Powerpoint Templates and Google slides for Information Security Management
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Security information and event management about our siem company
Security information and event management about our siem companyThis slide provides the glimpse about the SIEM company which covers the companys background, firms operations and offerings. Increase audience engagement and knowledge by dispensing information using Security Information And Event Management About Our SIEM Company. This template helps you present information on four stages. You can also present information on About Our SIEM Company using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security information and event management benchmarking maturity model
Security information and event management benchmarking maturity modelThis slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Introducing Security Information And Event Management Benchmarking Maturity Model to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Improve, Visibility, Identify, using this template. Grab it now to reap its full benefits.
-
 Security information and event management benefits siem services
Security information and event management benefits siem servicesThis slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Increase audience engagement and knowledge by dispensing information using Security Information And Event Management Benefits SIEM Services. This template helps you present information on four stages. You can also present information on Financial, Managing, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security information and event management calculating network device
Security information and event management calculating network deviceThis slide covers the SIEM sizing wherein velocity is calculated for various selected network devices and conduct an inventory of the devices from where logs can be collected. Present the topic in a bit more detail with this Security Information And Event Management Calculating Network Device. Use it as a tool for discussion and navigation on Calculating Network Device Velocity Sizing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management cloud siem model
Security information and event management cloud siem modelThis slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver an outstanding presentation on the topic using this Security Information And Event Management Cloud SIEM Model. Dispense information and present a thorough explanation of Visualization, Alerting, Analytics using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security information and event management companys enhanced features
Security information and event management companys enhanced featuresThis slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. Present the topic in a bit more detail with this Security Information And Event Management Companys Enhanced Features. Use it as a tool for discussion and navigation on Detection, Investigation, Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management estimating ownership siem
Security information and event management estimating ownership siemThis slide covers the cost breakdown of SIEM solution based on initial expenses, recurring expenses and amount saved by the client if they choose our company. Deliver an outstanding presentation on the topic using this Security Information And Event Management Estimating Ownership SIEM. Dispense information and present a thorough explanation of Infrastructure, Product, Expenses using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security information and event management fully managed service model
Security information and event management fully managed service modelPresent the topic in a bit more detail with this Security Information And Event Management Fully Managed Service Model. Use it as a tool for discussion and navigation on Visualization, Correlation, Aggregation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management how siem works
Security information and event management how siem worksDeliver an outstanding presentation on the topic using this Security Information And Event Management How SIEM Works. Dispense information and present a thorough explanation of Operating Systems, Network Device, Security Device using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security information and event management hybrid managed siem model
Security information and event management hybrid managed siem modelPresent the topic in a bit more detail with this Security Information And Event Management Hybrid Managed SIEM Model. Use it as a tool for discussion and navigation on Hybrid Managed SIEM Model. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management key features of siem software
Security information and event management key features of siem softwareThis slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. Introducing Security Information And Event Management Key Features Of SIEM Software to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Comprehensive, Collection, Compliance, using this template. Grab it now to reap its full benefits.
-
 Security information and event management log management metrics
Security information and event management log management metricsIncrease audience engagement and knowledge by dispensing information using Security Information And Event Management Log Management Metrics. This template helps you present information on eight stages. You can also present information on Configurations, Virtualization, Application using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security information and event management need for siem software in your company
Security information and event management need for siem software in your companyThis slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management Introducing Security Information And Event Management Need For SIEM Software In Your Company to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Digital, Security, Generating, using this template. Grab it now to reap its full benefits.
-
 Security information and event management next evolution of siem software
Security information and event management next evolution of siem softwareThis slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Increase audience engagement and knowledge by dispensing information using Security Information And Event Management Next Evolution Of SIEM Software. This template helps you present information on six stages. You can also present information on Traffic Analysis, Behavior Analytics, Threat Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security information and event management our organization flow
Security information and event management our organization flowThis slide covers the companys log flow and understand how the data is gathered, security alerts are notified to the clients. Introducing Security Information And Event Management Our Organization Flow to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Our Organization SIEM Log Flow, using this template. Grab it now to reap its full benefits.
-
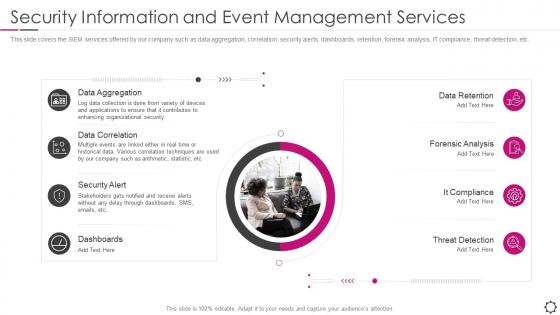 Security information and event management security management services
Security information and event management security management servicesThis slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Introducing Security Information And Event Management Security Management Services to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Aggregation, Data Correlation, Security Alert, using this template. Grab it now to reap its full benefits.
