Powerpoint Templates and Google slides for Information Security Strategy
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementation Of Information Ict Business Security Kpi Dashboard Strategy SS V
Implementation Of Information Ict Business Security Kpi Dashboard Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Present the topic in a bit more detail with this Implementation Of Information Ict Business Security Kpi Dashboard Strategy SS V. Use it as a tool for discussion and navigation on Issues By Control Type, Standard Control Issues. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Key Ict Security Measures Used By Businesses Strategy SS V
Implementation Of Information Key Ict Security Measures Used By Businesses Strategy SS VThis slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Deliver an outstanding presentation on the topic using this Implementation Of Information Key Ict Security Measures Used By Businesses Strategy SS V. Dispense information and present a thorough explanation of Survey Goal, Responsible Person using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats
Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Deliver an outstanding presentation on the topic using this Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Cyber Security Budget Spent, It Costs And Revenue, Issue Status Summary using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information security strategy ppt powerpoint presentation icon example cpb
Information security strategy ppt powerpoint presentation icon example cpbPresenting Information Security Strategy Ppt Powerpoint Presentation Icon Example Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Information Security Strategy. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Strategies Information Security In Powerpoint And Google Slides Cpb
Strategies Information Security In Powerpoint And Google Slides CpbPresenting our Strategies Information Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Strategies Information Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Implementation Of Information Best Practices For Effective Endpoint Security Strategy SS V
Implementation Of Information Best Practices For Effective Endpoint Security Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users finding and tracking business owned devices and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Implementation Of Information Best Practices For Effective Endpoint Security Strategy SS V. This template helps you present information on three stages. You can also present information on Educate Users, Installation Maintenance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementation Of Information Data Encryption Model For Effective Information Security Strategy SS V
Implementation Of Information Data Encryption Model For Effective Information Security Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Present the topic in a bit more detail with this Implementation Of Information Data Encryption Model For Effective Information Security Strategy SS V. Use it as a tool for discussion and navigation on Backup Repository, Encrypted Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Key Access Security Control Models Strategy SS V
Implementation Of Information Key Access Security Control Models Strategy SS VThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role based access control and attributes based access control, Present the topic in a bit more detail with this Implementation Of Information Key Access Security Control Models Strategy SS V. Use it as a tool for discussion and navigation on Discretionary Access, Mandatory Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Most Commonly Types Of Ict Securities Used By Strategy SS V
Implementation Of Information Most Commonly Types Of Ict Securities Used By Strategy SS VThis slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Introducing Implementation Of Information Most Commonly Types Of Ict Securities Used By Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Access Security, using this template. Grab it now to reap its full benefits.
-
 Implementation Of Information Network Security Model To Effective Communication Strategy SS V
Implementation Of Information Network Security Model To Effective Communication Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Present the topic in a bit more detail with this Implementation Of Information Network Security Model To Effective Communication Strategy SS V. Use it as a tool for discussion and navigation on Message Transformation, Information Channel. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
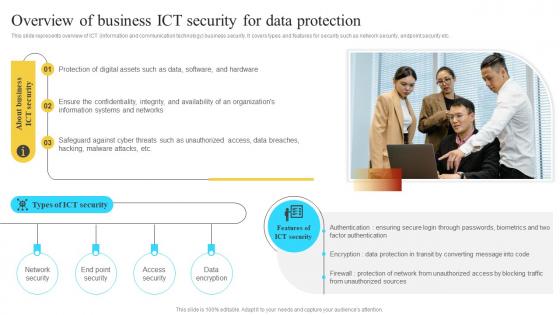 Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V
Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Protection Of Digital, Safeguard Against Cyber, using this template. Grab it now to reap its full benefits.
-
 Information Security Strategic Plan Components
Information Security Strategic Plan ComponentsThis slide showcase major components of information security strategic plan to reduce cyber security incident threat .It involves security awareness, risk prevention, data management, network security and control and monitor security measures. Presenting our set of slides with Information Security Strategic Plan Components. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Awareness, Data Management, Monitor Security Measures.
