain software, diversifying suppliers, creating a contingency plan, etc. Increase audience engagement and knowledge by dispensing information using Cost Reduction Strategies Risk Mitigation Mitigation Plan To Reduce Procurement Risks Strategy SS V. This template helps you present information on ones. You can also present information on Price Instability, Overspending, Probability, Mitigation Plan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cost Reduction Strategies Risk Mitigation Vendor Risk Assessment And Mitigation Plan Strategy SS V
Cost Reduction Strategies Risk Mitigation Vendor Risk Assessment And Mitigation Plan Strategy SS VThis slide provides an overview of the various types of risks associated with vendors that affect a companys operations. Major risks covered are strategic, operational, financial, reputational, compliance and regulatory. Introducing Cost Reduction Strategies Risk Mitigation Vendor Risk Assessment And Mitigation Plan Strategy SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Strategic Risk, Operational Risk, Reputational Risk, using this template. Grab it now to reap its full benefits.
-
 Cost Reduction Strategies Supplier Management Best Practices To Mitigate Risks Strategy SS V
Cost Reduction Strategies Supplier Management Best Practices To Mitigate Risks Strategy SS VThis slide provides an overview of the practices to be adopted by firms in order to ensure vendor management. Major best practices covered are aligning strategy and company goals, selecting the right supplier, signing SLA, using self service portal and monitoring performance. Introducing Cost Reduction Strategies Supplier Management Best Practices To Mitigate Risks Strategy SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Vendor Management, Strategy And Company Goals, Select Right Supplier, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Risk Mitigation Strategy Action Plan Icon
Cyber Security Risk Mitigation Strategy Action Plan IconIntroducing our premium set of slides with Cyber Security Risk Mitigation Strategy Action Plan Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Mitigation, Strategy, Action. So download instantly and tailor it with your information.
-
 Mitigation Solutions To Overcome Future Challenges In Telecom FIO SS
Mitigation Solutions To Overcome Future Challenges In Telecom FIO SSFollowing slide showcases strategic solutions to overcome issues that may e faced by telecommunication sector in future. It includes pointer such as partnerships, security protocols, sustainable practices, etc. Introducing our premium set of slides with Mitigation Solutions To Overcome Future Challenges In Telecom FIO SS. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Protocols, Sustainable Practices, Renewed Focus On Customer Needs. So download instantly and tailor it with your information.
-
 Effective Risk Management And Mitigation Process Risk Management And Mitigation
Effective Risk Management And Mitigation Process Risk Management And MitigationThis slide provides an overview of the steps covered in managing potential threats and risks that can negatively impact the firm. Major steps covered in the process are risk identification, analysis, prioritization, mitigation and monitoring. Introducing Effective Risk Management And Mitigation Process Risk Management And Mitigation to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identification, Analysis, Mitigation, using this template. Grab it now to reap its full benefits.
-
 Essential Risk Mitigation Strategies For Business Risk Management And Mitigation
Essential Risk Mitigation Strategies For Business Risk Management And MitigationThis slide provides an overview of risk mitigation techniques. Major strategies covered are keep opportunities and risk separate, provide optimal resources and align incentive structure Increase audience engagement and knowledge by dispensing information using Essential Risk Mitigation Strategies For Business Risk Management And Mitigation. This template helps you present information on three stages. You can also present information on Separate, Operational, Structure using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Framework To Optimize Risk Management Level Risk Management And Mitigation
Framework To Optimize Risk Management Level Risk Management And MitigationThis slide provides an overview of the model used for optimizing the level of threat management. The slide includes strategy, risk, performance and reward. Introducing Framework To Optimize Risk Management Level Risk Management And Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strategy, Performance, Reward, using this template. Grab it now to reap its full benefits.
