Powerpoint Templates and Google slides for It Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Strategic Password Authentication Training Plan IT Security Awareness Training Cybersecurity SS
Strategic Password Authentication Training Plan IT Security Awareness Training Cybersecurity SSThis slide represents training plan for verifying identity of user accessing a digital system. It includes details related to password authentication methods, training sessions etc. Deliver an outstanding presentation on the topic using this Strategic Password Authentication Training Plan IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Token Authentication, Biometric Authentication, Strategic Password, Authentication Training Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents IT Security Awareness Training Program Cybersecurity SS
Table Of Contents IT Security Awareness Training Program Cybersecurity SSIntroducing Table Of Contents IT Security Awareness Training Program Cybersecurity SS to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Team Roles And Responsibilities, Costs Incurred, Planning, Cloud Security, Social Engineering Program, using this template. Grab it now to reap its full benefits.
-
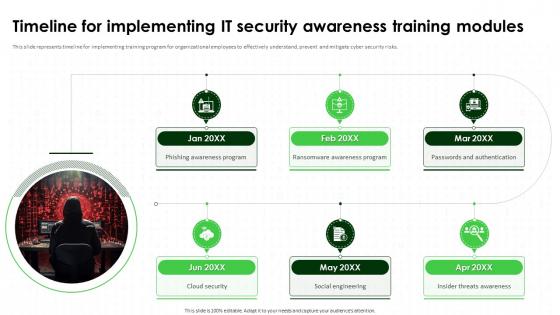 Timeline For Implementing IT Security Awareness Training Modules Cybersecurity SS
Timeline For Implementing IT Security Awareness Training Modules Cybersecurity SSThis slide represents timeline for implementing training program for organizational employees to effectively understand, prevent and mitigate cyber security risks. Increase audience engagement and knowledge by dispensing information using Timeline For Implementing IT Security Awareness Training Modules Cybersecurity SS. This template helps you present information on six stages. You can also present information on Ransomware Awareness Program, Passwords And Authentication, Social Engineering, Insider Threats Awareness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Training Plan For Detecting Phishing Attacks IT Security Awareness Training Cybersecurity SS
Training Plan For Detecting Phishing Attacks IT Security Awareness Training Cybersecurity SSThis slide represents details related to training plan to assist employees in detecting phishing attacks. It includes details related to training topics such as general signs of phishing attacks etc. Present the topic in a bit more detail with this Training Plan For Detecting Phishing Attacks IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Manufactured Rapport Or History, Manufactured Urgency, Sensitive Questions As Standard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Training Plan For Detecting Ransomware Attacks IT Security Awareness Training Cybersecurity SS
Training Plan For Detecting Ransomware Attacks IT Security Awareness Training Cybersecurity SSThis slide represents training plan for detecting to malware that is designed to deny a user or organization access to files on their computer or networks. It includes details related to detection techniques etc. Deliver an outstanding presentation on the topic using this Training Plan For Detecting Ransomware Attacks IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Signature Based Detection, Detection Based On Traffic, Detection By Data Behavior using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Training Plan For Mitigating Ransomware Attacks IT Security Awareness Training Cybersecurity SS
Training Plan For Mitigating Ransomware Attacks IT Security Awareness Training Cybersecurity SSThis slide represents training plan for mitigating malware that is designed to deny a user or organization access to files on their computer or networks. It includes details related to mitigation techniques etc. Introducing Training Plan For Mitigating Ransomware Attacks IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Managed Detection And Response, Extended Detection And Response, Endpoint Detection And Response, using this template. Grab it now to reap its full benefits.
