Powerpoint Templates and Google slides for It Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Types Of Cyber Security Measures To Safeguard It Infrastructure
Types Of Cyber Security Measures To Safeguard It InfrastructureThis slide depicts the kinds of cyber security approaches to safeguard companys IT infrastructure. The purpose of this slide is to help the business improve its cybersecurity measures in order to prevent online attacks. It includes operational security, network security, etc. Introducing our premium set of slides with Types Of Cyber Security Measures To Safeguard It Infrastructure Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Operational Security, Information Security, Network Security So download instantly and tailor it with your information.
-
 Devsecops Best Practices For Secure Characteristics Of Strong Devsecops Program In It
Devsecops Best Practices For Secure Characteristics Of Strong Devsecops Program In ItThis slide discusses the features adopted for a strong DevSecOps program. The purpose of this slide is to explain the various characteristics these are security awareness and ownership, automated operations, wide scope, shift-left and shift-right, etc. Increase audience engagement and knowledge by dispensing information using Devsecops Best Practices For Secure Characteristics Of Strong Devsecops Program In It. This template helps you present information on six stages. You can also present information on Automated Operations, Security Awareness And Ownership, Developer Acceptance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devsecops Best Practices For Secure IT Ops Responsibilities In Devsecops Model
Devsecops Best Practices For Secure IT Ops Responsibilities In Devsecops ModelThis slide highlights the IT operation responsibility in DevSecOps. The purpose of this slide is to discuss the IT responsibilities these are implementing infrastructure as code to create consistent and traceable resources and so on. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure IT Ops Responsibilities In Devsecops Model. Dispense information and present a thorough explanation of Consistent And Traceable Resources, Configuration Management Tools, Incorporate Security Measures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Advantages Of Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age It
Advantages Of Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age ItThis slide outlines the benefits of utilizing Hypertext Transfer Protocol Secure HTTPS for website encryption. The advantages discussed in this slide are secure interaction, data integrity, privacy and security, better performance, user experience, etc. Introducing Advantages Of Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Secure Interaction, Data Integrity, Better Performance, using this template. Grab it now to reap its full benefits.
-
 Advantages Of Quantum Cryptography To Secure Data Encryption For Data Privacy In Digital Age It
Advantages Of Quantum Cryptography To Secure Data Encryption For Data Privacy In Digital Age ItThis slide demonstrates the benefits of quantum encryption technique. The advantages discussed in this slide are provides secure communication, detects eavesdropping, several methods for security, provides perfect secrecy and future proof. Present the topic in a bit more detail with this Advantages Of Quantum Cryptography To Secure Data Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Quantum, Cryptography, Data Transmission. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Benefits Of Internet Protocol Security Encryption For Data Privacy In Digital Age It
Benefits Of Internet Protocol Security Encryption For Data Privacy In Digital Age ItThis slide demonstrates the advantages and disadvantages of Internet protocol Security IPsec technology. The various benefits explained in this slide are strong security, broad compatibility, flexibility, scalability and efficient network performance. Deliver an outstanding presentation on the topic using this Benefits Of Internet Protocol Security Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Key Management, Performance Impact, Compatibility Issues using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Characteristics Of Internet Protocol Security Technique Encryption For Data Privacy In Digital Age It
Characteristics Of Internet Protocol Security Technique Encryption For Data Privacy In Digital Age ItThis slide demonstrates the various features of Internet Protocol Security IPsec mechanism. The properties of IPsec include authentication, privacy, integrity, key management, tunnelling, flexibility and interoperability. Introducing Characteristics Of Internet Protocol Security Technique Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Key Management, Interoperability, using this template. Grab it now to reap its full benefits.
-
 Emerging Trends In Cryptographic Cloud Security Encryption For Data Privacy In Digital Age It
Emerging Trends In Cryptographic Cloud Security Encryption For Data Privacy In Digital Age ItThis slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc. Introducing Emerging Trends In Cryptographic Cloud Security Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Homomorphic Encryption, Quantum Safe Cryptography, Secure Multi Party Computation, using this template. Grab it now to reap its full benefits.
