Powerpoint Templates and Google slides for It Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Internet Gateway Security IT Steps To Select Next Generation Secure Web
Internet Gateway Security IT Steps To Select Next Generation Secure WebThis slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc. Introducing Internet Gateway Security IT Steps To Select Next Generation Secure Web to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Adopt Real Cloud Architecture, Decodes Apps And Cloud Services, Adapts To New Threats, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Swg Implementation Methodology Span Switched
Internet Gateway Security IT Swg Implementation Methodology Span SwitchedThis slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Introducing Internet Gateway Security IT Swg Implementation Methodology Span Switched to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Internet Gateway Rules, Deployment, Monitoring, Transparent Modes, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Table Of Contents
Internet Gateway Security IT Table Of ContentsIntroducing Internet Gateway Security IT Table Of Contents to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Secure Web Gateway Technology, Industries, using this template. Grab it now to reap its full benefits.
-
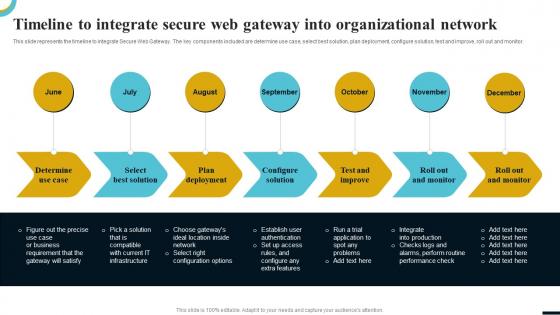 Internet Gateway Security IT Timeline To Integrate Secure Web Gateway
Internet Gateway Security IT Timeline To Integrate Secure Web GatewayThis slide represents the timeline to integrate Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Introducing Internet Gateway Security IT Timeline To Integrate Secure Web Gateway to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Determine Use Case, Select Best Solution, Plan Deployment, Configure Solution, Test And Improve, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Understanding Real World Use Cases Of Secure
Internet Gateway Security IT Understanding Real World Use Cases Of SecureThis slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. Introducing Internet Gateway Security IT Understanding Real World Use Cases Of Secure to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Real Time Web Traffic Surveillance, Blocking Of Harmful, Websites And Programs, Access Management, Rule Enforcement, On-Site And Remote Personnel, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Working Components Of Secure Web Gateway
Internet Gateway Security IT Working Components Of Secure Web GatewayThis slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc. Introducing Internet Gateway Security IT Working Components Of Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Traffic Inspection, URL Filtering, Application Control, Website Content Inspection, Secure Socket Layer SSL Inspection, using this template. Grab it now to reap its full benefits.
-
 Secure Web Gateway Implementation Internet Gateway Security IT
Secure Web Gateway Implementation Internet Gateway Security ITThis slide talks about explicit scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of explicit SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Introducing Secure Web Gateway Implementation Internet Gateway Security IT to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Manages Network Connection, Concentrates Most Sensitive, Protocols And Channels, Fewer Possible Disturbances Network, using this template. Grab it now to reap its full benefits.
-
 Secure Web Gateway Internet Gateway Security IT
Secure Web Gateway Internet Gateway Security ITThis slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Introducing Secure Web Gateway Internet Gateway Security IT to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Implement, Process And Manage, HTTP Traffic Connected, Internet, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Internet Gateway Security IT
Table Of Contents Internet Gateway Security ITIntroducing Table Of Contents Internet Gateway Security IT to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on SWG Budget And Training, Case Study And Use Cases, SWG Market And Trends, using this template. Grab it now to reap its full benefits.
-
 Hybrid It Cloud Server Security Architecture
Hybrid It Cloud Server Security ArchitectureFollowing slide showcases architecture of hybrid IT cloud server security, also including elements such as IAAS provider A,B,C, on premises, mergers and acquisitions, etc. Presenting our set of slides with Hybrid It Cloud Server Security Architecture. This exhibits information on fourstages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on On Premises, Mergers And Acquisitions, Security Architecture.
