Powerpoint Templates and Google slides for Lifecycle Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cloud Access Security Broker CASB V2 Shadow IT Management Lifecycle Overview
Cloud Access Security Broker CASB V2 Shadow IT Management Lifecycle OverviewThis slide outlines the lifecycle of shadow IT management for safely adopting cloud apps. The purpose of this slide is to showcase the various stages of the lifecycle, such as discovering shadow IT, knowing the risk level of apps, evaluating compliance, analyzing usage, governing cloud apps, and continuous monitoring. Introducing Cloud Access Security Broker CASB V2 Shadow IT Management Lifecycle Overview to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Evaluate Compliance, Govern Cloud Apps, Continuous Monitoring, Network Ecosystem, using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Working Lifecycle Of Web Application Firewall
Firewall Network Security Working Lifecycle Of Web Application FirewallThis slide depicts the various steps that the WAF mechanism takes to prevent the applications from harmful traffic. The purpose of this slide is to showcase the working lifecycle of WAF, including session block, IP address block, request block, user block, generating admin alerts, and creating history logs. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Working Lifecycle Of Web Application Firewall This template helps you present information on Seven stages. You can also present information on Log Out The User, Block The User, Generate Admin Alerts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Incident Response Plan Lifecycle
Security Incident Response Plan LifecycleThis slide showcases the security incident response plan lifecycle. The purpose of this slide is to help the business deploy suitable incident response plans through the use of following lifecycle. It includes elements such as digital forensics, preparations, etc. Introducing our Security Incident Response Plan Lifecycle set of slides. The topics discussed in these slides are Security Incident, Response Plan. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Shadow IT Management Lifecycle Overview CASB Cloud Security
Shadow IT Management Lifecycle Overview CASB Cloud SecurityThis slide outlines the lifecycle of shadow IT management for safely adopting cloud apps. The purpose of this slide is to showcase the various stages of the lifecycle, such as discovering shadow IT, knowing the risk level of apps, evaluating compliance, analyzing usage, governing cloud apps, and continuous monitoring. Introducing Shadow IT Management Lifecycle Overview CASB Cloud Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Evaluate Compliance, Govern Cloud Apps, Continuous Monitoring, Management Lifecycle Overview, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Risk Management Lifecycle
Cyber Security Risk Management LifecycleFollowing slide highlights risk management lifecycle of cyber security for maintaining customer trust. It further covers evaluate, analyse, implement and decision and further includes preparing cyber security policy, risk in data collection, etc. Introducing our premium set of slides with Cyber Security Risk Management Lifecycle. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Implement, Evaluate, Decision. So download instantly and tailor it with your information.
-
 Data Destruction Techniques For Securely Disposing Data Lifecycle Management To Enhance Flow
Data Destruction Techniques For Securely Disposing Data Lifecycle Management To Enhance FlowThis slide presents various data destruction techniques for securely disposing of data. It provides details about techniques such as, overwriting, degussing, physical destruction, cryptographic erasure and secure erase. Present the topic in a bit more detail with this Data Destruction Techniques For Securely Disposing Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Physical Destruction, Cryptographic Erasure, Secure Erase, Data Destruction Technique. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Integrating Algorithms For Encrypting Data Securely Data Lifecycle Management To Enhance Flow
Integrating Algorithms For Encrypting Data Securely Data Lifecycle Management To Enhance FlowThis slide presents algorithms for encrypting data to ensure its protection and security. It includes types such as, AES advanced encryption standard and RSA rivest-shamir-adleman and ECC elliptic curve cryptography. Present the topic in a bit more detail with this Integrating Algorithms For Encrypting Data Securely Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Encryption Algorithm, Key Characteristics, Implementation In Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Archival Stage To Ensure Secure Data Lifecycle Management To Enhance Flow
Overview Of Archival Stage To Ensure Secure Data Lifecycle Management To Enhance FlowThis stage presents an overview of the archival data stage to optimizes how necessary resources perform in the active system. It includes information about goals and benefits such as minimizing cost, enhanced backup and restore performance and decrease in data loss. Present the topic in a bit more detail with this Overview Of Archival Stage To Ensure Secure Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Data Archive Storage Devices, Long-Term Retention And Storage Of Data, Cost-Effective Information Storage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Assessing Data Storage Options To Ensure Securely Data Lifecycle Management To Enhance Flow
Assessing Data Storage Options To Ensure Securely Data Lifecycle Management To Enhance FlowThis slide presents the types of data storage technologies for data lifecycle management. It provides information about, relational , non-relational, object storage and cloud storage databases. Present the topic in a bit more detail with this Assessing Data Storage Options To Ensure Securely Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Relational Databases, Object Storage, Cloud Data Storage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Patch Management Process Lifecycle Mobile Security
Security Patch Management Process Lifecycle Mobile SecurityThis slide represents the patch management process lifecycle which include steps like standardize software versions, categorize assets and patches, etc. Introducing Security Patch Management Process Lifecycle Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Information Gathering, Exploitation using this template. Grab it now to reap its full benefits.