-
 Training Plan For Preventing Phishing Attacks IT Security Awareness Training Cybersecurity SS
Training Plan For Preventing Phishing Attacks IT Security Awareness Training Cybersecurity SSThis slide represents training plan to assist employees in effectively preventing phishing attacks. It includes details related to training topics such as email communication and hyperlinks etc. Present the topic in a bit more detail with this Training Plan For Preventing Phishing Attacks IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Report Phishing Attempts, Email Communications And Hyperlinks, Best Practices For Handling Mails. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web Security Upgradation Web Security Training Program For It Team
Web Security Upgradation Web Security Training Program For It TeamThis slide highlights the comprehensive training program for IT teams which aims to train beginners about web security. Present the topic in a bit more detail with this Web Security Upgradation Web Security Training Program For It Team. Use it as a tool for discussion and navigation on Modules, Training Hours, Hands-On Application Security Basics. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major IOT Security Challenges And Its Solutions
Major IOT Security Challenges And Its SolutionsThis slide showcases major challenges faced in securing IoT data along with its solutions. Issues covered are weak authentication, network vulnerability, mobile network and cloud gap. Introducing our Major IOT Security Challenges And Its Solutions set of slides. The topics discussed in these slides are Challenges, Network Vulnerability, Weak Authentication. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Possible Solutions For Server Virtualization Security Issues Server Virtualization In Modern IT
Possible Solutions For Server Virtualization Security Issues Server Virtualization In Modern ITThis slide represents the server virtualization security best practices. The purpose of this slide is to highlight the best practices of server virtualization security such as controlling the management of virtual machines, ensuring integrity, etc. Introducing Possible Solutions For Server Virtualization Security Issues Server Virtualization In Modern IT to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Management Platform, Management Program, Whole Virtual Infrastructure, using this template. Grab it now to reap its full benefits.
-
 Web Security Training Schedule For It Teams
Web Security Training Schedule For It TeamsThis slide represents the training schedule for IT teams in an organization to efficiently conduct web security. Present the topic in a bit more detail with this Web Security Training Schedule For It Teams. Use it as a tool for discussion and navigation on Connectivity And Protocols, Understanding Endpoint Security, Introduction To Web Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Penetration Testing Implementation Plan Existing It Security Infrastructure Constituants
Penetration Testing Implementation Plan Existing It Security Infrastructure ConstituantsThis slide highlights the components of the current IT security infrastructure, which are prone to several security concerns. These constituents are access control, application security, firewalls, virtual private networks VPN, antivirus, etc. Deliver an outstanding presentation on the topic using this Penetration Testing Implementation Plan Existing It Security Infrastructure Constituants. Dispense information and present a thorough explanation of Access Control, Application Security, Antivirus Or Antimalware Systems, Password Auditing Tools using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Penetration Testing Implementation Plan Key Challenges Of Existing It Security
Penetration Testing Implementation Plan Key Challenges Of Existing It SecurityThis slide discusses the security issues faced by the organization due to a lack of security in infrastructure. These concerns are unauthorized access, data breaches, malware and ransomware, phishing attacks, data loss or corruption, compliance, etc. Deliver an outstanding presentation on the topic using this Penetration Testing Implementation Plan Key Challenges Of Existing It Security. Dispense information and present a thorough explanation of Unauthorized Access, Data Breaches, Malware And Ransomware, Phishing Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Penetration Testing Implementation Plan Performance Analysis Of Existing It Security
Penetration Testing Implementation Plan Performance Analysis Of Existing It SecurityThe purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions. Increase audience engagement and knowledge by dispensing information using Penetration Testing Implementation Plan Performance Analysis Of Existing It Security. This template helps you present information on Four stages. You can also present information on Ideal Testing, Organization, Penetration Testing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IT Modernization Strategy Icon For Data Security
IT Modernization Strategy Icon For Data SecurityIntroducing our premium set of slides with IT Modernization Strategy Icon For Data Security Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Modernization Strategy, Data Security So download instantly and tailor it with your information.
-
 IT Network Security Audit Checklist
IT Network Security Audit ChecklistThis slide exhibits systematic assessment of security postures of organizations IT infrastructure to protect against various threats. It includdes aspects such as access control, network security measures, incident response, etc. Introducing our IT Network Security Audit Checklist set of slides. The topics discussed in these slides are Tasks, Aspects, Applicable. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 It security layout example ppt presentation
It security layout example ppt presentationPresenting it security layout example ppt presentation. This is a it security layout example ppt presentation. This is eight stage process. The stages in this process are attack detection, system guard, file lock, process quarantine, passwords, antivirus, application guard, firewall.
