Powerpoint Templates and Google slides for Intrusive
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD
Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CDWhile your presentation may contain top-notch content, if it lacks visual appeal, you are not fully engaging your audience. Introducing our Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, it is downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck.
-
 Intrusion Prevention System As An Element Of Network Security Training Ppt
Intrusion Prevention System As An Element Of Network Security Training PptPresenting Intrusion Prevention System as an Element of Network Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Intrusion Detection Systems IDS For Network Security Training Ppt
Intrusion Detection Systems IDS For Network Security Training PptPresenting Intrusion Detection Systems IDS for Network Security. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Cybersecurity Kpis Dashboard Showcasing Intrusion Attempts
Cybersecurity Kpis Dashboard Showcasing Intrusion AttemptsThis slide showcases the cybersecurity KPIs dashboard showcasing intrusion attempts which helps an organization to align metrics with broader business goals, objectives. It include details such as backup frequency per month, mean response time, etc. Introducing our Cybersecurity Kpis Dashboard Showcasing Intrusion Attempts set of slides. The topics discussed in these slides are Intrusion Attempts By Week, Mean Response Time. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Implementing Intrusion Prevention Gap Analysis For Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Gap Analysis For Intrusion Prevention System Cybersecurity SSThis slide represents the gap analysis to help organizations understand the gaps so that they can build effective strategies to eliminate these gaps and achieve desired results. Present the topic in a bit more detail with this Implementing Intrusion Prevention Gap Analysis For Intrusion Prevention System Cybersecurity SS. Use it as a tool for discussion and navigation on Proactive Security Measures, Average Incident Response, Network Traffic Monitored. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
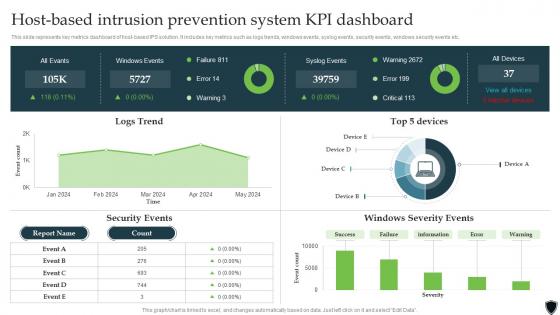 Implementing Intrusion Prevention Host Based Intrusion Prevention System KPI Cybersecurity SS
Implementing Intrusion Prevention Host Based Intrusion Prevention System KPI Cybersecurity SSThis slide represents key metrics dashboard of host-based IPS solution. It includes key metrics such as logs trends, windows events, syslog events, security events, windows security events etc. Present the topic in a bit more detail with this Implementing Intrusion Prevention Host Based Intrusion Prevention System Kpi Cybersecurity SS. Use it as a tool for discussion and navigation on Success, Failure, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
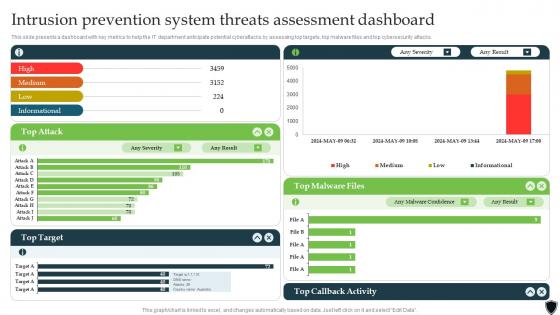 Implementing Intrusion Prevention Intrusion Prevention System Threats Assessment Cybersecurity SS
Implementing Intrusion Prevention Intrusion Prevention System Threats Assessment Cybersecurity SSThis slide presents a dashboard with key metrics to help the IT department anticipate potential cyberattacks by assessing top targets, top malware files and top cybersecurity attacks. Present the topic in a bit more detail with this Implementing Intrusion Prevention Intrusion Prevention System Threats Assessment Cybersecurity SS. Use it as a tool for discussion and navigation on Callback Activity, Malware Files, Target. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Overview Steps For Implementing Intrusion Cybersecurity SS
Implementing Intrusion Prevention Overview Steps For Implementing Intrusion Cybersecurity SSThis slide represents the process for effectively deploying a network security tool that monitors the network for malicious activities. It includes steps such as defining network segmentation etc. Introducing Implementing Intrusion Prevention Overview Steps For Implementing Intrusion Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Define Network Segmentation, Select Right Hardware And Software, Installation And Configuration, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Potential Impact Of Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Potential Impact Of Intrusion Prevention Cybersecurity SSThis slide highlights the impact of deploying effective Intrusion prevention system solution on organizational operations, such as increased real-time threat visibility, proactive threat detection etc. Present the topic in a bit more detail with this Implementing Intrusion Prevention Potential Impact Of Intrusion Prevention Cybersecurity SS. Use it as a tool for discussion and navigation on Increase In Real-Time Threat Visibility, Increase In Proactive Threat Detection Rates, Decrease In Average Cost Per Breach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Potential Roi After Implementing Intrusion Cybersecurity SS