-
 Social Engineering Lifecycle In Mobile Security Mobile Security
Social Engineering Lifecycle In Mobile Security Mobile SecurityThis slide gives an overview of lifecycle of social engineering in mobile security which includes information gathering, developing relationship, exploitation, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Lifecycle In Mobile Security Mobile Security This template helps you present information on Five stages. You can also present information on Create An Asset Inventory, Software Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Pam Cybersecurity Lifecycle For Securing Account Access
Pam Cybersecurity Lifecycle For Securing Account AccessThis slide represents lifecycle of PAM cybersecurity that assists companies to enhance their account protection by access management. It includes various steps such as defining, discovering, managing, protecting, monitoring, detecting abnormal usage, etc. Presenting our set of slides with Pam Cybersecurity Lifecycle For Securing Account Access. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Respond To Incidents, Detect Abnormal Usage, Manage Protect.
-
 Secure progress lifecycle example powerpoint shapes
Secure progress lifecycle example powerpoint shapesPresenting secure progress lifecycle example powerpoint shapes. This is a secure progress lifecycle example powerpoint shapes. This is five stage process. The stages in this process are plan and optimize, manage and operate, respond and educate, static analysis, dynamic analysis.
-
 Security lifecycle managing cyber risk in a digital age
Security lifecycle managing cyber risk in a digital ageIncrease audience engagement and knowledge by dispensing information using Security Lifecycle Managing Cyber Risk In A Digital Age. This template helps you present information on one stages. You can also present information on Security Lifecycle using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
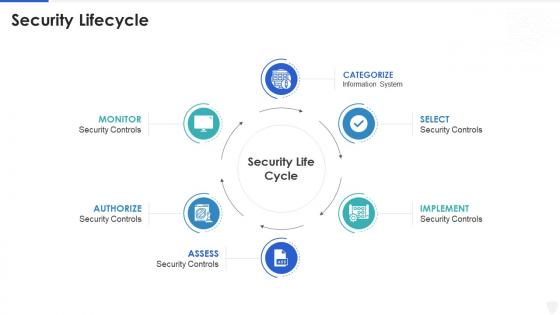
 Information Security Program Cybersecurity Management Security Lifecycle
Information Security Program Cybersecurity Management Security LifecycleIncrease audience engagement and knowledge by dispensing information using Information Security Program Cybersecurity Management Security Lifecycle. This template helps you present information on six stages. You can also present information on Categorize, Implement, Authorize using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity and digital business risk management security lifecycle
Cybersecurity and digital business risk management security lifecycleIntroducing Cybersecurity And Digital Business Risk Management Security Lifecycle to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Security Lifecycle, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Response Lifecycle
Cyber Security Incident Response LifecycleThis slide covers cyber security incident response lifecycle. It involves four phases such as preparation, detection, containment and post incident activity. Introducing our premium set of slides with name Cyber Security Incident Response Lifecycle. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Detection And Analysis, Preparation, Containment Eradication. So download instantly and tailor it with your information.