-
 Cyberterrorism it impact of implementing cyber security measures in the company
Cyberterrorism it impact of implementing cyber security measures in the companyThis slide represents the current state of cyber assaults in a business after implementing the cyber security model. Present the topic in a bit more detail with this Cyberterrorism IT Impact Of Implementing Cyber Security Measures In The Company. Use it as a tool for discussion and navigation on Number Attacks, Cyber Terrorists Attacks 2021, Cyber Terrorists Attacks 2022. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Prepare And Deploy Strong It Policies
Information Security Prepare And Deploy Strong It PoliciesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Present the topic in a bit more detail with this Information Security Prepare And Deploy Strong It Policies. Use it as a tool for discussion and navigation on Prepare And Deploy Strong IT Policies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improve it security vulnerability security information event management dashboard
Improve it security vulnerability security information event management dashboardThis slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an outstanding presentation on the topic using this Improve It Security Vulnerability Security Information Event Management Dashboard. Dispense information and present a thorough explanation of Information, Management, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Improve it security with vulnerability event management dashboard snapshot
Improve it security with vulnerability event management dashboard snapshotThis slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an outstanding presentation on the topic using this Improve It Security With Vulnerability Event Management Dashboard snapshot. Dispense information and present a thorough explanation of Information, Management, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Prepare And Deploy Strong It Policies
Network Security Prepare And Deploy Strong It PoliciesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an outstanding presentation on the topic using this Network Security Prepare And Deploy Strong It Policies. Dispense information and present a thorough explanation of Prepare And Deploy Strong It Policies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Prepare And Deploy Strong It Policies
Information Technology Security Prepare And Deploy Strong It PoliciesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an outstanding presentation on the topic using this Information Technology Security Prepare And Deploy Strong It Policies. Dispense information and present a thorough explanation of Prepare And Deploy Strong IT Policies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Infrastructure Cyber Security Budget Against Cyber Terrorism Attacks
IT Infrastructure Cyber Security Budget Against Cyber Terrorism AttacksThis slide depicts the IT infrastructure budget of incorporating cyber security, as well as the cost of each activity to the company. Present the topic in a bit more detail with this IT Infrastructure Cyber Security Budget Against Cyber Terrorism Attacks. Use it as a tool for discussion and navigation on It Infrastructure Cyber Security Budget Against Cyber Terrorism Fy19 20. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enhancing overall project security it project management activities tracking dashboard
Enhancing overall project security it project management activities tracking dashboardThis slide provides information regarding the dashboard which will help team in managing different activities associated to projects and keep track on the time, cost spent. Present the topic in a bit more detail with this Enhancing Overall Project Security It Project Management Activities Tracking Dashboard. Use it as a tool for discussion and navigation on Project Management Activities Tracking Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Dashboard Of An It Company
Cyber Security Dashboard Of An It CompanyIntroducing our Cyber Security Dashboard Of An It Company set of slides. The topics discussed in these slides are Identified Threat, Average Threats, Information Technology. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Dashboard Of Shadow It Services
Security Dashboard Of Shadow It ServicesPresenting our well structured Security Dashboard Of Shadow IT Services. The topics discussed in this slide are Social Network, It Services, Online Meeting. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 F516 It Ot Convergence Security Objectives Challenges Managing The Successful Convergence Of It And Ot
F516 It Ot Convergence Security Objectives Challenges Managing The Successful Convergence Of It And OtThis slide covers objectives challenges catalysts and benefits of the Security in IT or OT convergence and Reduce systems cyberattack surface Increase audience engagement and knowledge by dispensing information using F516 It Ot Convergence Security Objectives Challenges Managing The Successful Convergence Of It And Ot. This template helps you present information on four stages. You can also present information on Objectives, Resources, Convergence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Hacker Budget For IT Spending By The Company Ppt Powerpoint Presentation Slides
Security Hacker Budget For IT Spending By The Company Ppt Powerpoint Presentation SlidesThis slide represents the IT spending budget for the advancements and cyber security policy changes that the organization will implement in the coming years. Present the topic in a bit more detail with this Security Hacker Budget For IT Spending By The Company Ppt Powerpoint Presentation Slides. Use it as a tool for discussion and navigation on IT Services, IT Peripherals, Mobile Devices. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Certified Information Systems Security Top 15 IT Certifications In Demand For 2022