Implementing Intrusion Prevention Potential Roi After Implementing Intrusion Cybersecurity SSThis slide demonstrates the positive impact of implementing Intrusion prevention system solution on returns on investments. The graph depicts an increase in ROI and savings over time. Present the topic in a bit more detail with this Implementing Intrusion Prevention Potential Roi After Implementing Intrusion Cybersecurity SS. Use it as a tool for discussion and navigation on Potential ROI After Implementing, Intrusion Prevention System. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Intrusion Detection Broken Shield Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Intrusion Detection Broken Shield Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon features a broken shield with a distressed texture. It is perfect for conveying a sense of vulnerability, fragility, or failure in presentations. It is available in a range of vibrant colours and can be used to highlight key points or draw attention to important concepts.
-
 Intrusion Detection Broken Shield Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Intrusion Detection Broken Shield Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint icon depicts a broken shield, representing a lack of protection or security. It is perfect for conveying a sense of vulnerability, fragility, or danger in presentations. It can also be used to illustrate a lack of trust or loyalty.
-
 Host Intrusion Detection System For Security
Host Intrusion Detection System For SecurityThis slide highlights security benefits for host intrusion detection system. This further includes benefits such as evaluate traffic, threat intelligence and intrusion notification. Introducing our Host Intrusion Detection System For Security set of slides. The topics discussed in these slides are Evaluate Traffic, Threat Intelligence, Intrusion Notification. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Firewall Network Security Intrusion Prevention Systems Ipss Overview And Methods
Firewall Network Security Intrusion Prevention Systems Ipss Overview And MethodsThis slide talks about the Intrusion Prevention System and its various methods for analyzing traffic. The purpose of this slide is to give an overview of Intrusion Prevention Systems and their methods, such as signature-based detection, statistical anomaly detection, and stateful protocol analysis detection. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Intrusion Prevention Systems Ipss Overview And Methods This template helps you present information on Three stages. You can also present information on Spyware Protection, Against Viruses, Prevents Hacking using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IoT Solutions For Transforming Food IoT Model For Food Tracking And Warehouse Intrusion IoT SS
IoT Solutions For Transforming Food IoT Model For Food Tracking And Warehouse Intrusion IoT SSFollowing slide represents framework to understand IoT enable process for inventory tracking to prevent unwanted intrusion or defects. It includes elements such as communication link, transmitter, sensors, RFID tags, GPRS, etc. Present the topic in a bit more detail with this IoT Solutions For Transforming Food IoT Model For Food Tracking And Warehouse Intrusion IoT SS. Use it as a tool for discussion and navigation on Inventory Tracking, Prevent Unwanted Intrusion, Food Tracking, Warehouse Intrusion Detection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Intrusion Detection Using Ai And Ml In IoT Ecosystem IoT Security And Privacy Safeguarding IoT SS
Intrusion Detection Using Ai And Ml In IoT Ecosystem IoT Security And Privacy Safeguarding IoT SSThis slide provides information on intrusion detection system that helps to monitor and analyse user data, networks and services to detect vulnerabilities. It includes three stages such as monitoring stage, analysing stage and detection stage.Present the topic in a bit more detail with this Intrusion Detection Using Ai And Ml In IoT Ecosystem IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Features Extraction, Anomaly Detection, Pattern Signature. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Types Of Intrusion Detection System IoT Security And Privacy Safeguarding IoT SS
Types Of Intrusion Detection System IoT Security And Privacy Safeguarding IoT SSThis slide exhibits two types of intrusion detection systems that may be deployed to provide layered security and enhance business operations. It includes two types of intrusion detection system such as network intrusion detection system and host intrusion detection system. Present the topic in a bit more detail with this Types Of Intrusion Detection System IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Network Intrusion, Best Suitable, Operating System. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Role Of Intrusion Prevention Systems In Wireless Internet Security
Role Of Intrusion Prevention Systems In Wireless Internet SecurityThe outlined slide covers essential aspects, including encryption, authentication, access control, device security, and intrusion detection prevention. It provides a comprehensive view of wireless internet security measures, crucial for thwarting data theft. Introducing our premium set of slides with Role Of Intrusion Prevention Systems In Wireless Internet Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Compliance Requirements, Increased Network Visibility, Cost Effective Security. So download instantly and tailor it with your information.
