Powerpoint Templates and Google slides for Information Cyber Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Risk Based Methodology To Cyber And Information Security Powerpoint Presentation Slides
Risk Based Methodology To Cyber And Information Security Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Risk Based Methodology To Cyber And Information Security Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the fifty four slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Information Technology Expenditure Summary Dashboard Creating Cyber Security Awareness
Information Technology Expenditure Summary Dashboard Creating Cyber Security AwarenessThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Deliver an outstanding presentation on the topic using this Information Technology Expenditure Summary Dashboard Creating Cyber Security Awareness Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Security Failure By Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats
Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Deliver an outstanding presentation on the topic using this Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Cyber Security Budget Spent, It Costs And Revenue, Issue Status Summary using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security information security ppt powerpoint presentation layouts demonstration cpb
Cyber security information security ppt powerpoint presentation layouts demonstration cpbPresenting Cyber Security Information Security Ppt Powerpoint Presentation Layouts Demonstration Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Security Information Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Information System Shield For Cyber Security Icon
Information System Shield For Cyber Security IconIntroducing our premium set of slides with Information System Shield For Cyber Security Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information System, Shield For Cyber Security Icon. So download instantly and tailor it with your information.
-
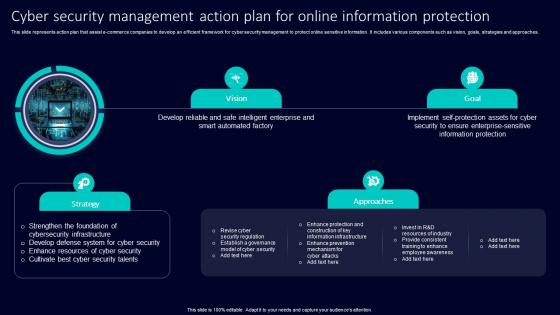 Cyber Security Management Action Plan For Online Information Protection
Cyber Security Management Action Plan For Online Information ProtectionThis slide represents action plan that assist e commerce companies to develop an efficient framework for cyber security management to protect online sensitive information. It includes various components such as vision, goals, strategies and approaches. Presenting our set of slides with Cyber Security Management Action Plan For Online Information Protection. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Strengthen Foundation Cybersecurity Infrastructure, Develop Defense System Cyber Security, Enhance Resources Cyber Security.
-
 Identify Threat And Vulnerabilities Within Information System Creating Cyber Security Awareness
Identify Threat And Vulnerabilities Within Information System Creating Cyber Security AwarenessThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Deliver an outstanding presentation on the topic using this Identify Threat And Vulnerabilities Within Information System Creating Cyber Security Awareness Dispense information and present a thorough explanation of Unclear Storage Mechanism, Monitor User Behaviour, No Appropriate Structure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber Security
Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber SecurityThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Deliver an outstanding presentation on the topic using this Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber Security Dispense information and present a thorough explanation of Vulnerability, Threat, Threat Source using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Policy Framework For Cyber Information Security
Policy Framework For Cyber Information SecurityThis slide covers key components of an information security policy. The purpose of this template is to serve as a quick reference guide for each component including purpose, audience, information security objectives, data classification, data operations, and responsibilities of personnel. Presenting our set of slides with Policy Framework For Cyber Information Security This exhibits information on Eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Purpose, Audience, Information Security Objectives
-
 Cyber Security Information Technology List
Cyber Security Information Technology ListThis slide showcases list of cyber security data technology. The purpose of this template is to help businesses in maintaining confidentiality of information systems for building trust of customers in digital age. It includes elements such as firewalls, antivirus, etc. Presenting our set of slides with name Cyber Security Information Technology List. This exhibits information on Eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Firewalls, Intrusion Detection And Prevention Systems, Antivirus, Access Control Systems.