Certified Information Systems Security Top 15 IT Certifications In Demand For 2022This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Present the topic in a bit more detail with this Certified Information Systems Security Top 15 IT Certifications In Demand For 2022. Use it as a tool for discussion and navigation on Job Responsibilities, Security Professional, Information Systems. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Professionals Certification Collection Certified Information Systems Security Professional CISSP
IT Professionals Certification Collection Certified Information Systems Security Professional CISSPThis slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc. Deliver an outstanding presentation on the topic using this IT Professionals Certification Collection Certified Information Systems Security Professional CISSP. Dispense information and present a thorough explanation of Security Operations, Asset Security, Security Engineering using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPI Dashboard To Track IT Security Performance
KPI Dashboard To Track IT Security PerformanceThis slide shows the dashboard of cyber security with incident and threat management. It includes overall progress, risk identified, number of critical incidents, initiatives, incident and threat management etc. Introducing our KPI Dashboard To Track IT Security Performance set of slides. The topics discussed in these slides are Critital Risks Identified, Incident Management, Threat Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Certified Information Systems Security Professional IT Professionals Certification Collection
Certified Information Systems Security Professional IT Professionals Certification CollectionThis slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver an outstanding presentation on the topic using this Certified Information Systems Security Professional IT Professionals Certification Collection. Dispense information and present a thorough explanation of Job Description, Certification, Employee using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Statistics Of It Security Automation System
Key Statistics Of It Security Automation SystemThe following slide highlights critical statistics of security automation in the IT industry. The statistics mentioned in the slide are alert processing, IR processing and preventing security exposures to network. Introducing our Key Statistics Of It Security Automation System set of slides. The topics discussed in these slides are Key Statistics, IT Security, Automation System. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 IT Security Technology User Market
IT Security Technology User MarketThe following slide provides the statistical data for user market of IT risk assessment and mitigation software to make business process efficient. The technology used are authentication, firewalls, encryption, data masking and data backup. Introducing our IT Security Technology User Market set of slides. The topics discussed in these slides are IT Security Technology, User Market. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 SDN Security IT Dashboard For Software Defined Networking SDN
SDN Security IT Dashboard For Software Defined Networking SDNThis slide depicts the dashboard for the software defined network by covering details of bandwidth administrator, traffic quality, active flows, development tools, completed tasks, wide-area network bandwidth, and G drive. Deliver an outstanding presentation on the topic using this SDN Security IT Dashboard For Software Defined Networking SDN. Dispense information and present a thorough explanation of Software, Networking, Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE IT Global Market Of Secure Access Service Edge Ppt Powerpoint Slides
SASE IT Global Market Of Secure Access Service Edge Ppt Powerpoint SlidesThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work-from-anywhere culture, and so on. Present the topic in a bit more detail with this SASE IT Global Market Of Secure Access Service Edge Ppt Powerpoint Slides. Use it as a tool for discussion and navigation on Changing Work Culture, Security Framework, Computing Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE IT Secure Access Service Edge Performance Tracking Dashboard Ppt Powerpoint Topics
SASE IT Secure Access Service Edge Performance Tracking Dashboard Ppt Powerpoint TopicsThis slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Present the topic in a bit more detail with this SASE IT Secure Access Service Edge Performance Tracking Dashboard Ppt Powerpoint Topics. Use it as a tool for discussion and navigation on SASE Connections, Critical Network Alarms, Critical Security Alerts. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective It Cost Optimization Initiatives Strategic Plan To Secure It Infrastructure Strategy SS V
Effective It Cost Optimization Initiatives Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding effective IT cost optimization strategies for IT executives such as revamping technology procurement, DevOps deployment, enabling business process reengineering, etc. Increase audience engagement and knowledge by dispensing information using Effective It Cost Optimization Initiatives Strategic Plan To Secure It Infrastructure Strategy SS V. This template helps you present information on four stages. You can also present information on Revamping Technology Procurement, Enabling Business Process Reengineering, Optimization Initiatives using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 F1471 Dashboard To Track Essential Activities Strategic Plan To Secure It Infrastructure Strategy SS V
F1471 Dashboard To Track Essential Activities Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding dashboard to monitor critical activities related to IT in terms of incident tracker, outage report, IT spend per employee, application trends, etc. Present the topic in a bit more detail with this F1471 Dashboard To Track Essential Activities Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Dashboard, Associated, Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It Performance Dashboard To Track Customer Strategic Plan To Secure It Infrastructure Strategy SS V