-
 Comparative Analysis For Network Intrusion Protection Cyber Security Tools
Comparative Analysis For Network Intrusion Protection Cyber Security ToolsThis slide depicts the comparative evaluation of NIPS security tools. The purpose of this slide is to help the business make a well informed purchase decision. It includes comparison on the basis of the free trial period, features, ratings, etc. Introducing our premium set of slides with Comparative Analysis For Network Intrusion Protection Cyber Security Tools Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Distinctive Features, Free Trial, Tools So download instantly and tailor it with your information.
-
 Intrusion Prevention VS Detection Under NIPS Cyber Security
Intrusion Prevention VS Detection Under NIPS Cyber SecurityThis slide highlights the comparison between intrusion detection systems and intrusion prevention systems. The purpose of this slide is to help the business determine its business needs and implement suitable processes. It includes comparison on the basis of location, use, etc. Presenting our well structured Intrusion Prevention VS Detection Under NIPS Cyber Security The topics discussed in this slide are Description, Location, False Positive This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Network Intrusion And Prevention Cyber Security Icon
Network Intrusion And Prevention Cyber Security IconPresenting our set of slides with Network Intrusion And Prevention Cyber Security Icon This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Intrusion, Prevention Cyber Security Icon
-
 Network Intrusion Prevention Cyber Security System
Network Intrusion Prevention Cyber Security SystemThis slide highlights the network intrusion prevention system cybersecurity. The purpose of this slide is to help ensure that suitable processes are undertaken during security incidents. It includes elements such as network perimeters, internet, LAN, etc. Introducing our Network Intrusion Prevention Cyber Security System set of slides. The topics discussed in these slides are Internet, Network Perimeter, Prevention Systems This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Technique Of Network Intrusion Protection Systems
Technique Of Network Intrusion Protection SystemsThis slide depicts the network intrusion determination cybersecurity system tactics. The purpose of this slide is to help identify its business needs and utilize suitable approaches. It includes approaches such as policy based detection, anomaly based detection, etc. Introducing our Technique Of Network Intrusion Protection Systems set of slides. The topics discussed in these slides are Policy Based Detection, Anomaly Based Detection, Signature Based Detection This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Endpoint Security Intrusion Detection And Prevention System Idps In Endpoint Security
Endpoint Security Intrusion Detection And Prevention System Idps In Endpoint SecurityThis slide highlights the introduction of Intrusion Detection and Prevention System IDPS in endpoint security for preventing threats. Increase audience engagement and knowledge by dispensing information using Endpoint Security Intrusion Detection And Prevention System Idps In Endpoint Security. This template helps you present information on six stages. You can also present information on Alerts And Remediates Threat, Stop Detected Threats, Monitors Networks For Threats, Intrusion Detection And Prevention System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Intrusion Detection System In Powerpoint And Google Slides Cpp
Best Intrusion Detection System In Powerpoint And Google Slides CppPresenting Best Intrusion Detection System In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Best Intrusion Detection System. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities And Prevent Threats, Protect Organizations Networks, Filter Out Malicious Activities, Security Devices Or Controls, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing our well researched set of slides titled Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
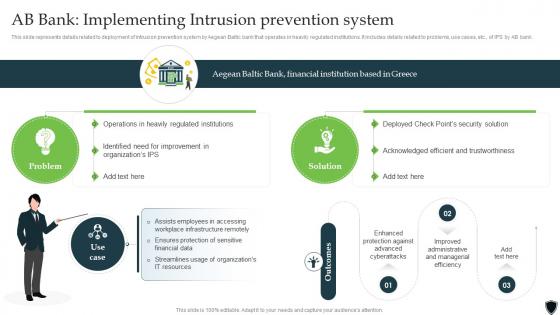 Implementing Intrusion Prevention Ab Bank Implementing Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Ab Bank Implementing Intrusion Prevention System Cybersecurity SSThis slide represents details related to deployment of intrusion prevention system by Aegean Baltic bank that operates in heavily regulated institutions. It includes details related to problems, use cases, etc., of IPS by AB bank. Introducing Implementing Intrusion Prevention Ab Bank Implementing Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Problem, Solution, Enhanced Protection Against Advanced Cyberattacks, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Alerting Configuration For Implemented Intrusion Cybersecurity SS