-
 Encryption Adaptability To Tackle Recent Security Challenges Encryption For Data Privacy In Digital Age It
Encryption Adaptability To Tackle Recent Security Challenges Encryption For Data Privacy In Digital Age ItThis slide discusses about the increasing adoption of encryption to solve current cyber security issues. The key points discussed are more use of cloud encryption in banking sector, introduction of homomorphic encryption, increase in BYOE adoption, etc. Increase audience engagement and knowledge by dispensing information using Encryption Adaptability To Tackle Recent Security Challenges Encryption For Data Privacy In Digital Age It. This template helps you present information on five stages. You can also present information on Homomorphic, Encryption, Introduction using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age It
Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc. Introducing Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Data Protection, Poor Key Management, Software Engineers, using this template. Grab it now to reap its full benefits.
-
 Introduction To Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age It
Introduction To Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age ItThis slide talks about the Hypertext Transfer Protocol Secure HTTPS, which is an advance version of HTTP. The purpose of this slide is to discuss the importance of using HTTPS to encrypt communication between browser and server. Present the topic in a bit more detail with this Introduction To Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Introduction, Overview, Protocol Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Components Of Internet Protocol Security Encryption For Data Privacy In Digital Age It
Key Components Of Internet Protocol Security Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to discuss the main components of Internet Protocol Security IPsec architecture. These three components are Encapsulating Security Payload ESP, Authentication Header AH, and Internet Key Exchange IKE. Deliver an outstanding presentation on the topic using this Key Components Of Internet Protocol Security Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Authentication Header, Internet Key Exchange, Encapsulating Security Payload using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Relationship Between Byoe And Hardware Security Module Encryption For Data Privacy In Digital Age It
Relationship Between Byoe And Hardware Security Module Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to highlight the benefits and capabilities of Hardware Security Modules HSMs. The key components included are cloud server, private key, encrypted request, encrypted data, HSM isolated environment, etc. Deliver an outstanding presentation on the topic using this Relationship Between Byoe And Hardware Security Module Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Relationship, Hardware, Cryptographic using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age It
Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the role of HTTPS in encrypting web communication and use of the Secure Sockets Layer SSL protocol for secure connections. This slide also discusses the incorporation of symmetric and asymmetric encryption during the SSL handshake. Deliver an outstanding presentation on the topic using this Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Technology, Asymmetric, Symmetric using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps Followed By Internet Protocol Security Connections Encryption For Data Privacy In Digital Age It
Steps Followed By Internet Protocol Security Connections Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to outline the working steps of Internet Protocol Security connections. These are key exchange, packet headers and trailers, packet authentication, encryption, data transmission and decryption of data packets. Deliver an outstanding presentation on the topic using this Steps Followed By Internet Protocol Security Connections Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Connections, Protocol Security, Data Transmission using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tunnel And Transport Modes Of Internet Protocol Security Encryption For Data Privacy In Digital Age It
Tunnel And Transport Modes Of Internet Protocol Security Encryption For Data Privacy In Digital Age ItThis slide talks about the distinction between the two methods of protecting information transmission. The purpose of this slide is to explain the concepts of transport mode and tunnel mode in the context of securing data during communication. Present the topic in a bit more detail with this Tunnel And Transport Modes Of Internet Protocol Security Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Transport Mode, Protocol Security, Transmission. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Of Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age It
Working Of Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age ItThis slide illustrates the flow of several components in the working of Hypertext Transfer Protocol Secure HTTPS. The purpose of this slide is to showcase how data is encrypted in transit and transferred to the user using public and private keys. Present the topic in a bit more detail with this Working Of Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Asymmetric Encryption, Symmetric Encryption, Transmission. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Factors Affecting Security Compliance In It Audit
Factors Affecting Security Compliance In It AuditFollowing slide showcases factors in IT audit that affect security compliance for risk mitigation. It further covers factors such as logical and physical security, regulatory compliance and hardware. Introducing our premium set of slides with Factors Affecting Security Compliance In It Audit. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Physical Security, Regulatory Compliance, Management System. So download instantly and tailor it with your information.
