Powerpoint Templates and Google slides for Information Sensitivity
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
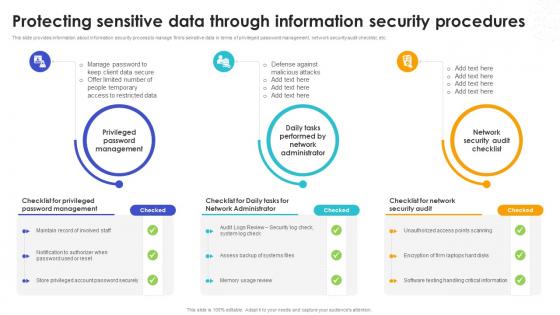 Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SS
Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information about information security process to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc.Introducing Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Audit, Privileged Password Management, Network Administrator, using this template. Grab it now to reap its full benefits.
-
 Data security it prepare data backup for sensitive information
Data security it prepare data backup for sensitive informationThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Present the topic in a bit more detail with this Data Security IT Prepare Data Backup For Sensitive Information. Use it as a tool for discussion and navigation on Data Backup, Provide Cloud Services, Prevent Data, Natural Disasters. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security prepare data backup for sensitive information
Computer system security prepare data backup for sensitive informationThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Introducing Computer System Security Prepare Data Backup For Sensitive Information to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Prepare Data Backup For Sensitive Information, using this template. Grab it now to reap its full benefits.
-
 Debt Recovery Process Safeguarding Personal And Sensitive Information Of Debtor
Debt Recovery Process Safeguarding Personal And Sensitive Information Of DebtorThis slide shows safeguarding policy to protect data of debtor or customers for being used wrongly. It include main situations for processing personal information and procedure to safeguard sensitive information, etc. Introducing Debt Recovery Process Safeguarding Personal And Sensitive Information Of Debtor to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Debt Collection Agency Employees, Footage For Security Purposes, Database Of Debtors Is Created, using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS V
Blockchain And Cybersecurity Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS VThe following slide illustrates some methods to minimize crypto phishing attacks and. It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Introducing Blockchain And Cybersecurity Ways To Minimize 51 Percent Attacks And Optimize Hash Rate BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Cross Check Emails, Factor Authentication, Unprotected Wi-Fi-Networks using this template. Grab it now to reap its full benefits.
-
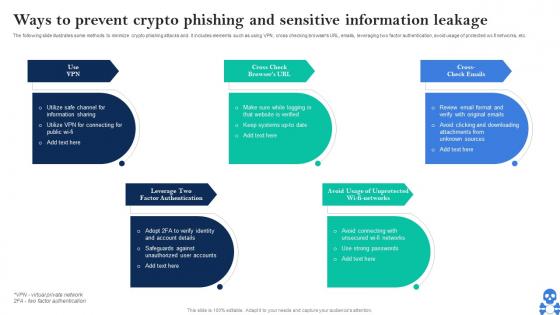 Cyber Threats In Blockchain Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS V
Cyber Threats In Blockchain Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS VThe following slide illustrates some methods to minimize crypto phishing attacks and. it includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Introducing Cyber Threats In Blockchain Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Use VPN, Factor Authentication, Avoid Usage Of Unprotected using this template. Grab it now to reap its full benefits.
-
 SAP Cybersecurity Icon To Safeguard Sensitive Information
SAP Cybersecurity Icon To Safeguard Sensitive InformationPresenting our set of slides with SAP Cybersecurity Icon To Safeguard Sensitive Information. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on SAP Cybersecurity, Icon To Safeguard, Sensitive Information.
-
 Ways To Prevent Crypto Phishing And Sensitive Information Leakage Guide For Blockchain BCT SS V
Ways To Prevent Crypto Phishing And Sensitive Information Leakage Guide For Blockchain BCT SS VThe following slide illustrates some methods to minimize crypto phishing attacks and. It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Introducing Ways To Prevent Crypto Phishing And Sensitive Information Leakage Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cross Check Emails, Factor Authentication, Unprotected Wi Fi Networks using this template. Grab it now to reap its full benefits.
-
 Salesforce Data Classification Icon For Tracking Sensitive Information
Salesforce Data Classification Icon For Tracking Sensitive InformationPresenting our set of slides with Salesforce Data Classification Icon For Tracking Sensitive Information. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Salesforce Data Classification, Icon, Tracking Sensitive Information.