-
 It Infrastructure Management To Enhance Server Security
It Infrastructure Management To Enhance Server SecurityFollowing slide highlights enhancing server security with IT infrastructure management, also including server support, assistance of incidents, handling of issues, configuration oversight, etc. Introducing our premium set of slides with It Infrastructure Management To Enhance Server Security. Ellicudate the fourstages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Supervised Network Functions, Storage Management Solutions, Management Of Change. So download instantly and tailor it with your information.
-
 How Common Network Security Stacks Collaborate It
How Common Network Security Stacks Collaborate ItThis slide showcases the common network security stacks measures used for aligning information technology which helps an organization to provide enough web developers resources. It include details such as provide stateless protection devices, employ network traffic capabilities, etc. Introducing our premium set of slides with name How Common Network Security Stacks Collaborate It Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Provide Stateless, Protection Devices, Traffic Capabilities. So download instantly and tailor it with your information.
-
 Utilization Of Triage Cyber Security Process In It
Utilization Of Triage Cyber Security Process In ItThis slide represents utilization of triage cyber security process in IT which assists to handle large number of tickets and increases help desk efficiency. It includes utilization of triage cyber security process in IT such as IT operations, email, etc Presenting our set of slides with name Utilization Of Triage Cyber Security Process In It This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Software Testing, Agile Software Development, IT Operations
-
 Impact Of Patch Management On IT Security
Impact Of Patch Management On IT SecurityThis slide shows multiple potential results of deploying a patch management process in an organization. It includes regular security updates, feature updates, bug fixes, and prioritization. Presenting our set of slides with name Impact Of Patch Management On IT Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Updates, Features Updates, Bug Fixes.
-
 Shadow IT Management Lifecycle Overview CASB Cloud Security
Shadow IT Management Lifecycle Overview CASB Cloud SecurityThis slide outlines the lifecycle of shadow IT management for safely adopting cloud apps. The purpose of this slide is to showcase the various stages of the lifecycle, such as discovering shadow IT, knowing the risk level of apps, evaluating compliance, analyzing usage, governing cloud apps, and continuous monitoring. Introducing Shadow IT Management Lifecycle Overview CASB Cloud Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Evaluate Compliance, Govern Cloud Apps, Continuous Monitoring, Management Lifecycle Overview, using this template. Grab it now to reap its full benefits.
-
 Security Incidents And Mitigation Solutions In IT Industry
Security Incidents And Mitigation Solutions In IT IndustryThis slide highlights mitigation solutions to various types of security threats that disrupts business operations. The purpose of this slide is to help organizations in strengthening their network and data security system. It covers mitigation solutions such as detecting security incidents, assessing user account activity, etc. Presenting our set of slides with Security Incidents And Mitigation Solutions In IT Industry This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Insider Threats, Phishing Attacks, Viruses.
-
 Levels Of IT Infrastructure Security Framework
Levels Of IT Infrastructure Security FrameworkThis slide represents the types of IT infrastructure security framework. Its aim is to generate data to inform critical business decisions. This slide includes data, application, network and physical. Introducing our premium set of slides with Levels Of IT Infrastructure Security Framework. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Protect, Secure, Application. So download instantly and tailor it with your information.
-
 Types Of Threats In IT Infrastructure Security
Types Of Threats In IT Infrastructure SecurityThis slide showcases the common threats faced in infrastructure security. Its aim is to identify threats and eliminate them. This slide includes phishing, ransomware, botnet and physical theft. Presenting our set of slides with Types Of Threats In IT Infrastructure Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Infrastructure, Personal, Exploitation.
-
 Importance Of Cyber Security Policy For IT Organisation
Importance Of Cyber Security Policy For IT OrganisationThis slide covers the essential importance of a cybersecurity policy for IT organizations. The purpose of this template is to emphasize the role of a cybersecurity policy in safeguarding sensitive data, preventing cyber threats, ensuring regulatory adherence, and maintaining uninterrupted business operations. Introducing our premium set of slides with Importance Of Cyber Security Policy For IT Organisation Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Protection, Threat Mitigation, Regulatory Compliance. So download instantly and tailor it with your information.