-
 Electronic information security cyber attacks experienced company previous
Electronic information security cyber attacks experienced company previousThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Deliver an outstanding presentation on the topic using this Electronic Information Security Cyber Attacks Experienced Company Previous. Dispense information and present a thorough explanation of Cyber Attacks, Massive Increase using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
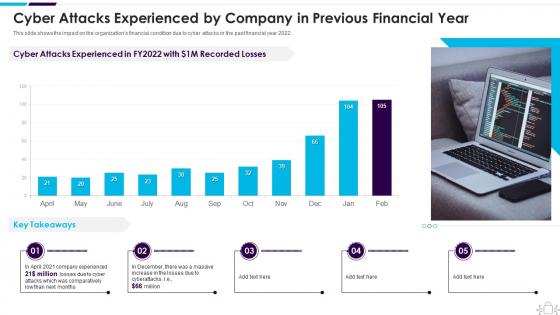 Cyber Attacks Experienced By Company In Previous Information Technology Security
Cyber Attacks Experienced By Company In Previous Information Technology SecurityThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Present the topic in a bit more detail with this Cyber Attacks Experienced By Company In Previous Information Technology Security. Use it as a tool for discussion and navigation on Experienced, Previous, Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Organization In Previous Information Security Risk Management
Cyber Attacks Faced By Organization In Previous Information Security Risk ManagementThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different types of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization In Previous Information Security Risk Management. Dispense information and present a thorough explanation of Cyber Attacks Faced, Organization, Previous Financial Year using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk Administration
Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk AdministrationThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk Administration. Dispense information and present a thorough explanation of Organization Experienced, Increasing A Rapid Rate, Financial Year using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
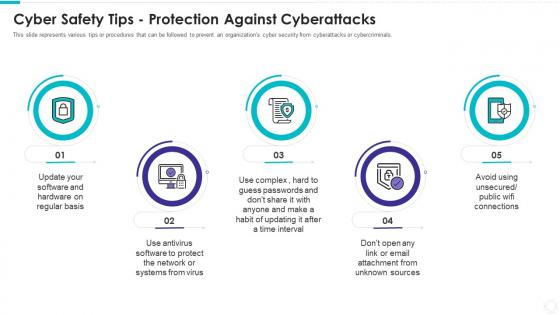 Electronic information security cyber safety tips protection against cyberattacks
Electronic information security cyber safety tips protection against cyberattacksThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Introducing Electronic Information Security Cyber Safety Tips Protection Against Cyberattacks to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Regular Basis, Protect Network, Systems Virustime Interval, Email Attachment Unknown Sources, using this template. Grab it now to reap its full benefits.
-
 Electronic information security cyber threat landscape in cloud security
Electronic information security cyber threat landscape in cloud securityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Present the topic in a bit more detail with this Electronic Information Security Cyber Threat Landscape In Cloud Security. Use it as a tool for discussion and navigation on Organized Criminals, Hacktivists, Nation States, Insiders Partners, Competitors. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information gathering cyber security ppt powerpoint presentation portfolio display cpb
Information gathering cyber security ppt powerpoint presentation portfolio display cpbIncrease audience engagement and knowledge by dispensing information using Information Gathering Cyber Security Ppt Powerpoint Presentation Portfolio Display Cpb. This template helps you present information on five stages. You can also present information on Information Gathering Cyber Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
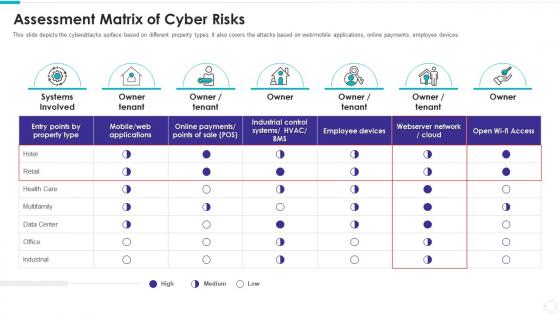 Electronic information security assessment matrix of cyber risks
Electronic information security assessment matrix of cyber risksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Present the topic in a bit more detail with this Electronic Information Security Assessment Matrix Of Cyber Risks. Use it as a tool for discussion and navigation on Systems Involved, Owner Tenant, Data Center, Industrial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Electronic information security strategies to manage cyber risks
Electronic information security strategies to manage cyber risksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Increase audience engagement and knowledge by dispensing information using Electronic Information Security Strategies To Manage Cyber Risks. This template helps you present information on four stages. You can also present information on Prioritize Cyber Risk Strategic Issue, Build Policies And Structures, Invest Worthy Implementation, Conduct Awareness Sessions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 5 practices of information and cyber security risk management
5 practices of information and cyber security risk managementMentioned slide delineates best practices for information security risk management. Knowledge of IT environment and assets, developing risk management strategy, embedding risk management into organization culture, continuous risk assessment and security protocols are the practices covered in this slide. Presenting our set of slides with 5 Practices Of Information And Cyber Security Risk Management. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Management, Organization, Risk.