-
 IoT Cybersecurity Challenges For Securing Sensitive Information
IoT Cybersecurity Challenges For Securing Sensitive InformationThis slide exhibits cybersecurity challenges for creating secure and resilient IoT ecosystem delivering benefits of efficiency, automation, and connectivity. It includes challenges such as software and firmware vulnerabilities, insecure communications, etc. Introducing our premium set of slides with IoT Cybersecurity Challenges For Securing Sensitive Information Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Software Firmware Vulnerabilities, Insecure Communications, Data Leaks Iot Systems So download instantly and tailor it with your information.
-
 Data Masking Workflow For Optimizing Sensitive Information Protection
Data Masking Workflow For Optimizing Sensitive Information ProtectionThis slide represents flowchart of data masking that assist IT companies to enhance security of their sensitive data improving operational efficiency. It includes various steps such as metadata collection, sensitive data discovery, etc. Introducing our Data Masking Workflow For Optimizing Sensitive Information Protection set of slides. The topics discussed in these slides are Data Masking Definition, Data Masking Process, Data Subsetting Definition.This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Monitoring Sensitive Data Tracking Information Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Monitoring Sensitive Data Tracking Information Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is designed to represent tracking sensitive information. With its eye-catching design and vibrant colours, it is the perfect addition to any presentation on data security and privacy. Use it to highlight the importance of tracking and safeguarding sensitive information in your next presentation.
-
 Monitoring Sensitive Data Tracking Information Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Monitoring Sensitive Data Tracking Information Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is designed to help users easily track and manage sensitive information within their presentations. With its simple yet effective design, this icon provides a visual representation of the importance of safeguarding confidential data. Perfect for professionals and businesses who prioritize data privacy and security.
-
 Information Security Process To Manage Firms Sensitive Data Defense Plan To Protect Firm Assets
Information Security Process To Manage Firms Sensitive Data Defense Plan To Protect Firm AssetsThis slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Present the topic in a bit more detail with this Information Security Process To Manage Firms Sensitive Data Defense Plan To Protect Firm Assets. Use it as a tool for discussion and navigation on Privileged Password Management, Network Administrator. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information security process to manage firms sensitive data key initiatives for project safety it
Information security process to manage firms sensitive data key initiatives for project safety itThis slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an outstanding presentation on the topic using this Information Security Process To Manage Firms Sensitive Data Key Initiatives For Project Safety It. Dispense information and present a thorough explanation of Management, Network, Security, Performed using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information security process to manage firms sensitive data project safety management it
Information security process to manage firms sensitive data project safety management itThis slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an outstanding presentation on the topic using this Information Security Process To Manage Firms Sensitive Data Project Safety Management It. Dispense information and present a thorough explanation of Management, Network, Systems, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Electronic information security prepare data backup sensitive information
Electronic information security prepare data backup sensitive informationThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Introducing Electronic Information Security Prepare Data Backup Sensitive Information to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Data Backup, Natural Disasters, Provide Cloud Services, Data Backups Offline, using this template. Grab it now to reap its full benefits.
-
 Cyber threat security icon to capture sensitive information
Cyber threat security icon to capture sensitive informationIntroducing our premium set of slides with Cyber Threat Security Icon To Capture Sensitive Information. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Threat Security Icon To Capture Sensitive Information. So download instantly and tailor it with your information.
-
 Information Security Data Backup For Sensitive Information
Information Security Data Backup For Sensitive InformationThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Increase audience engagement and knowledge by dispensing information using Information Security Data Backup For Sensitive Information. This template helps you present information on three stages. You can also present information on Protect, Information, Manipulation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Building organizational security strategy plan information security process to manage firms sensitive
Building organizational security strategy plan information security process to manage firms sensitiveThis slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Information Security Process To Manage Firms Sensitive. Use it as a tool for discussion and navigation on Information, Process, Sensitive. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Hacking it backup of sensitive information ppt styles infographic template
Hacking it backup of sensitive information ppt styles infographic templateThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Increase audience engagement and knowledge by dispensing information using Hacking It Backup Of Sensitive Information Ppt Styles Infographic Template. This template helps you present information on four stages. You can also present information on Sensitive, Information, Manipulation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network Security Prepare Data Backup For Sensitive Information
Network Security Prepare Data Backup For Sensitive InformationThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Increase audience engagement and knowledge by dispensing information using Network Security Prepare Data Backup For Sensitive Information. This template helps you present information on three stages. You can also present information on Information, Protect, Manipulation, Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Data Backup For Sensitive Information
Information Technology Security Data Backup For Sensitive InformationThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Introducing Information Technology Security Data Backup For Sensitive Information to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Prepare Data Backup For Sensitive Information, using this template. Grab it now to reap its full benefits.