It Performance Dashboard To Track Customer Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding the dashboard to monitor overall IT performance. The dashboard tracks occupancy rate, net promoter score, avg. first contact resolution rate, etc. Present the topic in a bit more detail with this It Performance Dashboard To Track Customer Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Performance, Dashboard, Satisfaction. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Pivotal Responsibilities Managed By Cios Across Strategic Plan To Secure It Infrastructure Strategy SS V
Pivotal Responsibilities Managed By Cios Across Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding responsibilities managed by CIOs across firm in terms of task delegation to improve productivity, management of IT dept., Administer network and system deployment, etc. Present the topic in a bit more detail with this Pivotal Responsibilities Managed By Cios Across Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Responsibilities, Management, Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps To Build Competent Application Rationalization Strategic Plan To Secure It Infrastructure Strategy SS V
Steps To Build Competent Application Rationalization Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding the key steps required to develop an application rationalization framework and their feasibility. The steps include determining business value, measuring application TCO, etc. Present the topic in a bit more detail with this Steps To Build Competent Application Rationalization Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Application, Rationalization, Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps To Develop Targeted Marketing Initiatives Strategic Plan To Secure It Infrastructure Strategy SS V
Steps To Develop Targeted Marketing Initiatives Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information various steps required to develop target marketing initiatives for IT department. The initiatives include detect target market, conduct market research, develop objectives and goals, etc. Introducing Steps To Develop Targeted Marketing Initiatives Strategic Plan To Secure It Infrastructure Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Marketing, Initiatives, Department, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Strategic Plan To Secure It Infrastructure Strategy SS V
Table Of Contents For Strategic Plan To Secure It Infrastructure Strategy SS VPresent the topic in a bit more detail with this Table Of Contents For Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Strategic Business Alignment, Workforce And Cost Management, Deploy Application Rationalization . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine established security centre overview key initiatives for project safety it
Determine established security centre overview key initiatives for project safety itThis slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver an outstanding presentation on the topic using this Determine Established Security Centre Overview Key Initiatives For Project Safety It. Dispense information and present a thorough explanation of Functional Business, Security, External Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
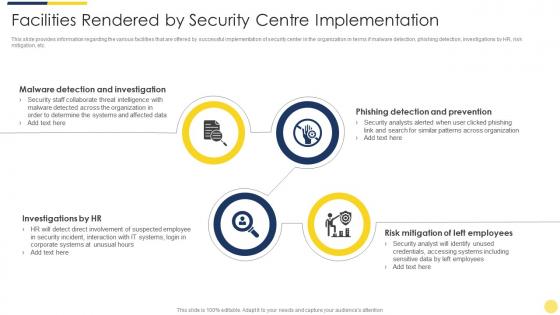 Facilities rendered by security centre implementation key initiatives for project safety it
Facilities rendered by security centre implementation key initiatives for project safety itThis slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Increase audience engagement and knowledge by dispensing information using Enabling Data Security Risk Management Action Plan Key Initiatives For Project Safety It. This template helps you present information on four stages. You can also present information on Determine, Organization, Data, Security, Organization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information security process key initiatives for project safety it ppt gallery example
Information security process key initiatives for project safety it ppt gallery exampleThis slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Present the topic in a bit more detail with this Information Security Process Key Initiatives For Project Safety It Ppt Gallery Example. Use it as a tool for discussion and navigation on Process, Information, Dynamic, System, Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine established security centre overview project safety management it
Determine established security centre overview project safety management itThis slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Present the topic in a bit more detail with this Determine Established Security Centre Overview Project Safety Management It. Use it as a tool for discussion and navigation on Functional Business, Security, Management, Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine role of security centre to ensure project safety project safety management it
Determine role of security centre to ensure project safety project safety management itThis slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Present the topic in a bit more detail with this Determine Role Of Security Centre To Ensure Project Safety Project Safety Management It. Use it as a tool for discussion and navigation on Organizational, System, Security, Team, Analysts. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
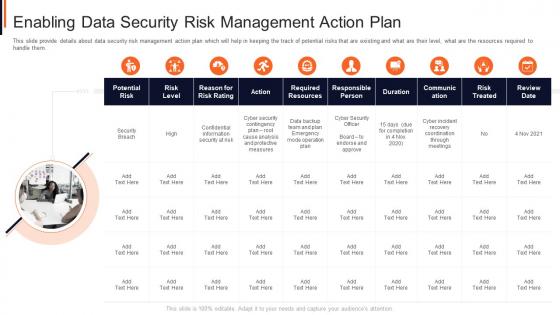 Enabling data security risk management action plan project safety management it
Enabling data security risk management action plan project safety management itThis slide provide details about data security risk management action plan which will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Introducing Enabling Data Security Risk Management Action Plan Project Safety Management It to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Analysis, Measures, Plan, Security, Risk, using this template. Grab it now to reap its full benefits.