Implementing Intrusion Prevention Alerting Configuration For Implemented Intrusion Cybersecurity SSThis slide outlines the steps to configure an alerting system for a network security tool implemented to monitor networks to prevent, report, and block malicious activities. Introducing Implementing Intrusion Prevention Alerting Configuration For Implemented Intrusion Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Automate Monitoring For Intrusions, Cyber Security Data Breaches, Deploy Alarms For Detected, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Best Practices To Configure Span Ports Cybersecurity SS
Implementing Intrusion Prevention Best Practices To Configure Span Ports Cybersecurity SSThis slide represents tactics to effectively configure switched port analyzers such as focusing on filtering, checking logs, and not over-capturing and analyzing the organizational environment. Introducing Implementing Intrusion Prevention Best Practices To Configure Span Ports Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Environment, Focus On Filtering, Check Logs, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Challenges Experienced By Organization Due Cybersecurity SS
Implementing Intrusion Prevention Challenges Experienced By Organization Due Cybersecurity SSThis slide outlines the issues that enterprise face with outdated cybersecurity solutions, including limited threat visibility, inability to combat APTs, lack of granular control, and insufficient incident response capabilities. Introducing Implementing Intrusion Prevention Challenges Experienced By Organization Due Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Limited Threat Visibility, Inability To Combat Apts, Lack Of Granular Control, Insufficient Incident Response, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Cisco Data Centers Deploying Network Based Ips Cybersecurity SS
Implementing Intrusion Prevention Cisco Data Centers Deploying Network Based Ips Cybersecurity SSThis slide represents details related to deployment of intrusion prevention system by Cisco data centers . It includes details related to problems, solutions, use cases and outcomes of deploying IPS by Cisco data centers. Introducing Implementing Intrusion Prevention Cisco Data Centers Deploying Network Based Ips Cybersecurity SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Problem, Solution, Outcomes, Fewer Service Interruptions, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Comparative Analysis Of Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Comparative Analysis Of Intrusion Prevention Cybersecurity SSThis slide represents details related to deployment of intrusion prevention system by Cisco data centers . It includes details related to problems, solutions, use cases and outcomes of deploying IPS by Cisco data centers. Present the topic in a bit more detail with this Implementing Intrusion Prevention Comparative Analysis Of Intrusion Prevention Cybersecurity SS. Use it as a tool for discussion and navigation on Softwares, Features, USP, Pricing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
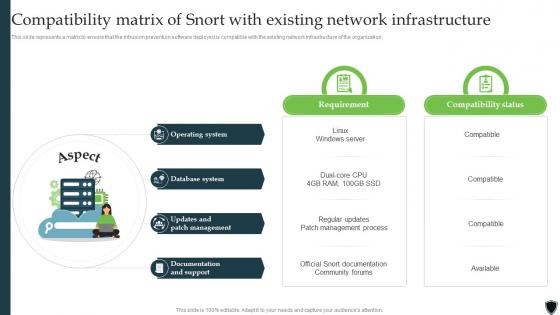 Implementing Intrusion Prevention Compatibility Matrix Of Snort With Existing Cybersecurity SS
Implementing Intrusion Prevention Compatibility Matrix Of Snort With Existing Cybersecurity SSThis slide represents a matrix to ensure that the intrusion prevention software deployed is compatible with the existing network infrastructure of the organization. Introducing Implementing Intrusion Prevention Compatibility Matrix Of Snort With Existing Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Operating System, Database System, Updates And Patch Management, Documentation And Support, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Configuring Alerts For Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Configuring Alerts For Intrusion Prevention Cybersecurity SSThis slide represents details related to the configuration of alerts for deployed network security tool that monitors networks for preventing, reporting, and blocking malicious activities. Introducing Implementing Intrusion Prevention Configuring Alerts For Intrusion Prevention Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on SNMP Alert Objects, Remote Syslog Alert Objects, Quarantine Response Objects, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Cost Benefit Analysis Of Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Cost Benefit Analysis Of Intrusion Prevention Cybersecurity SSThis slide shows the cost-benefit analysis of deploying Intrusion prevention system, including the costs incurred in deploying IPS platform and providing training to employees. Present the topic in a bit more detail with this Implementing Intrusion Prevention Cost Benefit Analysis Of Intrusion Prevention Cybersecurity SS. Use it as a tool for discussion and navigation on Initial Cost, Costs, Training Costs. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Costs Incurred In Deploying Intrusion Cybersecurity SS