-
 Security Hacker Backup Of Sensitive Information Ppt Powerpoint Presentation Outline
Security Hacker Backup Of Sensitive Information Ppt Powerpoint Presentation OutlineThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Increase audience engagement and knowledge by dispensing information using Security Hacker Backup Of Sensitive Information Ppt Powerpoint Presentation Outline. This template helps you present information on four stages. You can also present information on Manipulation And Hacking, Emergency Access, Encryption Key using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Monitor Access To Sensitive And Regulated Data Information Privacy Ppt Powerpoint Presentation Outline Images
Monitor Access To Sensitive And Regulated Data Information Privacy Ppt Powerpoint Presentation Outline ImagesThis slide explains we help you with data privacy by monitoring access of sensitive and regulated data, in which automation engine assists you in achieving the least privilege and compliance faster.Increase audience engagement and knowledge by dispensing information using Monitor Access To Sensitive And Regulated Data Information Privacy Ppt Powerpoint Presentation Outline Images. This template helps you present information on five stages. You can also present information on Entitlement Assessments, Individuals Access, Unrestricted Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Monitor And Detect Abnormal Activity On Sensitive Data Information Privacy Ppt Inspiration Images
Monitor And Detect Abnormal Activity On Sensitive Data Information Privacy Ppt Inspiration ImagesThis slide highlights that you will have continuous monitoring and detection of abnormal activities of all the organizations data.Introducing Monitor And Detect Abnormal Activity On Sensitive Data Information Privacy Ppt Inspiration Images to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Customer Personal, Regulated Problematic, Business Provide, using this template. Grab it now to reap its full benefits.
-
 Sensitive Information Logs Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Sensitive Information Logs Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Sensitive information logs colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Sensitive Information Logs Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Sensitive Information Logs Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Sensitive information logs monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Confidential Sensitive Data Information Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Confidential Sensitive Data Information Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is perfect for representing confidential information. It is a bright, eye catching image that will make your presentation stand out. It is easy to use and can be used to highlight confidential information in a professional and visually appealing way.
-
 Confidential Sensitive Data Information Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Confidential Sensitive Data Information Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon is perfect for presentations on confidential information. It features a black and white design that conveys a sense of security and privacy. Perfect for any presentation that requires a confidential approach.
-
 List prioritized risks historical information planning inputs sensitivity analysis
List prioritized risks historical information planning inputs sensitivity analysisPresenting this set of slides with name - List Prioritized Risks Historical Information Planning Inputs Sensitivity Analysis. This is an editable eight stages graphic that deals with topics like List Prioritized Risks, Historical Information, Planning Inputs, Sensitivity Analysis to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Industry opportunities threats company knowledge base information sensitivity
Industry opportunities threats company knowledge base information sensitivityPresenting this set of slides with name - Industry Opportunities Threats Company Knowledge Base Information Sensitivity. This is an editable seven stages graphic that deals with topics like Industry Opportunities Threats, Company Knowledge Base, Information Sensitivity to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Spiral booklet icon with sensitive information
Spiral booklet icon with sensitive informationPresenting this set of slides with name Spiral Booklet Icon With Sensitive Information. The topics discussed in these slides is Spiral Booklet Icon With Sensitive Information. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Communication software to secure sensitive information
Communication software to secure sensitive informationPresenting our set of slides with Communication Software To Secure Sensitive Information. This exhibits information on one stage of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Communication Software To Secure Sensitive Information.
-
 Prepare data backup for sensitive information cyber security it ppt powerpoint samples
Prepare data backup for sensitive information cyber security it ppt powerpoint samplesThis slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Present the topic in a bit more detail with this Prepare Data Backup For Sensitive Information Cyber Security IT Ppt Powerpoint Samples. Use it as a tool for discussion and navigation on Manipulation, Secure, Natural Disasters, Cloud Services. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information security process to manage firms sensitive data contd management to improve project safety it
Information security process to manage firms sensitive data contd management to improve project safety itThis slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Introducing Information Security Process To Manage Firms Sensitive Data Contd Management To Improve Project Safety IT to increase your presentation threshold. Encompassed with Firewall Audit Checklist, VPN Configuration, Penetrating Testing stages, this template is a great option to educate and entice your audience. Dispence information on Firewall Audit Checklist,VPN Configuration,Penetrating Testing, using this template. Grab it now to reap its full benefits.
-
 Information security process to manage firms sensitive data management to improve project safety it
Information security process to manage firms sensitive data management to improve project safety itThis slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Increase audience engagement and knowledge by dispensing information using Information Security Process To Manage Firms Sensitive Data Management To Improve Project Safety IT. This template helps you present information on three stages. You can also present information on Privileged Password Management, Daily Tasks Performed By Network Administrator, Network Security Audit Checklist using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.