-
 Facilities rendered by security centre implementation project safety management it
Facilities rendered by security centre implementation project safety management itThis slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Increase audience engagement and knowledge by dispensing information using Facilities Rendered By Security Centre Implementation Project Safety Management It. This template helps you present information on four stages. You can also present information on Analysts, Security, Organization, Data, Determine using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information security process to manage firms project safety management it
Information security process to manage firms project safety management itThis slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Present the topic in a bit more detail with this Information Security Process To Manage Firms Project Safety Management It. Use it as a tool for discussion and navigation on Security, Network, Employees, Dynamic, System. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Role of it professionals in digitalization cloud security architect skills scope
Role of it professionals in digitalization cloud security architect skills scopeThis slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc. Deliver an outstanding presentation on the topic using this Role Of IT Professionals In Digitalization Cloud Security Architect Skills Scope. Dispense information and present a thorough explanation of Architecture And Strategy, Technical, Legend, Leadership, Operational using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Role of it professionals in digitalization role of chief information security officer
Role of it professionals in digitalization role of chief information security officerThis slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. Increase audience engagement and knowledge by dispensing information using Role Of IT Professionals In Digitalization Role Of Chief Information Security Officer. This template helps you present information on seven stages. You can also present information on Business Advisor, Identify C Level, Team Member, Monthly Reports, Stay Informed, Embed Security Information, External Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 It infrastructure electronic information security budget for fy2020
It infrastructure electronic information security budget for fy2020This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an outstanding presentation on the topic using this IT Infrastructure Electronic Information Security Budget For FY2020. Dispense information and present a thorough explanation of Antivirus, Anti Malware, IT Security Budget, Total Costs using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 What is electronic information security and how does it work
What is electronic information security and how does it workThis slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Introducing What Is Electronic Information Security And How Does IT Work to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Caused Natural Disasters, Collective Methods, Techniques And Procedures, Protect Data, using this template. Grab it now to reap its full benefits.
-
 It security area ppt powerpoint presentation portfolio infographics cpb
It security area ppt powerpoint presentation portfolio infographics cpbPresenting our It Security Area Ppt Powerpoint Presentation Portfolio Infographics Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Medical Billing Terminology This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Web application firewall waf it security use cases of web application firewall deployment
Web application firewall waf it security use cases of web application firewall deploymentThis slide represents the security use cases of web application firewall and how it would stop cyberattacks such as DDoS attacks, malicious bot abuse, and customer data breaches. Introducing Web Application Firewall Waf It Security Use Cases Of Web Application Firewall Deployment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Application, Performance, Deployment, using this template. Grab it now to reap its full benefits.
-
 Web application firewall waf it types of web application firewall security models
Web application firewall waf it types of web application firewall security modelsThis slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Present the topic in a bit more detail with this Web Application Firewall Waf It Types Of Web Application Firewall Security Models. Use it as a tool for discussion and navigation on Organizations, Application, Firewall. This template is free to edit as deemed fit for your organization. Therefore download it now.