-
 Security information and event management siem logging sources
Security information and event management siem logging sourcesThis slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Increase audience engagement and knowledge by dispensing information using Security Information And Event Management SIEM Logging Sources. This template helps you present information on four stages. You can also present information on Security Devices, Network Devices, Servers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
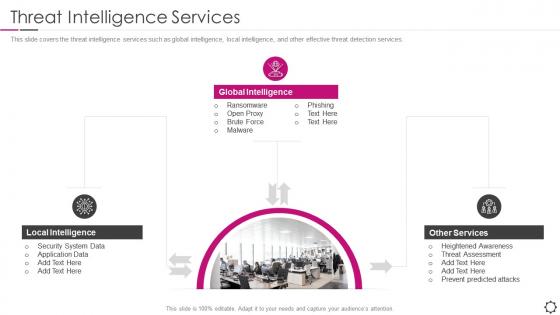 Security information and event management threat intelligence services
Security information and event management threat intelligence servicesThis slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. Introducing Security Information And Event Management Threat Intelligence Services to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Global Intelligence, Local Intelligence, Services, using this template. Grab it now to reap its full benefits.
-
 Security information and event management traditional siem deployment
Security information and event management traditional siem deploymentThis slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Present the topic in a bit more detail with this Security Information And Event Management Traditional SIEM Deployment. Use it as a tool for discussion and navigation on Visualization, Collection, Aggregation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management various siem cost
Security information and event management various siem costThis slide covers the different costs plan offered by our company such as basic, intermediate, advanced, learning model costs. Deliver an outstanding presentation on the topic using this Security Information And Event Management Various SIEM Cost. Dispense information and present a thorough explanation of Correlation, Response, Intermediate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
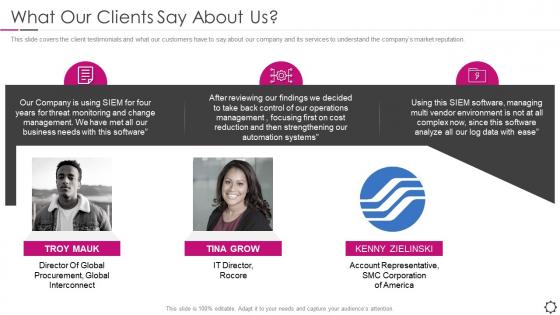 Security information and event management what about us
Security information and event management what about usThis slide covers the client testimonials and what our customers have to say about our company and its services to understand the companys market reputation.Introducing Security Information And Event Management What About Us to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on What Our Clients Say About Us, using this template. Grab it now to reap its full benefits.
-
 Security information and event management security intelligence services
Security information and event management security intelligence servicesThis slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Introducing Security Information And Event Management Security Intelligence Services to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Response, Management, Cyber, Analytics, using this template. Grab it now to reap its full benefits.
-
 Security information and event management sim vs sem vs siem
Security information and event management sim vs sem vs siemIncrease audience engagement and knowledge by dispensing information using Security Information And Event Management SIM Vs SEM Vs SIEM. This template helps you present information on three stages. You can also present information on Information, Management, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Siem competitive advantage security information and event management
Siem competitive advantage security information and event managementThis slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Present the topic in a bit more detail with this SIEM Competitive Advantage Security Information And Event Management. Use it as a tool for discussion and navigation on Experience, Management, Performance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information and event management siem software challenges
Security information and event management siem software challengesThis slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. Deliver an outstanding presentation on the topic using this Security Information And Event Management SIEM Software Challenges. Dispense information and present a thorough explanation of Configurations, Respond, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Siem competitive value security information and event management
Siem competitive value security information and event managementThis slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Present the topic in a bit more detail with this SIEM Competitive Value Security Information And Event Management. Use it as a tool for discussion and navigation on SIEM Competitive Advantage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information process security information and event management
Security information process security information and event managementThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Introducing Security Information Process Security Information And Event Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Connecting, Assessing, Streaming, Protocol, using this template. Grab it now to reap its full benefits.