-
 Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use
Encryption Implementation Strategies Data Protection Technologies To Secure Information In UseThis slide compares different data in use protection methods, and their working and associated cost. These methods are IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use. Use it as a tool for discussion and navigation on Identity Management Tools, Digital Rights Protection, Data Protection Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Organizational Compliance Regulations For Information Security
Encryption Implementation Strategies Organizational Compliance Regulations For Information SecurityThe purpose of this slide is to summarize the most common regulations that organizations need to comply with, and their requirements. These regulations are HIPAA Health Insurance Portability and Accountability Act, SOX, PCI DSS, breach laws in all US states, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Organizational Compliance Regulations For Information Security. Use it as a tool for discussion and navigation on Health Insurance Portability, Accountability Act, Payment Card Industry, Data Security Standard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V
Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Present the topic in a bit more detail with this Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V Use it as a tool for discussion and navigation on Employee Headcount, Average Employee Age, Gender Diversity Ratio This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber Security
Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber SecurityThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Deliver an outstanding presentation on the topic using this Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber Security Dispense information and present a thorough explanation of Vulnerability, Threat, Threat Source using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategies To Ensure Information Security From Ransomware Attacks
Strategies To Ensure Information Security From Ransomware AttacksThis slide highlights techniques for securing information against ransomware attacks. The purpose of this slide is to assist professionals in ensuring business continuity and minimizing downtime. It includes elements such as email security, patch updates, network segmentation, etc. Introducing our premium set of slides with Strategies To Ensure Information Security From Ransomware Attacks. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Control, Data Encryption, Awareness. So download instantly and tailor it with your information.
-
 Strategic Information Technology Security Plan
Strategic Information Technology Security PlanThis slide represents strategic plan for information technology security which includes security types such as network security, internet security, endpoint security, etc. Introducing our premium set of slides with name Strategic Information Technology Security Plan. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Purpose, Person Responsible, Actions Required, Status. So download instantly and tailor it with your information.
-
 Security information and event management successful siem strategies for audit compliance
Security information and event management successful siem strategies for audit complianceThis slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Present the topic in a bit more detail with this Security Information And Event Management Successful Siem Strategies For Audit Compliance. Use it as a tool for discussion and navigation on Information, Management, Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Impact On Organization After Implementing Information Strategy Training
Information Security Impact On Organization After Implementing Information Strategy TrainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Present the topic in a bit more detail with this Information Security Impact On Organization After Implementing Information Strategy Training. Use it as a tool for discussion and navigation on Implementing, Information, Strategy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Impact Organization After Implementing Strategy Training
Information Technology Security Impact Organization After Implementing Strategy TrainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Present the topic in a bit more detail with this Information Technology Security Impact Organization After Implementing Strategy Training. Use it as a tool for discussion and navigation on Organization, Implementing, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Information Security Strategy On Company
Impact Of Information Security Strategy On CompanyThe slide showcases impact initiated by information security strategy and training provided to employees on company. The slide contains key takeaways and impact on company after implying the security software in the organization. Presenting our well structured Impact Of Information Security Strategy On Company. The topics discussed in this slide are Impact Of Information, Security, Strategy On Company. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
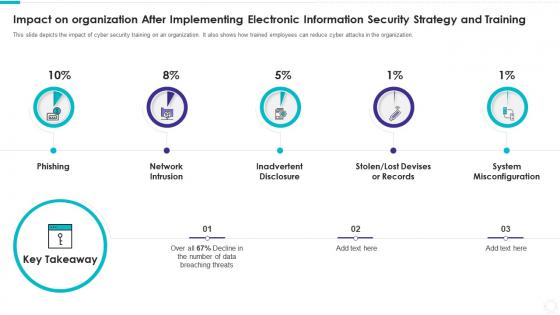 Impact on organization after implementing electronic information security strategy
Impact on organization after implementing electronic information security strategyThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Introducing Impact On Organization After Implementing Electronic Information Security Strategy to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing, Network Intrusion, Inadvertent Disclosure, Stolen, Lost Devises Or Records, System Misconfiguration, using this template. Grab it now to reap its full benefits.