-
 Implementing Effective Software Testing Existing IT Security Infrastructure Constituents
Implementing Effective Software Testing Existing IT Security Infrastructure ConstituentsThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. These constituents are regulatory and compliance, budget, complex integration, and so on. Present the topic in a bit more detail with this Implementing Effective Software Testing Existing IT Security Infrastructure Constituents. Use it as a tool for discussion and navigation on Complex Integration, Strict Compliance Requirements, Functional Disrupt, IT Security Infrastructure Constituents. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda For Internet Gateway Security IT
Agenda For Internet Gateway Security ITIntroducing Agenda For Internet Gateway Security IT to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Global Market Analysis, Remote Worker Protection, Integrate Secure Web Gateway, Technologies, using this template. Grab it now to reap its full benefits.
-
 Comparison Between Secure Web Internet Gateway Security IT
Comparison Between Secure Web Internet Gateway Security ITThis slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. Present the topic in a bit more detail with this Comparison Between Secure Web Internet Gateway Security IT. Use it as a tool for discussion and navigation on Parameter, Scope, Deployment, Architecture, Features, Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide For Internet Gateway Security IT
Icons Slide For Internet Gateway Security ITIntroducing our well researched set of slides titled Icons Slide For Internet Gateway Security IT. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
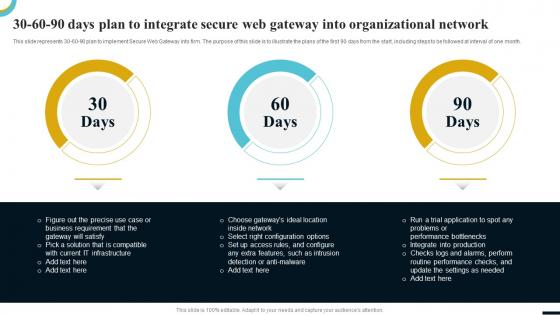 Internet Gateway Security IT 30 60 90 Days Plan To Integrate Secure Web
Internet Gateway Security IT 30 60 90 Days Plan To Integrate Secure WebThis slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Introducing Internet Gateway Security IT 30 60 90 Days Plan To Integrate Secure Web to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on 30 60 90 Days Plan, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Applications Of Secure Web Gateway In Various
Internet Gateway Security IT Applications Of Secure Web Gateway In VariousThis slide talks about how Secure Web Gateway is used in several industrial domains. The purpose of this slide is to explain how SWG is used in different sectors. The industries covered are financial services, healthcare, education, manufacturing, etc. Introducing Internet Gateway Security IT Applications Of Secure Web Gateway In Various to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Financial Services, Healthcare, Education, Manufacturing, Government, Retail, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Architecture Of Citrix Secure Web Gateway
Internet Gateway Security IT Architecture Of Citrix Secure Web GatewayThis slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Architecture Of Citrix Secure Web Gateway. Use it as a tool for discussion and navigation on Citrix ADC Appliance, URL Filtering, Policies, Citrix Application Delivery Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Before Vs After Implementing Secure Web
Internet Gateway Security IT Before Vs After Implementing Secure WebThis slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Before Vs After Implementing Secure Web. Use it as a tool for discussion and navigation on Security, Visibility, Compliance, Productivity, Costs. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Best Practices For Secure Web Gateway
Internet Gateway Security IT Best Practices For Secure Web GatewayThis slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. Introducing Internet Gateway Security IT Best Practices For Secure Web Gateway to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Perform A Risk Assessment, Deploy Safe Setups, Monitor And Analyse Traffic, Keep Software Up To Date, Provide User Awareness Training, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Case Study Citrix Solutions To Safeguard
Internet Gateway Security IT Case Study Citrix Solutions To SafeguardThis slide depicts the services offered by Citrix solutions to protect networks from web-based threats. These are comprehensive SWG, more private architecture based on instances and cloud delivery. This slide also talks about the benefits of SWG to IT directors. Introducing Internet Gateway Security IT Case Study Citrix Solutions To Safeguard to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Comprehensive SWG, Cloud Delivery, Secure Web Gateway Services, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Checklist To Implement Secure Web Gateway
Internet Gateway Security IT Checklist To Implement Secure Web GatewayThis slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Present the topic in a bit more detail with this Internet Gateway Security IT Checklist To Implement Secure Web Gateway. Use it as a tool for discussion and navigation on Determine Use Case, Select Best Solution, Plan Deployment, Configure Solution, Test And Improve, Roll Out And Monitor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Comparison Between Secure Web Gateway
Internet Gateway Security IT Comparison Between Secure Web GatewayThis slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment. Present the topic in a bit more detail with this Internet Gateway Security IT Comparison Between Secure Web Gateway. Use it as a tool for discussion and navigation on Function, Scope, Granularity, Features, Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Current Trends Enhancing Performance
Internet Gateway Security IT Current Trends Enhancing PerformanceThis slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc. Introducing Internet Gateway Security IT Current Trends Enhancing Performance to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Based SWG, Advanced Threat Protection, User Behavior Analytics, Secure Access Service Edge, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Different Types Of Secure Web Gateway