-
 Security Gap Analysis Icon For IT Team
Security Gap Analysis Icon For IT TeamPresenting our set of slides with name Security Gap Analysis Icon For IT Team. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Gap Analysis Icon, IT Team.
-
 Card Payment Overview With Its Types Enhancing Transaction Security With E Payment
Card Payment Overview With Its Types Enhancing Transaction Security With E PaymentFollowing slide provides information about card payment methods which can be used by businesses for making daily business purchases and offers customers options for payment. It includes key components such as description and types of card payments. Deliver an outstanding presentation on the topic using this Card Payment Overview With Its Types Enhancing Transaction Security With E Payment Dispense information and present a thorough explanation of Credit Card, Debit Card, Services Purchase using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security In IT Industry Icon
Cyber Security In IT Industry IconIntroducing our premium set of slides with Cyber Security In IT Industry Icon. Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security In IT Industry Icon. So download instantly and tailor it with your information.
-
 Implementing Effective Tokenization Existing IT Security Infrastructure Threats
Implementing Effective Tokenization Existing IT Security Infrastructure ThreatsThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. Present the topic in a bit more detail with this Implementing Effective Tokenization Existing IT Security Infrastructure Threats. Use it as a tool for discussion and navigation on Compliance Challenges, Resource Intensiveness, Faced Security Vulnerabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Training Schedule For IT Teams
Application Security Training Schedule For IT TeamsThis slide represents the training schedule for IT teams in an organization to efficiently implementing application security. Deliver an outstanding presentation on the topic using this Application Security Training Schedule For IT Teams. Dispense information and present a thorough explanation of Application Security Fundamentals, Application Security Deployment, Application Security Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Existing IT Security Strategic Implementation Of Regression Testing
Existing IT Security Strategic Implementation Of Regression TestingThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. These constituents are vulnerability scanners, improper functioning, functional disrupt, and so on. Deliver an outstanding presentation on the topic using this Existing IT Security Strategic Implementation Of Regression Testing. Dispense information and present a thorough explanation of Existing IT Security, Infrastructure Constituents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Major Web Based Software Security Challenges For It Department
Major Web Based Software Security Challenges For It DepartmentThis slide showcases some SaaS security challenges faced by IT team to plan mitigation actions. This includes file security, insider threats and imposing minimum privilege access. Presenting our set of slides with Major Web Based Software Security Challenges For It Department. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on File Security, Insider Threat, Minimum Privilege Access.
-
 Application Security Implementation Plan Existing IT Security Infrastructure Threats
Application Security Implementation Plan Existing IT Security Infrastructure ThreatsThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Existing IT Security Infrastructure Threats. Dispense information and present a thorough explanation of Broken Authentication, Cross Site Scripting, Denial Of Service, Infrastructure Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Statistics Of It Infrastructure Attacks On Organization
Application Security Implementation Plan Statistics Of It Infrastructure Attacks On OrganizationThis slide summarizes security attacks across different organizational departments, such as IT, HR, Sales, Finance, etc. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Statistics Of IT Infrastructure Attacks On Organization. Dispense information and present a thorough explanation of Statistics Of IT Infrastructure, Attacks On Organization, Organizational Departments, Finance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Endpoint Security Endpoint Security Training Schedule For It Teams
Endpoint Security Endpoint Security Training Schedule For It TeamsThis slide represents the training schedule for IT teams in an organization to efficiently implementing endpoint security. Present the topic in a bit more detail with this Endpoint Security Endpoint Security Training Schedule For IT Teams. Use it as a tool for discussion and navigation on Endpoint Security Fundamentals, Endpoint Security Protocols, Device Environment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Training Schedule For It Teams To Conduct Tokenization