-
 HR Risk Management Plan Steps Risk Management And Mitigation
HR Risk Management Plan Steps Risk Management And MitigationThis slide provides an overview of the steps followed to determine potential threats in human resource management. Major steps covered are assessing and prioritizing risks, designing solutions, regular tracking and improving management skills Increase audience engagement and knowledge by dispensing information using HR Risk Management Plan Steps Risk Management And Mitigation. This template helps you present information on five stages. You can also present information on Potential, Solutions, Regular using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Risk Management Software Stats For Businesses Risk Management And Mitigation
Key Risk Management Software Stats For Businesses Risk Management And MitigationThis slide provides an overview of the stats regarding risk management software. Major stats covered are firms earn great revenue annually, businesses need less workforce, etc. Increase audience engagement and knowledge by dispensing information using Key Risk Management Software Stats For Businesses Risk Management And Mitigation. This template helps you present information on three stages. You can also present information on Businesses, Workforces, Software using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Managing Various Types Of Strategic Risks Risk Management And Mitigation
Managing Various Types Of Strategic Risks Risk Management And MitigationThis slide provides an overview of the multiple strategic risks. Major internal and types of risks covered are regulatory, political, competitor, economic, change, reputational, governance, financial and operational. Introducing Managing Various Types Of Strategic Risks Risk Management And Mitigation to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Regulatory, Competitor, Economic, using this template. Grab it now to reap its full benefits.
-
 Organizational Risk Assessment And Mitigation Canvas Risk Management And Mitigation
Organizational Risk Assessment And Mitigation Canvas Risk Management And MitigationThis slide provides an overview of the companys risk assessment canvas that includes likelihood, impact and score. Major risks covered are late payment, loss of energy, better competitor pricing and compliance risk Deliver an outstanding presentation on the topic using this Organizational Risk Assessment And Mitigation Canvas Risk Management And Mitigation. Dispense information and present a thorough explanation of Payment, Energy, Pricing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Of Procurement Risk Management Strategy Risk Management And Mitigation
Overview Of Procurement Risk Management Strategy Risk Management And MitigationThis slide exhibits the risk management strategy adopted by firms to reduce the impact of uncertain events. The slide covers types, steps for risk management and the importance that is provides better quality data, boosts customer satisfaction, etc. Introducing Overview Of Procurement Risk Management Strategy Risk Management And Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Importance, Procurement, Management, using this template. Grab it now to reap its full benefits.
-
 Probability And Impact Matrix To Prioritize And Risk Management And Mitigation
Probability And Impact Matrix To Prioritize And Risk Management And MitigationThis slide provides an overview of a firms probability impact matrix to determine the level of risk and task corrective actions. Major risks covered are operational integrity, geopolitical instability, climate risk, etc. Present the topic in a bit more detail with this Probability And Impact Matrix To Prioritize And Risk Management And Mitigation. Use it as a tool for discussion and navigation on Probability, Impact, Manage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Analysis Decision Tree To Analyze Procurement Risk Management And Mitigation
Risk Analysis Decision Tree To Analyze Procurement Risk Management And MitigationThis slide provides an overview of the decision tree diagram created to determine the suitable supplier and risk involved. It further includes key takeaways that include the reasons for selecting the supplier. Introducing Risk Analysis Decision Tree To Analyze Procurement Risk Management And Mitigation to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Success, Analyze, Procurement, using this template. Grab it now to reap its full benefits.