Implementing Intrusion Prevention Costs Incurred In Deploying Intrusion Cybersecurity SSThis slide details the costs associated with deploying an Intrusion prevention system solution in an enterprise. It includes expenses for implementing IPS software, IT talent acquisition costs, training costs etc. Introducing Implementing Intrusion Prevention Costs Incurred In Deploying Intrusion Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Intrusion Prevention Software, IT Talent Acquisition Costs, Training Costs, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Create Network Segmentation Zones Based Cybersecurity SS
Implementing Intrusion Prevention Create Network Segmentation Zones Based Cybersecurity SSThis slide represents details related to the first step of deploying a network security tool that monitors networks to prevent malicious activities including blocking, reporting or dropping it. Introducing Implementing Intrusion Prevention Create Network Segmentation Zones Based Cybersecurity SS to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Active Directory, IT Monitoring Servers, Public Servers, Database Servers, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Customize Deployed Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Customize Deployed Intrusion Prevention Cybersecurity SSThis slide represents details related to customization of implemented network security tool that monitors networks to prevent, report and block malicious activities to organizations IT environment. Introducing Implementing Intrusion Prevention Customize Deployed Intrusion Prevention Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Servers, Metric Performance, Values, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Cybersecurity Incident Response Plan Timeline Cybersecurity SS
Implementing Intrusion Prevention Cybersecurity Incident Response Plan Timeline Cybersecurity SSThis slide represents a strategic plan to effectively respond to cybersecurity incidents experienced by the organization, including action steps such as a cyber incident reports, verification of incidents, etc. Present the topic in a bit more detail with this Implementing Intrusion Prevention Cybersecurity Incident Response Plan Timeline Cybersecurity SS. Use it as a tool for discussion and navigation on Cyber Incident Report, Verification Of Incident, Response Arrives. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
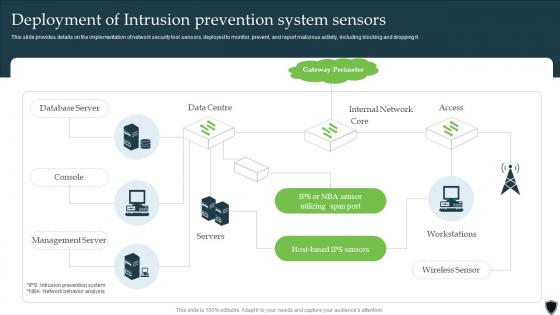 Implementing Intrusion Prevention Deployment Of Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Deployment Of Intrusion Prevention System Cybersecurity SSThis slide provides details on the implementation of network security tool sensors, deployed to monitor, prevent, and report malicious activity, including blocking and dropping it. Introducing Implementing Intrusion Prevention Deployment Of Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Database Server, Gateway Perimeter, Workstations, Management Server, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Fine Tune Detection Rules To Align With Threat Cybersecurity SS
Implementing Intrusion Prevention Fine Tune Detection Rules To Align With Threat Cybersecurity SSThis slide represents details related to fine-tuning threat detection rules for the implemented IPS software to effectively align with the organizations threat landscape. Present the topic in a bit more detail with this Implementing Intrusion Prevention Fine Tune Detection Rules To Align With Threat Cybersecurity SS. Use it as a tool for discussion and navigation on Preprocessor Rule, Standard Text Rule, Shared Object Rule. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
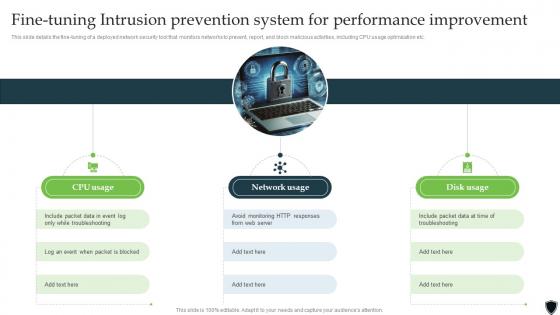 Implementing Intrusion Prevention Fine Tuning Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Fine Tuning Intrusion Prevention System Cybersecurity SSThis slide details the fine-tuning of a deployed network security tool that monitors networks to prevent, report, and block malicious activities, including CPU usage optimization etc. Introducing Implementing Intrusion Prevention Fine Tuning Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on CPU Usage, Network Usage, Disk Usage, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Hardware Requirements For Effective Ips Cybersecurity SS