Tokenization For Improved Data Security Training Schedule For It Teams To Conduct TokenizationThis slide represents the training schedule for IT teams in an organization to efficiently carry out tokenization. It includes the time slots for training, total days of training, and the modules to be covered in the training. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Training Schedule For IT Teams To Conduct Tokenization. Dispense information and present a thorough explanation of Tokenization Implementation, Tokenization Architecture, Tokenization Fundamentals using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Application Security Training Program For IT Team
Application Security Implementation Plan Application Security Training Program For IT TeamThis slide highlights the comprehensive training program for software testers which aims to train beginners about application security. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Application Security Training Program For IT Team. Dispense information and present a thorough explanation of Understanding Functionalities, Application Security, Training Program using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Existing It Security Infrastructure Constituent Vpn Implementation Plan
Existing It Security Infrastructure Constituent Vpn Implementation PlanThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns.Deliver an outstanding presentation on the topic using this Existing It Security Infrastructure Constituent Vpn Implementation Plan. Dispense information and present a thorough explanation of Constituent, Problems Observed, Incidents Observed using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Physical Security Control Methods And Its Functions
Physical Security Control Methods And Its FunctionsThis slide showcases security control system types that are physical, technical and administrative controls. These help to prevent unauthorized access, maintain confidentiality, etc. Introducing our premium set of slides with Physical Security Control Methods And Its Functions. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Physical Controls, Technical Controls, Administrative Controls. So download instantly and tailor it with your information.
-
 Major Incident Details Related To It Failure Business Recovery Plan To Overcome Cyber Security Threat
Major Incident Details Related To It Failure Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about cyber attack incidents. It includes information about incident date, impact, and incident information comprising loss of customer name, address, phone number, birth date, etc. Increase audience engagement and knowledge by dispensing information using Major Incident Details Related To It Failure Business Recovery Plan To Overcome Cyber Security Threat. This template helps you present information on three stages. You can also present information on Ransomware, Information, Cyber Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Approaches For IT And OT Cyber Security Convergence
Approaches For IT And OT Cyber Security ConvergenceIntroducing our premium set of slides with Approaches For IT And OT Cyber Security Convergence Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Understand Unique Needs, Select Right Technology Blend, Team Collaboration So download instantly and tailor it with your information.
-
 OT Cyber Security Training Schedule For It Employees
OT Cyber Security Training Schedule For It EmployeesThis slide represents training plan that assist companies to educate their IT employee for enhancing operational technology cyber security effectively. It includes various elements such as course, details, timings, modules, mode, etc. Introducing our OT Cyber Security Training Schedule For It Employees set of slides. The topics discussed in these slides are Details, Timings, ModulesThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Agenda IT Security Awareness Training Program Cybersecurity SS
Agenda IT Security Awareness Training Program Cybersecurity SSIntroducing Agenda IT Security Awareness Training Program Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Financial Resources, Resilient Environment, Security Awareness, Training Program, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Minimizing Risks Of Insider Threats IT Security Awareness Training Cybersecurity SS
Best Practices For Minimizing Risks Of Insider Threats IT Security Awareness Training Cybersecurity SSThis slide represents best practices for mitigating threats that originate from within the targeted organization. It includes best practices such as perform enterprise-wide risk assessment etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Minimizing Risks Of Insider Threats IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Enforce Policies And Controls, Establish Physical Security, Harden Network Perimeter Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Budget Plan For IT Security Awareness Training Program Cybersecurity SS