-
 Risk Analysis Risk Analysis Register To Determine Risk Management And Mitigation
Risk Analysis Risk Analysis Register To Determine Risk Management And MitigationThis slide provides an overview of the log register used to identify the potential risks and their mitigation plan. The risks covered are price instability, overspending, inaccurate forecasting, disruptions and fraud. Deliver an outstanding presentation on the topic using this Risk Analysis Risk Analysis Register To Determine Risk Management And Mitigation. Dispense information and present a thorough explanation of Occurring, Impact, Severity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Identification Checklist To Identify And Manage Risk Management And Mitigation
Risk Identification Checklist To Identify And Manage Risk Management And MitigationThis slide provides an overview of the checklist created to identify potential risks. The risks covered are inaccurate need analysis, inadequate vendor management, lack od automation, poor supplier management, overspending, etc. Present the topic in a bit more detail with this Risk Identification Checklist To Identify And Manage Risk Management And Mitigation. Use it as a tool for discussion and navigation on Inaccurate, Management, Procurement. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
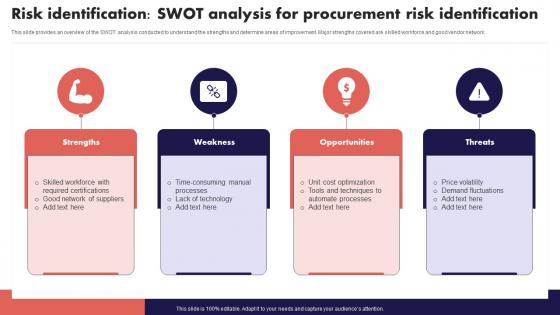 Risk Identification SWOT Analysis For Procurement Risk Management And Mitigation
Risk Identification SWOT Analysis For Procurement Risk Management And MitigationThis slide provides an overview of the SWOT analysis conducted to understand the strengths and determine areas of improvement. Major strengths covered are skilled workforce and good vendor network. Increase audience engagement and knowledge by dispensing information using Risk Identification SWOT Analysis For Procurement Risk Management And Mitigation. This template helps you present information on four stages. You can also present information on Strengths, Weakness, Opportunities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Risk Management Steps For Corporate Firm Risk Management And Mitigation
Risk Management Steps For Corporate Firm Risk Management And MitigationThis slide provides an overview of the risk management steps followed by a company. Main steps covered are identifying, measuring, responding, monitoring and reporting Introducing Risk Management Steps For Corporate Firm Risk Management And Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Monitor, Respond, Measure, using this template. Grab it now to reap its full benefits.
-
 Risk Mitigation Plan To Reduce Risk Management And Mitigation
Risk Mitigation Plan To Reduce Risk Management And MitigationThis slide provides an overview of the strategies adopted to reduce risk impacts. The plans covered are adopting hedge funding, having flexible budget, using supply chain software, diversifying suppliers, creating a contingency plan, etc. Deliver an outstanding presentation on the topic using this Risk Mitigation Plan To Reduce Risk Management And Mitigation. Dispense information and present a thorough explanation of Instability, Inaccurate, Disruptions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Mitigation Vendor Risk Assessment And Risk Management And Mitigation
Risk Mitigation Vendor Risk Assessment And Risk Management And MitigationThis slide provides an overview of the various types of risks associated with vendors that affect a companys operations. Major risks covered are strategic, operational, financial, reputational, compliance and regulatory. Present the topic in a bit more detail with this Risk Mitigation Vendor Risk Assessment And Risk Management And Mitigation. Use it as a tool for discussion and navigation on Strategic, Operational, Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Monitoring Procurement Software To Assess Risk Management And Mitigation
Risk Monitoring Procurement Software To Assess Risk Management And MitigationThis slide provides an overview of the procurement software adopted by the firm to ensure seamless working. The slide covers features, benefits and pricing of the software. Deliver an outstanding presentation on the topic using this Risk Monitoring Procurement Software To Assess Risk Management And Mitigation. Dispense information and present a thorough explanation of Increased, Satisfaction, Investments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Prioritization Impact Assessment Matrix For Risk Management And Mitigation
Risk Prioritization Impact Assessment Matrix For Risk Management And MitigationThis slide provides an overview of the probability impact matrix to prioritize potential threats. The matrix includes scores that help to determine the risk level which is high, moderate and low. Present the topic in a bit more detail with this Risk Prioritization Impact Assessment Matrix For Risk Management And Mitigation. Use it as a tool for discussion and navigation on Instability, Forecasting, Disruptions. This template is free to edit as deemed fit for your organization. Therefore download it now.