-
 Electronic information security strategies to manage cyber risks
Electronic information security strategies to manage cyber risksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Increase audience engagement and knowledge by dispensing information using Electronic Information Security Strategies To Manage Cyber Risks. This template helps you present information on four stages. You can also present information on Prioritize Cyber Risk Strategic Issue, Build Policies And Structures, Invest Worthy Implementation, Conduct Awareness Sessions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Model For Information Security Program
Strategic Model For Information Security ProgramThis slide focuses on strategic model for information security program which includes governance and management such as security risk analysis, audit and assessment, supplier management, backup and recovery, etc. Presenting our well-structured Strategic Model For Information Security Program. The topics discussed in this slide are Evaluation And Direction, Leadership, Human Resource Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Successful siem strategies audit compliance security information event management services
Successful siem strategies audit compliance security information event management servicesThis slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Introducing Successful Siem Strategies Audit Compliance Security Information Event Management Services to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Data Aggregation, Data Correlation, Dashboards, using this template. Grab it now to reap its full benefits.
-
 Information Security Strategies To Manage Cyber Risks
Information Security Strategies To Manage Cyber RisksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Introducing Information Security Strategies To Manage Cyber Risks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strategies To Manage Cyber Risks, using this template. Grab it now to reap its full benefits.
-
 Role Of Chief Information Security Officer It Strategy For Digitalization In Business
Role Of Chief Information Security Officer It Strategy For Digitalization In BusinessThis slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. Introducing Role Of Chief Information Security Officer It Strategy For Digitalization In Business to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Business Advisor, Team Members, Security Information, using this template. Grab it now to reap its full benefits.
-
 Building organizational security strategy plan information security process to manage firms sensitive
Building organizational security strategy plan information security process to manage firms sensitiveThis slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Information Security Process To Manage Firms Sensitive. Use it as a tool for discussion and navigation on Information, Process, Sensitive. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Strategies To Manage Cyber Risks
Information Technology Security Strategies To Manage Cyber RisksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Increase audience engagement and knowledge by dispensing information using Information Technology Security Strategies To Manage Cyber Risks. This template helps you present information on four stages. You can also present information on Strategic, Structures, Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Addressing three essential attributes of information building organizational security strategy plan
Addressing three essential attributes of information building organizational security strategy planThis slide provides information about essential attributes of information in terms of protecting confidentiality, ensuring integrity and maintaining availability. Introducing Addressing Three Essential Attributes Of Information Building Organizational Security Strategy Plan to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Information, Confidentiality, Responsibilities, using this template. Grab it now to reap its full benefits.
-
 Mitigation Strategies To Avoid Information Breach Information Security Risk Management
Mitigation Strategies To Avoid Information Breach Information Security Risk ManagementThis slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Introducing Mitigation Strategies To Avoid Information Breach Information Security Risk Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Implement Antivirus Software, Monitor Network Traffic, Incident Response Plan, using this template. Grab it now to reap its full benefits.
-
 Mitigation Strategies To Tackle Information Security Threats Information Security Risk Management
Mitigation Strategies To Tackle Information Security Threats Information Security Risk ManagementThis slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business. Increase audience engagement and knowledge by dispensing information using Mitigation Strategies To Tackle Information Security Threats Information Security Risk Management. This template helps you present information on five stages. You can also present information on Mitigation Strategies, Tackle Information, Security Threats using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Mitigation Strategies To Avoid Information Breach Information System Security And Risk Administration Plan
Mitigation Strategies To Avoid Information Breach Information System Security And Risk Administration PlanThis slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Increase audience engagement and knowledge by dispensing information using Mitigation Strategies To Avoid Information Breach Information System Security And Risk Administration Plan. This template helps you present information on five stages. You can also present information on Incident Response Plan, Monitor Network Traffic, Patch Management Schedule using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mitigation Strategies To Tackle Information Security Information System Security And Risk Administration Plan
Mitigation Strategies To Tackle Information Security Information System Security And Risk Administration PlanThis slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and main reputation of business. Introducing Mitigation Strategies To Tackle Information Security Information System Security And Risk Administration Plan to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Malware, Phishing, SQL Injection, using this template. Grab it now to reap its full benefits.
-
 Mitigation Strategies To Tackle Information Security Cybersecurity Risk Analysis And Management Plan
Mitigation Strategies To Tackle Information Security Cybersecurity Risk Analysis And Management PlanThis slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and main reputation of business Introducing Mitigation Strategies To Tackle Information Security Cybersecurity Risk Analysis And Management Plan to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Mitigation, Strategies, Information, using this template. Grab it now to reap its full benefits.