Budget Plan For IT Security Awareness Training Program Cybersecurity SSThis slide represents the budget prepared to predict cash flows and allocate required resources for IT security awareness training program. It includes parameters such as mooc courses etc. Deliver an outstanding presentation on the topic using this Budget Plan For IT Security Awareness Training Program Cybersecurity SS. Dispense information and present a thorough explanation of External Trainers Fee, Ransomware Management, Social Engineering Management, Password Authentication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Ensure Effective Completion Of IT Security Awareness Training Cybersecurity SS
Checklist To Ensure Effective Completion Of IT Security Awareness Training Cybersecurity SSThis slide represents checklist for promoting strategy adopted by security professionals for preventing and mitigating cyber security risks. It includes activities such as gain executive buy-in etc. Present the topic in a bit more detail with this Checklist To Ensure Effective Completion Of IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Organizational Activities, Security Awareness Training, Ensure Effective Completion. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of IT Security Awareness Training Tools Cybersecurity SS
Comparative Assessment Of IT Security Awareness Training Tools Cybersecurity SSThis slide represents comparison between IT security awareness training tools based on features such as audio mixing, text animation, time mapping, titles and captions etc. Deliver an outstanding presentation on the topic using this Comparative Assessment Of IT Security Awareness Training Tools Cybersecurity SS. Dispense information and present a thorough explanation of Time Mapping, Text Animation, Tram Reviews, Security Awareness Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
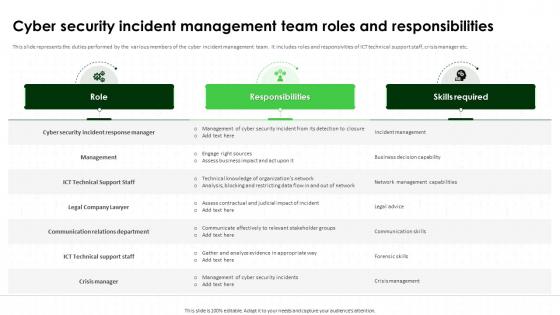 Cyber Security Incident Management Team Roles IT Security Awareness Training Cybersecurity SS
Cyber Security Incident Management Team Roles IT Security Awareness Training Cybersecurity SSThis slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. Deliver an outstanding presentation on the topic using this Cyber Security Incident Management Team Roles IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Cyber Security Incident Response, Management, Roles And Responsibilities, Network Management Capabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
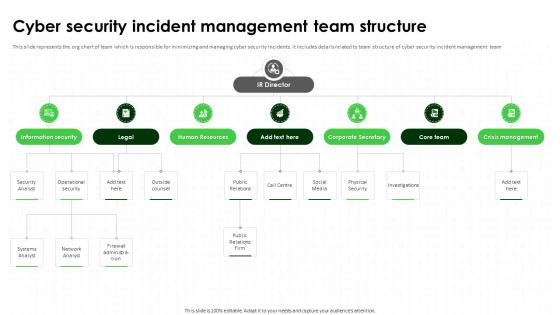 Cyber Security Incident Management Team Structure IT Security Awareness Training Cybersecurity SS
Cyber Security Incident Management Team Structure IT Security Awareness Training Cybersecurity SSThis slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Team Structure IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Cyber Security Incident, Management Team Structure, Managing Cyber Security Incidents using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Essential Components Of Effective IT Security Awareness Training Program Cybersecurity SS
Essential Components Of Effective IT Security Awareness Training Program Cybersecurity SSThis slide represents essential elements for developing training program which helps to mitigate cyber security risks. It include components such as educational content, testing etc. Introducing Essential Components Of Effective IT Security Awareness Training Program Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Educational Content, Metrics And Reporting, Testing, Security Awareness Training Program, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For IT Security Awareness Training Program Cybersecurity SS
Icons Slide For IT Security Awareness Training Program Cybersecurity SSIntroducing our well researched set of slides titled Icons Slide For IT Security Awareness Training Program Cybersecurity SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Impact Of Cyber Attacks On Organizational Operations IT Security Awareness Training Cybersecurity SS
Impact Of Cyber Attacks On Organizational Operations IT Security Awareness Training Cybersecurity SSThis slide represents impact of attacks that are attempted to steal sensitive information in the form of user names, credit card numbers etc. on organizational operations. Increase audience engagement and knowledge by dispensing information using Impact Of Cyber Attacks On Organizational Operations IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Reputational Damage, Stolen Intellectual Property, Operational Disruption, Increased Costs using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Insider Threats Awareness Training Program IT Security Awareness Training Cybersecurity SS
Insider Threats Awareness Training Program IT Security Awareness Training Cybersecurity SSThis slide represents details related to training program for mitigating threats that arises from within the targeted organization. It includes details related to mode of training, key learnings etc. Introducing Insider Threats Awareness Training Program IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Insider Threats Awareness, Training Program, Key Learnings, Mitigating Threats, using this template. Grab it now to reap its full benefits.