Internet Gateway Security IT Different Types Of Secure Web GatewayThis slide demonstrates the various kinds of SWG deployments. The purpose of this slide is to explain the different types of Secure Web Gateway deployment methods such as on-premises deployment, cloud-based deployment and hybrid deployment. Introducing Internet Gateway Security IT Different Types Of Secure Web Gateway to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on On Premises Deployment, CLOUD Based Deployment, Hybrid Deployment, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Estimated Budget Of Secure Web Gateway
Internet Gateway Security IT Estimated Budget Of Secure Web GatewayThis slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Estimated Budget Of Secure Web Gateway. Use it as a tool for discussion and navigation on Hardware And Software, Maintenance And Support, Training, Third Party Services, Deployment Team. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Features Of Next Generation Secure Web
Internet Gateway Security IT Features Of Next Generation Secure WebThis slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc. Introducing Internet Gateway Security IT Features Of Next Generation Secure Web to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Based Architecture, More Visibility And Control, Advanced Threat Intelligence, Multi-Factor Authentication, Integrated Data Loss Prevention, Zero Trust Security, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Future Of Secure Web Gateway Technology
Internet Gateway Security IT Future Of Secure Web Gateway TechnologyThis slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. Introducing Internet Gateway Security IT Future Of Secure Web Gateway Technology to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Sales Are Predicted, SWG Market Anticipated, Security Solution, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Impact Of Secure Web Gateway On Application
Internet Gateway Security IT Impact Of Secure Web Gateway On ApplicationThis slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Impact Of Secure Web Gateway On Application. Use it as a tool for discussion and navigation on Parameters, Content Filtering, Policy Enforcement, Data Loss Prevention. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Importance Of Secure Web Gateway For Businesses
Internet Gateway Security IT Importance Of Secure Web Gateway For BusinessesThis slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc. Introducing Internet Gateway Security IT Importance Of Secure Web Gateway For Businesses to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Client Connector, Data Center, Iot Headquarters, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Industry Wise Market Segmentation Of Swg
Internet Gateway Security IT Industry Wise Market Segmentation Of SwgThis slide demonstrates the contribution of different industries in growth of Secure Web Gateway market. The purpose of this slide is to represent the industry wise market share of different sectors such as BFSI, IT and telecom, retail and e-Commerce, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Industry Wise Market Segmentation Of Swg. Use it as a tool for discussion and navigation on Global, Retail And E-Commerce Sectors, Market, IT And Telecom Industries. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Integration Of Swg Inside Sase Architecture
Internet Gateway Security IT Integration Of Swg Inside Sase ArchitectureThis slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. Introducing Internet Gateway Security IT Integration Of Swg Inside Sase Architecture to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Web Sites, Cloud Apps, Private Cloud, Corporate Datacenter, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Introduction To Next Generation Secure Web
Internet Gateway Security IT Introduction To Next Generation Secure WebThis slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. Introducing Internet Gateway Security IT Introduction To Next Generation Secure Web to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Applications, Services, Risks Enabled, Vulnerability, Public Resources, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Introduction To Secure Web Gateway Technology
Internet Gateway Security IT Introduction To Secure Web Gateway TechnologyThis slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Introducing Internet Gateway Security IT Introduction To Secure Web Gateway Technology to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Traffic Inspection, Application Control, Website Content Inspection, Data Loss Prevention, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Key Benefits Of Using Secure Web Gateway
Internet Gateway Security IT Key Benefits Of Using Secure Web GatewayThis slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc. Introducing Internet Gateway Security IT Key Benefits Of Using Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Improved Security, Increased Productivity, Reduced Risk Of Data Loss, Compliance, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Key Growth Drivers Of Next Generation
Internet Gateway Security IT Key Growth Drivers Of Next GenerationThis slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market. Introducing Internet Gateway Security IT Key Growth Drivers Of Next Generation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Growing Cloud Applications, Services, Rising Data Theft And Vulnerability, Cloud Dominated World, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Key Secure Web Gateway Solution Providers
Internet Gateway Security IT Key Secure Web Gateway Solution ProvidersThis slide outlines the popular service providers of Secure Wen Gateway. The purpose of this slide is to demonstrate the services provided by various SWG solutions such as Cisco, Symantec, McAfee, Zscaler, Barracuda Networks, Fortinet, etc. Introducing Internet Gateway Security IT Key Secure Web Gateway Solution Providers to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Cisco, Symantec, Forcepoint, Fortinet, Barracuda Networks, using this template. Grab it now to reap its full benefits.