-
 Mitigation Strategies To Tackle Information Security Threats Formulating Cybersecurity Plan
Mitigation Strategies To Tackle Information Security Threats Formulating Cybersecurity PlanThis slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business. Increase audience engagement and knowledge by dispensing information using Mitigation Strategies To Tackle Information Security Threats Formulating Cybersecurity Plan. This template helps you present information on five stages. You can also present information on Malware, Phishing, Mitigation Strategies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Governance Strategic Model
Information Security Governance Strategic ModelThe following slide showcases a framework presenting strategy development and implementation phase in information security governance. It includes key components such as organizational structure, value delivery, strategic alignment, resource optimization, performance measurement, etc. Presenting our set of slides with Information Security Governance Strategic Model. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Organizational Structure, Strategic Alignment, Compliance.
-
 Information Security And Governance Guide To Build It Strategy Plan For Organizational Growth
Information Security And Governance Guide To Build It Strategy Plan For Organizational GrowthThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this Information Security And Governance Guide To Build It Strategy Plan For Organizational Growth. Use it as a tool for discussion and navigation on Governance, Management, Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Handler Contact Information Incident Response Strategies Deployment
Cyber Security Incident Handler Contact Information Incident Response Strategies DeploymentThis slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Handler Contact Information Incident Response Strategies Deployment. This template helps you present information on three stages. You can also present information on Organisation, Role, Contact using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Initiatives Playbook Information Security And Governance Management Framework
Strategic Initiatives Playbook Information Security And Governance Management FrameworkThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this Strategic Initiatives Playbook Information Security And Governance Management Framework. Use it as a tool for discussion and navigation on Information Security, Governance, Management, Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Governance Management Framework IT Cost Optimization And Management Strategy SS
Information Security And Governance Management Framework IT Cost Optimization And Management Strategy SSThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Deliver an outstanding presentation on the topic using this Information Security And Governance Management Framework IT Cost Optimization And Management Strategy SS. Dispense information and present a thorough explanation of Context, Leadership, Evaluation Direction using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Governance Management Develop Business Aligned IT Strategy
Information Security And Governance Management Develop Business Aligned IT StrategyThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this Information Security And Governance Management Develop Business Aligned IT Strategy. Use it as a tool for discussion and navigation on Infrastructure Security, Response And Recovery, Security Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Framework To Manage IT Information Security And Governance Management Strategy SS
Strategic Framework To Manage IT Information Security And Governance Management Strategy SSThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this Strategic Framework To Manage IT Information Security And Governance Management Strategy SS. Use it as a tool for discussion and navigation on Information Security, Governance, Management, Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Strategy Planning Guide Information Security And Governance Management Framework Strategy SS V
IT Strategy Planning Guide Information Security And Governance Management Framework Strategy SS VThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this IT Strategy Planning Guide Information Security And Governance Management Framework Strategy SS V. Use it as a tool for discussion and navigation on Information Security, Governance, Management Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard To Track It Security Incidents Prevailing Blueprint Develop Information It Roadmap Strategy Ss
Dashboard To Track It Security Incidents Prevailing Blueprint Develop Information It Roadmap Strategy SsThis slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Deliver an outstanding presentation on the topic using this Dashboard To Track It Security Incidents Prevailing Blueprint Develop Information It Roadmap Strategy Ss. Dispense information and present a thorough explanation of Dashboard, Information, Authentification using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Governance Management Blueprint Develop Information It Roadmap Strategy Ss
Information Security And Governance Management Blueprint Develop Information It Roadmap Strategy SsThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this Information Security And Governance Management Blueprint Develop Information It Roadmap Strategy Ss. Use it as a tool for discussion and navigation on Evaluation And Direction, Identify Security, Infrastructure Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It Risk Management Framework To Manage Security Blueprint Develop Information It Roadmap Strategy Ss