-
 IT Security Awareness Training Defense Against Cyber Threats Cybersecurity SS
IT Security Awareness Training Defense Against Cyber Threats Cybersecurity SSThis slide represents details related to ways security awareness training helps in preventing and mitigating common threats faced by organization such as data breaches, phishing attacks etc. Deliver an outstanding presentation on the topic using this IT Security Awareness Training Defense Against Cyber Threats Cybersecurity SS. Dispense information and present a thorough explanation of Data Breaches, Phishing Attacks, Insider Threats, Social Engineering using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Security Awareness Training Executive Dashboard Cybersecurity SS
IT Security Awareness Training Executive Dashboard Cybersecurity SSThis slide represents dashboard to analyze effectiveness strategy implemented by security professionals for preventing and mitigating cyber security risks. It includes KPIs such as training completion rate etc. Present the topic in a bit more detail with this IT Security Awareness Training Executive Dashboard Cybersecurity SS. Use it as a tool for discussion and navigation on Training Completion Rate, Training Time, Email Report Rate, Executive Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Security Awareness Training Program Implementing Table Of Contents Cybersecurity SS
IT Security Awareness Training Program Implementing Table Of Contents Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using IT Security Awareness Training Program Implementing Table Of Contents Cybersecurity SS. This template helps you present information on one stages. You can also present information on Phishing Awareness, Objectives, Detecting Phishing Attacks, Preventing Phishing Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Objectives Of Cloud Security Training Program IT Security Awareness Training Cybersecurity SS
Objectives Of Cloud Security Training Program IT Security Awareness Training Cybersecurity SSThis slide represents goals of providing training related to set of measures which protects data stored online from theft, leakage and detection. It includes objectives such as understanding identity and access management practices etc. Introducing Objectives Of Cloud Security Training Program IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Providers And Customers, Frameworks And Architecture Models, Cloud Environment, using this template. Grab it now to reap its full benefits.
-
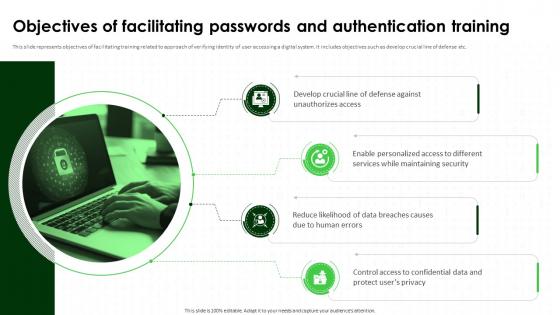 Objectives Of Facilitating Passwords IT Security Awareness Training Cybersecurity SS
Objectives Of Facilitating Passwords IT Security Awareness Training Cybersecurity SSThis slide represents objectives of facilitating training related to approach of verifying identity of user accessing a digital system. It includes objectives such as develop crucial line of defense etc. Increase audience engagement and knowledge by dispensing information using Objectives Of Facilitating Passwords IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Enable Personalized Access, Confidential Data And Protect, Authentication Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Objectives Of Implementing Anti Phishing Training IT Security Awareness Training Cybersecurity SS
Objectives Of Implementing Anti Phishing Training IT Security Awareness Training Cybersecurity SSThis slide represents details related to need of implementing training program for employees regarding attacks that are attempted to steal sensitive information in the form of user names, credit card numbers etc. Introducing Objectives Of Implementing Anti Phishing Training IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Anti Phishing Training Program, Steal Sensitive Information, Employees Regarding Attacks, using this template. Grab it now to reap its full benefits.