Implementing Intrusion Prevention Hardware Requirements For Effective Ips Cybersecurity SSThis slide outlines the hardware requirements to consider when selecting a network security tool to monitor and prevent malicious activities. These requirements include network interfaces etc. Introducing Implementing Intrusion Prevention Hardware Requirements For Effective Ips Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Network Interfaces, Storage, Redundancy, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Identified Critical Assets And Threats Of Enterprise Cybersecurity SS
Implementing Intrusion Prevention Identified Critical Assets And Threats Of Enterprise Cybersecurity SSThis slide presents critical assets and associated threats, such as data breaches, information manipulation, data corruption, identity theft, etc., identified by the IT team. Present the topic in a bit more detail with this Implementing Intrusion Prevention Identified Critical Assets And Threats Of Enterprise Cybersecurity SS. Use it as a tool for discussion and navigation on Critical Assets, Network Infrastructure, Application Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS
Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SSThis slide represents the impact of outdated cybersecurity solutions on organizational operations which leads to compromised data security, data leakage, and damage to the organizations reputation. Introducing Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Compromised Data Integrity, Increase In Risk Of Data Leakage, Increase In Recovery Costs, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Monitor Real Time Intrusion Prevention Detection Cybersecurity SS
Implementing Intrusion Prevention Monitor Real Time Intrusion Prevention Detection Cybersecurity SSThis slide covers details related to real-time monitoring of system alerts provided by deployed network security tool that monitors networks for preventing, reporting and blocking malicious activities. Introducing Implementing Intrusion Prevention Monitor Real Time Intrusion Prevention Detection Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Pattern Recognition, Automated Response, Behavioral Analysis, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Patch Management Plan For Mitigating Cybersecurity SS
Implementing Intrusion Prevention Patch Management Plan For Mitigating Cybersecurity SSThis slide represents a strategic plan for protecting the organization against software vulnerabilities, including action steps such as establishing a regular patching schedule, successfully testing patches, etc. Introducing Implementing Intrusion Prevention Patch Management Plan For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Establish Regular Patching Schedule, Progress Status, Successfully Test Patches, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Potential Attacks Detected And Prevented Cybersecurity SS
Implementing Intrusion Prevention Potential Attacks Detected And Prevented Cybersecurity SSThis slide represents cybersecurity attacks detected and prevented by a network security tool that monitors the network for malicious activities, including DDoS attacks, ARP spoofing, and IP fragmentation. Introducing Implementing Intrusion Prevention Potential Attacks Detected And Prevented Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Distributed Denial Of Service, Address Resolution Protocol ARP Spoofing, IP Fragmentation, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Reasons To Invest In Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Reasons To Invest In Intrusion Prevention System Cybersecurity SSThis slide presents reasons to invest in a network security tool that monitors the network to prevent malicious activities, protect against known and unknown threats, etc. Introducing Implementing Intrusion Prevention Reasons To Invest In Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Protection Against Known, Unknown Threats, Real-Time Detection, Blocking Of Malicious Traffic, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Software Requirements For Effective Ips Solution Cybersecurity SS
Implementing Intrusion Prevention Software Requirements For Effective Ips Solution Cybersecurity SSThis slide outlines the software requirements to consider when selecting a network security tool to monitor and prevent malicious activities. These requirements include scalability, operating system etc. Introducing Implementing Intrusion Prevention Software Requirements For Effective Ips Solution Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Scalability, Operating System, Database Management System, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention System Intrusion Prevention System Training Plan Cybersecurity SS