-
 Cyber and information security risk management framework
Cyber and information security risk management frameworkMentioned slide exhibits information security risk management framework which can be used to enhance cybersecurity of organization. The various components covered in this framework are service design, transition and operationalization, penetration testing etc. Introducing our Cyber And Information Security Risk Management Framework set of slides. The topics discussed in these slides are Development, Service Transition, Service Operationalization. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon for information and cyber security risk management
Icon for information and cyber security risk managementIntroducing our premium set of slides with Icon For Information And Cyber Security Risk Management. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon For Information And Cyber Security Risk Management. So download instantly and tailor it with your information.
-
 Information and cyber security risk management maturity levels
Information and cyber security risk management maturity levelsMentioned slide showcase maturity stages of information security risk management, which will assist company to develop comprehensive cybersecurity strategy. The maturity stages could be Partial informed repetitive and adaptive. Introducing our premium set of slides with Information And Cyber Security Risk Management Maturity Levels. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Partial, Informed, Repetitive. So download instantly and tailor it with your information.
-
 Information and cyber security risk management plan
Information and cyber security risk management planMentioned slide showcase information security risk management plan. The template provides information about various risks such as DDoS, crypto jacking, malware and password theft and with other details like degree of risk involved, impact, strategies to be deployed. Introducing our Information And Cyber Security Risk Management Plan set of slides. The topics discussed in these slides are Degree Of Risk, Strategies, Devices. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information security program framework managing cyber risk in a digital age
Information security program framework managing cyber risk in a digital ageMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver an outstanding presentation on the topic using this Information Security Program Framework Managing Cyber Risk In A Digital Age. Dispense information and present a thorough explanation of Information Security Program Framework Key Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing cyber risk in a digital age information security program values to business
Managing cyber risk in a digital age information security program values to businessFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Introducing Managing Cyber Risk In A Digital Age Information Security Program Values To Business to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Response, Management, Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Cyber threat security icon to capture sensitive information
Cyber threat security icon to capture sensitive informationIntroducing our premium set of slides with Cyber Threat Security Icon To Capture Sensitive Information. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Threat Security Icon To Capture Sensitive Information. So download instantly and tailor it with your information.
-
 Risk Based Methodology To Cyber And Information Security Table Of Contents
Risk Based Methodology To Cyber And Information Security Table Of ContentsDeliver an outstanding presentation on the topic using this Risk Based Methodology To Cyber And Information Security Table Of Contents Dispense information and present a thorough explanation of Threat Matrix, Identified Assets, Impact Assessment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Based Methodology To Cyber Information Security Program Framework Key Components
Risk Based Methodology To Cyber Information Security Program Framework Key ComponentsMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc.Introducing Risk Based Methodology To Cyber Information Security Program Framework Key Components to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Culture And Awareness, Security Risk Management, Data Security And Privacy, using this template. Grab it now to reap its full benefits.
-
 Information Security Assessment Matrix Of Cyber Risks
Information Security Assessment Matrix Of Cyber RisksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Present the topic in a bit more detail with this Information Security Assessment Matrix Of Cyber Risks. Use it as a tool for discussion and navigation on Assessment Matrix Of Cyber Risks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Cyber Threat Landscape In Information Security
Information Security Cyber Threat Landscape In Information SecurityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Present the topic in a bit more detail with this Information Security Cyber Threat Landscape In Information Security. Use it as a tool for discussion and navigation on Landscape, Information, Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Strategies To Manage Cyber Risks
Information Security Strategies To Manage Cyber RisksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Introducing Information Security Strategies To Manage Cyber Risks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strategies To Manage Cyber Risks, using this template. Grab it now to reap its full benefits.
-
 Information Security Program Cybersecurity Communication Plan For Cyber Breaches
Information Security Program Cybersecurity Communication Plan For Cyber BreachesMentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Communication Plan For Cyber Breaches. Dispense information and present a thorough explanation of Communication Plan For Cyber Breaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Defining Business Priorities To Ensure Information Security Risk Based Methodology To Cyber
Defining Business Priorities To Ensure Information Security Risk Based Methodology To CyberThis slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security.Increase audience engagement and knowledge by dispensing information using Defining Business Priorities To Ensure Information Security Risk Based Methodology To Cyber This template helps you present information on three stages. You can also present information on Efficient Risk Management, Transparent Communication, Standardized Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Risk Based Methodology To Cyber and Information Security
Icons Slide For Risk Based Methodology To Cyber and Information SecurityPresenting our well crafted Icons Slide For Risk Based Methodology To Cyber and Information Security set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Information Security Program Framework Key Components Risk Based Methodology To Cyber
Information Security Program Framework Key Components Risk Based Methodology To CyberMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc.Introducing Information Security Program Framework Key Components Risk Based Methodology To Cyber to increase your presentation threshold. Encompassed with one stage this template is a great option to educate and entice your audience. Dispence information on Culture And Awareness, Security Risk Management, Data Security And Privacy using this template. Grab it now to reap its full benefits.