-
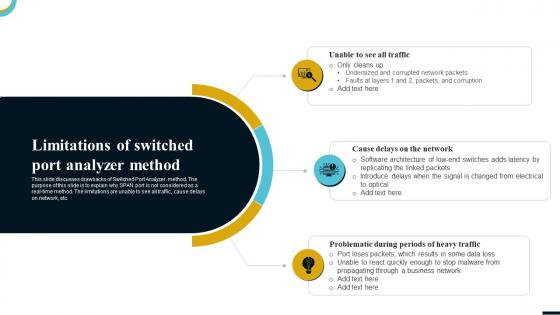 Internet Gateway Security IT Limitations Of Switched Port Analyzer Method
Internet Gateway Security IT Limitations Of Switched Port Analyzer MethodThis slide discusses drawbacks of Switched Port Analyzer method. The purpose of this slide is to explain why SPAN port is not considered as a real-time method. The limitations are unable to see all traffic, cause delays on network, etc. Introducing Internet Gateway Security IT Limitations Of Switched Port Analyzer Method to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Unable To See All Traffic, Cause Delays On The Network, Problematic During Periods Heavy Traffic, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Methods To Implement Security Policies
Internet Gateway Security IT Methods To Implement Security PoliciesThis slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Methods To Implement Security Policies. Use it as a tool for discussion and navigation on Data Loss Prevention, Encrypted Traffic Examination, Protocol Support, Constant Security Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Prominent Users Of Secure Web Gateway
Internet Gateway Security IT Prominent Users Of Secure Web GatewayThis slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc. Introducing Internet Gateway Security IT Prominent Users Of Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on IT Security Experts, Network Administrators, Compliance Officers, HR Managers, Business Executives, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Reasons Behind Need For Secure Web Gateway
Internet Gateway Security IT Reasons Behind Need For Secure Web GatewayThis slide discusses the requirement of Secure Web Gateway in protecting organizations from various cyber crimes. The reasons behind need of Secure Web Gateway are protection against web-based threats, enforce security policies, controlled access, etc. Introducing Internet Gateway Security IT Reasons Behind Need For Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Rise In Web-Based Threats, Non-Compliance To Security Policies, Need Of Access Control, Web Traffic Monitoring, Remote Worker Protection, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Relationship Between Secure Access Service
Internet Gateway Security IT Relationship Between Secure Access ServiceThis slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc. Introducing Internet Gateway Security IT Relationship Between Secure Access Service to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Administration Of Microservices, Distributed Environment, Visibility Control Over Traffic Passing, Cloud-Native Application, using this template. Grab it now to reap its full benefits.