-
 Cyber Security Incident Response Lifecycle Model
Cyber Security Incident Response Lifecycle ModelThis slide covers cyber security incident response lifecycle model. It involves stages such as prepare, identify, eradicate, contain and recover. Introducing our Cyber Security Incident Response Lifecycle Model set of slides. The topics discussed in these slides are Identify, Contain, Eradicate, Digital Forensics. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Business Security Assurance And Maintenance Lifecycle
Business Security Assurance And Maintenance LifecycleThis slide covers business security assurance and maintenance lifecycle vulnerability management ,policy management and operational monitoring. Presenting our well structured Business Security Assurance And Maintenance Lifecycle. The topics discussed in this slide are Business Security, Assurance, Maintenance Lifecycle. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Incident Response Lifecycle Ppt Powerpoint Presentation Ideas Good
Cyber Security Incident Response Lifecycle Ppt Powerpoint Presentation Ideas GoodThis slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Introducing Cyber Security Incident Response Lifecycle Ppt Powerpoint Presentation Ideas Good to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Preparation, Containment Eradication, Detection And Analysis, using this template. Grab it now to reap its full benefits.
-
 Five Stage Security Policy Management Lifecycle
Five Stage Security Policy Management LifecycleFollowing slide includes five stage process for security policy management which can be used by businesses to improve communication across departments. It includes stages such as discover and visualize, plan and assess, migrate and deploy, maintain, and decommission. Introducing our premium set of slides with Five Stage Security Policy Management Lifecycle. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Discover And Visualize, Plan And Access, Migrate And Deploy. So download instantly and tailor it with your information.
-
 Cyber Security Incident Response Lifecycle Incident Response Strategies Deployment
Cyber Security Incident Response Lifecycle Incident Response Strategies DeploymentThis slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Present the topic in a bit more detail with this Cyber Security Incident Response Lifecycle Incident Response Strategies Deployment. Use it as a tool for discussion and navigation on Preparation, Activity, DetectionThis template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Response Lifecycle Development And Implementation Of Security Incident Management
Cyber Security Incident Response Lifecycle Development And Implementation Of Security Incident ManagementThis slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Introducing Cyber Security Incident Response Lifecycle Development And Implementation Of Security Incident Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Preparation, Detection Analysis, Containment Eradication Recovery, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Response Lifecycle Cyber Security Attacks Response Plan
Cyber Security Incident Response Lifecycle Cyber Security Attacks Response PlanThis slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response Lifecycle Cyber Security Attacks Response Plan. Dispense information and present a thorough explanation of Preparation, Detection And Analysis, Containment Eradication And Recovery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Response Lifecycle Deploying Computer Security Incident Management
Cyber Security Incident Response Lifecycle Deploying Computer Security Incident ManagementThis slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc.Introducing Cyber Security Incident Response Lifecycle Deploying Computer Security Incident Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Eradication Recovery, Post Incident Activity, Remove Malwares, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB Shadow It Management Lifecycle Overview
Cloud Access Security Broker CASB Shadow It Management Lifecycle OverviewThis slide outlines the lifecycle of shadow IT management for safely adopting cloud apps. The purpose of this slide is to showcase the various stages of the lifecycle, such as discovering shadow IT, knowing the risk level of apps, evaluating compliance, analyzing usage, governing cloud apps, and continuous monitoring. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB Shadow It Management Lifecycle Overview. This template helps you present information on six stages. You can also present information on Discover Shadow It, Continuous Monitoring, Govern Cloud Apps using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Seven staged network security lifecycle ppt slides
Seven staged network security lifecycle ppt slidesPresenting seven staged network security lifecycle ppt slides. This is a seven staged network security lifecycle ppt slides. This is a seven stage process. The stages in this process are security.