-
 Information Security Program Values To Business Risk Based Methodology To Cyber
Information Security Program Values To Business Risk Based Methodology To CyberFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management.Increase audience engagement and knowledge by dispensing information using Information Security Program Values To Business Risk Based Methodology To Cyber This template helps you present information on two stages. You can also present information on Undetectable By Current, Vulnerabilities In The Current, Threats To The Companys Environment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents For Risk Based Methodology To Cyber and Information Security
Table Of Contents For Risk Based Methodology To Cyber and Information SecurityPresent the topic in a bit more detail with this Table Of Contents For Risk Based Methodology To Cyber and Information Security Use it as a tool for discussion and navigation on Defining Business Priorities, Global Market Insights, Companies Digitization Levels This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Assessment Matrix Of Cyber Risks
Information Technology Security Assessment Matrix Of Cyber RisksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an outstanding presentation on the topic using this Information Technology Security Assessment Matrix Of Cyber Risks. Dispense information and present a thorough explanation of Assessment Matrix Of Cyber Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Cyber Threat Landscape In Information Technology Security
Information Technology Security Cyber Threat Landscape In Information Technology SecurityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver an outstanding presentation on the topic using this Information Technology Security Cyber Threat Landscape In Information Technology Security. Dispense information and present a thorough explanation of Landscape, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Strategies To Manage Cyber Risks
Information Technology Security Strategies To Manage Cyber RisksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Increase audience engagement and knowledge by dispensing information using Information Technology Security Strategies To Manage Cyber Risks. This template helps you present information on four stages. You can also present information on Strategic, Structures, Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Individual Cyber Security Insurance Ppt Powerpoint Presentation Ideas Information Cpb
Individual Cyber Security Insurance Ppt Powerpoint Presentation Ideas Information CpbPresenting our Individual Cyber Security Insurance Ppt Powerpoint Presentation Ideas Information Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Individual Cyber Security Insurance This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
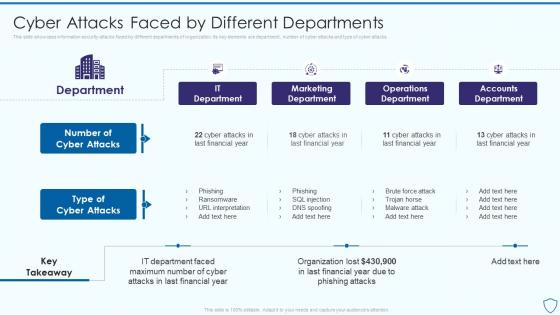 Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different
Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By DifferentThis slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks Deliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different. Dispense information and present a thorough explanation of Marketing Department, Operations Department, Accounts Department using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Cyber Security Icon
Information Technology Cyber Security IconIntroducing our premium set of slides with Information Technology Cyber Security Icon. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Technology, Cyber Security. So download instantly and tailor it with your information.
-
 Information And Cyber Security Policy Development
Information And Cyber Security Policy DevelopmentThe following slide highlights the information and cyber security policy development by depicting purpose, audience, information security, access control, data segregation, data support, security awareness and responsibilities. Introducing our premium set of slides with name Information And Cyber Security Policy Development. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Awareness, Responsibilities, Information Security, Data Segregation. So download instantly and tailor it with your information.