-
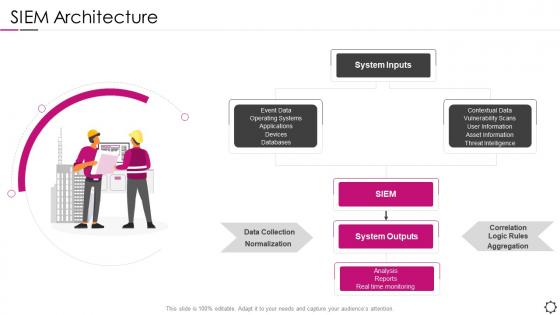 Siem architecture security information and event management
Siem architecture security information and event managementPresent the topic in a bit more detail with this SIEM Architecture Security Information And Event Management. Use it as a tool for discussion and navigation on Operating, Systems, Vulnerability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Electronic information security strategies to manage cyber risks
Electronic information security strategies to manage cyber risksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Increase audience engagement and knowledge by dispensing information using Electronic Information Security Strategies To Manage Cyber Risks. This template helps you present information on four stages. You can also present information on Prioritize Cyber Risk Strategic Issue, Build Policies And Structures, Invest Worthy Implementation, Conduct Awareness Sessions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda of effective information security risk management process
Agenda of effective information security risk management processIncrease audience engagement and knowledge by dispensing information using Agenda Of Effective Information Security Risk Management Process. This template helps you present information on three stages. You can also present information on Agenda using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Asset components effective information security risk management process
Asset components effective information security risk management processFollowing slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost.Present the topic in a bit more detail with this Asset Components Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Impact Rating On Business, Criticality Rating, Failure Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Budget for information effective information security risk management process
Budget for information effective information security risk management processMentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost.Deliver an outstanding presentation on the topic using this Budget For Information Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Incident Management, Asset Management, Training Duration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Defining risk level effective information security risk management process
Defining risk level effective information security risk management processFollowing slide defines the incident risk level. It includes details about risk level, risk score and its description. Deliver an outstanding presentation on the topic using this Defining Risk Level Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Immediate Controlling, Controlling Measures, Offered By The Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Defining security threats effective information security risk management process
Defining security threats effective information security risk management processThis slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures.Introducing Defining Security Threats Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Natural Disaster, Environmental Control Failures, Deliberate Software Attacks, using this template. Grab it now to reap its full benefits.
-
 Defining vulnerability rating effective information security risk management process
Defining vulnerability rating effective information security risk management processFollowing slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description.Present the topic in a bit more detail with this Defining Vulnerability Rating Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Occurrence Of Attack, Organization Is Reasonably, Organization Is Capable Enough. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security management process information security risk assessment
Effective information security management process information security risk assessmentThis slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence.Deliver an outstanding presentation on the topic using this Effective Information Security Management Process Information Security Risk Assessment. Dispense information and present a thorough explanation of Facilities And Equipment, Unauthorized Disclosure, Valuable Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Employee training schedule effective information security risk management process
Employee training schedule effective information security risk management processThis slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration.Present the topic in a bit more detail with this Employee Training Schedule Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Training Duration, Intermediate, Training Mode. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons slide for effective information security risk management process
Icons slide for effective information security risk management processPresenting our well crafted Icons Slide For Effective Information Security Risk Management Process set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Impact assessment matrix effective information security risk management process
Impact assessment matrix effective information security risk management processPresent the topic in a bit more detail with this Impact Assessment Matrix Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Minor To No Infringement, Suspected Malicious Intent, Impact Medium. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact on security performance effective information security risk management process
Impact on security performance effective information security risk management processMentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver an outstanding presentation on the topic using this Impact On Security Performance Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of After Introducing, Risk Assessment Process, Assets Efficiently using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Incident management tool effective information security risk management process
Incident management tool effective information security risk management processMentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform.Present the topic in a bit more detail with this Incident Management Tool Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Notify Employee, Message During Any Breach, Automated Workflow. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
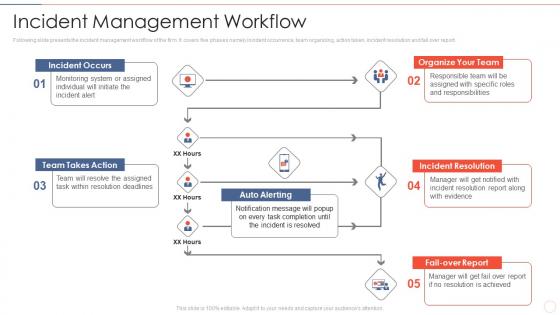 Incident management workflow effective information security risk management process
Incident management workflow effective information security risk management processFollowing slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report.Introducing Incident Management Workflow Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Organize Your Team, Incident Resolution, Team Takes Action, using this template. Grab it now to reap its full benefits.