-
 Security management integration directory process composer lifecycle management
Security management integration directory process composer lifecycle managementPresenting this set of slides with name - Security Management Integration Directory Process Composer Lifecycle Management. This is an editable three stages graphic that deals with topics like Security Management, Integration Directory, Process Composer, Lifecycle Management to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Vulnerability management lifecycle risk security reporting monitoring
Vulnerability management lifecycle risk security reporting monitoringPresenting this set of slides with name - Vulnerability Management Lifecycle Risk Security Reporting Monitoring. This is a six stage process. The stages in this process are Vulnerability Management, Risk Management, Vulnerability Planning.
-
 Identity And Access Management Lifecycle In Cloud Security
Identity And Access Management Lifecycle In Cloud SecurityThis slide depicts access and identification management lifecycle in cloud computing systems. It provides information about user request, revoke access, approval, deletions, validations, etc. Presenting our set of slides with Identity And Access Management Lifecycle In Cloud Security. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identity And Access Management Lifecycle In Cloud Security.
-
 Saas security lifecycle ppt powerpoint presentation ideas layout cpb
Saas security lifecycle ppt powerpoint presentation ideas layout cpbPresenting this set of slides with name SAAS Security Lifecycle Ppt Powerpoint Presentation Ideas Layout Cpb. This is an editable Powerpoint four stages graphic that deals with topics like SAAS Security Lifecycle to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Organization security system development lifecycle
Organization security system development lifecyclePresenting this set of slides with name Organization Security System Development Lifecycle. This is a five stage process. The stages in this process are Logical Design, Analysis, Maintenance And Change, Deployment, Physical Design And Implementation, Preliminary Research, Identify Problems And Implement Changes, Track And Monitor Performance, Rolling Out Plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Security development lifecycle phases ppt presentation layouts topics cpb
Security development lifecycle phases ppt presentation layouts topics cpbPresenting this set of slides with name Security Development Lifecycle Phases Ppt Presentation Layouts Topics Cpb. This is an editable Powerpoint eight stages graphic that deals with topics like Security Development Lifecycle Phases to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Secure development lifecycle ppt powerpoint presentation icon display cpb
Secure development lifecycle ppt powerpoint presentation icon display cpbPresenting this set of slides with name Secure Development Lifecycle Ppt Powerpoint Presentation Icon Display Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Secure Development Lifecycle to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Secure development lifecycle agile ppt powerpoint presentation infographic template model cpb
Secure development lifecycle agile ppt powerpoint presentation infographic template model cpbPresenting Secure Development Lifecycle Agile Ppt Powerpoint Presentation Infographic Template Model Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Development Lifecycle Agile. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cloud secure data lifecycle ppt powerpoint presentation pictures inspiration cpb
Cloud secure data lifecycle ppt powerpoint presentation pictures inspiration cpbPresenting our Cloud Secure Data Lifecycle Ppt Powerpoint Presentation Pictures Inspiration Cpb PowerPoint template design. This PowerPoint slide showcases eight stages. It is useful to share insightful information on Cloud Secure Data Lifecycle This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security application lifecycle management ppt powerpoint presentation sample cpb
Security application lifecycle management ppt powerpoint presentation sample cpbPresenting our Security Application Lifecycle Management Ppt Powerpoint Presentation Sample Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Security Application Lifecycle Management This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Lifecycle security ppt powerpoint presentation summary cpb
Lifecycle security ppt powerpoint presentation summary cpbPresenting our Lifecycle Security Ppt Powerpoint Presentation Summary Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Lifecycle Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Asset management lifecycle security optimizing infrastructure using modern techniques ppt icons
Asset management lifecycle security optimizing infrastructure using modern techniques ppt iconsIntroducing Asset Management Lifecycle Security Optimizing Infrastructure Using Modern Techniques Ppt Icons to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Preventive Maintenance Planning, Planning Purchase, Asset Procurement Planning, Security, Technology, using this template. Grab it now to reap its full benefits.
-
 Steps For Information Security Program Lifecycle
Steps For Information Security Program LifecycleThis slide shows information security program steps to protect information that support operations and assets of program. It further includes steps such as identify, assess, design, implement protect and monitor. Presenting our set of slides with Steps For Information Security Program Lifecycle This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Malware Warnings, Security Program Lifecycle.