-
 Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems
Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology SystemsThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Threat Risk, Risk Mitigation Plan, Risk Owner. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Elements IT Information Security Element Of Cyber Security Ppt Microsoft
Cyber Security Elements IT Information Security Element Of Cyber Security Ppt MicrosoftThis slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. These are also known as cyber security objectives. Increase audience engagement and knowledge by dispensing information using Cyber Security Elements IT Information Security Element Of Cyber Security Ppt Microsoft. This template helps you present information on three stages. You can also present information on Confidentiality, Availability, Integrity, Information Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Risk Management Icon In Information Technology
Cyber Security Risk Management Icon In Information TechnologyPresent the topic in a bit more detail with this Cyber Security Risk Management Icon In Information Technology. Use it as a tool for discussion and navigation on Cyber Security, Risk Management, Icon In Information Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Different Departments Information Security Risk Management
Cyber Attacks Faced By Different Departments Information Security Risk ManagementThis slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Introducing Cyber Attacks Faced By Different Departments Information Security Risk Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispense information on Department, Number Of Cyber Attacks, Type Of Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security Operations
Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security OperationsThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Increase audience engagement and knowledge by dispensing information using Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security Operations. This template helps you present information on four stages. You can also present information on Ineffective, Information, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Attacks Faced By Different Departments Information System Security And Risk Administration Plan
Cyber Attacks Faced By Different Departments Information System Security And Risk Administration PlanThis slide showcases information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Present the topic in a bit more detail with this Cyber Attacks Faced By Different Departments Information System Security And Risk Administration Plan. Use it as a tool for discussion and navigation on It Department, Marketing Department, Operations Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Handler Contact Information Ppt Powerpoint Presentation Infographics
Cyber Security Incident Handler Contact Information Ppt Powerpoint Presentation InfographicsThis slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Introducing Cyber Security Incident Handler Contact Information Ppt Powerpoint Presentation Infographics to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Organisation, Cyber Security, Contact Information, using this template. Grab it now to reap its full benefits.
-
 Information Asset Cyber Security In Powerpoint And Google Slides Cpb
Information Asset Cyber Security In Powerpoint And Google Slides CpbPresenting our Information Asset Cyber Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Information Asset Cyber Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber Security Policy Critical Components Of Information Technology Policy
Cyber Security Policy Critical Components Of Information Technology PolicyThis slide depicts the critical components of information technology policy, and it includes integrity, confidentiality, and availability, including how these components work. Deliver an outstanding presentation on the topic using this Cyber Security Policy Critical Components Of Information Technology Policy. Dispense information and present a thorough explanation of Information, Technology, Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Policy Information System Change Management Policy
Cyber Security Policy Information System Change Management PolicyThis slide depicts the change management policy that includes SDLC, hardware, software, database, and application changes to system settings such as moves, adds, and deletes. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Information System Change Management Policy. This template helps you present information on seven stages. You can also present information on Information, Management, Documentation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Policy Information Technology Policy Implementation Budget For Fy2022
Cyber Security Policy Information Technology Policy Implementation Budget For Fy2022This slide represents the companys IT policy implementation budget for FY2022. It covers the details of the software application and security services that need to be purchased and updated. Present the topic in a bit more detail with this Cyber Security Policy Information Technology Policy Implementation Budget For Fy2022. Use it as a tool for discussion and navigation on Information, Technology, Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Policy Introduction To Information Technology Policy
Cyber Security Policy Introduction To Information Technology PolicyThis slide represents the introduction to information technology policy, and it also describes the components of IT policy, such as investments, business applications, architecture, and infrastructure. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Introduction To Information Technology Policy. This template helps you present information on seven stages. You can also present information on Introduction, Information, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Policy Overview Of Information Retention Policy For Employees
Cyber Security Policy Overview Of Information Retention Policy For EmployeesThis slide talks about the data retention policy, including the involved data types such as documents, customer records, transactional information, email communication, and contracts. Introducing Cyber Security Policy Overview Of Information Retention Policy For Employees to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Information, Communications, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Handler Contact Information Incident Response Strategies Deployment
Cyber Security Incident Handler Contact Information Incident Response Strategies DeploymentThis slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Handler Contact Information Incident Response Strategies Deployment. This template helps you present information on three stages. You can also present information on Organisation, Role, Contact using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
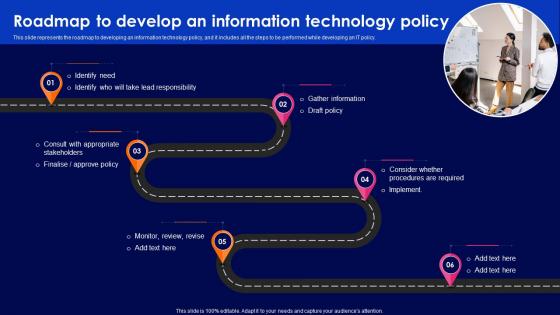 Cyber Security Policy Roadmap To Develop An Information Technology Policy
Cyber Security Policy Roadmap To Develop An Information Technology PolicyThis slide represents the roadmap to developing an information technology policy, and it includes all the steps to be performed while developing an IT policy. Introducing Cyber Security Policy Roadmap To Develop An Information Technology Policy to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Roadmap, Information, Technology, using this template. Grab it now to reap its full benefits.