It Risk Management Framework To Manage Security Blueprint Develop Information It Roadmap Strategy SsThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Present the topic in a bit more detail with this It Risk Management Framework To Manage Security Blueprint Develop Information It Roadmap Strategy Ss. Use it as a tool for discussion and navigation on Management, Framework, Environment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Governance Management Strategic Initiatives To Boost IT Strategy SS V
Information Security And Governance Management Strategic Initiatives To Boost IT Strategy SS VThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Deliver an outstanding presentation on the topic using this Information Security And Governance Management Strategic Initiatives To Boost IT Strategy SS V. Dispense information and present a thorough explanation of Security, Governance, Framework using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Encryption Model For Effective Information Security Strategy SS
Data Encryption Model For Effective Information Security Strategy SSThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc.Present the topic in a bit more detail with this Data Encryption Model For Effective Information Security Strategy SS. Use it as a tool for discussion and navigation on Backup Repository, Encrypted Data, Proper Decryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Governance Management Framework Definitive Guide To Manage Strategy SS V
Information Security And Governance Management Framework Definitive Guide To Manage Strategy SS VThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this Information Security And Governance Management Framework Definitive Guide To Manage Strategy SS V. Use it as a tool for discussion and navigation on Context Leadership, Evaluation, Direction. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Governance Strategic Plan To Secure It Infrastructure Strategy SS V
Information Security And Governance Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Deliver an outstanding presentation on the topic using this Information Security And Governance Strategic Plan To Secure It Infrastructure Strategy SS V. Dispense information and present a thorough explanation of Information, Governance, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Governance Management Framework Cios Guide For It Strategy Strategy SS V
Information Security And Governance Management Framework Cios Guide For It Strategy Strategy SS VThis slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Present the topic in a bit more detail with this Information Security And Governance Management Framework Cios Guide For It Strategy Strategy SS V. Use it as a tool for discussion and navigation on Information, Governance, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Encryption Model For Effective Information Security ICT Strategic Framework Strategy SS V
Data Encryption Model For Effective Information Security ICT Strategic Framework Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Deliver an outstanding presentation on the topic using this Data Encryption Model For Effective Information Security ICT Strategic Framework Strategy SS V. Dispense information and present a thorough explanation of Encrypted Data, Backup Repository, Tape Media, Secret Key using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information security strategy activities controls monitor measure
Information security strategy activities controls monitor measurePresenting this set of slides with name - Information Security Strategy Activities Controls Monitor Measure. This is a three stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Information security strategy assessment ethical hacking
Information security strategy assessment ethical hackingPresenting this set of slides with name - Information Security Strategy Assessment Ethical Hacking. This is a four stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
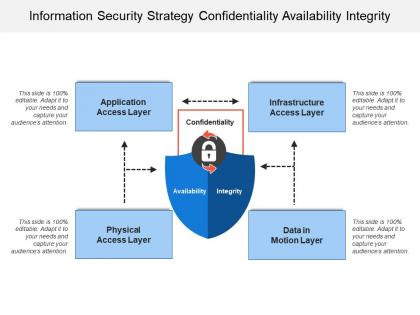 Information security strategy confidentiality availability integrity
Information security strategy confidentiality availability integrityPresenting this set of slides with name - Information Security Strategy Confidentiality Availability Integrity. This is a four stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
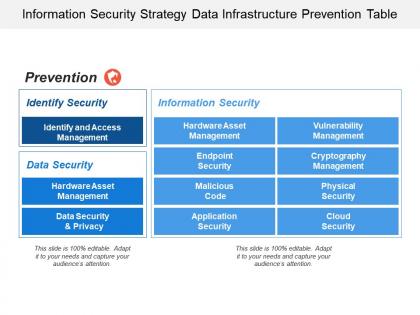 Information security strategy data infrastructure prevention table
Information security strategy data infrastructure prevention tablePresenting this set of slides with name - Information Security Strategy Data Infrastructure Prevention Table. This is a two stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Information security strategy icons
Information security strategy iconsPresenting this set of slides with name - Information Security Strategy Icons. This is a three stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
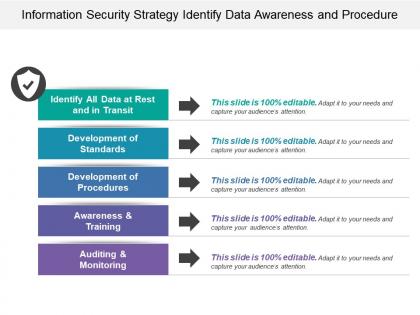 Information security strategy identify data awareness and procedure
Information security strategy identify data awareness and procedurePresenting this set of slides with name - Information Security Strategy Identify Data Awareness And Procedure. This is a five stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.