-
 Objectives Of Insider Threats Awareness Training IT Security Awareness Training Cybersecurity SS
Objectives Of Insider Threats Awareness Training IT Security Awareness Training Cybersecurity SSThis slide represents objectives of providing training for mitigating treats that originates from within the targeted organization. It includes objectives such as identify and report behaviors of insider threats etc. Increase audience engagement and knowledge by dispensing information using Objectives Of Insider Threats Awareness Training IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Unintentional Insider Threats, Malicious Or Unintentional Insider, Public And National Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
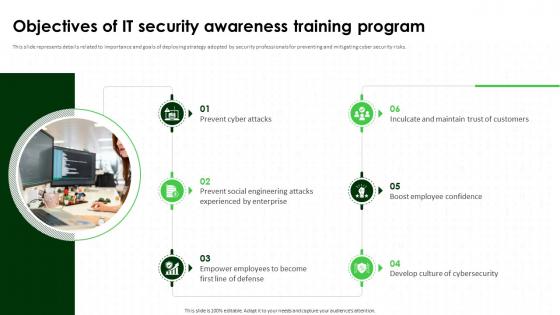 Objectives Of IT Security Awareness Training Program Cybersecurity SS
Objectives Of IT Security Awareness Training Program Cybersecurity SSThis slide represents details related to importance and goals of deploying strategy adopted by security professionals for preventing and mitigating cyber security risks. Introducing Objectives Of IT Security Awareness Training Program Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Develop Culture Of Cybersecurity, Boost Employee Confidence, Prevent Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Objectives Of Ransomware Awareness Training Program IT Security Awareness Training Cybersecurity SS
Objectives Of Ransomware Awareness Training Program IT Security Awareness Training Cybersecurity SSThis slide represents goals of providing training related to malware that is designed to deny a user or organization access to files on their computer or networks. Increase audience engagement and knowledge by dispensing information using Objectives Of Ransomware Awareness Training Program IT Security Awareness Training Cybersecurity SS. This template helps you present information on three stages. You can also present information on Objectives Of Ransomware Awareness, Training Program, Computer Or Networks, Goals Of Providing Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Objectives Of Social Engineering Awareness Program IT Security Awareness Training Cybersecurity SS
Objectives Of Social Engineering Awareness Program IT Security Awareness Training Cybersecurity SSThis slide represents objectives for facilitating training related to cybercrime which involves tracking a target into giving money or data. It includes objectives such as implementing strategies for mitigating personnel attacks etc. Introducing Objectives Of Social Engineering Awareness Program IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering Attacks, Prevent Data Breaches, Procedures For Defeating Deceptions, using this template. Grab it now to reap its full benefits.
-
 Overview IT Security Awareness Training Modules Cybersecurity SS
Overview IT Security Awareness Training Modules Cybersecurity SSThis slide represents overview of training modules to be facilitated to organizational employees for effectively understanding, preventing and mitigating cyber security risks. Increase audience engagement and knowledge by dispensing information using Overview IT Security Awareness Training Modules Cybersecurity SS. This template helps you present information on six stages. You can also present information on Social Engineering, Insider Threats Awareness, Cloud Security, Ransomware Awareness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Robust Password Management Training For End Users IT Security Awareness Training Cybersecurity SS
Robust Password Management Training For End Users IT Security Awareness Training Cybersecurity SSThis slide represents training plan for robust management of verifying identity of user accessing a digital system. It includes details related to training modules such as beyond passwords etc. Present the topic in a bit more detail with this Robust Password Management Training For End Users IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Beyond Passwords, Multi Factor Authentication, Password Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps For Creating Effective IT Security Awareness Training Program Cybersecurity SS
Steps For Creating Effective IT Security Awareness Training Program Cybersecurity SSThis slide represents procedure for developing training program which helps to mitigate cyber security risks. It include steps such as identify risks, change behavior etc. Increase audience engagement and knowledge by dispensing information using Steps For Creating Effective IT Security Awareness Training Program Cybersecurity SS. This template helps you present information on five stages. You can also present information on Change Behavior, Identify Risks, Security Awareness, Training Program, Track Metrics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