-
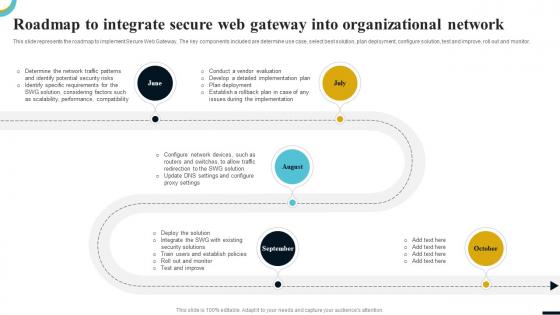 Internet Gateway Security IT Roadmap To Integrate Secure Web Gateway
Internet Gateway Security IT Roadmap To Integrate Secure Web GatewayThis slide represents the roadmap to implement Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Introducing Internet Gateway Security IT Roadmap To Integrate Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Scalability, Performance, Compatibility, Implementation, Plan Deployment, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Architecture And Working
Internet Gateway Security IT Secure Web Gateway Architecture And WorkingThis slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. Introducing Internet Gateway Security IT Secure Web Gateway Architecture And Working to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Policy Enforcement, Malware Detection, Web Proxy, Public Internet, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Challenges And Solutions
Internet Gateway Security IT Secure Web Gateway Challenges And SolutionsThis slide outlines the limitations of Secure Web Gateway such as increasingly sophisticated threats, encrypted traffic, cloud-based applications and mobile devices. This purpose of this slide is to explain the possible solutions to these challenges. Present the topic in a bit more detail with this Internet Gateway Security IT Secure Web Gateway Challenges And Solutions. Use it as a tool for discussion and navigation on Increasingly, Sophisticated Threats, Encrypted Traffic, Cloud-Based Applications, Mobile Devices. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Secure Web Gateway For Remote And On Site
Internet Gateway Security IT Secure Web Gateway For Remote And On SiteThis slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees. Introducing Internet Gateway Security IT Secure Web Gateway For Remote And On Site to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Remote Users, Internet, Cloud Based Secure Web Gateway, Secure Web Gateway, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Implementation
Internet Gateway Security IT Secure Web Gateway ImplementationThis slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Introducing Internet Gateway Security IT Secure Web Gateway Implementation to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Internet Gateway, Internet Connected Network Site, Administrative Costs, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Implementation Scenarios
Internet Gateway Security IT Secure Web Gateway Implementation ScenariosThis slide represents the different types of Secure Web Gateway deployment methods. The purpose of this slide is to outline SWG implementation methodologies. These are inline, explicit, transparent and SPAN Switched Port Analyzer port. Introducing Internet Gateway Security IT Secure Web Gateway Implementation Scenarios to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Inline, Transparent, Explicit, SPAN, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Set Up Configuration
Internet Gateway Security IT Secure Web Gateway Set Up ConfigurationThis slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc. Introducing Internet Gateway Security IT Secure Web Gateway Set Up Configuration to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Configure Web Gateway Software, Install And Configure SSL, TLS Certificates, Establish Security Policies, Set Up Access Restrictions, Test The Web Gateway, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Set Up Ongoing
Internet Gateway Security IT Secure Web Gateway Set Up OngoingThis slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc. Introducing Internet Gateway Security IT Secure Web Gateway Set Up Ongoing to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Inspect Web Gateway, Examine Security Policies, Train Staff And Users, Update And Patch Software, Perform Routine Security Audits, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Set Up Planning
Internet Gateway Security IT Secure Web Gateway Set Up PlanningThis slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the planning and preparation phase of SWG set-up. The key points included are define scope of project, identify network architecture, etc. Introducing Internet Gateway Security IT Secure Web Gateway Set Up Planning to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Define Scope Of Project, Identify Network Architecture, Define Security Policy, Select Appropriate Hardware And Software, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Training Program
Internet Gateway Security IT Secure Web Gateway Training ProgramThis slide represents the training program for the Secure Web Gateway. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Present the topic in a bit more detail with this Internet Gateway Security IT Secure Web Gateway Training Program. Use it as a tool for discussion and navigation on Agenda, System Requirements, Mode, Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Steps To Integrate Secure Web Gateway
Internet Gateway Security IT Steps To Integrate Secure Web GatewayThis slide demonstrates the steps for successful implementation of SWG into firms. The purpose of this slide is to outline the procedure of Secure Web integration. The steps included are determine use case, select best solution, plan deployment, etc. Introducing Internet Gateway Security IT Steps To Integrate Secure Web Gateway to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Determine Use Case, Select Best Solution, Plan Deployment, Configure Solution, Test And Improve, Roll Out And Monitor, using this template. Grab it now to reap its full benefits.