Implementing Intrusion Prevention System Intrusion Prevention System Training Plan Cybersecurity SSThis slide details the training plan to facilitate the effective use of deployed IPS software by employees. It includes training topics such as traffic analysis, IPS signatures and analysis, web app attacks etc. Present the topic in a bit more detail with this Implementing Intrusion Prevention System Intrusion Prevention System Training Plan Cybersecurity SS. Use it as a tool for discussion and navigation on Training Method, Traffic Analysis, Anomaly Detection Systems, Web Application Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Update Signatures And Rules For Deployed Ips Solution Cybersecurity SS
Implementing Intrusion Prevention Update Signatures And Rules For Deployed Ips Solution Cybersecurity SSThis slide represents details related to upgradation of signatures and rules for the implemented network security tool that monitors networks to prevent, report and block malicious activities. Present the topic in a bit more detail with this Implementing Intrusion Prevention Update Signatures And Rules For Deployed Ips Solution Cybersecurity SS. Use it as a tool for discussion and navigation on Update Server, Internet, Manager Server, Sensor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security
Table Of Contents For Implementing Intrusion Prevention System For Effective Network SecurityIntroducing Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Issues Experienced Due Inefficient Network Security, Impact On Organizational Operations, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Budget Plan, Impact Assessment, Dashboards, Case Study Analysis, using this template. Grab it now to reap its full benefits.
-
 Deepfake Technology Threat Intrusion Framework
Deepfake Technology Threat Intrusion FrameworkThe purpose of this slide is to help businesses identify key considerations for mitigating deepfake threats. It covers various action steps such as intent, target research, training deepfake model, creating media and disseminating deepfake. Introducing our premium set of slides with name Deepfake Technology Threat Intrusion Framework. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Target Research, Intent, Create Media. So download instantly and tailor it with your information.
-
 Types intrusion detection systems ppt powerpoint presentation styles graphics design cpb
Types intrusion detection systems ppt powerpoint presentation styles graphics design cpbPresenting Types Intrusion Detection Systems Ppt Powerpoint Presentation Styles Graphics Design Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Types Intrusion Detection Systems. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Multiple Laws In Place To Limit Ambush Marketing By Intrusion Ambushing Competitors MKT SS V
Multiple Laws In Place To Limit Ambush Marketing By Intrusion Ambushing Competitors MKT SS VThis slide provides glimpse about different legal controls to limit ambush marketing done by intrusion on multiple big events. It includes contractual controls, special legislation, etc. Introducing Multiple Laws In Place To Limit Ambush Marketing By Intrusion Ambushing Competitors MKT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Contractual Controls, Special Legislation, Marketing By Intrusion, using this template. Grab it now to reap its full benefits.
-
 Multiple Laws In Place To Limit Ambush Marketing By Intrusion Garnering Massive Brand Exposure
Multiple Laws In Place To Limit Ambush Marketing By Intrusion Garnering Massive Brand ExposureThis slide provides glimpse about different legal controls to limit ambush marketing done by intrusion on multiple big events. It includes contractual controls, special legislation, etc. Increase audience engagement and knowledge by dispensing information using Multiple Laws In Place To Limit Ambush Marketing By Intrusion Garnering Massive Brand Exposure. This template helps you present information on three stages. You can also present information on Contractual Controls, Special Legislation, Ambush Marketing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network Monitoring And Intrusion Detection Icon
Network Monitoring And Intrusion Detection IconIntroducing our premium set of slides with Network Monitoring And Intrusion Detection Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Monitoring, Intrusion Detection Icon. So download instantly and tailor it with your information.