-
 Incidents effective information security risk management process
Incidents effective information security risk management processThis slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level.Present the topic in a bit more detail with this Incidents Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Preform Primary Work Functions, Inconvenient, Medium Multiple. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
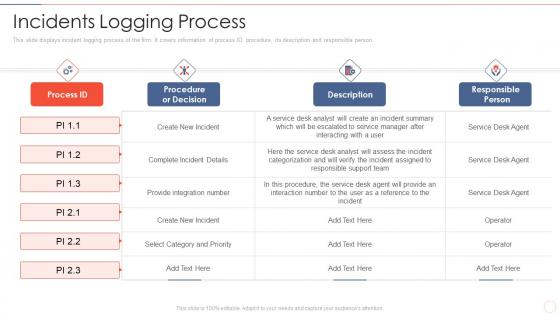 Incidents logging process effective information security risk management process
Incidents logging process effective information security risk management processThis slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person.Deliver an outstanding presentation on the topic using this Incidents Logging Process Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Select Category And Priority, Procedure, The Service, Responsible Person using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information security decision effective information security risk management process
Information security decision effective information security risk management processIncrease audience engagement and knowledge by dispensing information using Information Security Decision Effective Information Security Risk Management Process. This template helps you present information on eight stages. You can also present information on Risk Management, Implementation Responsiveness, Prioritization Weighting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information security effective information security risk management process
Information security effective information security risk management processMentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm.Present the topic in a bit more detail with this Information Security Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Asset And Consequences, Overheating In Server Room, Asset And Consequences. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introducing process workflow effective information security risk management process
Introducing process workflow effective information security risk management processFollowing slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results Deliver an outstanding presentation on the topic using this Introducing Process Workflow Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Threat Categorization, System Characterization, Assigned Remediation Measures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mitigation plan for threat effective information security risk management process
Mitigation plan for threat effective information security risk management processMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver an outstanding presentation on the topic using this Mitigation Plan For Threat Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Resources Required, Expected Resolution Time, Communication Mode using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Multitiered risk effective information security risk management process
Multitiered risk effective information security risk management processIntroducing Multitiered Risk Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Orgnization, Mission Or Business Processes, Information Systems, using this template. Grab it now to reap its full benefits.
-
 Present security effective information security risk management process
Present security effective information security risk management processFollowing slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings.Present the topic in a bit more detail with this Present Security Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Assessing Information, Incident Occurrence Identification, Vulnerability Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk reporting and likelihood effective information security risk management process
Risk reporting and likelihood effective information security risk management processMentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an outstanding presentation on the topic using this Risk Reporting And Likelihood Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Attack Scenario, Risk Encountered, Equipment Failure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Roles and responsibilities effective information security risk management process
Roles and responsibilities effective information security risk management processFollowing slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development.Increase audience engagement and knowledge by dispensing information using Roles And Responsibilities Effective Information Security Risk Management Process. This template helps you present information on one stage. You can also present information on Information Management Manager, Risk Management Officer, Development And Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security risk management process incidents prioritization matrix effective information
Security risk management process incidents prioritization matrix effective informationThis slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level Present the topic in a bit more detail with this Security Risk Management Process Incidents Prioritization Matrix Effective Information. Use it as a tool for discussion and navigation on Enterprise Or Multiple Segments, Single Segment Or Entire Site, Event Underway. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
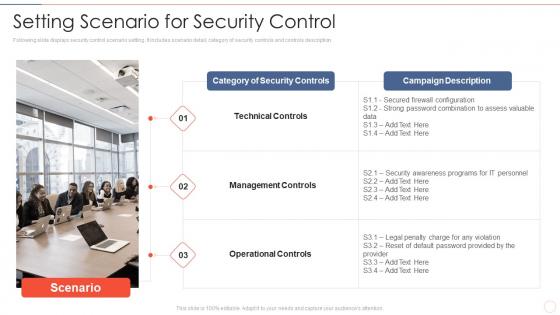 Setting scenario security control effective information security risk management process
Setting scenario security control effective information security risk management processFollowing slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Introducing Setting Scenario Security Control Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Controls, Operational Controls, Technical Controls, using this template. Grab it now to reap its full benefits.
-
 System categorization worksheet effective information security risk management process
System categorization worksheet effective information security risk management processThis slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information.Present the topic in a bit more detail with this System Categorization Worksheet Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on System Accessibility, Accessible Within Organization Boundary, Valuable Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 System disposal checklist effective information security risk management process
System disposal checklist effective information security risk management processMentioned slide shows system disposal checklist. It covers information such as system requirement, its compliance and remarks.Deliver an outstanding presentation on the topic using this System Disposal Checklist Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Stored Information Is Removed, Hardcopy Information, Requirement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 System management checklist effective information security risk management process
System management checklist effective information security risk management processFollowing slide displays system management checklist. It includes system management activities and frequency of performing them.Present the topic in a bit more detail with this System Management Checklist Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on System Monitoring, Security Patches, Virus Scanning . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table of contents for effective information security risk management process
Table of contents for effective information security risk management processDeliver an outstanding presentation on the topic using this Table Of Contents For Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Present Scenario, Training And Budget, Dashboards using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat assessment effective information security risk management process
Threat assessment effective information security risk management processFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Threat Assessment Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Affected Asset, Potential Vulnerability, Vulnerability Ranking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Effective information security budget for information security management
Effective information security budget for information security managementMentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost. Present the topic in a bit more detail with this Effective Information Security Budget For Information Security Management. Use it as a tool for discussion and navigation on Incident Management, Risk Management, Asset Management . This template is free to edit as deemed fit for your organization. Therefore download it now.





